Unnamed: 0
int64 0
832k
| id
float64 2.49B
32.1B
| type
stringclasses 1
value | created_at
stringlengths 19
19
| repo
stringlengths 5
112
| repo_url
stringlengths 34
141
| action
stringclasses 3
values | title
stringlengths 1
957
| labels
stringlengths 4
795
| body
stringlengths 1
259k
| index
stringclasses 12
values | text_combine
stringlengths 96
259k
| label
stringclasses 2
values | text
stringlengths 96
252k
| binary_label
int64 0
1
|
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
24,090 | 7,452,978,295 | IssuesEvent | 2018-03-29 10:12:32 | data2viz/data2viz | https://api.github.com/repos/data2viz/data2viz | closed | Remove DCE of example for fast builds | build enhancement | It takes time during development workflow. Should only be launched for bundle task. | 1.0 | Remove DCE of example for fast builds - It takes time during development workflow. Should only be launched for bundle task. | non_priority | remove dce of example for fast builds it takes time during development workflow should only be launched for bundle task | 0 |
43,754 | 5,559,389,555 | IssuesEvent | 2017-03-24 16:49:51 | backdrop-contrib/drush | https://api.github.com/repos/backdrop-contrib/drush | closed | Sitename with ampersand causes `drush up backdrop` failure | pr - reviewed & tested by the community status - has pull request type - bug | It gives a success message but the files are not replaced correctly if the sitename contains an asterisk.
I suppose we could pretty easily add another `str_replace` [on this line](https://github.com/backdrop-contrib/drush/blob/d16a9d782c78b659abd117a04ae45355e37e7125/commands/pm/backdrop_pm.drush.inc#L310), but there are probably other problem characters out there. We may need to figure a better way to handle this part. Does [Transliteration](https://backdropcms.org/project/transliteration) provide a function that may be useful here?
```
$ drush up backdrop
Current Backdrop Version: 1.6.0
Proposed Backdrop Version: 1.6.3
Code updates will be made to Backdrop core.
WARNING: Updating core will discard any
modifications made to Backdrop core files. If you have made any
modifications to these files, please back them up before updating so that
you can re-create your modifications in the updated version of the file.
Note: Updating core can potentially break your site.
It is NOT recommended to update production sites without prior testing.
Do you wish to continue? (y or n): y
Backing up current core folder to /home/username/.drush/name_&_name2-core-1.6.0
sh: _name2-core-1.6.0: command not found
mv: cannot move `/home/username/public_html/core' to `/home/username/.drush/name_/core': File exists
No database updates required [success]
Finished performing updates. [ok]
You can retrieve your old core files, should you need
to from: /home/username/.drush/core-1.6.0
Success: Backdrop updated to 1.6.3.
``` | 1.0 | Sitename with ampersand causes `drush up backdrop` failure - It gives a success message but the files are not replaced correctly if the sitename contains an asterisk.
I suppose we could pretty easily add another `str_replace` [on this line](https://github.com/backdrop-contrib/drush/blob/d16a9d782c78b659abd117a04ae45355e37e7125/commands/pm/backdrop_pm.drush.inc#L310), but there are probably other problem characters out there. We may need to figure a better way to handle this part. Does [Transliteration](https://backdropcms.org/project/transliteration) provide a function that may be useful here?
```
$ drush up backdrop
Current Backdrop Version: 1.6.0
Proposed Backdrop Version: 1.6.3
Code updates will be made to Backdrop core.
WARNING: Updating core will discard any
modifications made to Backdrop core files. If you have made any
modifications to these files, please back them up before updating so that
you can re-create your modifications in the updated version of the file.
Note: Updating core can potentially break your site.
It is NOT recommended to update production sites without prior testing.
Do you wish to continue? (y or n): y
Backing up current core folder to /home/username/.drush/name_&_name2-core-1.6.0
sh: _name2-core-1.6.0: command not found
mv: cannot move `/home/username/public_html/core' to `/home/username/.drush/name_/core': File exists
No database updates required [success]
Finished performing updates. [ok]
You can retrieve your old core files, should you need
to from: /home/username/.drush/core-1.6.0
Success: Backdrop updated to 1.6.3.
``` | non_priority | sitename with ampersand causes drush up backdrop failure it gives a success message but the files are not replaced correctly if the sitename contains an asterisk i suppose we could pretty easily add another str replace but there are probably other problem characters out there we may need to figure a better way to handle this part does provide a function that may be useful here drush up backdrop current backdrop version proposed backdrop version code updates will be made to backdrop core warning updating core will discard any modifications made to backdrop core files if you have made any modifications to these files please back them up before updating so that you can re create your modifications in the updated version of the file note updating core can potentially break your site it is not recommended to update production sites without prior testing do you wish to continue y or n y backing up current core folder to home username drush name core sh core command not found mv cannot move home username public html core to home username drush name core file exists no database updates required finished performing updates you can retrieve your old core files should you need to from home username drush core success backdrop updated to | 0 |
12,035 | 4,349,584,679 | IssuesEvent | 2016-07-30 17:21:05 | joomla/joomla-cms | https://api.github.com/repos/joomla/joomla-cms | closed | News Feed in sample data dead? | No Code Attached Yet | #### Steps to reproduce the issue
In the sample data is a News Feed called Joomla Connect
Create a menu item to display that news feed
#### Expected result
News Feed will display
#### Actual result
0 No registered feed parser for type html.
#### System information (as much as possible)
Joomla 3.6 staging
php 7
#### Additional comments
At a guess the problem is that http://feeds.joomla.org/JoomlaConnect is no longer an rss feed
So we either have to remove the feed from the sample data or get it fixed on the web site
| 1.0 | News Feed in sample data dead? - #### Steps to reproduce the issue
In the sample data is a News Feed called Joomla Connect
Create a menu item to display that news feed
#### Expected result
News Feed will display
#### Actual result
0 No registered feed parser for type html.
#### System information (as much as possible)
Joomla 3.6 staging
php 7
#### Additional comments
At a guess the problem is that http://feeds.joomla.org/JoomlaConnect is no longer an rss feed
So we either have to remove the feed from the sample data or get it fixed on the web site
| non_priority | news feed in sample data dead steps to reproduce the issue in the sample data is a news feed called joomla connect create a menu item to display that news feed expected result news feed will display actual result no registered feed parser for type html system information as much as possible joomla staging php additional comments at a guess the problem is that is no longer an rss feed so we either have to remove the feed from the sample data or get it fixed on the web site | 0 |
14,991 | 10,239,438,542 | IssuesEvent | 2019-08-19 18:15:05 | aws/aws-lambda-dotnet | https://api.github.com/repos/aws/aws-lambda-dotnet | closed | ALB returning 502 from Lambda | guidance service-api | I've created a Lambda that check on a DynamoDB table the existence of a record matching host and request path and, if found, returns a redirect to the matching URL.
My Lambda returns this response but the ALB returns 502.
```
{
"statusCode": 301,
"statusDescription": null,
"headers": {
"Location": "https://www.my-target.co.uk/"
},
"multiValueHeaders": null,
"body": "Redirecting to https://www.my-target.co.uk/",
"isBase64Encoded": false
}
```
This is the log I find in CloudWatch for the Lambda function
```
START RequestId: 8b5a28f2-c56d-4418-a7b9-66ebe0ba2470 Version: $LATEST
[Information] EMG.ApplicationLoadBalancerRequestHandler: Received: GET /
[Information] EMG.ApplicationLoadBalancerRequestHandler: Processing: my-test.net /
[Information] EMG.RedirectManagers.RedirectTableRedirectManager: Fetching item: my-test.net / from table redirect-table
[Information] EMG.ApplicationLoadBalancerRequestHandler: Found: https://www.target.co.uk/ Permanent
END RequestId: 8b5a28f2-c56d-4418-a7b9-66ebe0ba2470
REPORT RequestId: 8b5a28f2-c56d-4418-a7b9-66ebe0ba2470 Duration: 69.59 ms Billed Duration: 100 ms Memory Size: 128 MB Max Memory Used: 39 MB
```
This is the response I get
```
HTTP/1.1 502
status: 502
Server: awselb/2.0
Date: Thu, 15 Aug 2019 19:13:58 GMT
Content-Type: text/html
Content-Length: 138
Connection: keep-alive
<html>
<head><title>502 Bad Gateway</title></head>
<body bgcolor="white">
<center><h1>502 Bad Gateway</h1></center>
</body>
</html>
```
I couldn't find anything saying we can't return non-200 responses from Lambda, so I really have no idea... | 1.0 | ALB returning 502 from Lambda - I've created a Lambda that check on a DynamoDB table the existence of a record matching host and request path and, if found, returns a redirect to the matching URL.
My Lambda returns this response but the ALB returns 502.
```
{
"statusCode": 301,
"statusDescription": null,
"headers": {
"Location": "https://www.my-target.co.uk/"
},
"multiValueHeaders": null,
"body": "Redirecting to https://www.my-target.co.uk/",
"isBase64Encoded": false
}
```
This is the log I find in CloudWatch for the Lambda function
```
START RequestId: 8b5a28f2-c56d-4418-a7b9-66ebe0ba2470 Version: $LATEST
[Information] EMG.ApplicationLoadBalancerRequestHandler: Received: GET /
[Information] EMG.ApplicationLoadBalancerRequestHandler: Processing: my-test.net /
[Information] EMG.RedirectManagers.RedirectTableRedirectManager: Fetching item: my-test.net / from table redirect-table
[Information] EMG.ApplicationLoadBalancerRequestHandler: Found: https://www.target.co.uk/ Permanent
END RequestId: 8b5a28f2-c56d-4418-a7b9-66ebe0ba2470
REPORT RequestId: 8b5a28f2-c56d-4418-a7b9-66ebe0ba2470 Duration: 69.59 ms Billed Duration: 100 ms Memory Size: 128 MB Max Memory Used: 39 MB
```
This is the response I get
```
HTTP/1.1 502
status: 502
Server: awselb/2.0
Date: Thu, 15 Aug 2019 19:13:58 GMT
Content-Type: text/html
Content-Length: 138
Connection: keep-alive
<html>
<head><title>502 Bad Gateway</title></head>
<body bgcolor="white">
<center><h1>502 Bad Gateway</h1></center>
</body>
</html>
```
I couldn't find anything saying we can't return non-200 responses from Lambda, so I really have no idea... | non_priority | alb returning from lambda i ve created a lambda that check on a dynamodb table the existence of a record matching host and request path and if found returns a redirect to the matching url my lambda returns this response but the alb returns statuscode statusdescription null headers location multivalueheaders null body redirecting to false this is the log i find in cloudwatch for the lambda function start requestid version latest emg applicationloadbalancerrequesthandler received get emg applicationloadbalancerrequesthandler processing my test net emg redirectmanagers redirecttableredirectmanager fetching item my test net from table redirect table emg applicationloadbalancerrequesthandler found permanent end requestid report requestid duration ms billed duration ms memory size mb max memory used mb this is the response i get http status server awselb date thu aug gmt content type text html content length connection keep alive bad gateway bad gateway i couldn t find anything saying we can t return non responses from lambda so i really have no idea | 0 |
208,173 | 23,584,955,799 | IssuesEvent | 2022-08-23 10:47:59 | jandhollander/spotless | https://api.github.com/repos/jandhollander/spotless | opened | sortpom-sorter-3.0.0.jar: 1 vulnerabilities (highest severity is: 7.5) | security vulnerability | <details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Library - <b>sortpom-sorter-3.0.0.jar</b></p></summary>
<p></p>
<p>Path to dependency file: /lib/build.gradle</p>
<p>Path to vulnerable library: /home/wss-scanner/.gradle/caches/modules-2/files-2.1/org.jdom/jdom/1.1.3/8bdfeb39fa929c35f5e4f0b02d34350db39a1efc/jdom-1.1.3.jar</p>
<p>
<p>Found in HEAD commit: <a href="https://github.com/jandhollander/spotless/commit/cb43de2c615b46f3b48289367981eb1862476ca3">cb43de2c615b46f3b48289367981eb1862476ca3</a></p></details>
## Vulnerabilities
| CVE | Severity | <img src='https://whitesource-resources.whitesourcesoftware.com/cvss3.png' width=19 height=20> CVSS | Dependency | Type | Fixed in | Remediation Available |
| ------------- | ------------- | ----- | ----- | ----- | --- | --- |
| [CVE-2021-33813](https://vuln.whitesourcesoftware.com/vulnerability/CVE-2021-33813) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 7.5 | jdom-1.1.3.jar | Transitive | N/A | ❌ |
## Details
<details>
<summary><img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> CVE-2021-33813</summary>
### Vulnerable Library - <b>jdom-1.1.3.jar</b></p>
<p>A complete, Java-based solution for accessing, manipulating,
and outputting XML data</p>
<p>Library home page: <a href="http://www.jdom.org">http://www.jdom.org</a></p>
<p>Path to dependency file: /lib/build.gradle</p>
<p>Path to vulnerable library: /home/wss-scanner/.gradle/caches/modules-2/files-2.1/org.jdom/jdom/1.1.3/8bdfeb39fa929c35f5e4f0b02d34350db39a1efc/jdom-1.1.3.jar</p>
<p>
Dependency Hierarchy:
- sortpom-sorter-3.0.0.jar (Root Library)
- :x: **jdom-1.1.3.jar** (Vulnerable Library)
<p>Found in HEAD commit: <a href="https://github.com/jandhollander/spotless/commit/cb43de2c615b46f3b48289367981eb1862476ca3">cb43de2c615b46f3b48289367981eb1862476ca3</a></p>
<p>Found in base branch: <b>main</b></p>
</p>
<p></p>
### Vulnerability Details
<p>
An XXE issue in SAXBuilder in JDOM through 2.0.6 allows attackers to cause a denial of service via a crafted HTTP request.
<p>Publish Date: 2021-06-16
<p>URL: <a href=https://vuln.whitesourcesoftware.com/vulnerability/CVE-2021-33813>CVE-2021-33813</a></p>
</p>
<p></p>
### CVSS 3 Score Details (<b>7.5</b>)
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: None
- Integrity Impact: None
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
<p></p>
### Suggested Fix
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://nvd.nist.gov/vuln/detail/CVE-2021-33813">https://nvd.nist.gov/vuln/detail/CVE-2021-33813</a></p>
<p>Release Date: 2021-06-16</p>
<p>Fix Resolution: org.apache.servicemix.bundles:org.apache.servicemix.bundles.jdom - 2.0.5_1;org.jdom:jdom2:2.0.6.1</p>
</p>
<p></p>
Step up your Open Source Security Game with Mend [here](https://www.whitesourcesoftware.com/full_solution_bolt_github)
</details> | True | sortpom-sorter-3.0.0.jar: 1 vulnerabilities (highest severity is: 7.5) - <details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Library - <b>sortpom-sorter-3.0.0.jar</b></p></summary>
<p></p>
<p>Path to dependency file: /lib/build.gradle</p>
<p>Path to vulnerable library: /home/wss-scanner/.gradle/caches/modules-2/files-2.1/org.jdom/jdom/1.1.3/8bdfeb39fa929c35f5e4f0b02d34350db39a1efc/jdom-1.1.3.jar</p>
<p>
<p>Found in HEAD commit: <a href="https://github.com/jandhollander/spotless/commit/cb43de2c615b46f3b48289367981eb1862476ca3">cb43de2c615b46f3b48289367981eb1862476ca3</a></p></details>
## Vulnerabilities
| CVE | Severity | <img src='https://whitesource-resources.whitesourcesoftware.com/cvss3.png' width=19 height=20> CVSS | Dependency | Type | Fixed in | Remediation Available |
| ------------- | ------------- | ----- | ----- | ----- | --- | --- |
| [CVE-2021-33813](https://vuln.whitesourcesoftware.com/vulnerability/CVE-2021-33813) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 7.5 | jdom-1.1.3.jar | Transitive | N/A | ❌ |
## Details
<details>
<summary><img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> CVE-2021-33813</summary>
### Vulnerable Library - <b>jdom-1.1.3.jar</b></p>
<p>A complete, Java-based solution for accessing, manipulating,
and outputting XML data</p>
<p>Library home page: <a href="http://www.jdom.org">http://www.jdom.org</a></p>
<p>Path to dependency file: /lib/build.gradle</p>
<p>Path to vulnerable library: /home/wss-scanner/.gradle/caches/modules-2/files-2.1/org.jdom/jdom/1.1.3/8bdfeb39fa929c35f5e4f0b02d34350db39a1efc/jdom-1.1.3.jar</p>
<p>
Dependency Hierarchy:
- sortpom-sorter-3.0.0.jar (Root Library)
- :x: **jdom-1.1.3.jar** (Vulnerable Library)
<p>Found in HEAD commit: <a href="https://github.com/jandhollander/spotless/commit/cb43de2c615b46f3b48289367981eb1862476ca3">cb43de2c615b46f3b48289367981eb1862476ca3</a></p>
<p>Found in base branch: <b>main</b></p>
</p>
<p></p>
### Vulnerability Details
<p>
An XXE issue in SAXBuilder in JDOM through 2.0.6 allows attackers to cause a denial of service via a crafted HTTP request.
<p>Publish Date: 2021-06-16
<p>URL: <a href=https://vuln.whitesourcesoftware.com/vulnerability/CVE-2021-33813>CVE-2021-33813</a></p>
</p>
<p></p>
### CVSS 3 Score Details (<b>7.5</b>)
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: None
- Integrity Impact: None
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
<p></p>
### Suggested Fix
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://nvd.nist.gov/vuln/detail/CVE-2021-33813">https://nvd.nist.gov/vuln/detail/CVE-2021-33813</a></p>
<p>Release Date: 2021-06-16</p>
<p>Fix Resolution: org.apache.servicemix.bundles:org.apache.servicemix.bundles.jdom - 2.0.5_1;org.jdom:jdom2:2.0.6.1</p>
</p>
<p></p>
Step up your Open Source Security Game with Mend [here](https://www.whitesourcesoftware.com/full_solution_bolt_github)
</details> | non_priority | sortpom sorter jar vulnerabilities highest severity is vulnerable library sortpom sorter jar path to dependency file lib build gradle path to vulnerable library home wss scanner gradle caches modules files org jdom jdom jdom jar found in head commit a href vulnerabilities cve severity cvss dependency type fixed in remediation available high jdom jar transitive n a details cve vulnerable library jdom jar a complete java based solution for accessing manipulating and outputting xml data library home page a href path to dependency file lib build gradle path to vulnerable library home wss scanner gradle caches modules files org jdom jdom jdom jar dependency hierarchy sortpom sorter jar root library x jdom jar vulnerable library found in head commit a href found in base branch main vulnerability details an xxe issue in saxbuilder in jdom through allows attackers to cause a denial of service via a crafted http request publish date url a href cvss score details base score metrics exploitability metrics attack vector network attack complexity low privileges required none user interaction none scope unchanged impact metrics confidentiality impact none integrity impact none availability impact high for more information on scores click a href suggested fix type upgrade version origin a href release date fix resolution org apache servicemix bundles org apache servicemix bundles jdom org jdom step up your open source security game with mend | 0 |
83,313 | 16,112,458,435 | IssuesEvent | 2021-04-28 00:02:54 | distributed-system-analysis/pbench | https://api.github.com/repos/distributed-system-analysis/pbench | closed | Refactor Tool Meister work to move common variables, constants, methods, functions, and classes to a proper module | Agent Code Infrastructure enhancement tools | The Tool Meister work provides a number of opportunities to condense code and re-use (not repeat) structures and definitions for variables, constants, methods, functions, and classes. Move these to a proper Python3 module hierarchy would be great. | 1.0 | Refactor Tool Meister work to move common variables, constants, methods, functions, and classes to a proper module - The Tool Meister work provides a number of opportunities to condense code and re-use (not repeat) structures and definitions for variables, constants, methods, functions, and classes. Move these to a proper Python3 module hierarchy would be great. | non_priority | refactor tool meister work to move common variables constants methods functions and classes to a proper module the tool meister work provides a number of opportunities to condense code and re use not repeat structures and definitions for variables constants methods functions and classes move these to a proper module hierarchy would be great | 0 |
75,238 | 15,397,079,207 | IssuesEvent | 2021-03-03 21:35:30 | idonthaveafifaaddiction/visx | https://api.github.com/repos/idonthaveafifaaddiction/visx | opened | CVE-2019-11358 (Medium) detected in jquery-1.11.3.js | security vulnerability | ## CVE-2019-11358 - Medium Severity Vulnerability
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Library - <b>jquery-1.11.3.js</b></p></summary>
<p>JavaScript library for DOM operations</p>
<p>Library home page: <a href="https://cdnjs.cloudflare.com/ajax/libs/jquery/1.11.3/jquery.js">https://cdnjs.cloudflare.com/ajax/libs/jquery/1.11.3/jquery.js</a></p>
<p>Path to dependency file: visx/node_modules/es6-shim/test/index.html</p>
<p>Path to vulnerable library: visx/node_modules/es6-shim/test/index.html</p>
<p>
Dependency Hierarchy:
- :x: **jquery-1.11.3.js** (Vulnerable Library)
<p>Found in HEAD commit: <a href="https://github.com/idonthaveafifaaddiction/visx/commit/d093d266b596a350577f1132623e642c2d77cdeb">d093d266b596a350577f1132623e642c2d77cdeb</a></p>
<p>Found in base branch: <b>master</b></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/medium_vul.png' width=19 height=20> Vulnerability Details</summary>
<p>
jQuery before 3.4.0, as used in Drupal, Backdrop CMS, and other products, mishandles jQuery.extend(true, {}, ...) because of Object.prototype pollution. If an unsanitized source object contained an enumerable __proto__ property, it could extend the native Object.prototype.
<p>Publish Date: 2019-04-20
<p>URL: <a href=https://vuln.whitesourcesoftware.com/vulnerability/CVE-2019-11358>CVE-2019-11358</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/cvss3.png' width=19 height=20> CVSS 3 Score Details (<b>6.1</b>)</summary>
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: Required
- Scope: Changed
- Impact Metrics:
- Confidentiality Impact: Low
- Integrity Impact: Low
- Availability Impact: None
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/suggested_fix.png' width=19 height=20> Suggested Fix</summary>
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-11358">https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-11358</a></p>
<p>Release Date: 2019-04-20</p>
<p>Fix Resolution: 3.4.0</p>
</p>
</details>
<p></p>
<!-- <REMEDIATE>{"isOpenPROnVulnerability":false,"isPackageBased":true,"isDefaultBranch":true,"packages":[{"packageType":"JavaScript","packageName":"jquery","packageVersion":"1.11.3","packageFilePaths":["/node_modules/es6-shim/test/index.html"],"isTransitiveDependency":false,"dependencyTree":"jquery:1.11.3","isMinimumFixVersionAvailable":true,"minimumFixVersion":"3.4.0"}],"baseBranches":["master"],"vulnerabilityIdentifier":"CVE-2019-11358","vulnerabilityDetails":"jQuery before 3.4.0, as used in Drupal, Backdrop CMS, and other products, mishandles jQuery.extend(true, {}, ...) because of Object.prototype pollution. If an unsanitized source object contained an enumerable __proto__ property, it could extend the native Object.prototype.","vulnerabilityUrl":"https://vuln.whitesourcesoftware.com/vulnerability/CVE-2019-11358","cvss3Severity":"medium","cvss3Score":"6.1","cvss3Metrics":{"A":"None","AC":"Low","PR":"None","S":"Changed","C":"Low","UI":"Required","AV":"Network","I":"Low"},"extraData":{}}</REMEDIATE> --> | True | CVE-2019-11358 (Medium) detected in jquery-1.11.3.js - ## CVE-2019-11358 - Medium Severity Vulnerability
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Library - <b>jquery-1.11.3.js</b></p></summary>
<p>JavaScript library for DOM operations</p>
<p>Library home page: <a href="https://cdnjs.cloudflare.com/ajax/libs/jquery/1.11.3/jquery.js">https://cdnjs.cloudflare.com/ajax/libs/jquery/1.11.3/jquery.js</a></p>
<p>Path to dependency file: visx/node_modules/es6-shim/test/index.html</p>
<p>Path to vulnerable library: visx/node_modules/es6-shim/test/index.html</p>
<p>
Dependency Hierarchy:
- :x: **jquery-1.11.3.js** (Vulnerable Library)
<p>Found in HEAD commit: <a href="https://github.com/idonthaveafifaaddiction/visx/commit/d093d266b596a350577f1132623e642c2d77cdeb">d093d266b596a350577f1132623e642c2d77cdeb</a></p>
<p>Found in base branch: <b>master</b></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/medium_vul.png' width=19 height=20> Vulnerability Details</summary>
<p>
jQuery before 3.4.0, as used in Drupal, Backdrop CMS, and other products, mishandles jQuery.extend(true, {}, ...) because of Object.prototype pollution. If an unsanitized source object contained an enumerable __proto__ property, it could extend the native Object.prototype.
<p>Publish Date: 2019-04-20
<p>URL: <a href=https://vuln.whitesourcesoftware.com/vulnerability/CVE-2019-11358>CVE-2019-11358</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/cvss3.png' width=19 height=20> CVSS 3 Score Details (<b>6.1</b>)</summary>
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: Required
- Scope: Changed
- Impact Metrics:
- Confidentiality Impact: Low
- Integrity Impact: Low
- Availability Impact: None
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/suggested_fix.png' width=19 height=20> Suggested Fix</summary>
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-11358">https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-11358</a></p>
<p>Release Date: 2019-04-20</p>
<p>Fix Resolution: 3.4.0</p>
</p>
</details>
<p></p>
<!-- <REMEDIATE>{"isOpenPROnVulnerability":false,"isPackageBased":true,"isDefaultBranch":true,"packages":[{"packageType":"JavaScript","packageName":"jquery","packageVersion":"1.11.3","packageFilePaths":["/node_modules/es6-shim/test/index.html"],"isTransitiveDependency":false,"dependencyTree":"jquery:1.11.3","isMinimumFixVersionAvailable":true,"minimumFixVersion":"3.4.0"}],"baseBranches":["master"],"vulnerabilityIdentifier":"CVE-2019-11358","vulnerabilityDetails":"jQuery before 3.4.0, as used in Drupal, Backdrop CMS, and other products, mishandles jQuery.extend(true, {}, ...) because of Object.prototype pollution. If an unsanitized source object contained an enumerable __proto__ property, it could extend the native Object.prototype.","vulnerabilityUrl":"https://vuln.whitesourcesoftware.com/vulnerability/CVE-2019-11358","cvss3Severity":"medium","cvss3Score":"6.1","cvss3Metrics":{"A":"None","AC":"Low","PR":"None","S":"Changed","C":"Low","UI":"Required","AV":"Network","I":"Low"},"extraData":{}}</REMEDIATE> --> | non_priority | cve medium detected in jquery js cve medium severity vulnerability vulnerable library jquery js javascript library for dom operations library home page a href path to dependency file visx node modules shim test index html path to vulnerable library visx node modules shim test index html dependency hierarchy x jquery js vulnerable library found in head commit a href found in base branch master vulnerability details jquery before as used in drupal backdrop cms and other products mishandles jquery extend true because of object prototype pollution if an unsanitized source object contained an enumerable proto property it could extend the native object prototype publish date url a href cvss score details base score metrics exploitability metrics attack vector network attack complexity low privileges required none user interaction required scope changed impact metrics confidentiality impact low integrity impact low availability impact none for more information on scores click a href suggested fix type upgrade version origin a href release date fix resolution isopenpronvulnerability false ispackagebased true isdefaultbranch true packages istransitivedependency false dependencytree jquery isminimumfixversionavailable true minimumfixversion basebranches vulnerabilityidentifier cve vulnerabilitydetails jquery before as used in drupal backdrop cms and other products mishandles jquery extend true because of object prototype pollution if an unsanitized source object contained an enumerable proto property it could extend the native object prototype vulnerabilityurl | 0 |
22,093 | 3,594,434,899 | IssuesEvent | 2016-02-01 23:40:36 | Cockatrice/Cockatrice | https://api.github.com/repos/Cockatrice/Cockatrice | closed | Putting cards on the bottom of your library in a random order (Cascade) | App - Cockatrice App - Protocol / API App - Servatrice Defect - Game Rules Compliance | I think this is a "Defect - Game Rules Compliance".
At the moment it is not possible to accurately resolve a Cascade trigger.
The cards revealed and not cast can not be put on the bottom of your library in random order.
Especially relevent if higher numbers of cards are flipped and you would be almost stacking your deck.
702.84. Cascade
702.84a Cascade is a triggered ability that functions only while the spell with cascade is on the stack. “Cascade” means “When you cast this spell, exile cards from the top of your library until you exile a nonland card whose converted mana cost is less than this spell’s converted mana cost. You may cast that card without paying its mana cost. Then put all cards exiled this way that weren’t cast on the bottom of your library in a random order.” | 1.0 | Putting cards on the bottom of your library in a random order (Cascade) - I think this is a "Defect - Game Rules Compliance".
At the moment it is not possible to accurately resolve a Cascade trigger.
The cards revealed and not cast can not be put on the bottom of your library in random order.
Especially relevent if higher numbers of cards are flipped and you would be almost stacking your deck.
702.84. Cascade
702.84a Cascade is a triggered ability that functions only while the spell with cascade is on the stack. “Cascade” means “When you cast this spell, exile cards from the top of your library until you exile a nonland card whose converted mana cost is less than this spell’s converted mana cost. You may cast that card without paying its mana cost. Then put all cards exiled this way that weren’t cast on the bottom of your library in a random order.” | non_priority | putting cards on the bottom of your library in a random order cascade i think this is a defect game rules compliance at the moment it is not possible to accurately resolve a cascade trigger the cards revealed and not cast can not be put on the bottom of your library in random order especially relevent if higher numbers of cards are flipped and you would be almost stacking your deck cascade cascade is a triggered ability that functions only while the spell with cascade is on the stack “cascade” means “when you cast this spell exile cards from the top of your library until you exile a nonland card whose converted mana cost is less than this spell’s converted mana cost you may cast that card without paying its mana cost then put all cards exiled this way that weren’t cast on the bottom of your library in a random order ” | 0 |
286,300 | 31,476,900,442 | IssuesEvent | 2023-08-30 11:22:16 | Trinadh465/platform_hardware_interfaces | https://api.github.com/repos/Trinadh465/platform_hardware_interfaces | opened | CVE-2021-0587 (High) detected in https://source.codeaurora.org/quic/la/platform/hardware/interfaces/LA.AU.0.1.0.r1-03400-gen3meta.0, https://source.codeaurora.org/quic/la/platform/hardware/interfaces/LA.AU.0.1.0.r1-03400-gen3meta.0 | Mend: dependency security vulnerability | ## CVE-2021-0587 - High Severity Vulnerability
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Libraries - <b>https://source.codeaurora.org/quic/la/platform/hardware/interfaces/LA.AU.0.1.0.r1-03400-gen3meta.0</b>, <b>https://source.codeaurora.org/quic/la/platform/hardware/interfaces/LA.AU.0.1.0.r1-03400-gen3meta.0</b></p></summary>
<p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png?' width=19 height=20> Vulnerability Details</summary>
<p>
In StreamOut::prepareForWriting of StreamOut.cpp, there is a possible out of bounds write due to a use after free. This could lead to local escalation of privilege with no additional execution privileges needed. User interaction is not needed for exploitation.Product: AndroidVersions: Android-8.1 Android-9 Android-10 Android-11Android ID: A-185259758
<p>Publish Date: 2021-07-14
<p>URL: <a href=https://www.mend.io/vulnerability-database/CVE-2021-0587>CVE-2021-0587</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/cvss3.png' width=19 height=20> CVSS 3 Score Details (<b>7.8</b>)</summary>
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Local
- Attack Complexity: Low
- Privileges Required: Low
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: High
- Integrity Impact: High
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/suggested_fix.png' width=19 height=20> Suggested Fix</summary>
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://source.android.com/security/bulletin/2021-07-01">https://source.android.com/security/bulletin/2021-07-01</a></p>
<p>Release Date: 2020-11-07</p>
<p>Fix Resolution: android-11.0.0_r39</p>
</p>
</details>
<p></p>
***
Step up your Open Source Security Game with Mend [here](https://www.whitesourcesoftware.com/full_solution_bolt_github) | True | CVE-2021-0587 (High) detected in https://source.codeaurora.org/quic/la/platform/hardware/interfaces/LA.AU.0.1.0.r1-03400-gen3meta.0, https://source.codeaurora.org/quic/la/platform/hardware/interfaces/LA.AU.0.1.0.r1-03400-gen3meta.0 - ## CVE-2021-0587 - High Severity Vulnerability
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Libraries - <b>https://source.codeaurora.org/quic/la/platform/hardware/interfaces/LA.AU.0.1.0.r1-03400-gen3meta.0</b>, <b>https://source.codeaurora.org/quic/la/platform/hardware/interfaces/LA.AU.0.1.0.r1-03400-gen3meta.0</b></p></summary>
<p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png?' width=19 height=20> Vulnerability Details</summary>
<p>
In StreamOut::prepareForWriting of StreamOut.cpp, there is a possible out of bounds write due to a use after free. This could lead to local escalation of privilege with no additional execution privileges needed. User interaction is not needed for exploitation.Product: AndroidVersions: Android-8.1 Android-9 Android-10 Android-11Android ID: A-185259758
<p>Publish Date: 2021-07-14
<p>URL: <a href=https://www.mend.io/vulnerability-database/CVE-2021-0587>CVE-2021-0587</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/cvss3.png' width=19 height=20> CVSS 3 Score Details (<b>7.8</b>)</summary>
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Local
- Attack Complexity: Low
- Privileges Required: Low
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: High
- Integrity Impact: High
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/suggested_fix.png' width=19 height=20> Suggested Fix</summary>
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://source.android.com/security/bulletin/2021-07-01">https://source.android.com/security/bulletin/2021-07-01</a></p>
<p>Release Date: 2020-11-07</p>
<p>Fix Resolution: android-11.0.0_r39</p>
</p>
</details>
<p></p>
***
Step up your Open Source Security Game with Mend [here](https://www.whitesourcesoftware.com/full_solution_bolt_github) | non_priority | cve high detected in cve high severity vulnerability vulnerable libraries vulnerability details in streamout prepareforwriting of streamout cpp there is a possible out of bounds write due to a use after free this could lead to local escalation of privilege with no additional execution privileges needed user interaction is not needed for exploitation product androidversions android android android android id a publish date url a href cvss score details base score metrics exploitability metrics attack vector local attack complexity low privileges required low user interaction none scope unchanged impact metrics confidentiality impact high integrity impact high availability impact high for more information on scores click a href suggested fix type upgrade version origin a href release date fix resolution android step up your open source security game with mend | 0 |
347,092 | 31,141,051,679 | IssuesEvent | 2023-08-16 00:02:05 | CommunityToolkit/Tooling-Windows-Submodule | https://api.github.com/repos/CommunityToolkit/Tooling-Windows-Submodule | opened | `[UIThreadTestMethod]` doesn't forward `[Ignore]` for test to cause test to be ignored when running tests... | bug :bug: source generator :gear: testing 🏗 | ### Describe the bug
Found this out when trying to remove a test from our matrix: https://github.com/CommunityToolkit/Windows/pull/174
Apparently, it wasn't actually removed as the `[UIThreadTestMethod]` doesn't forward the `[Ignore]` attribute over to the generated test.
### Steps to reproduce
```text
1. Take a test with a `[UIThreadTestMethod]` attribute
2. Add `[Ignore]` to method
```
### Expected behavior
Expect generated test to also have `[Ignore]` on it.
### Screenshots
_No response_
### Code Platform
- [ ] UWP
- [ ] WinAppSDK / WinUI 3
- [ ] Web Assembly (WASM)
- [ ] Android
- [ ] iOS
- [ ] MacOS
- [ ] Linux / GTK
### Windows Build Number
- [ ] Windows 10 1809 (Build 17763)
- [ ] Windows 10 1903 (Build 18362)
- [ ] Windows 10 1909 (Build 18363)
- [ ] Windows 10 2004 (Build 19041)
- [ ] Windows 10 20H2 (Build 19042)
- [ ] Windows 10 21H1 (Build 19043)
- [ ] Windows 11 21H2 (Build 22000)
- [ ] Other (specify)
### Other Windows Build number
_No response_
### App minimum and target SDK version
- [ ] Windows 10, version 1809 (Build 17763)
- [ ] Windows 10, version 1903 (Build 18362)
- [ ] Windows 10, version 1909 (Build 18363)
- [ ] Windows 10, version 2004 (Build 19041)
- [ ] Other (specify)
### Other SDK version
_No response_
### Visual Studio Version
_No response_
### Visual Studio Build Number
_No response_
### Device form factor
_No response_
### Additional context
_No response_
### Help us help you
Yes, but only if others can assist. | 1.0 | `[UIThreadTestMethod]` doesn't forward `[Ignore]` for test to cause test to be ignored when running tests... - ### Describe the bug
Found this out when trying to remove a test from our matrix: https://github.com/CommunityToolkit/Windows/pull/174
Apparently, it wasn't actually removed as the `[UIThreadTestMethod]` doesn't forward the `[Ignore]` attribute over to the generated test.
### Steps to reproduce
```text
1. Take a test with a `[UIThreadTestMethod]` attribute
2. Add `[Ignore]` to method
```
### Expected behavior
Expect generated test to also have `[Ignore]` on it.
### Screenshots
_No response_
### Code Platform
- [ ] UWP
- [ ] WinAppSDK / WinUI 3
- [ ] Web Assembly (WASM)
- [ ] Android
- [ ] iOS
- [ ] MacOS
- [ ] Linux / GTK
### Windows Build Number
- [ ] Windows 10 1809 (Build 17763)
- [ ] Windows 10 1903 (Build 18362)
- [ ] Windows 10 1909 (Build 18363)
- [ ] Windows 10 2004 (Build 19041)
- [ ] Windows 10 20H2 (Build 19042)
- [ ] Windows 10 21H1 (Build 19043)
- [ ] Windows 11 21H2 (Build 22000)
- [ ] Other (specify)
### Other Windows Build number
_No response_
### App minimum and target SDK version
- [ ] Windows 10, version 1809 (Build 17763)
- [ ] Windows 10, version 1903 (Build 18362)
- [ ] Windows 10, version 1909 (Build 18363)
- [ ] Windows 10, version 2004 (Build 19041)
- [ ] Other (specify)
### Other SDK version
_No response_
### Visual Studio Version
_No response_
### Visual Studio Build Number
_No response_
### Device form factor
_No response_
### Additional context
_No response_
### Help us help you
Yes, but only if others can assist. | non_priority | doesn t forward for test to cause test to be ignored when running tests describe the bug found this out when trying to remove a test from our matrix apparently it wasn t actually removed as the doesn t forward the attribute over to the generated test steps to reproduce text take a test with a attribute add to method expected behavior expect generated test to also have on it screenshots no response code platform uwp winappsdk winui web assembly wasm android ios macos linux gtk windows build number windows build windows build windows build windows build windows build windows build windows build other specify other windows build number no response app minimum and target sdk version windows version build windows version build windows version build windows version build other specify other sdk version no response visual studio version no response visual studio build number no response device form factor no response additional context no response help us help you yes but only if others can assist | 0 |
85,546 | 10,449,731,322 | IssuesEvent | 2019-09-19 09:02:51 | magnusdahlgren/magnetizer | https://api.github.com/repos/magnusdahlgren/magnetizer | closed | More documentation updates | documentation | - [x] Filenames should be unique
- [x] Headings are downgraded on index page and should be styled as such
- [x] `website_base_url` (no trailing `/`) and `website_author` in config
- [x] Describe `magnetizer-license` css class
- [x] Describe `magnetizer-more` css class
- [x] Start posts with `<h1>`
- [x] Always include date
- [x] `<!-- MAGNETIZER_META -->` | 1.0 | More documentation updates - - [x] Filenames should be unique
- [x] Headings are downgraded on index page and should be styled as such
- [x] `website_base_url` (no trailing `/`) and `website_author` in config
- [x] Describe `magnetizer-license` css class
- [x] Describe `magnetizer-more` css class
- [x] Start posts with `<h1>`
- [x] Always include date
- [x] `<!-- MAGNETIZER_META -->` | non_priority | more documentation updates filenames should be unique headings are downgraded on index page and should be styled as such website base url no trailing and website author in config describe magnetizer license css class describe magnetizer more css class start posts with always include date | 0 |
7,611 | 25,267,967,086 | IssuesEvent | 2022-11-16 06:53:50 | treasuryguild/Catalyst-Training-and-Automation | https://api.github.com/repos/treasuryguild/Catalyst-Training-and-Automation | closed | 116.804168 ADA Outgoing | Catalyst-Training-and-Automation-Treasury-Wallet Fund8 Outgoing | {
"id" : "1668581395548",
"date": "Wed, 16 Nov 2022 06:49:55 GMT",
"fund": "Fund8",
"project": "Catalyst-Training-and-Automation",
"proposal": "Catalyst-Training-and-Automation-Treasury-Wallet",
"ideascale": "",
"budget": "Comm-Org-Tools",
"name": "uxd83r",
"exchangeRate": "0.341 USD per ADA",
"ada" : "116.80",
"walletBalance": ["3604.11 ADA"],
"txid": "a13db64598ad7135aab5cd231f4f223457877e7c13c5b12fb7d5d496ae6d8b99",
"description": "Payment for November Gitbook subscrition "
}
| 1.0 | 116.804168 ADA Outgoing - {
"id" : "1668581395548",
"date": "Wed, 16 Nov 2022 06:49:55 GMT",
"fund": "Fund8",
"project": "Catalyst-Training-and-Automation",
"proposal": "Catalyst-Training-and-Automation-Treasury-Wallet",
"ideascale": "",
"budget": "Comm-Org-Tools",
"name": "uxd83r",
"exchangeRate": "0.341 USD per ADA",
"ada" : "116.80",
"walletBalance": ["3604.11 ADA"],
"txid": "a13db64598ad7135aab5cd231f4f223457877e7c13c5b12fb7d5d496ae6d8b99",
"description": "Payment for November Gitbook subscrition "
}
| non_priority | ada outgoing id date wed nov gmt fund project catalyst training and automation proposal catalyst training and automation treasury wallet ideascale budget comm org tools name exchangerate usd per ada ada walletbalance txid description payment for november gitbook subscrition | 0 |
32,963 | 7,625,735,202 | IssuesEvent | 2018-05-03 22:45:21 | dotnet/coreclr | https://api.github.com/repos/dotnet/coreclr | closed | [RyuJIT][CQ] Loop trip count test is not efficient | area-CodeGen enhancement optimization tenet-performance | Per @hoyMS
For the following loop,
```
long iterations = Int64.Parse(args[0]);
for (long i = 0; i < iterations; i++)
{
}
```
RyuJit generates
```
G_M63536_IG03:
IN000d: 000041 mov rdx, rax
IN000e: 000044 inc rcx
G_M63536_IG04:
IN000f: 000047 cmp rcx, rsi
IN0010: 00004A setl r8b
IN0011: 00004E movzx r8, r8b
IN0012: 000052 test r8d, r8d
IN0013: 000055 jne SHORT G_M63536_IG03
IN0014: 000057 mov rax, rdx
```
Better would be:
```
00007ffb`45800545 488bce :
00007ffb`4580054d 48ffc3 inc rbx
00007ffb`45800550 483bdf cmp rbx,rdi
00007ffb`45800553 7cf0 jl enum!M.NoTime(Int64)+0x35 (00007ffb`45800545)
```
There’s probably a phase ordering issue with the folding away of the setcc/cmp branch.
| 1.0 | [RyuJIT][CQ] Loop trip count test is not efficient - Per @hoyMS
For the following loop,
```
long iterations = Int64.Parse(args[0]);
for (long i = 0; i < iterations; i++)
{
}
```
RyuJit generates
```
G_M63536_IG03:
IN000d: 000041 mov rdx, rax
IN000e: 000044 inc rcx
G_M63536_IG04:
IN000f: 000047 cmp rcx, rsi
IN0010: 00004A setl r8b
IN0011: 00004E movzx r8, r8b
IN0012: 000052 test r8d, r8d
IN0013: 000055 jne SHORT G_M63536_IG03
IN0014: 000057 mov rax, rdx
```
Better would be:
```
00007ffb`45800545 488bce :
00007ffb`4580054d 48ffc3 inc rbx
00007ffb`45800550 483bdf cmp rbx,rdi
00007ffb`45800553 7cf0 jl enum!M.NoTime(Int64)+0x35 (00007ffb`45800545)
```
There’s probably a phase ordering issue with the folding away of the setcc/cmp branch.
| non_priority | loop trip count test is not efficient per hoyms for the following loop long iterations parse args for long i i iterations i ryujit generates g mov rdx rax inc rcx g cmp rcx rsi setl movzx test jne short g mov rax rdx better would be inc rbx cmp rbx rdi jl enum m notime there’s probably a phase ordering issue with the folding away of the setcc cmp branch | 0 |
31,476 | 6,536,781,324 | IssuesEvent | 2017-08-31 19:32:17 | hazelcast/hazelcast | https://api.github.com/repos/hazelcast/hazelcast | closed | [cache] Cache eviction not fail fast. | Team: Core Type: Defect | When using the following hz xml only on retrieving the cache, I get a validation error. But the XML file could be validated when loaded.
```xml
<hazelcast xsi:schemaLocation="http://www.hazelcast.com/schema/config
http://www.hazelcast.com/schema/config/hazelcast-config-3.8.xsd"
xmlns="http://www.hazelcast.com/schema/config"
xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance">
<group>
<name>workers</name>
</group>
<lite-member enabled="true"/>
<network>
<port port-count="200" auto-increment="true">5701</port>
<join>
<multicast enabled="false"/>
<tcp-ip enabled="true">
<member>192.168.0.1:5701</member>
<member>192.168.0.2:5701</member>
</tcp-ip>
</join>
<ssl enabled="false"/>
</network>
<properties>
<property name="hazelcast.phone.home.enabled">false</property>
</properties>
<license-key>...</license-key>
<!--MANAGEMENT_CENTER_CONFIG-->
<native-memory allocator-type="POOLED" enabled="true">
<size unit="GIGABYTES" value="2" />
<metadata-space-percentage>20</metadata-space-percentage>
</native-memory>
<cache name="cache">
<eviction size="10000000" max-size-policy="ENTRY_COUNT" eviction-policy="LFU"/>
<backup-count>1</backup-count>
<async-backup-count>0</async-backup-count>
<in-memory-format>NATIVE</in-memory-format>
</cache>
</hazelcast>
```
```java
ERROR 2017-06-07 19:28:12,284 [Thread-5] com.hazelcast.simulator.worker.testcontainer.TestManager: --------------------------- global prepare of LongStringCacheTest FAILED ---------------------------
java.lang.IllegalArgumentException: Invalid max-size policy (ENTRY_COUNT) for com.hazelcast.cache.hidensity.impl.nativememory.HiDensityNativeMemoryCacheRecordStore! Only USED_NATIVE_MEMORY_SIZE, USED_NATIVE_MEMORY_PERCENTAGE, FREE_NATIVE_MEMORY_SIZE, FREE_NATIVE_MEMORY_PERCENTAGE are supported.
at com.hazelcast.cache.hidensity.impl.nativememory.HiDensityNativeMemoryCacheRecordStore.createCacheEvictionChecker(HiDensityNativeMemoryCacheRecordStore.java:121)
at com.hazelcast.cache.impl.AbstractCacheRecordStore.<init>(AbstractCacheRecordStore.java:150)
at com.hazelcast.cache.hidensity.impl.nativememory.HiDensityNativeMemoryCacheRecordStore.<init>(HiDensityNativeMemoryCacheRecordStore.java:59)
at com.hazelcast.cache.EnterpriseCacheService.newNativeRecordStore(EnterpriseCacheService.java:243)
at com.hazelcast.cache.EnterpriseCacheService.createNewRecordStore(EnterpriseCacheService.java:217)
at com.hazelcast.cache.impl.CachePartitionSegment.createNew(CachePartitionSegment.java:51)
at com.hazelcast.cache.impl.CachePartitionSegment.createNew(CachePartitionSegment.java:37)
at com.hazelcast.util.ConcurrencyUtil.getOrPutSynchronized(ConcurrencyUtil.java:73)
at com.hazelcast.cache.impl.CachePartitionSegment.getOrCreateRecordStore(CachePartitionSegment.java:67)
at com.hazelcast.cache.impl.AbstractCacheService.getOrCreateRecordStore(AbstractCacheService.java:278)
``` | 1.0 | [cache] Cache eviction not fail fast. - When using the following hz xml only on retrieving the cache, I get a validation error. But the XML file could be validated when loaded.
```xml
<hazelcast xsi:schemaLocation="http://www.hazelcast.com/schema/config
http://www.hazelcast.com/schema/config/hazelcast-config-3.8.xsd"
xmlns="http://www.hazelcast.com/schema/config"
xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance">
<group>
<name>workers</name>
</group>
<lite-member enabled="true"/>
<network>
<port port-count="200" auto-increment="true">5701</port>
<join>
<multicast enabled="false"/>
<tcp-ip enabled="true">
<member>192.168.0.1:5701</member>
<member>192.168.0.2:5701</member>
</tcp-ip>
</join>
<ssl enabled="false"/>
</network>
<properties>
<property name="hazelcast.phone.home.enabled">false</property>
</properties>
<license-key>...</license-key>
<!--MANAGEMENT_CENTER_CONFIG-->
<native-memory allocator-type="POOLED" enabled="true">
<size unit="GIGABYTES" value="2" />
<metadata-space-percentage>20</metadata-space-percentage>
</native-memory>
<cache name="cache">
<eviction size="10000000" max-size-policy="ENTRY_COUNT" eviction-policy="LFU"/>
<backup-count>1</backup-count>
<async-backup-count>0</async-backup-count>
<in-memory-format>NATIVE</in-memory-format>
</cache>
</hazelcast>
```
```java
ERROR 2017-06-07 19:28:12,284 [Thread-5] com.hazelcast.simulator.worker.testcontainer.TestManager: --------------------------- global prepare of LongStringCacheTest FAILED ---------------------------
java.lang.IllegalArgumentException: Invalid max-size policy (ENTRY_COUNT) for com.hazelcast.cache.hidensity.impl.nativememory.HiDensityNativeMemoryCacheRecordStore! Only USED_NATIVE_MEMORY_SIZE, USED_NATIVE_MEMORY_PERCENTAGE, FREE_NATIVE_MEMORY_SIZE, FREE_NATIVE_MEMORY_PERCENTAGE are supported.
at com.hazelcast.cache.hidensity.impl.nativememory.HiDensityNativeMemoryCacheRecordStore.createCacheEvictionChecker(HiDensityNativeMemoryCacheRecordStore.java:121)
at com.hazelcast.cache.impl.AbstractCacheRecordStore.<init>(AbstractCacheRecordStore.java:150)
at com.hazelcast.cache.hidensity.impl.nativememory.HiDensityNativeMemoryCacheRecordStore.<init>(HiDensityNativeMemoryCacheRecordStore.java:59)
at com.hazelcast.cache.EnterpriseCacheService.newNativeRecordStore(EnterpriseCacheService.java:243)
at com.hazelcast.cache.EnterpriseCacheService.createNewRecordStore(EnterpriseCacheService.java:217)
at com.hazelcast.cache.impl.CachePartitionSegment.createNew(CachePartitionSegment.java:51)
at com.hazelcast.cache.impl.CachePartitionSegment.createNew(CachePartitionSegment.java:37)
at com.hazelcast.util.ConcurrencyUtil.getOrPutSynchronized(ConcurrencyUtil.java:73)
at com.hazelcast.cache.impl.CachePartitionSegment.getOrCreateRecordStore(CachePartitionSegment.java:67)
at com.hazelcast.cache.impl.AbstractCacheService.getOrCreateRecordStore(AbstractCacheService.java:278)
``` | non_priority | cache eviction not fail fast when using the following hz xml only on retrieving the cache i get a validation error but the xml file could be validated when loaded xml hazelcast xsi schemalocation xmlns xmlns xsi workers false native java error com hazelcast simulator worker testcontainer testmanager global prepare of longstringcachetest failed java lang illegalargumentexception invalid max size policy entry count for com hazelcast cache hidensity impl nativememory hidensitynativememorycacherecordstore only used native memory size used native memory percentage free native memory size free native memory percentage are supported at com hazelcast cache hidensity impl nativememory hidensitynativememorycacherecordstore createcacheevictionchecker hidensitynativememorycacherecordstore java at com hazelcast cache impl abstractcacherecordstore abstractcacherecordstore java at com hazelcast cache hidensity impl nativememory hidensitynativememorycacherecordstore hidensitynativememorycacherecordstore java at com hazelcast cache enterprisecacheservice newnativerecordstore enterprisecacheservice java at com hazelcast cache enterprisecacheservice createnewrecordstore enterprisecacheservice java at com hazelcast cache impl cachepartitionsegment createnew cachepartitionsegment java at com hazelcast cache impl cachepartitionsegment createnew cachepartitionsegment java at com hazelcast util concurrencyutil getorputsynchronized concurrencyutil java at com hazelcast cache impl cachepartitionsegment getorcreaterecordstore cachepartitionsegment java at com hazelcast cache impl abstractcacheservice getorcreaterecordstore abstractcacheservice java | 0 |
42,685 | 11,045,175,813 | IssuesEvent | 2019-12-09 14:40:49 | rust-lang/rust | https://api.github.com/repos/rust-lang/rust | closed | Update CONTRIBUTING.md's build system docs | A-rustbuild C-enhancement | It seems likely that there are a number of tasks here, but the known one is that https://github.com/rust-lang/rust/pull/47460 needs to be added upon merge.
| 1.0 | Update CONTRIBUTING.md's build system docs - It seems likely that there are a number of tasks here, but the known one is that https://github.com/rust-lang/rust/pull/47460 needs to be added upon merge.
| non_priority | update contributing md s build system docs it seems likely that there are a number of tasks here but the known one is that needs to be added upon merge | 0 |
227,104 | 25,031,128,254 | IssuesEvent | 2022-11-04 12:29:02 | sast-automation-dev/vulnado-46 | https://api.github.com/repos/sast-automation-dev/vulnado-46 | opened | spring-boot-starter-web-2.1.2.RELEASE.jar: 68 vulnerabilities (highest severity is: 9.8) | security vulnerability | <details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Library - <b>spring-boot-starter-web-2.1.2.RELEASE.jar</b></p></summary>
<p></p>
<p>Path to dependency file: /pom.xml</p>
<p>Path to vulnerable library: /home/wss-scanner/.m2/repository/org/apache/tomcat/embed/tomcat-embed-core/9.0.14/tomcat-embed-core-9.0.14.jar</p>
<p>
<p>Found in HEAD commit: <a href="https://github.com/sast-automation-dev/vulnado-46/commit/bbbdc414743ce0d1eacca72de56770d0c21f8a4f">bbbdc414743ce0d1eacca72de56770d0c21f8a4f</a></p></details>
## Vulnerabilities
| CVE | Severity | <img src='https://whitesource-resources.whitesourcesoftware.com/cvss3.png' width=19 height=20> CVSS | Dependency | Type | Fixed in (spring-boot-starter-web version) | Remediation Available |
| ------------- | ------------- | ----- | ----- | ----- | ------------- | --- |
| [CVE-2019-14540](https://www.mend.io/vulnerability-database/CVE-2019-14540) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 9.8 | jackson-databind-2.9.8.jar | Transitive | 2.2.0.RELEASE | ✅ |
| [CVE-2019-17531](https://www.mend.io/vulnerability-database/CVE-2019-17531) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 9.8 | jackson-databind-2.9.8.jar | Transitive | 2.2.0.RELEASE | ✅ |
| [CVE-2016-1000027](https://www.mend.io/vulnerability-database/CVE-2016-1000027) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 9.8 | spring-web-5.1.4.RELEASE.jar | Transitive | 2.1.15.RELEASE | ✅ |
| [CVE-2019-16335](https://www.mend.io/vulnerability-database/CVE-2019-16335) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 9.8 | jackson-databind-2.9.8.jar | Transitive | 2.1.10.RELEASE | ✅ |
| [CVE-2019-17267](https://www.mend.io/vulnerability-database/CVE-2019-17267) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 9.8 | jackson-databind-2.9.8.jar | Transitive | 2.1.10.RELEASE | ✅ |
| [CVE-2020-8840](https://www.mend.io/vulnerability-database/CVE-2020-8840) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 9.8 | jackson-databind-2.9.8.jar | Transitive | 2.2.0.RELEASE | ✅ |
| [CVE-2019-16942](https://www.mend.io/vulnerability-database/CVE-2019-16942) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 9.8 | jackson-databind-2.9.8.jar | Transitive | 2.2.0.RELEASE | ✅ |
| [CVE-2019-16943](https://www.mend.io/vulnerability-database/CVE-2019-16943) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 9.8 | jackson-databind-2.9.8.jar | Transitive | 2.2.0.RELEASE | ✅ |
| [CVE-2019-14893](https://www.mend.io/vulnerability-database/CVE-2019-14893) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 9.8 | jackson-databind-2.9.8.jar | Transitive | 2.1.10.RELEASE | ✅ |
| [CVE-2019-14892](https://www.mend.io/vulnerability-database/CVE-2019-14892) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 9.8 | jackson-databind-2.9.8.jar | Transitive | 2.1.10.RELEASE | ✅ |
| [CVE-2020-9546](https://www.mend.io/vulnerability-database/CVE-2020-9546) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 9.8 | jackson-databind-2.9.8.jar | Transitive | 2.2.0.RELEASE | ✅ |
| [CVE-2019-14379](https://www.mend.io/vulnerability-database/CVE-2019-14379) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 9.8 | jackson-databind-2.9.8.jar | Transitive | 2.1.10.RELEASE | ✅ |
| [CVE-2020-9547](https://www.mend.io/vulnerability-database/CVE-2020-9547) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 9.8 | jackson-databind-2.9.8.jar | Transitive | 2.2.0.RELEASE | ✅ |
| [CVE-2020-9548](https://www.mend.io/vulnerability-database/CVE-2020-9548) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 9.8 | jackson-databind-2.9.8.jar | Transitive | 2.2.0.RELEASE | ✅ |
| [CVE-2019-20330](https://www.mend.io/vulnerability-database/CVE-2019-20330) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 9.8 | jackson-databind-2.9.8.jar | Transitive | 2.2.0.RELEASE | ✅ |
| [CVE-2020-10968](https://www.mend.io/vulnerability-database/CVE-2020-10968) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 8.8 | jackson-databind-2.9.8.jar | Transitive | 2.1.6.RELEASE | ✅ |
| [CVE-2020-10969](https://www.mend.io/vulnerability-database/CVE-2020-10969) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 8.8 | jackson-databind-2.9.8.jar | Transitive | 2.2.0.RELEASE | ✅ |
| [CVE-2020-11111](https://www.mend.io/vulnerability-database/CVE-2020-11111) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 8.8 | jackson-databind-2.9.8.jar | Transitive | 2.2.0.RELEASE | ✅ |
| [CVE-2020-11113](https://www.mend.io/vulnerability-database/CVE-2020-11113) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 8.8 | jackson-databind-2.9.8.jar | Transitive | 2.2.0.RELEASE | ✅ |
| [CVE-2020-11112](https://www.mend.io/vulnerability-database/CVE-2020-11112) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 8.8 | jackson-databind-2.9.8.jar | Transitive | 2.2.0.RELEASE | ✅ |
| [CVE-2020-10672](https://www.mend.io/vulnerability-database/CVE-2020-10672) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 8.8 | jackson-databind-2.9.8.jar | Transitive | 2.2.0.RELEASE | ✅ |
| [CVE-2020-10673](https://www.mend.io/vulnerability-database/CVE-2020-10673) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 8.8 | jackson-databind-2.9.8.jar | Transitive | 2.2.0.RELEASE | ✅ |
| [CVE-2019-0232](https://www.mend.io/vulnerability-database/CVE-2019-0232) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 8.1 | tomcat-embed-core-9.0.14.jar | Transitive | 2.1.5.RELEASE | ✅ |
| [CVE-2020-11619](https://www.mend.io/vulnerability-database/CVE-2020-11619) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 8.1 | jackson-databind-2.9.8.jar | Transitive | 2.2.0.RELEASE | ✅ |
| [CVE-2020-35728](https://www.mend.io/vulnerability-database/CVE-2020-35728) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 8.1 | jackson-databind-2.9.8.jar | Transitive | 2.2.0.RELEASE | ✅ |
| [CVE-2020-36189](https://www.mend.io/vulnerability-database/CVE-2020-36189) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 8.1 | jackson-databind-2.9.8.jar | Transitive | 2.2.0.RELEASE | ✅ |
| [CVE-2020-36188](https://www.mend.io/vulnerability-database/CVE-2020-36188) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 8.1 | jackson-databind-2.9.8.jar | Transitive | 2.2.0.RELEASE | ✅ |
| [CVE-2020-11620](https://www.mend.io/vulnerability-database/CVE-2020-11620) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 8.1 | jackson-databind-2.9.8.jar | Transitive | 2.2.0.RELEASE | ✅ |
| [CVE-2020-36181](https://www.mend.io/vulnerability-database/CVE-2020-36181) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 8.1 | jackson-databind-2.9.8.jar | Transitive | 2.2.0.RELEASE | ✅ |
| [CVE-2020-36180](https://www.mend.io/vulnerability-database/CVE-2020-36180) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 8.1 | jackson-databind-2.9.8.jar | Transitive | 2.2.0.RELEASE | ✅ |
| [CVE-2020-36183](https://www.mend.io/vulnerability-database/CVE-2020-36183) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 8.1 | jackson-databind-2.9.8.jar | Transitive | 2.2.0.RELEASE | ✅ |
| [CVE-2020-35490](https://www.mend.io/vulnerability-database/CVE-2020-35490) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 8.1 | jackson-databind-2.9.8.jar | Transitive | 2.2.0.RELEASE | ✅ |
| [CVE-2020-36182](https://www.mend.io/vulnerability-database/CVE-2020-36182) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 8.1 | jackson-databind-2.9.8.jar | Transitive | 2.2.0.RELEASE | ✅ |
| [CVE-2020-36185](https://www.mend.io/vulnerability-database/CVE-2020-36185) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 8.1 | jackson-databind-2.9.8.jar | Transitive | 2.2.0.RELEASE | ✅ |
| [CVE-2020-36184](https://www.mend.io/vulnerability-database/CVE-2020-36184) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 8.1 | jackson-databind-2.9.8.jar | Transitive | 2.2.0.RELEASE | ✅ |
| [CVE-2020-35491](https://www.mend.io/vulnerability-database/CVE-2020-35491) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 8.1 | jackson-databind-2.9.8.jar | Transitive | 2.2.0.RELEASE | ✅ |
| [CVE-2020-36187](https://www.mend.io/vulnerability-database/CVE-2020-36187) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 8.1 | jackson-databind-2.9.8.jar | Transitive | 2.2.0.RELEASE | ✅ |
| [CVE-2020-36186](https://www.mend.io/vulnerability-database/CVE-2020-36186) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 8.1 | jackson-databind-2.9.8.jar | Transitive | 2.2.0.RELEASE | ✅ |
| [CVE-2021-20190](https://www.mend.io/vulnerability-database/CVE-2021-20190) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 8.1 | jackson-databind-2.9.8.jar | Transitive | 2.2.0.RELEASE | ✅ |
| [CVE-2020-36179](https://www.mend.io/vulnerability-database/CVE-2020-36179) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 8.1 | jackson-databind-2.9.8.jar | Transitive | 2.2.0.RELEASE | ✅ |
| [CVE-2020-24616](https://www.mend.io/vulnerability-database/CVE-2020-24616) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 8.1 | jackson-databind-2.9.8.jar | Transitive | 2.2.0.RELEASE | ✅ |
| [CVE-2020-14060](https://www.mend.io/vulnerability-database/CVE-2020-14060) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 8.1 | jackson-databind-2.9.8.jar | Transitive | 2.2.0.RELEASE | ✅ |
| [CVE-2020-14061](https://www.mend.io/vulnerability-database/CVE-2020-14061) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 8.1 | jackson-databind-2.9.8.jar | Transitive | 2.2.0.RELEASE | ✅ |
| [CVE-2020-14062](https://www.mend.io/vulnerability-database/CVE-2020-14062) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 8.1 | jackson-databind-2.9.8.jar | Transitive | 2.2.0.RELEASE | ✅ |
| [CVE-2020-24750](https://www.mend.io/vulnerability-database/CVE-2020-24750) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 8.1 | jackson-databind-2.9.8.jar | Transitive | 2.2.0.RELEASE | ✅ |
| [CVE-2020-14195](https://www.mend.io/vulnerability-database/CVE-2020-14195) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 8.1 | jackson-databind-2.9.8.jar | Transitive | 2.2.0.RELEASE | ✅ |
| [CVE-2019-12086](https://www.mend.io/vulnerability-database/CVE-2019-12086) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 7.5 | jackson-databind-2.9.8.jar | Transitive | 2.1.6.RELEASE | ✅ |
| [CVE-2020-25649](https://www.mend.io/vulnerability-database/CVE-2020-25649) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 7.5 | jackson-databind-2.9.8.jar | Transitive | 2.2.0.RELEASE | ✅ |
| [CVE-2020-5398](https://www.mend.io/vulnerability-database/CVE-2020-5398) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 7.5 | spring-web-5.1.4.RELEASE.jar | Transitive | 2.1.12.RELEASE | ✅ |
| [CVE-2019-10072](https://www.mend.io/vulnerability-database/CVE-2019-10072) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 7.5 | tomcat-embed-core-9.0.14.jar | Transitive | 2.1.6.RELEASE | ✅ |
| [CVE-2019-14439](https://www.mend.io/vulnerability-database/CVE-2019-14439) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 7.5 | jackson-databind-2.9.8.jar | Transitive | 2.1.10.RELEASE | ✅ |
| [CVE-2021-25122](https://www.mend.io/vulnerability-database/CVE-2021-25122) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 7.5 | tomcat-embed-core-9.0.14.jar | Transitive | 2.1.7.RELEASE | ✅ |
| [CVE-2019-17563](https://www.mend.io/vulnerability-database/CVE-2019-17563) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 7.5 | tomcat-embed-core-9.0.14.jar | Transitive | 2.1.7.RELEASE | ✅ |
| [CVE-2020-11996](https://www.mend.io/vulnerability-database/CVE-2020-11996) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 7.5 | tomcat-embed-core-9.0.14.jar | Transitive | 2.1.7.RELEASE | ✅ |
| [CVE-2020-13934](https://www.mend.io/vulnerability-database/CVE-2020-13934) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 7.5 | tomcat-embed-core-9.0.14.jar | Transitive | 2.1.7.RELEASE | ✅ |
| [CVE-2020-13935](https://www.mend.io/vulnerability-database/CVE-2020-13935) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 7.5 | tomcat-embed-websocket-9.0.14.jar | Transitive | 2.1.13.RELEASE | ✅ |
| [CVE-2020-9484](https://www.mend.io/vulnerability-database/CVE-2020-9484) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 7.0 | tomcat-embed-core-9.0.14.jar | Transitive | 2.1.7.RELEASE | ✅ |
| [CVE-2021-25329](https://www.mend.io/vulnerability-database/CVE-2021-25329) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 7.0 | tomcat-embed-core-9.0.14.jar | Transitive | 2.1.7.RELEASE | ✅ |
| [CVE-2020-5421](https://www.mend.io/vulnerability-database/CVE-2020-5421) | <img src='https://whitesource-resources.whitesourcesoftware.com/medium_vul.png' width=19 height=20> Medium | 6.5 | spring-web-5.1.4.RELEASE.jar | Transitive | 2.1.17.RELEASE | ✅ |
| [CVE-2019-0221](https://www.mend.io/vulnerability-database/CVE-2019-0221) | <img src='https://whitesource-resources.whitesourcesoftware.com/medium_vul.png' width=19 height=20> Medium | 6.1 | tomcat-embed-core-9.0.14.jar | Transitive | 2.1.5.RELEASE | ✅ |
| [CVE-2019-10219](https://www.mend.io/vulnerability-database/CVE-2019-10219) | <img src='https://whitesource-resources.whitesourcesoftware.com/medium_vul.png' width=19 height=20> Medium | 6.1 | hibernate-validator-6.0.14.Final.jar | Transitive | 2.1.10.RELEASE | ✅ |
| [CVE-2019-12814](https://www.mend.io/vulnerability-database/CVE-2019-12814) | <img src='https://whitesource-resources.whitesourcesoftware.com/medium_vul.png' width=19 height=20> Medium | 5.9 | jackson-databind-2.9.8.jar | Transitive | 2.1.10.RELEASE | ✅ |
| [CVE-2019-12384](https://www.mend.io/vulnerability-database/CVE-2019-12384) | <img src='https://whitesource-resources.whitesourcesoftware.com/medium_vul.png' width=19 height=20> Medium | 5.9 | jackson-databind-2.9.8.jar | Transitive | 2.1.10.RELEASE | ✅ |
| [CVE-2021-24122](https://www.mend.io/vulnerability-database/CVE-2021-24122) | <img src='https://whitesource-resources.whitesourcesoftware.com/medium_vul.png' width=19 height=20> Medium | 5.9 | tomcat-embed-core-9.0.14.jar | Transitive | 2.1.7.RELEASE | ✅ |
| [CVE-2020-10693](https://www.mend.io/vulnerability-database/CVE-2020-10693) | <img src='https://whitesource-resources.whitesourcesoftware.com/medium_vul.png' width=19 height=20> Medium | 5.3 | hibernate-validator-6.0.14.Final.jar | Transitive | 2.1.15.RELEASE | ✅ |
| [CVE-2019-10202](https://www.mend.io/vulnerability-database/CVE-2019-10202) | <img src='https://whitesource-resources.whitesourcesoftware.com/medium_vul.png' width=19 height=20> Medium | 4.9 | jackson-databind-2.9.8.jar | Transitive | N/A* | ❌ |
| [CVE-2020-1935](https://www.mend.io/vulnerability-database/CVE-2020-1935) | <img src='https://whitesource-resources.whitesourcesoftware.com/medium_vul.png' width=19 height=20> Medium | 4.8 | tomcat-embed-core-9.0.14.jar | Transitive | 2.1.7.RELEASE | ✅ |
| [CVE-2020-13943](https://www.mend.io/vulnerability-database/CVE-2020-13943) | <img src='https://whitesource-resources.whitesourcesoftware.com/medium_vul.png' width=19 height=20> Medium | 4.3 | tomcat-embed-core-9.0.14.jar | Transitive | 2.1.7.RELEASE | ✅ |
<p>*For some transitive vulnerabilities, there is no version of direct dependency with a fix. Check the section "Details" below to see if there is a version of transitive dependency where vulnerability is fixed.</p>
## Details
> Partial details (19 vulnerabilities) are displayed below due to a content size limitation in GitHub. To view information on the remaining vulnerabilities, navigate to the Mend Application.<br>
<details>
<summary><img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> CVE-2019-14540</summary>
### Vulnerable Library - <b>jackson-databind-2.9.8.jar</b></p>
<p>General data-binding functionality for Jackson: works on core streaming API</p>
<p>Library home page: <a href="http://github.com/FasterXML/jackson">http://github.com/FasterXML/jackson</a></p>
<p>Path to dependency file: /pom.xml</p>
<p>Path to vulnerable library: /home/wss-scanner/.m2/repository/com/fasterxml/jackson/core/jackson-databind/2.9.8/jackson-databind-2.9.8.jar</p>
<p>
Dependency Hierarchy:
- spring-boot-starter-web-2.1.2.RELEASE.jar (Root Library)
- spring-boot-starter-json-2.1.2.RELEASE.jar
- :x: **jackson-databind-2.9.8.jar** (Vulnerable Library)
<p>Found in HEAD commit: <a href="https://github.com/sast-automation-dev/vulnado-46/commit/bbbdc414743ce0d1eacca72de56770d0c21f8a4f">bbbdc414743ce0d1eacca72de56770d0c21f8a4f</a></p>
<p>Found in base branch: <b>master</b></p>
</p>
<p></p>
### Vulnerability Details
<p>
A Polymorphic Typing issue was discovered in FasterXML jackson-databind before 2.9.10. It is related to com.zaxxer.hikari.HikariConfig.
<p>Publish Date: 2019-09-15
<p>URL: <a href=https://www.mend.io/vulnerability-database/CVE-2019-14540>CVE-2019-14540</a></p>
</p>
<p></p>
### CVSS 3 Score Details (<b>9.8</b>)
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: High
- Integrity Impact: High
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
<p></p>
### Suggested Fix
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-14540">https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-14540</a></p>
<p>Release Date: 2019-09-15</p>
<p>Fix Resolution (com.fasterxml.jackson.core:jackson-databind): 2.9.10.redhat-00005</p>
<p>Direct dependency fix Resolution (org.springframework.boot:spring-boot-starter-web): 2.2.0.RELEASE</p>
</p>
<p></p>
:rescue_worker_helmet: Automatic Remediation is available for this issue
</details><details>
<summary><img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> CVE-2019-17531</summary>
### Vulnerable Library - <b>jackson-databind-2.9.8.jar</b></p>
<p>General data-binding functionality for Jackson: works on core streaming API</p>
<p>Library home page: <a href="http://github.com/FasterXML/jackson">http://github.com/FasterXML/jackson</a></p>
<p>Path to dependency file: /pom.xml</p>
<p>Path to vulnerable library: /home/wss-scanner/.m2/repository/com/fasterxml/jackson/core/jackson-databind/2.9.8/jackson-databind-2.9.8.jar</p>
<p>
Dependency Hierarchy:
- spring-boot-starter-web-2.1.2.RELEASE.jar (Root Library)
- spring-boot-starter-json-2.1.2.RELEASE.jar
- :x: **jackson-databind-2.9.8.jar** (Vulnerable Library)
<p>Found in HEAD commit: <a href="https://github.com/sast-automation-dev/vulnado-46/commit/bbbdc414743ce0d1eacca72de56770d0c21f8a4f">bbbdc414743ce0d1eacca72de56770d0c21f8a4f</a></p>
<p>Found in base branch: <b>master</b></p>
</p>
<p></p>
### Vulnerability Details
<p>
A Polymorphic Typing issue was discovered in FasterXML jackson-databind 2.0.0 through 2.9.10. When Default Typing is enabled (either globally or for a specific property) for an externally exposed JSON endpoint and the service has the apache-log4j-extra (version 1.2.x) jar in the classpath, and an attacker can provide a JNDI service to access, it is possible to make the service execute a malicious payload.
<p>Publish Date: 2019-10-12
<p>URL: <a href=https://www.mend.io/vulnerability-database/CVE-2019-17531>CVE-2019-17531</a></p>
</p>
<p></p>
### CVSS 3 Score Details (<b>9.8</b>)
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: High
- Integrity Impact: High
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
<p></p>
### Suggested Fix
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-17531">https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-17531</a></p>
<p>Release Date: 2019-10-12</p>
<p>Fix Resolution (com.fasterxml.jackson.core:jackson-databind): 2.9.10.redhat-00002</p>
<p>Direct dependency fix Resolution (org.springframework.boot:spring-boot-starter-web): 2.2.0.RELEASE</p>
</p>
<p></p>
:rescue_worker_helmet: Automatic Remediation is available for this issue
</details><details>
<summary><img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> CVE-2016-1000027</summary>
### Vulnerable Library - <b>spring-web-5.1.4.RELEASE.jar</b></p>
<p>Spring Web</p>
<p>Library home page: <a href="https://github.com/spring-projects/spring-framework">https://github.com/spring-projects/spring-framework</a></p>
<p>Path to dependency file: /pom.xml</p>
<p>Path to vulnerable library: /home/wss-scanner/.m2/repository/org/springframework/spring-web/5.1.4.RELEASE/spring-web-5.1.4.RELEASE.jar</p>
<p>
Dependency Hierarchy:
- spring-boot-starter-web-2.1.2.RELEASE.jar (Root Library)
- :x: **spring-web-5.1.4.RELEASE.jar** (Vulnerable Library)
<p>Found in HEAD commit: <a href="https://github.com/sast-automation-dev/vulnado-46/commit/bbbdc414743ce0d1eacca72de56770d0c21f8a4f">bbbdc414743ce0d1eacca72de56770d0c21f8a4f</a></p>
<p>Found in base branch: <b>master</b></p>
</p>
<p></p>
### Vulnerability Details
<p>
Pivotal Spring Framework 4.1.4 suffers from a potential remote code execution (RCE) issue if used for Java deserialization of untrusted data. Depending on how the library is implemented within a product, this issue may or not occur, and authentication may be required.
<p>Publish Date: 2020-01-02
<p>URL: <a href=https://www.mend.io/vulnerability-database/CVE-2016-1000027>CVE-2016-1000027</a></p>
</p>
<p></p>
### CVSS 3 Score Details (<b>9.8</b>)
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: High
- Integrity Impact: High
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
<p></p>
### Suggested Fix
<p>
<p>Type: Upgrade version</p>
<p>Release Date: 2020-01-02</p>
<p>Fix Resolution (org.springframework:spring-web): 5.1.16.RELEASE</p>
<p>Direct dependency fix Resolution (org.springframework.boot:spring-boot-starter-web): 2.1.15.RELEASE</p>
</p>
<p></p>
:rescue_worker_helmet: Automatic Remediation is available for this issue
</details><details>
<summary><img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> CVE-2019-16335</summary>
### Vulnerable Library - <b>jackson-databind-2.9.8.jar</b></p>
<p>General data-binding functionality for Jackson: works on core streaming API</p>
<p>Library home page: <a href="http://github.com/FasterXML/jackson">http://github.com/FasterXML/jackson</a></p>
<p>Path to dependency file: /pom.xml</p>
<p>Path to vulnerable library: /home/wss-scanner/.m2/repository/com/fasterxml/jackson/core/jackson-databind/2.9.8/jackson-databind-2.9.8.jar</p>
<p>
Dependency Hierarchy:
- spring-boot-starter-web-2.1.2.RELEASE.jar (Root Library)
- spring-boot-starter-json-2.1.2.RELEASE.jar
- :x: **jackson-databind-2.9.8.jar** (Vulnerable Library)
<p>Found in HEAD commit: <a href="https://github.com/sast-automation-dev/vulnado-46/commit/bbbdc414743ce0d1eacca72de56770d0c21f8a4f">bbbdc414743ce0d1eacca72de56770d0c21f8a4f</a></p>
<p>Found in base branch: <b>master</b></p>
</p>
<p></p>
### Vulnerability Details
<p>
A Polymorphic Typing issue was discovered in FasterXML jackson-databind before 2.9.10. It is related to com.zaxxer.hikari.HikariDataSource. This is a different vulnerability than CVE-2019-14540.
<p>Publish Date: 2019-09-15
<p>URL: <a href=https://www.mend.io/vulnerability-database/CVE-2019-16335>CVE-2019-16335</a></p>
</p>
<p></p>
### CVSS 3 Score Details (<b>9.8</b>)
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: High
- Integrity Impact: High
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
<p></p>
### Suggested Fix
<p>
<p>Type: Upgrade version</p>
<p>Release Date: 2019-09-15</p>
<p>Fix Resolution (com.fasterxml.jackson.core:jackson-databind): 2.9.9.3-redhat-00001</p>
<p>Direct dependency fix Resolution (org.springframework.boot:spring-boot-starter-web): 2.1.10.RELEASE</p>
</p>
<p></p>
:rescue_worker_helmet: Automatic Remediation is available for this issue
</details><details>
<summary><img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> CVE-2019-17267</summary>
### Vulnerable Library - <b>jackson-databind-2.9.8.jar</b></p>
<p>General data-binding functionality for Jackson: works on core streaming API</p>
<p>Library home page: <a href="http://github.com/FasterXML/jackson">http://github.com/FasterXML/jackson</a></p>
<p>Path to dependency file: /pom.xml</p>
<p>Path to vulnerable library: /home/wss-scanner/.m2/repository/com/fasterxml/jackson/core/jackson-databind/2.9.8/jackson-databind-2.9.8.jar</p>
<p>
Dependency Hierarchy:
- spring-boot-starter-web-2.1.2.RELEASE.jar (Root Library)
- spring-boot-starter-json-2.1.2.RELEASE.jar
- :x: **jackson-databind-2.9.8.jar** (Vulnerable Library)
<p>Found in HEAD commit: <a href="https://github.com/sast-automation-dev/vulnado-46/commit/bbbdc414743ce0d1eacca72de56770d0c21f8a4f">bbbdc414743ce0d1eacca72de56770d0c21f8a4f</a></p>
<p>Found in base branch: <b>master</b></p>
</p>
<p></p>
### Vulnerability Details
<p>
A Polymorphic Typing issue was discovered in FasterXML jackson-databind before 2.9.10. It is related to net.sf.ehcache.hibernate.EhcacheJtaTransactionManagerLookup.
<p>Publish Date: 2019-10-07
<p>URL: <a href=https://www.mend.io/vulnerability-database/CVE-2019-17267>CVE-2019-17267</a></p>
</p>
<p></p>
### CVSS 3 Score Details (<b>9.8</b>)
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: High
- Integrity Impact: High
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
<p></p>
### Suggested Fix
<p>
<p>Type: Upgrade version</p>
<p>Release Date: 2019-10-07</p>
<p>Fix Resolution (com.fasterxml.jackson.core:jackson-databind): 2.9.9.3-redhat-00001</p>
<p>Direct dependency fix Resolution (org.springframework.boot:spring-boot-starter-web): 2.1.10.RELEASE</p>
</p>
<p></p>
:rescue_worker_helmet: Automatic Remediation is available for this issue
</details><details>
<summary><img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> CVE-2020-8840</summary>
### Vulnerable Library - <b>jackson-databind-2.9.8.jar</b></p>
<p>General data-binding functionality for Jackson: works on core streaming API</p>
<p>Library home page: <a href="http://github.com/FasterXML/jackson">http://github.com/FasterXML/jackson</a></p>
<p>Path to dependency file: /pom.xml</p>
<p>Path to vulnerable library: /home/wss-scanner/.m2/repository/com/fasterxml/jackson/core/jackson-databind/2.9.8/jackson-databind-2.9.8.jar</p>
<p>
Dependency Hierarchy:
- spring-boot-starter-web-2.1.2.RELEASE.jar (Root Library)
- spring-boot-starter-json-2.1.2.RELEASE.jar
- :x: **jackson-databind-2.9.8.jar** (Vulnerable Library)
<p>Found in HEAD commit: <a href="https://github.com/sast-automation-dev/vulnado-46/commit/bbbdc414743ce0d1eacca72de56770d0c21f8a4f">bbbdc414743ce0d1eacca72de56770d0c21f8a4f</a></p>
<p>Found in base branch: <b>master</b></p>
</p>
<p></p>
### Vulnerability Details
<p>
FasterXML jackson-databind 2.0.0 through 2.9.10.2 lacks certain xbean-reflect/JNDI blocking, as demonstrated by org.apache.xbean.propertyeditor.JndiConverter.
<p>Publish Date: 2020-02-10
<p>URL: <a href=https://www.mend.io/vulnerability-database/CVE-2020-8840>CVE-2020-8840</a></p>
</p>
<p></p>
### CVSS 3 Score Details (<b>9.8</b>)
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: High
- Integrity Impact: High
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
<p></p>
### Suggested Fix
<p>
<p>Type: Upgrade version</p>
<p>Release Date: 2020-02-10</p>
<p>Fix Resolution (com.fasterxml.jackson.core:jackson-databind): 2.9.10.redhat-00005</p>
<p>Direct dependency fix Resolution (org.springframework.boot:spring-boot-starter-web): 2.2.0.RELEASE</p>
</p>
<p></p>
:rescue_worker_helmet: Automatic Remediation is available for this issue
</details><details>
<summary><img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> CVE-2019-16942</summary>
### Vulnerable Library - <b>jackson-databind-2.9.8.jar</b></p>
<p>General data-binding functionality for Jackson: works on core streaming API</p>
<p>Library home page: <a href="http://github.com/FasterXML/jackson">http://github.com/FasterXML/jackson</a></p>
<p>Path to dependency file: /pom.xml</p>
<p>Path to vulnerable library: /home/wss-scanner/.m2/repository/com/fasterxml/jackson/core/jackson-databind/2.9.8/jackson-databind-2.9.8.jar</p>
<p>
Dependency Hierarchy:
- spring-boot-starter-web-2.1.2.RELEASE.jar (Root Library)
- spring-boot-starter-json-2.1.2.RELEASE.jar
- :x: **jackson-databind-2.9.8.jar** (Vulnerable Library)
<p>Found in HEAD commit: <a href="https://github.com/sast-automation-dev/vulnado-46/commit/bbbdc414743ce0d1eacca72de56770d0c21f8a4f">bbbdc414743ce0d1eacca72de56770d0c21f8a4f</a></p>
<p>Found in base branch: <b>master</b></p>
</p>
<p></p>
### Vulnerability Details
<p>
A Polymorphic Typing issue was discovered in FasterXML jackson-databind 2.0.0 through 2.9.10. When Default Typing is enabled (either globally or for a specific property) for an externally exposed JSON endpoint and the service has the commons-dbcp (1.4) jar in the classpath, and an attacker can find an RMI service endpoint to access, it is possible to make the service execute a malicious payload. This issue exists because of org.apache.commons.dbcp.datasources.SharedPoolDataSource and org.apache.commons.dbcp.datasources.PerUserPoolDataSource mishandling.
<p>Publish Date: 2019-10-01
<p>URL: <a href=https://www.mend.io/vulnerability-database/CVE-2019-16942>CVE-2019-16942</a></p>
</p>
<p></p>
### CVSS 3 Score Details (<b>9.8</b>)
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: High
- Integrity Impact: High
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
<p></p>
### Suggested Fix
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-16942">https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-16942</a></p>
<p>Release Date: 2019-10-01</p>
<p>Fix Resolution (com.fasterxml.jackson.core:jackson-databind): 2.9.10.redhat-00002</p>
<p>Direct dependency fix Resolution (org.springframework.boot:spring-boot-starter-web): 2.2.0.RELEASE</p>
</p>
<p></p>
:rescue_worker_helmet: Automatic Remediation is available for this issue
</details><details>
<summary><img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> CVE-2019-16943</summary>
### Vulnerable Library - <b>jackson-databind-2.9.8.jar</b></p>
<p>General data-binding functionality for Jackson: works on core streaming API</p>
<p>Library home page: <a href="http://github.com/FasterXML/jackson">http://github.com/FasterXML/jackson</a></p>
<p>Path to dependency file: /pom.xml</p>
<p>Path to vulnerable library: /home/wss-scanner/.m2/repository/com/fasterxml/jackson/core/jackson-databind/2.9.8/jackson-databind-2.9.8.jar</p>
<p>
Dependency Hierarchy:
- spring-boot-starter-web-2.1.2.RELEASE.jar (Root Library)
- spring-boot-starter-json-2.1.2.RELEASE.jar
- :x: **jackson-databind-2.9.8.jar** (Vulnerable Library)
<p>Found in HEAD commit: <a href="https://github.com/sast-automation-dev/vulnado-46/commit/bbbdc414743ce0d1eacca72de56770d0c21f8a4f">bbbdc414743ce0d1eacca72de56770d0c21f8a4f</a></p>
<p>Found in base branch: <b>master</b></p>
</p>
<p></p>
### Vulnerability Details
<p>
A Polymorphic Typing issue was discovered in FasterXML jackson-databind 2.0.0 through 2.9.10. When Default Typing is enabled (either globally or for a specific property) for an externally exposed JSON endpoint and the service has the p6spy (3.8.6) jar in the classpath, and an attacker can find an RMI service endpoint to access, it is possible to make the service execute a malicious payload. This issue exists because of com.p6spy.engine.spy.P6DataSource mishandling.
<p>Publish Date: 2019-10-01
<p>URL: <a href=https://www.mend.io/vulnerability-database/CVE-2019-16943>CVE-2019-16943</a></p>
</p>
<p></p>
### CVSS 3 Score Details (<b>9.8</b>)
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: High
- Integrity Impact: High
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
<p></p>
### Suggested Fix
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-16943">https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-16943</a></p>
<p>Release Date: 2019-10-01</p>
<p>Fix Resolution (com.fasterxml.jackson.core:jackson-databind): 2.9.10.redhat-00002</p>
<p>Direct dependency fix Resolution (org.springframework.boot:spring-boot-starter-web): 2.2.0.RELEASE</p>
</p>
<p></p>
:rescue_worker_helmet: Automatic Remediation is available for this issue
</details><details>
<summary><img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> CVE-2019-14893</summary>
### Vulnerable Library - <b>jackson-databind-2.9.8.jar</b></p>
<p>General data-binding functionality for Jackson: works on core streaming API</p>
<p>Library home page: <a href="http://github.com/FasterXML/jackson">http://github.com/FasterXML/jackson</a></p>
<p>Path to dependency file: /pom.xml</p>
<p>Path to vulnerable library: /home/wss-scanner/.m2/repository/com/fasterxml/jackson/core/jackson-databind/2.9.8/jackson-databind-2.9.8.jar</p>
<p>
Dependency Hierarchy:
- spring-boot-starter-web-2.1.2.RELEASE.jar (Root Library)
- spring-boot-starter-json-2.1.2.RELEASE.jar
- :x: **jackson-databind-2.9.8.jar** (Vulnerable Library)
<p>Found in HEAD commit: <a href="https://github.com/sast-automation-dev/vulnado-46/commit/bbbdc414743ce0d1eacca72de56770d0c21f8a4f">bbbdc414743ce0d1eacca72de56770d0c21f8a4f</a></p>
<p>Found in base branch: <b>master</b></p>
</p>
<p></p>
### Vulnerability Details
<p>
A flaw was discovered in FasterXML jackson-databind in all versions before 2.9.10 and 2.10.0, where it would permit polymorphic deserialization of malicious objects using the xalan JNDI gadget when used in conjunction with polymorphic type handling methods such as `enableDefaultTyping()` or when @JsonTypeInfo is using `Id.CLASS` or `Id.MINIMAL_CLASS` or in any other way which ObjectMapper.readValue might instantiate objects from unsafe sources. An attacker could use this flaw to execute arbitrary code.
<p>Publish Date: 2020-03-02
<p>URL: <a href=https://www.mend.io/vulnerability-database/CVE-2019-14893>CVE-2019-14893</a></p>
</p>
<p></p>
### CVSS 3 Score Details (<b>9.8</b>)
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: High
- Integrity Impact: High
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
<p></p>
### Suggested Fix
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-14893">https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-14893</a></p>
<p>Release Date: 2020-03-02</p>
<p>Fix Resolution (com.fasterxml.jackson.core:jackson-databind): 2.9.10</p>
<p>Direct dependency fix Resolution (org.springframework.boot:spring-boot-starter-web): 2.1.10.RELEASE</p>
</p>
<p></p>
:rescue_worker_helmet: Automatic Remediation is available for this issue
</details><details>
<summary><img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> CVE-2019-14892</summary>
### Vulnerable Library - <b>jackson-databind-2.9.8.jar</b></p>
<p>General data-binding functionality for Jackson: works on core streaming API</p>
<p>Library home page: <a href="http://github.com/FasterXML/jackson">http://github.com/FasterXML/jackson</a></p>
<p>Path to dependency file: /pom.xml</p>
<p>Path to vulnerable library: /home/wss-scanner/.m2/repository/com/fasterxml/jackson/core/jackson-databind/2.9.8/jackson-databind-2.9.8.jar</p>
<p>
Dependency Hierarchy:
- spring-boot-starter-web-2.1.2.RELEASE.jar (Root Library)
- spring-boot-starter-json-2.1.2.RELEASE.jar
- :x: **jackson-databind-2.9.8.jar** (Vulnerable Library)
<p>Found in HEAD commit: <a href="https://github.com/sast-automation-dev/vulnado-46/commit/bbbdc414743ce0d1eacca72de56770d0c21f8a4f">bbbdc414743ce0d1eacca72de56770d0c21f8a4f</a></p>
<p>Found in base branch: <b>master</b></p>
</p>
<p></p>
### Vulnerability Details
<p>
A flaw was discovered in jackson-databind in versions before 2.9.10, 2.8.11.5 and 2.6.7.3, where it would permit polymorphic deserialization of a malicious object using commons-configuration 1 and 2 JNDI classes. An attacker could use this flaw to execute arbitrary code.
<p>Publish Date: 2020-03-02
<p>URL: <a href=https://www.mend.io/vulnerability-database/CVE-2019-14892>CVE-2019-14892</a></p>
</p>
<p></p>
### CVSS 3 Score Details (<b>9.8</b>)
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: High
- Integrity Impact: High
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
<p></p>
### Suggested Fix
<p>
<p>Type: Upgrade version</p>
<p>Release Date: 2020-09-04</p>
<p>Fix Resolution (com.fasterxml.jackson.core:jackson-databind): 2.9.9.3-redhat-00001</p>
<p>Direct dependency fix Resolution (org.springframework.boot:spring-boot-starter-web): 2.1.10.RELEASE</p>
</p>
<p></p>
:rescue_worker_helmet: Automatic Remediation is available for this issue
</details><details>
<summary><img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> CVE-2020-9546</summary>
### Vulnerable Library - <b>jackson-databind-2.9.8.jar</b></p>
<p>General data-binding functionality for Jackson: works on core streaming API</p>
<p>Library home page: <a href="http://github.com/FasterXML/jackson">http://github.com/FasterXML/jackson</a></p>
<p>Path to dependency file: /pom.xml</p>
<p>Path to vulnerable library: /home/wss-scanner/.m2/repository/com/fasterxml/jackson/core/jackson-databind/2.9.8/jackson-databind-2.9.8.jar</p>
<p>
Dependency Hierarchy:
- spring-boot-starter-web-2.1.2.RELEASE.jar (Root Library)
- spring-boot-starter-json-2.1.2.RELEASE.jar
- :x: **jackson-databind-2.9.8.jar** (Vulnerable Library)
<p>Found in HEAD commit: <a href="https://github.com/sast-automation-dev/vulnado-46/commit/bbbdc414743ce0d1eacca72de56770d0c21f8a4f">bbbdc414743ce0d1eacca72de56770d0c21f8a4f</a></p>
<p>Found in base branch: <b>master</b></p>
</p>
<p></p>
### Vulnerability Details
<p>
FasterXML jackson-databind 2.x before 2.9.10.4 mishandles the interaction between serialization gadgets and typing, related to org.apache.hadoop.shaded.com.zaxxer.hikari.HikariConfig (aka shaded hikari-config).
<p>Publish Date: 2020-03-02
<p>URL: <a href=https://www.mend.io/vulnerability-database/CVE-2020-9546>CVE-2020-9546</a></p>
</p>
<p></p>
### CVSS 3 Score Details (<b>9.8</b>)
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: High
- Integrity Impact: High
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
<p></p>
### Suggested Fix
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2020-9546">https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2020-9546</a></p>
<p>Release Date: 2020-03-02</p>
<p>Fix Resolution (com.fasterxml.jackson.core:jackson-databind): 2.9.10.redhat-00005</p>
<p>Direct dependency fix Resolution (org.springframework.boot:spring-boot-starter-web): 2.2.0.RELEASE</p>
</p>
<p></p>
:rescue_worker_helmet: Automatic Remediation is available for this issue
</details><details>
<summary><img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> CVE-2019-14379</summary>
### Vulnerable Library - <b>jackson-databind-2.9.8.jar</b></p>
<p>General data-binding functionality for Jackson: works on core streaming API</p>
<p>Library home page: <a href="http://github.com/FasterXML/jackson">http://github.com/FasterXML/jackson</a></p>
<p>Path to dependency file: /pom.xml</p>
<p>Path to vulnerable library: /home/wss-scanner/.m2/repository/com/fasterxml/jackson/core/jackson-databind/2.9.8/jackson-databind-2.9.8.jar</p>
<p>
Dependency Hierarchy:
- spring-boot-starter-web-2.1.2.RELEASE.jar (Root Library)
- spring-boot-starter-json-2.1.2.RELEASE.jar
- :x: **jackson-databind-2.9.8.jar** (Vulnerable Library)
<p>Found in HEAD commit: <a href="https://github.com/sast-automation-dev/vulnado-46/commit/bbbdc414743ce0d1eacca72de56770d0c21f8a4f">bbbdc414743ce0d1eacca72de56770d0c21f8a4f</a></p>
<p>Found in base branch: <b>master</b></p>
</p>
<p></p>
### Vulnerability Details
<p>
SubTypeValidator.java in FasterXML jackson-databind before 2.9.9.2 mishandles default typing when ehcache is used (because of net.sf.ehcache.transaction.manager.DefaultTransactionManagerLookup), leading to remote code execution.
<p>Publish Date: 2019-07-29
<p>URL: <a href=https://www.mend.io/vulnerability-database/CVE-2019-14379>CVE-2019-14379</a></p>
</p>
<p></p>
### CVSS 3 Score Details (<b>9.8</b>)
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: High
- Integrity Impact: High
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
<p></p>
### Suggested Fix
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-14379">https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-14379</a></p>
<p>Release Date: 2019-07-29</p>
<p>Fix Resolution (com.fasterxml.jackson.core:jackson-databind): 2.9.9.2</p>
<p>Direct dependency fix Resolution (org.springframework.boot:spring-boot-starter-web): 2.1.10.RELEASE</p>
</p>
<p></p>
:rescue_worker_helmet: Automatic Remediation is available for this issue
</details><details>
<summary><img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> CVE-2020-9547</summary>
### Vulnerable Library - <b>jackson-databind-2.9.8.jar</b></p>
<p>General data-binding functionality for Jackson: works on core streaming API</p>
<p>Library home page: <a href="http://github.com/FasterXML/jackson">http://github.com/FasterXML/jackson</a></p>
<p>Path to dependency file: /pom.xml</p>
<p>Path to vulnerable library: /home/wss-scanner/.m2/repository/com/fasterxml/jackson/core/jackson-databind/2.9.8/jackson-databind-2.9.8.jar</p>
<p>
Dependency Hierarchy:
- spring-boot-starter-web-2.1.2.RELEASE.jar (Root Library)
- spring-boot-starter-json-2.1.2.RELEASE.jar
- :x: **jackson-databind-2.9.8.jar** (Vulnerable Library)
<p>Found in HEAD commit: <a href="https://github.com/sast-automation-dev/vulnado-46/commit/bbbdc414743ce0d1eacca72de56770d0c21f8a4f">bbbdc414743ce0d1eacca72de56770d0c21f8a4f</a></p>
<p>Found in base branch: <b>master</b></p>
</p>
<p></p>
### Vulnerability Details
<p>
FasterXML jackson-databind 2.x before 2.9.10.4 mishandles the interaction between serialization gadgets and typing, related to com.ibatis.sqlmap.engine.transaction.jta.JtaTransactionConfig (aka ibatis-sqlmap).
<p>Publish Date: 2020-03-02
<p>URL: <a href=https://www.mend.io/vulnerability-database/CVE-2020-9547>CVE-2020-9547</a></p>
</p>
<p></p>
### CVSS 3 Score Details (<b>9.8</b>)
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: High
- Integrity Impact: High
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
<p></p>
### Suggested Fix
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2020-9547">https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2020-9547</a></p>
<p>Release Date: 2020-03-02</p>
<p>Fix Resolution (com.fasterxml.jackson.core:jackson-databind): 2.9.10.redhat-00005</p>
<p>Direct dependency fix Resolution (org.springframework.boot:spring-boot-starter-web): 2.2.0.RELEASE</p>
</p>
<p></p>
:rescue_worker_helmet: Automatic Remediation is available for this issue
</details><details>
<summary><img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> CVE-2020-9548</summary>
### Vulnerable Library - <b>jackson-databind-2.9.8.jar</b></p>
<p>General data-binding functionality for Jackson: works on core streaming API</p>
<p>Library home page: <a href="http://github.com/FasterXML/jackson">http://github.com/FasterXML/jackson</a></p>
<p>Path to dependency file: /pom.xml</p>
<p>Path to vulnerable library: /home/wss-scanner/.m2/repository/com/fasterxml/jackson/core/jackson-databind/2.9.8/jackson-databind-2.9.8.jar</p>
<p>
Dependency Hierarchy:
- spring-boot-starter-web-2.1.2.RELEASE.jar (Root Library)
- spring-boot-starter-json-2.1.2.RELEASE.jar
- :x: **jackson-databind-2.9.8.jar** (Vulnerable Library)
<p>Found in HEAD commit: <a href="https://github.com/sast-automation-dev/vulnado-46/commit/bbbdc414743ce0d1eacca72de56770d0c21f8a4f">bbbdc414743ce0d1eacca72de56770d0c21f8a4f</a></p>
<p>Found in base branch: <b>master</b></p>
</p>
<p></p>
### Vulnerability Details
<p>
FasterXML jackson-databind 2.x before 2.9.10.4 mishandles the interaction between serialization gadgets and typing, related to br.com.anteros.dbcp.AnterosDBCPConfig (aka anteros-core).
<p>Publish Date: 2020-03-02
<p>URL: <a href=https://www.mend.io/vulnerability-database/CVE-2020-9548>CVE-2020-9548</a></p>
</p>
<p></p>
### CVSS 3 Score Details (<b>9.8</b>)
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: High
- Integrity Impact: High
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
<p></p>
### Suggested Fix
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2020-9548">https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2020-9548</a></p>
<p>Release Date: 2020-03-02</p>
<p>Fix Resolution (com.fasterxml.jackson.core:jackson-databind): 2.9.10.redhat-00005</p>
<p>Direct dependency fix Resolution (org.springframework.boot:spring-boot-starter-web): 2.2.0.RELEASE</p>
</p>
<p></p>
:rescue_worker_helmet: Automatic Remediation is available for this issue
</details><details>
<summary><img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> CVE-2019-20330</summary>
### Vulnerable Library - <b>jackson-databind-2.9.8.jar</b></p>
<p>General data-binding functionality for Jackson: works on core streaming API</p>
<p>Library home page: <a href="http://github.com/FasterXML/jackson">http://github.com/FasterXML/jackson</a></p>
<p>Path to dependency file: /pom.xml</p>
<p>Path to vulnerable library: /home/wss-scanner/.m2/repository/com/fasterxml/jackson/core/jackson-databind/2.9.8/jackson-databind-2.9.8.jar</p>
<p>
Dependency Hierarchy:
- spring-boot-starter-web-2.1.2.RELEASE.jar (Root Library)
- spring-boot-starter-json-2.1.2.RELEASE.jar
- :x: **jackson-databind-2.9.8.jar** (Vulnerable Library)
<p>Found in HEAD commit: <a href="https://github.com/sast-automation-dev/vulnado-46/commit/bbbdc414743ce0d1eacca72de56770d0c21f8a4f">bbbdc414743ce0d1eacca72de56770d0c21f8a4f</a></p>
<p>Found in base branch: <b>master</b></p>
</p>
<p></p>
### Vulnerability Details
<p>
FasterXML jackson-databind 2.x before 2.9.10.2 lacks certain net.sf.ehcache blocking.
<p>Publish Date: 2020-01-03
<p>URL: <a href=https://www.mend.io/vulnerability-database/CVE-2019-20330>CVE-2019-20330</a></p>
</p>
<p></p>
### CVSS 3 Score Details (<b>9.8</b>)
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: High
- Integrity Impact: High
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
<p></p>
### Suggested Fix
<p>
<p>Type: Upgrade version</p>
<p>Release Date: 2020-01-03</p>
<p>Fix Resolution (com.fasterxml.jackson.core:jackson-databind): 2.9.10.redhat-00005</p>
<p>Direct dependency fix Resolution (org.springframework.boot:spring-boot-starter-web): 2.2.0.RELEASE</p>
</p>
<p></p>
:rescue_worker_helmet: Automatic Remediation is available for this issue
</details><details>
<summary><img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> CVE-2020-10968</summary>
### Vulnerable Library - <b>jackson-databind-2.9.8.jar</b></p>
<p>General data-binding functionality for Jackson: works on core streaming API</p>
<p>Library home page: <a href="http://github.com/FasterXML/jackson">http://github.com/FasterXML/jackson</a></p>
<p>Path to dependency file: /pom.xml</p>
<p>Path to vulnerable library: /home/wss-scanner/.m2/repository/com/fasterxml/jackson/core/jackson-databind/2.9.8/jackson-databind-2.9.8.jar</p>
<p>
Dependency Hierarchy:
- spring-boot-starter-web-2.1.2.RELEASE.jar (Root Library)
- spring-boot-starter-json-2.1.2.RELEASE.jar
- :x: **jackson-databind-2.9.8.jar** (Vulnerable Library)
<p>Found in HEAD commit: <a href="https://github.com/sast-automation-dev/vulnado-46/commit/bbbdc414743ce0d1eacca72de56770d0c21f8a4f">bbbdc414743ce0d1eacca72de56770d0c21f8a4f</a></p>
<p>Found in base branch: <b>master</b></p>
</p>
<p></p>
### Vulnerability Details
<p>
FasterXML jackson-databind 2.x before 2.9.10.4 mishandles the interaction between serialization gadgets and typing, related to org.aoju.bus.proxy.provider.remoting.RmiProvider (aka bus-proxy).
<p>Publish Date: 2020-03-26
<p>URL: <a href=https://www.mend.io/vulnerability-database/CVE-2020-10968>CVE-2020-10968</a></p>
</p>
<p></p>
### CVSS 3 Score Details (<b>8.8</b>)
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: Required
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: High
- Integrity Impact: High
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
<p></p>
### Suggested Fix
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://nvd.nist.gov/vuln/detail/CVE-2020-10968">https://nvd.nist.gov/vuln/detail/CVE-2020-10968</a></p>
<p>Release Date: 2020-03-26</p>
<p>Fix Resolution (com.fasterxml.jackson.core:jackson-databind): 2.9.8.redhat-00002</p>
<p>Direct dependency fix Resolution (org.springframework.boot:spring-boot-starter-web): 2.1.6.RELEASE</p>
</p>
<p></p>
:rescue_worker_helmet: Automatic Remediation is available for this issue
</details><details>
<summary><img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> CVE-2020-10969</summary>
### Vulnerable Library - <b>jackson-databind-2.9.8.jar</b></p>
<p>General data-binding functionality for Jackson: works on core streaming API</p>
<p>Library home page: <a href="http://github.com/FasterXML/jackson">http://github.com/FasterXML/jackson</a></p>
<p>Path to dependency file: /pom.xml</p>
<p>Path to vulnerable library: /home/wss-scanner/.m2/repository/com/fasterxml/jackson/core/jackson-databind/2.9.8/jackson-databind-2.9.8.jar</p>
<p>
Dependency Hierarchy:
- spring-boot-starter-web-2.1.2.RELEASE.jar (Root Library)
- spring-boot-starter-json-2.1.2.RELEASE.jar
- :x: **jackson-databind-2.9.8.jar** (Vulnerable Library)
<p>Found in HEAD commit: <a href="https://github.com/sast-automation-dev/vulnado-46/commit/bbbdc414743ce0d1eacca72de56770d0c21f8a4f">bbbdc414743ce0d1eacca72de56770d0c21f8a4f</a></p>
<p>Found in base branch: <b>master</b></p>
</p>
<p></p>
### Vulnerability Details
<p>
FasterXML jackson-databind 2.x before 2.9.10.4 mishandles the interaction between serialization gadgets and typing, related to javax.swing.JEditorPane.
<p>Publish Date: 2020-03-26
<p>URL: <a href=https://www.mend.io/vulnerability-database/CVE-2020-10969>CVE-2020-10969</a></p>
</p>
<p></p>
### CVSS 3 Score Details (<b>8.8</b>)
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: Required
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: High
- Integrity Impact: High
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
<p></p>
### Suggested Fix
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2020-10969">https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2020-10969</a></p>
<p>Release Date: 2020-03-26</p>
<p>Fix Resolution (com.fasterxml.jackson.core:jackson-databind): 2.9.10.redhat-00005</p>
<p>Direct dependency fix Resolution (org.springframework.boot:spring-boot-starter-web): 2.2.0.RELEASE</p>
</p>
<p></p>
:rescue_worker_helmet: Automatic Remediation is available for this issue
</details><details>
<summary><img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> CVE-2020-11111</summary>
### Vulnerable Library - <b>jackson-databind-2.9.8.jar</b></p>
<p>General data-binding functionality for Jackson: works on core streaming API</p>
<p>Library home page: <a href="http://github.com/FasterXML/jackson">http://github.com/FasterXML/jackson</a></p>
<p>Path to dependency file: /pom.xml</p>
<p>Path to vulnerable library: /home/wss-scanner/.m2/repository/com/fasterxml/jackson/core/jackson-databind/2.9.8/jackson-databind-2.9.8.jar</p>
<p>
Dependency Hierarchy:
- spring-boot-starter-web-2.1.2.RELEASE.jar (Root Library)
- spring-boot-starter-json-2.1.2.RELEASE.jar
- :x: **jackson-databind-2.9.8.jar** (Vulnerable Library)
<p>Found in HEAD commit: <a href="https://github.com/sast-automation-dev/vulnado-46/commit/bbbdc414743ce0d1eacca72de56770d0c21f8a4f">bbbdc414743ce0d1eacca72de56770d0c21f8a4f</a></p>
<p>Found in base branch: <b>master</b></p>
</p>
<p></p>
### Vulnerability Details
<p>
FasterXML jackson-databind 2.x before 2.9.10.4 mishandles the interaction between serialization gadgets and typing, related to org.apache.activemq.* (aka activemq-jms, activemq-core, activemq-pool, and activemq-pool-jms).
<p>Publish Date: 2020-03-31
<p>URL: <a href=https://www.mend.io/vulnerability-database/CVE-2020-11111>CVE-2020-11111</a></p>
</p>
<p></p>
### CVSS 3 Score Details (<b>8.8</b>)
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: Required
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: High
- Integrity Impact: High
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
<p></p>
### Suggested Fix
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2020-11113">https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2020-11113</a></p>
<p>Release Date: 2020-03-31</p>
<p>Fix Resolution (com.fasterxml.jackson.core:jackson-databind): 2.9.10.redhat-00005</p>
<p>Direct dependency fix Resolution (org.springframework.boot:spring-boot-starter-web): 2.2.0.RELEASE</p>
</p>
<p></p>
:rescue_worker_helmet: Automatic Remediation is available for this issue
</details><details>
<summary><img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> CVE-2020-11113</summary>
### Vulnerable Library - <b>jackson-databind-2.9.8.jar</b></p>
<p>General data-binding functionality for Jackson: works on core streaming API</p>
<p>Library home page: <a href="http://github.com/FasterXML/jackson">http://github.com/FasterXML/jackson</a></p>
<p>Path to dependency file: /pom.xml</p>
<p>Path to vulnerable library: /home/wss-scanner/.m2/repository/com/fasterxml/jackson/core/jackson-databind/2.9.8/jackson-databind-2.9.8.jar</p>
<p>
Dependency Hierarchy:
- spring-boot-starter-web-2.1.2.RELEASE.jar (Root Library)
- spring-boot-starter-json-2.1.2.RELEASE.jar
- :x: **jackson-databind-2.9.8.jar** (Vulnerable Library)
<p>Found in HEAD commit: <a href="https://github.com/sast-automation-dev/vulnado-46/commit/bbbdc414743ce0d1eacca72de56770d0c21f8a4f">bbbdc414743ce0d1eacca72de56770d0c21f8a4f</a></p>
<p>Found in base branch: <b>master</b></p>
</p>
<p></p>
### Vulnerability Details
<p>
FasterXML jackson-databind 2.x before 2.9.10.4 mishandles the interaction between serialization gadgets and typing, related to org.apache.openjpa.ee.WASRegistryManagedRuntime (aka openjpa).
<p>Publish Date: 2020-03-31
<p>URL: <a href=https://www.mend.io/vulnerability-database/CVE-2020-11113>CVE-2020-11113</a></p>
</p>
<p></p>
### CVSS 3 Score Details (<b>8.8</b>)
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: Required
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: High
- Integrity Impact: High
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
<p></p>
### Suggested Fix
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2020-11113">https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2020-11113</a></p>
<p>Release Date: 2020-03-31</p>
<p>Fix Resolution (com.fasterxml.jackson.core:jackson-databind): 2.9.10.redhat-00005</p>
<p>Direct dependency fix Resolution (org.springframework.boot:spring-boot-starter-web): 2.2.0.RELEASE</p>
</p>
<p></p>
:rescue_worker_helmet: Automatic Remediation is available for this issue
</details>
***
<p>:rescue_worker_helmet: Automatic Remediation is available for this issue.</p> | True | spring-boot-starter-web-2.1.2.RELEASE.jar: 68 vulnerabilities (highest severity is: 9.8) - <details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Library - <b>spring-boot-starter-web-2.1.2.RELEASE.jar</b></p></summary>
<p></p>
<p>Path to dependency file: /pom.xml</p>
<p>Path to vulnerable library: /home/wss-scanner/.m2/repository/org/apache/tomcat/embed/tomcat-embed-core/9.0.14/tomcat-embed-core-9.0.14.jar</p>
<p>
<p>Found in HEAD commit: <a href="https://github.com/sast-automation-dev/vulnado-46/commit/bbbdc414743ce0d1eacca72de56770d0c21f8a4f">bbbdc414743ce0d1eacca72de56770d0c21f8a4f</a></p></details>
## Vulnerabilities
| CVE | Severity | <img src='https://whitesource-resources.whitesourcesoftware.com/cvss3.png' width=19 height=20> CVSS | Dependency | Type | Fixed in (spring-boot-starter-web version) | Remediation Available |
| ------------- | ------------- | ----- | ----- | ----- | ------------- | --- |
| [CVE-2019-14540](https://www.mend.io/vulnerability-database/CVE-2019-14540) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 9.8 | jackson-databind-2.9.8.jar | Transitive | 2.2.0.RELEASE | ✅ |
| [CVE-2019-17531](https://www.mend.io/vulnerability-database/CVE-2019-17531) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 9.8 | jackson-databind-2.9.8.jar | Transitive | 2.2.0.RELEASE | ✅ |
| [CVE-2016-1000027](https://www.mend.io/vulnerability-database/CVE-2016-1000027) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 9.8 | spring-web-5.1.4.RELEASE.jar | Transitive | 2.1.15.RELEASE | ✅ |
| [CVE-2019-16335](https://www.mend.io/vulnerability-database/CVE-2019-16335) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 9.8 | jackson-databind-2.9.8.jar | Transitive | 2.1.10.RELEASE | ✅ |
| [CVE-2019-17267](https://www.mend.io/vulnerability-database/CVE-2019-17267) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 9.8 | jackson-databind-2.9.8.jar | Transitive | 2.1.10.RELEASE | ✅ |
| [CVE-2020-8840](https://www.mend.io/vulnerability-database/CVE-2020-8840) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 9.8 | jackson-databind-2.9.8.jar | Transitive | 2.2.0.RELEASE | ✅ |
| [CVE-2019-16942](https://www.mend.io/vulnerability-database/CVE-2019-16942) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 9.8 | jackson-databind-2.9.8.jar | Transitive | 2.2.0.RELEASE | ✅ |
| [CVE-2019-16943](https://www.mend.io/vulnerability-database/CVE-2019-16943) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 9.8 | jackson-databind-2.9.8.jar | Transitive | 2.2.0.RELEASE | ✅ |
| [CVE-2019-14893](https://www.mend.io/vulnerability-database/CVE-2019-14893) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 9.8 | jackson-databind-2.9.8.jar | Transitive | 2.1.10.RELEASE | ✅ |
| [CVE-2019-14892](https://www.mend.io/vulnerability-database/CVE-2019-14892) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 9.8 | jackson-databind-2.9.8.jar | Transitive | 2.1.10.RELEASE | ✅ |
| [CVE-2020-9546](https://www.mend.io/vulnerability-database/CVE-2020-9546) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 9.8 | jackson-databind-2.9.8.jar | Transitive | 2.2.0.RELEASE | ✅ |
| [CVE-2019-14379](https://www.mend.io/vulnerability-database/CVE-2019-14379) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 9.8 | jackson-databind-2.9.8.jar | Transitive | 2.1.10.RELEASE | ✅ |
| [CVE-2020-9547](https://www.mend.io/vulnerability-database/CVE-2020-9547) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 9.8 | jackson-databind-2.9.8.jar | Transitive | 2.2.0.RELEASE | ✅ |
| [CVE-2020-9548](https://www.mend.io/vulnerability-database/CVE-2020-9548) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 9.8 | jackson-databind-2.9.8.jar | Transitive | 2.2.0.RELEASE | ✅ |
| [CVE-2019-20330](https://www.mend.io/vulnerability-database/CVE-2019-20330) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 9.8 | jackson-databind-2.9.8.jar | Transitive | 2.2.0.RELEASE | ✅ |
| [CVE-2020-10968](https://www.mend.io/vulnerability-database/CVE-2020-10968) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 8.8 | jackson-databind-2.9.8.jar | Transitive | 2.1.6.RELEASE | ✅ |
| [CVE-2020-10969](https://www.mend.io/vulnerability-database/CVE-2020-10969) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 8.8 | jackson-databind-2.9.8.jar | Transitive | 2.2.0.RELEASE | ✅ |
| [CVE-2020-11111](https://www.mend.io/vulnerability-database/CVE-2020-11111) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 8.8 | jackson-databind-2.9.8.jar | Transitive | 2.2.0.RELEASE | ✅ |
| [CVE-2020-11113](https://www.mend.io/vulnerability-database/CVE-2020-11113) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 8.8 | jackson-databind-2.9.8.jar | Transitive | 2.2.0.RELEASE | ✅ |
| [CVE-2020-11112](https://www.mend.io/vulnerability-database/CVE-2020-11112) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 8.8 | jackson-databind-2.9.8.jar | Transitive | 2.2.0.RELEASE | ✅ |
| [CVE-2020-10672](https://www.mend.io/vulnerability-database/CVE-2020-10672) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 8.8 | jackson-databind-2.9.8.jar | Transitive | 2.2.0.RELEASE | ✅ |
| [CVE-2020-10673](https://www.mend.io/vulnerability-database/CVE-2020-10673) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 8.8 | jackson-databind-2.9.8.jar | Transitive | 2.2.0.RELEASE | ✅ |
| [CVE-2019-0232](https://www.mend.io/vulnerability-database/CVE-2019-0232) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 8.1 | tomcat-embed-core-9.0.14.jar | Transitive | 2.1.5.RELEASE | ✅ |
| [CVE-2020-11619](https://www.mend.io/vulnerability-database/CVE-2020-11619) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 8.1 | jackson-databind-2.9.8.jar | Transitive | 2.2.0.RELEASE | ✅ |
| [CVE-2020-35728](https://www.mend.io/vulnerability-database/CVE-2020-35728) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 8.1 | jackson-databind-2.9.8.jar | Transitive | 2.2.0.RELEASE | ✅ |
| [CVE-2020-36189](https://www.mend.io/vulnerability-database/CVE-2020-36189) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 8.1 | jackson-databind-2.9.8.jar | Transitive | 2.2.0.RELEASE | ✅ |
| [CVE-2020-36188](https://www.mend.io/vulnerability-database/CVE-2020-36188) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 8.1 | jackson-databind-2.9.8.jar | Transitive | 2.2.0.RELEASE | ✅ |
| [CVE-2020-11620](https://www.mend.io/vulnerability-database/CVE-2020-11620) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 8.1 | jackson-databind-2.9.8.jar | Transitive | 2.2.0.RELEASE | ✅ |
| [CVE-2020-36181](https://www.mend.io/vulnerability-database/CVE-2020-36181) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 8.1 | jackson-databind-2.9.8.jar | Transitive | 2.2.0.RELEASE | ✅ |
| [CVE-2020-36180](https://www.mend.io/vulnerability-database/CVE-2020-36180) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 8.1 | jackson-databind-2.9.8.jar | Transitive | 2.2.0.RELEASE | ✅ |
| [CVE-2020-36183](https://www.mend.io/vulnerability-database/CVE-2020-36183) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 8.1 | jackson-databind-2.9.8.jar | Transitive | 2.2.0.RELEASE | ✅ |
| [CVE-2020-35490](https://www.mend.io/vulnerability-database/CVE-2020-35490) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 8.1 | jackson-databind-2.9.8.jar | Transitive | 2.2.0.RELEASE | ✅ |
| [CVE-2020-36182](https://www.mend.io/vulnerability-database/CVE-2020-36182) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 8.1 | jackson-databind-2.9.8.jar | Transitive | 2.2.0.RELEASE | ✅ |
| [CVE-2020-36185](https://www.mend.io/vulnerability-database/CVE-2020-36185) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 8.1 | jackson-databind-2.9.8.jar | Transitive | 2.2.0.RELEASE | ✅ |
| [CVE-2020-36184](https://www.mend.io/vulnerability-database/CVE-2020-36184) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 8.1 | jackson-databind-2.9.8.jar | Transitive | 2.2.0.RELEASE | ✅ |
| [CVE-2020-35491](https://www.mend.io/vulnerability-database/CVE-2020-35491) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 8.1 | jackson-databind-2.9.8.jar | Transitive | 2.2.0.RELEASE | ✅ |
| [CVE-2020-36187](https://www.mend.io/vulnerability-database/CVE-2020-36187) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 8.1 | jackson-databind-2.9.8.jar | Transitive | 2.2.0.RELEASE | ✅ |
| [CVE-2020-36186](https://www.mend.io/vulnerability-database/CVE-2020-36186) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 8.1 | jackson-databind-2.9.8.jar | Transitive | 2.2.0.RELEASE | ✅ |
| [CVE-2021-20190](https://www.mend.io/vulnerability-database/CVE-2021-20190) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 8.1 | jackson-databind-2.9.8.jar | Transitive | 2.2.0.RELEASE | ✅ |
| [CVE-2020-36179](https://www.mend.io/vulnerability-database/CVE-2020-36179) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 8.1 | jackson-databind-2.9.8.jar | Transitive | 2.2.0.RELEASE | ✅ |
| [CVE-2020-24616](https://www.mend.io/vulnerability-database/CVE-2020-24616) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 8.1 | jackson-databind-2.9.8.jar | Transitive | 2.2.0.RELEASE | ✅ |
| [CVE-2020-14060](https://www.mend.io/vulnerability-database/CVE-2020-14060) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 8.1 | jackson-databind-2.9.8.jar | Transitive | 2.2.0.RELEASE | ✅ |
| [CVE-2020-14061](https://www.mend.io/vulnerability-database/CVE-2020-14061) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 8.1 | jackson-databind-2.9.8.jar | Transitive | 2.2.0.RELEASE | ✅ |
| [CVE-2020-14062](https://www.mend.io/vulnerability-database/CVE-2020-14062) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 8.1 | jackson-databind-2.9.8.jar | Transitive | 2.2.0.RELEASE | ✅ |
| [CVE-2020-24750](https://www.mend.io/vulnerability-database/CVE-2020-24750) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 8.1 | jackson-databind-2.9.8.jar | Transitive | 2.2.0.RELEASE | ✅ |
| [CVE-2020-14195](https://www.mend.io/vulnerability-database/CVE-2020-14195) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 8.1 | jackson-databind-2.9.8.jar | Transitive | 2.2.0.RELEASE | ✅ |
| [CVE-2019-12086](https://www.mend.io/vulnerability-database/CVE-2019-12086) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 7.5 | jackson-databind-2.9.8.jar | Transitive | 2.1.6.RELEASE | ✅ |
| [CVE-2020-25649](https://www.mend.io/vulnerability-database/CVE-2020-25649) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 7.5 | jackson-databind-2.9.8.jar | Transitive | 2.2.0.RELEASE | ✅ |
| [CVE-2020-5398](https://www.mend.io/vulnerability-database/CVE-2020-5398) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 7.5 | spring-web-5.1.4.RELEASE.jar | Transitive | 2.1.12.RELEASE | ✅ |
| [CVE-2019-10072](https://www.mend.io/vulnerability-database/CVE-2019-10072) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 7.5 | tomcat-embed-core-9.0.14.jar | Transitive | 2.1.6.RELEASE | ✅ |
| [CVE-2019-14439](https://www.mend.io/vulnerability-database/CVE-2019-14439) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 7.5 | jackson-databind-2.9.8.jar | Transitive | 2.1.10.RELEASE | ✅ |
| [CVE-2021-25122](https://www.mend.io/vulnerability-database/CVE-2021-25122) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 7.5 | tomcat-embed-core-9.0.14.jar | Transitive | 2.1.7.RELEASE | ✅ |
| [CVE-2019-17563](https://www.mend.io/vulnerability-database/CVE-2019-17563) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 7.5 | tomcat-embed-core-9.0.14.jar | Transitive | 2.1.7.RELEASE | ✅ |
| [CVE-2020-11996](https://www.mend.io/vulnerability-database/CVE-2020-11996) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 7.5 | tomcat-embed-core-9.0.14.jar | Transitive | 2.1.7.RELEASE | ✅ |
| [CVE-2020-13934](https://www.mend.io/vulnerability-database/CVE-2020-13934) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 7.5 | tomcat-embed-core-9.0.14.jar | Transitive | 2.1.7.RELEASE | ✅ |
| [CVE-2020-13935](https://www.mend.io/vulnerability-database/CVE-2020-13935) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 7.5 | tomcat-embed-websocket-9.0.14.jar | Transitive | 2.1.13.RELEASE | ✅ |
| [CVE-2020-9484](https://www.mend.io/vulnerability-database/CVE-2020-9484) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 7.0 | tomcat-embed-core-9.0.14.jar | Transitive | 2.1.7.RELEASE | ✅ |
| [CVE-2021-25329](https://www.mend.io/vulnerability-database/CVE-2021-25329) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 7.0 | tomcat-embed-core-9.0.14.jar | Transitive | 2.1.7.RELEASE | ✅ |
| [CVE-2020-5421](https://www.mend.io/vulnerability-database/CVE-2020-5421) | <img src='https://whitesource-resources.whitesourcesoftware.com/medium_vul.png' width=19 height=20> Medium | 6.5 | spring-web-5.1.4.RELEASE.jar | Transitive | 2.1.17.RELEASE | ✅ |
| [CVE-2019-0221](https://www.mend.io/vulnerability-database/CVE-2019-0221) | <img src='https://whitesource-resources.whitesourcesoftware.com/medium_vul.png' width=19 height=20> Medium | 6.1 | tomcat-embed-core-9.0.14.jar | Transitive | 2.1.5.RELEASE | ✅ |
| [CVE-2019-10219](https://www.mend.io/vulnerability-database/CVE-2019-10219) | <img src='https://whitesource-resources.whitesourcesoftware.com/medium_vul.png' width=19 height=20> Medium | 6.1 | hibernate-validator-6.0.14.Final.jar | Transitive | 2.1.10.RELEASE | ✅ |
| [CVE-2019-12814](https://www.mend.io/vulnerability-database/CVE-2019-12814) | <img src='https://whitesource-resources.whitesourcesoftware.com/medium_vul.png' width=19 height=20> Medium | 5.9 | jackson-databind-2.9.8.jar | Transitive | 2.1.10.RELEASE | ✅ |
| [CVE-2019-12384](https://www.mend.io/vulnerability-database/CVE-2019-12384) | <img src='https://whitesource-resources.whitesourcesoftware.com/medium_vul.png' width=19 height=20> Medium | 5.9 | jackson-databind-2.9.8.jar | Transitive | 2.1.10.RELEASE | ✅ |
| [CVE-2021-24122](https://www.mend.io/vulnerability-database/CVE-2021-24122) | <img src='https://whitesource-resources.whitesourcesoftware.com/medium_vul.png' width=19 height=20> Medium | 5.9 | tomcat-embed-core-9.0.14.jar | Transitive | 2.1.7.RELEASE | ✅ |
| [CVE-2020-10693](https://www.mend.io/vulnerability-database/CVE-2020-10693) | <img src='https://whitesource-resources.whitesourcesoftware.com/medium_vul.png' width=19 height=20> Medium | 5.3 | hibernate-validator-6.0.14.Final.jar | Transitive | 2.1.15.RELEASE | ✅ |
| [CVE-2019-10202](https://www.mend.io/vulnerability-database/CVE-2019-10202) | <img src='https://whitesource-resources.whitesourcesoftware.com/medium_vul.png' width=19 height=20> Medium | 4.9 | jackson-databind-2.9.8.jar | Transitive | N/A* | ❌ |
| [CVE-2020-1935](https://www.mend.io/vulnerability-database/CVE-2020-1935) | <img src='https://whitesource-resources.whitesourcesoftware.com/medium_vul.png' width=19 height=20> Medium | 4.8 | tomcat-embed-core-9.0.14.jar | Transitive | 2.1.7.RELEASE | ✅ |
| [CVE-2020-13943](https://www.mend.io/vulnerability-database/CVE-2020-13943) | <img src='https://whitesource-resources.whitesourcesoftware.com/medium_vul.png' width=19 height=20> Medium | 4.3 | tomcat-embed-core-9.0.14.jar | Transitive | 2.1.7.RELEASE | ✅ |
<p>*For some transitive vulnerabilities, there is no version of direct dependency with a fix. Check the section "Details" below to see if there is a version of transitive dependency where vulnerability is fixed.</p>
## Details
> Partial details (19 vulnerabilities) are displayed below due to a content size limitation in GitHub. To view information on the remaining vulnerabilities, navigate to the Mend Application.<br>
<details>
<summary><img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> CVE-2019-14540</summary>
### Vulnerable Library - <b>jackson-databind-2.9.8.jar</b></p>
<p>General data-binding functionality for Jackson: works on core streaming API</p>
<p>Library home page: <a href="http://github.com/FasterXML/jackson">http://github.com/FasterXML/jackson</a></p>
<p>Path to dependency file: /pom.xml</p>
<p>Path to vulnerable library: /home/wss-scanner/.m2/repository/com/fasterxml/jackson/core/jackson-databind/2.9.8/jackson-databind-2.9.8.jar</p>
<p>
Dependency Hierarchy:
- spring-boot-starter-web-2.1.2.RELEASE.jar (Root Library)
- spring-boot-starter-json-2.1.2.RELEASE.jar
- :x: **jackson-databind-2.9.8.jar** (Vulnerable Library)
<p>Found in HEAD commit: <a href="https://github.com/sast-automation-dev/vulnado-46/commit/bbbdc414743ce0d1eacca72de56770d0c21f8a4f">bbbdc414743ce0d1eacca72de56770d0c21f8a4f</a></p>
<p>Found in base branch: <b>master</b></p>
</p>
<p></p>
### Vulnerability Details
<p>
A Polymorphic Typing issue was discovered in FasterXML jackson-databind before 2.9.10. It is related to com.zaxxer.hikari.HikariConfig.
<p>Publish Date: 2019-09-15
<p>URL: <a href=https://www.mend.io/vulnerability-database/CVE-2019-14540>CVE-2019-14540</a></p>
</p>
<p></p>
### CVSS 3 Score Details (<b>9.8</b>)
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: High
- Integrity Impact: High
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
<p></p>
### Suggested Fix
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-14540">https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-14540</a></p>
<p>Release Date: 2019-09-15</p>
<p>Fix Resolution (com.fasterxml.jackson.core:jackson-databind): 2.9.10.redhat-00005</p>
<p>Direct dependency fix Resolution (org.springframework.boot:spring-boot-starter-web): 2.2.0.RELEASE</p>
</p>
<p></p>
:rescue_worker_helmet: Automatic Remediation is available for this issue
</details><details>
<summary><img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> CVE-2019-17531</summary>
### Vulnerable Library - <b>jackson-databind-2.9.8.jar</b></p>
<p>General data-binding functionality for Jackson: works on core streaming API</p>
<p>Library home page: <a href="http://github.com/FasterXML/jackson">http://github.com/FasterXML/jackson</a></p>
<p>Path to dependency file: /pom.xml</p>
<p>Path to vulnerable library: /home/wss-scanner/.m2/repository/com/fasterxml/jackson/core/jackson-databind/2.9.8/jackson-databind-2.9.8.jar</p>
<p>
Dependency Hierarchy:
- spring-boot-starter-web-2.1.2.RELEASE.jar (Root Library)
- spring-boot-starter-json-2.1.2.RELEASE.jar
- :x: **jackson-databind-2.9.8.jar** (Vulnerable Library)
<p>Found in HEAD commit: <a href="https://github.com/sast-automation-dev/vulnado-46/commit/bbbdc414743ce0d1eacca72de56770d0c21f8a4f">bbbdc414743ce0d1eacca72de56770d0c21f8a4f</a></p>
<p>Found in base branch: <b>master</b></p>
</p>
<p></p>
### Vulnerability Details
<p>
A Polymorphic Typing issue was discovered in FasterXML jackson-databind 2.0.0 through 2.9.10. When Default Typing is enabled (either globally or for a specific property) for an externally exposed JSON endpoint and the service has the apache-log4j-extra (version 1.2.x) jar in the classpath, and an attacker can provide a JNDI service to access, it is possible to make the service execute a malicious payload.
<p>Publish Date: 2019-10-12
<p>URL: <a href=https://www.mend.io/vulnerability-database/CVE-2019-17531>CVE-2019-17531</a></p>
</p>
<p></p>
### CVSS 3 Score Details (<b>9.8</b>)
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: High
- Integrity Impact: High
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
<p></p>
### Suggested Fix
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-17531">https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-17531</a></p>
<p>Release Date: 2019-10-12</p>
<p>Fix Resolution (com.fasterxml.jackson.core:jackson-databind): 2.9.10.redhat-00002</p>
<p>Direct dependency fix Resolution (org.springframework.boot:spring-boot-starter-web): 2.2.0.RELEASE</p>
</p>
<p></p>
:rescue_worker_helmet: Automatic Remediation is available for this issue
</details><details>
<summary><img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> CVE-2016-1000027</summary>
### Vulnerable Library - <b>spring-web-5.1.4.RELEASE.jar</b></p>
<p>Spring Web</p>
<p>Library home page: <a href="https://github.com/spring-projects/spring-framework">https://github.com/spring-projects/spring-framework</a></p>
<p>Path to dependency file: /pom.xml</p>
<p>Path to vulnerable library: /home/wss-scanner/.m2/repository/org/springframework/spring-web/5.1.4.RELEASE/spring-web-5.1.4.RELEASE.jar</p>
<p>
Dependency Hierarchy:
- spring-boot-starter-web-2.1.2.RELEASE.jar (Root Library)
- :x: **spring-web-5.1.4.RELEASE.jar** (Vulnerable Library)
<p>Found in HEAD commit: <a href="https://github.com/sast-automation-dev/vulnado-46/commit/bbbdc414743ce0d1eacca72de56770d0c21f8a4f">bbbdc414743ce0d1eacca72de56770d0c21f8a4f</a></p>
<p>Found in base branch: <b>master</b></p>
</p>
<p></p>
### Vulnerability Details
<p>
Pivotal Spring Framework 4.1.4 suffers from a potential remote code execution (RCE) issue if used for Java deserialization of untrusted data. Depending on how the library is implemented within a product, this issue may or not occur, and authentication may be required.
<p>Publish Date: 2020-01-02
<p>URL: <a href=https://www.mend.io/vulnerability-database/CVE-2016-1000027>CVE-2016-1000027</a></p>
</p>
<p></p>
### CVSS 3 Score Details (<b>9.8</b>)
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: High
- Integrity Impact: High
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
<p></p>
### Suggested Fix
<p>
<p>Type: Upgrade version</p>
<p>Release Date: 2020-01-02</p>
<p>Fix Resolution (org.springframework:spring-web): 5.1.16.RELEASE</p>
<p>Direct dependency fix Resolution (org.springframework.boot:spring-boot-starter-web): 2.1.15.RELEASE</p>
</p>
<p></p>
:rescue_worker_helmet: Automatic Remediation is available for this issue
</details><details>
<summary><img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> CVE-2019-16335</summary>
### Vulnerable Library - <b>jackson-databind-2.9.8.jar</b></p>
<p>General data-binding functionality for Jackson: works on core streaming API</p>
<p>Library home page: <a href="http://github.com/FasterXML/jackson">http://github.com/FasterXML/jackson</a></p>
<p>Path to dependency file: /pom.xml</p>
<p>Path to vulnerable library: /home/wss-scanner/.m2/repository/com/fasterxml/jackson/core/jackson-databind/2.9.8/jackson-databind-2.9.8.jar</p>
<p>
Dependency Hierarchy:
- spring-boot-starter-web-2.1.2.RELEASE.jar (Root Library)
- spring-boot-starter-json-2.1.2.RELEASE.jar
- :x: **jackson-databind-2.9.8.jar** (Vulnerable Library)
<p>Found in HEAD commit: <a href="https://github.com/sast-automation-dev/vulnado-46/commit/bbbdc414743ce0d1eacca72de56770d0c21f8a4f">bbbdc414743ce0d1eacca72de56770d0c21f8a4f</a></p>
<p>Found in base branch: <b>master</b></p>
</p>
<p></p>
### Vulnerability Details
<p>
A Polymorphic Typing issue was discovered in FasterXML jackson-databind before 2.9.10. It is related to com.zaxxer.hikari.HikariDataSource. This is a different vulnerability than CVE-2019-14540.
<p>Publish Date: 2019-09-15
<p>URL: <a href=https://www.mend.io/vulnerability-database/CVE-2019-16335>CVE-2019-16335</a></p>
</p>
<p></p>
### CVSS 3 Score Details (<b>9.8</b>)
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: High
- Integrity Impact: High
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
<p></p>
### Suggested Fix
<p>
<p>Type: Upgrade version</p>
<p>Release Date: 2019-09-15</p>
<p>Fix Resolution (com.fasterxml.jackson.core:jackson-databind): 2.9.9.3-redhat-00001</p>
<p>Direct dependency fix Resolution (org.springframework.boot:spring-boot-starter-web): 2.1.10.RELEASE</p>
</p>
<p></p>
:rescue_worker_helmet: Automatic Remediation is available for this issue
</details><details>
<summary><img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> CVE-2019-17267</summary>
### Vulnerable Library - <b>jackson-databind-2.9.8.jar</b></p>
<p>General data-binding functionality for Jackson: works on core streaming API</p>
<p>Library home page: <a href="http://github.com/FasterXML/jackson">http://github.com/FasterXML/jackson</a></p>
<p>Path to dependency file: /pom.xml</p>
<p>Path to vulnerable library: /home/wss-scanner/.m2/repository/com/fasterxml/jackson/core/jackson-databind/2.9.8/jackson-databind-2.9.8.jar</p>
<p>
Dependency Hierarchy:
- spring-boot-starter-web-2.1.2.RELEASE.jar (Root Library)
- spring-boot-starter-json-2.1.2.RELEASE.jar
- :x: **jackson-databind-2.9.8.jar** (Vulnerable Library)
<p>Found in HEAD commit: <a href="https://github.com/sast-automation-dev/vulnado-46/commit/bbbdc414743ce0d1eacca72de56770d0c21f8a4f">bbbdc414743ce0d1eacca72de56770d0c21f8a4f</a></p>
<p>Found in base branch: <b>master</b></p>
</p>
<p></p>
### Vulnerability Details
<p>
A Polymorphic Typing issue was discovered in FasterXML jackson-databind before 2.9.10. It is related to net.sf.ehcache.hibernate.EhcacheJtaTransactionManagerLookup.
<p>Publish Date: 2019-10-07
<p>URL: <a href=https://www.mend.io/vulnerability-database/CVE-2019-17267>CVE-2019-17267</a></p>
</p>
<p></p>
### CVSS 3 Score Details (<b>9.8</b>)
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: High
- Integrity Impact: High
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
<p></p>
### Suggested Fix
<p>
<p>Type: Upgrade version</p>
<p>Release Date: 2019-10-07</p>
<p>Fix Resolution (com.fasterxml.jackson.core:jackson-databind): 2.9.9.3-redhat-00001</p>
<p>Direct dependency fix Resolution (org.springframework.boot:spring-boot-starter-web): 2.1.10.RELEASE</p>
</p>
<p></p>
:rescue_worker_helmet: Automatic Remediation is available for this issue
</details><details>
<summary><img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> CVE-2020-8840</summary>
### Vulnerable Library - <b>jackson-databind-2.9.8.jar</b></p>
<p>General data-binding functionality for Jackson: works on core streaming API</p>
<p>Library home page: <a href="http://github.com/FasterXML/jackson">http://github.com/FasterXML/jackson</a></p>
<p>Path to dependency file: /pom.xml</p>
<p>Path to vulnerable library: /home/wss-scanner/.m2/repository/com/fasterxml/jackson/core/jackson-databind/2.9.8/jackson-databind-2.9.8.jar</p>
<p>
Dependency Hierarchy:
- spring-boot-starter-web-2.1.2.RELEASE.jar (Root Library)
- spring-boot-starter-json-2.1.2.RELEASE.jar
- :x: **jackson-databind-2.9.8.jar** (Vulnerable Library)
<p>Found in HEAD commit: <a href="https://github.com/sast-automation-dev/vulnado-46/commit/bbbdc414743ce0d1eacca72de56770d0c21f8a4f">bbbdc414743ce0d1eacca72de56770d0c21f8a4f</a></p>
<p>Found in base branch: <b>master</b></p>
</p>
<p></p>
### Vulnerability Details
<p>
FasterXML jackson-databind 2.0.0 through 2.9.10.2 lacks certain xbean-reflect/JNDI blocking, as demonstrated by org.apache.xbean.propertyeditor.JndiConverter.
<p>Publish Date: 2020-02-10
<p>URL: <a href=https://www.mend.io/vulnerability-database/CVE-2020-8840>CVE-2020-8840</a></p>
</p>
<p></p>
### CVSS 3 Score Details (<b>9.8</b>)
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: High
- Integrity Impact: High
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
<p></p>
### Suggested Fix
<p>
<p>Type: Upgrade version</p>
<p>Release Date: 2020-02-10</p>
<p>Fix Resolution (com.fasterxml.jackson.core:jackson-databind): 2.9.10.redhat-00005</p>
<p>Direct dependency fix Resolution (org.springframework.boot:spring-boot-starter-web): 2.2.0.RELEASE</p>
</p>
<p></p>
:rescue_worker_helmet: Automatic Remediation is available for this issue
</details><details>
<summary><img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> CVE-2019-16942</summary>
### Vulnerable Library - <b>jackson-databind-2.9.8.jar</b></p>
<p>General data-binding functionality for Jackson: works on core streaming API</p>
<p>Library home page: <a href="http://github.com/FasterXML/jackson">http://github.com/FasterXML/jackson</a></p>
<p>Path to dependency file: /pom.xml</p>
<p>Path to vulnerable library: /home/wss-scanner/.m2/repository/com/fasterxml/jackson/core/jackson-databind/2.9.8/jackson-databind-2.9.8.jar</p>
<p>
Dependency Hierarchy:
- spring-boot-starter-web-2.1.2.RELEASE.jar (Root Library)
- spring-boot-starter-json-2.1.2.RELEASE.jar
- :x: **jackson-databind-2.9.8.jar** (Vulnerable Library)
<p>Found in HEAD commit: <a href="https://github.com/sast-automation-dev/vulnado-46/commit/bbbdc414743ce0d1eacca72de56770d0c21f8a4f">bbbdc414743ce0d1eacca72de56770d0c21f8a4f</a></p>
<p>Found in base branch: <b>master</b></p>
</p>
<p></p>
### Vulnerability Details
<p>
A Polymorphic Typing issue was discovered in FasterXML jackson-databind 2.0.0 through 2.9.10. When Default Typing is enabled (either globally or for a specific property) for an externally exposed JSON endpoint and the service has the commons-dbcp (1.4) jar in the classpath, and an attacker can find an RMI service endpoint to access, it is possible to make the service execute a malicious payload. This issue exists because of org.apache.commons.dbcp.datasources.SharedPoolDataSource and org.apache.commons.dbcp.datasources.PerUserPoolDataSource mishandling.
<p>Publish Date: 2019-10-01
<p>URL: <a href=https://www.mend.io/vulnerability-database/CVE-2019-16942>CVE-2019-16942</a></p>
</p>
<p></p>
### CVSS 3 Score Details (<b>9.8</b>)
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: High
- Integrity Impact: High
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
<p></p>
### Suggested Fix
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-16942">https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-16942</a></p>
<p>Release Date: 2019-10-01</p>
<p>Fix Resolution (com.fasterxml.jackson.core:jackson-databind): 2.9.10.redhat-00002</p>
<p>Direct dependency fix Resolution (org.springframework.boot:spring-boot-starter-web): 2.2.0.RELEASE</p>
</p>
<p></p>
:rescue_worker_helmet: Automatic Remediation is available for this issue
</details><details>
<summary><img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> CVE-2019-16943</summary>
### Vulnerable Library - <b>jackson-databind-2.9.8.jar</b></p>
<p>General data-binding functionality for Jackson: works on core streaming API</p>
<p>Library home page: <a href="http://github.com/FasterXML/jackson">http://github.com/FasterXML/jackson</a></p>
<p>Path to dependency file: /pom.xml</p>
<p>Path to vulnerable library: /home/wss-scanner/.m2/repository/com/fasterxml/jackson/core/jackson-databind/2.9.8/jackson-databind-2.9.8.jar</p>
<p>
Dependency Hierarchy:
- spring-boot-starter-web-2.1.2.RELEASE.jar (Root Library)
- spring-boot-starter-json-2.1.2.RELEASE.jar
- :x: **jackson-databind-2.9.8.jar** (Vulnerable Library)
<p>Found in HEAD commit: <a href="https://github.com/sast-automation-dev/vulnado-46/commit/bbbdc414743ce0d1eacca72de56770d0c21f8a4f">bbbdc414743ce0d1eacca72de56770d0c21f8a4f</a></p>
<p>Found in base branch: <b>master</b></p>
</p>
<p></p>
### Vulnerability Details
<p>
A Polymorphic Typing issue was discovered in FasterXML jackson-databind 2.0.0 through 2.9.10. When Default Typing is enabled (either globally or for a specific property) for an externally exposed JSON endpoint and the service has the p6spy (3.8.6) jar in the classpath, and an attacker can find an RMI service endpoint to access, it is possible to make the service execute a malicious payload. This issue exists because of com.p6spy.engine.spy.P6DataSource mishandling.
<p>Publish Date: 2019-10-01
<p>URL: <a href=https://www.mend.io/vulnerability-database/CVE-2019-16943>CVE-2019-16943</a></p>
</p>
<p></p>
### CVSS 3 Score Details (<b>9.8</b>)
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: High
- Integrity Impact: High
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
<p></p>
### Suggested Fix
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-16943">https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-16943</a></p>
<p>Release Date: 2019-10-01</p>
<p>Fix Resolution (com.fasterxml.jackson.core:jackson-databind): 2.9.10.redhat-00002</p>
<p>Direct dependency fix Resolution (org.springframework.boot:spring-boot-starter-web): 2.2.0.RELEASE</p>
</p>
<p></p>
:rescue_worker_helmet: Automatic Remediation is available for this issue
</details><details>
<summary><img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> CVE-2019-14893</summary>
### Vulnerable Library - <b>jackson-databind-2.9.8.jar</b></p>
<p>General data-binding functionality for Jackson: works on core streaming API</p>
<p>Library home page: <a href="http://github.com/FasterXML/jackson">http://github.com/FasterXML/jackson</a></p>
<p>Path to dependency file: /pom.xml</p>
<p>Path to vulnerable library: /home/wss-scanner/.m2/repository/com/fasterxml/jackson/core/jackson-databind/2.9.8/jackson-databind-2.9.8.jar</p>
<p>
Dependency Hierarchy:
- spring-boot-starter-web-2.1.2.RELEASE.jar (Root Library)
- spring-boot-starter-json-2.1.2.RELEASE.jar
- :x: **jackson-databind-2.9.8.jar** (Vulnerable Library)
<p>Found in HEAD commit: <a href="https://github.com/sast-automation-dev/vulnado-46/commit/bbbdc414743ce0d1eacca72de56770d0c21f8a4f">bbbdc414743ce0d1eacca72de56770d0c21f8a4f</a></p>
<p>Found in base branch: <b>master</b></p>
</p>
<p></p>
### Vulnerability Details
<p>
A flaw was discovered in FasterXML jackson-databind in all versions before 2.9.10 and 2.10.0, where it would permit polymorphic deserialization of malicious objects using the xalan JNDI gadget when used in conjunction with polymorphic type handling methods such as `enableDefaultTyping()` or when @JsonTypeInfo is using `Id.CLASS` or `Id.MINIMAL_CLASS` or in any other way which ObjectMapper.readValue might instantiate objects from unsafe sources. An attacker could use this flaw to execute arbitrary code.
<p>Publish Date: 2020-03-02
<p>URL: <a href=https://www.mend.io/vulnerability-database/CVE-2019-14893>CVE-2019-14893</a></p>
</p>
<p></p>
### CVSS 3 Score Details (<b>9.8</b>)
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: High
- Integrity Impact: High
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
<p></p>
### Suggested Fix
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-14893">https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-14893</a></p>
<p>Release Date: 2020-03-02</p>
<p>Fix Resolution (com.fasterxml.jackson.core:jackson-databind): 2.9.10</p>
<p>Direct dependency fix Resolution (org.springframework.boot:spring-boot-starter-web): 2.1.10.RELEASE</p>
</p>
<p></p>
:rescue_worker_helmet: Automatic Remediation is available for this issue
</details><details>
<summary><img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> CVE-2019-14892</summary>
### Vulnerable Library - <b>jackson-databind-2.9.8.jar</b></p>
<p>General data-binding functionality for Jackson: works on core streaming API</p>
<p>Library home page: <a href="http://github.com/FasterXML/jackson">http://github.com/FasterXML/jackson</a></p>
<p>Path to dependency file: /pom.xml</p>
<p>Path to vulnerable library: /home/wss-scanner/.m2/repository/com/fasterxml/jackson/core/jackson-databind/2.9.8/jackson-databind-2.9.8.jar</p>
<p>
Dependency Hierarchy:
- spring-boot-starter-web-2.1.2.RELEASE.jar (Root Library)
- spring-boot-starter-json-2.1.2.RELEASE.jar
- :x: **jackson-databind-2.9.8.jar** (Vulnerable Library)
<p>Found in HEAD commit: <a href="https://github.com/sast-automation-dev/vulnado-46/commit/bbbdc414743ce0d1eacca72de56770d0c21f8a4f">bbbdc414743ce0d1eacca72de56770d0c21f8a4f</a></p>
<p>Found in base branch: <b>master</b></p>
</p>
<p></p>
### Vulnerability Details
<p>
A flaw was discovered in jackson-databind in versions before 2.9.10, 2.8.11.5 and 2.6.7.3, where it would permit polymorphic deserialization of a malicious object using commons-configuration 1 and 2 JNDI classes. An attacker could use this flaw to execute arbitrary code.
<p>Publish Date: 2020-03-02
<p>URL: <a href=https://www.mend.io/vulnerability-database/CVE-2019-14892>CVE-2019-14892</a></p>
</p>
<p></p>
### CVSS 3 Score Details (<b>9.8</b>)
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: High
- Integrity Impact: High
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
<p></p>
### Suggested Fix
<p>
<p>Type: Upgrade version</p>
<p>Release Date: 2020-09-04</p>
<p>Fix Resolution (com.fasterxml.jackson.core:jackson-databind): 2.9.9.3-redhat-00001</p>
<p>Direct dependency fix Resolution (org.springframework.boot:spring-boot-starter-web): 2.1.10.RELEASE</p>
</p>
<p></p>
:rescue_worker_helmet: Automatic Remediation is available for this issue
</details><details>
<summary><img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> CVE-2020-9546</summary>
### Vulnerable Library - <b>jackson-databind-2.9.8.jar</b></p>
<p>General data-binding functionality for Jackson: works on core streaming API</p>
<p>Library home page: <a href="http://github.com/FasterXML/jackson">http://github.com/FasterXML/jackson</a></p>
<p>Path to dependency file: /pom.xml</p>
<p>Path to vulnerable library: /home/wss-scanner/.m2/repository/com/fasterxml/jackson/core/jackson-databind/2.9.8/jackson-databind-2.9.8.jar</p>
<p>
Dependency Hierarchy:
- spring-boot-starter-web-2.1.2.RELEASE.jar (Root Library)
- spring-boot-starter-json-2.1.2.RELEASE.jar
- :x: **jackson-databind-2.9.8.jar** (Vulnerable Library)
<p>Found in HEAD commit: <a href="https://github.com/sast-automation-dev/vulnado-46/commit/bbbdc414743ce0d1eacca72de56770d0c21f8a4f">bbbdc414743ce0d1eacca72de56770d0c21f8a4f</a></p>
<p>Found in base branch: <b>master</b></p>
</p>
<p></p>
### Vulnerability Details
<p>
FasterXML jackson-databind 2.x before 2.9.10.4 mishandles the interaction between serialization gadgets and typing, related to org.apache.hadoop.shaded.com.zaxxer.hikari.HikariConfig (aka shaded hikari-config).
<p>Publish Date: 2020-03-02
<p>URL: <a href=https://www.mend.io/vulnerability-database/CVE-2020-9546>CVE-2020-9546</a></p>
</p>
<p></p>
### CVSS 3 Score Details (<b>9.8</b>)
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: High
- Integrity Impact: High
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
<p></p>
### Suggested Fix
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2020-9546">https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2020-9546</a></p>
<p>Release Date: 2020-03-02</p>
<p>Fix Resolution (com.fasterxml.jackson.core:jackson-databind): 2.9.10.redhat-00005</p>
<p>Direct dependency fix Resolution (org.springframework.boot:spring-boot-starter-web): 2.2.0.RELEASE</p>
</p>
<p></p>
:rescue_worker_helmet: Automatic Remediation is available for this issue
</details><details>
<summary><img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> CVE-2019-14379</summary>
### Vulnerable Library - <b>jackson-databind-2.9.8.jar</b></p>
<p>General data-binding functionality for Jackson: works on core streaming API</p>
<p>Library home page: <a href="http://github.com/FasterXML/jackson">http://github.com/FasterXML/jackson</a></p>
<p>Path to dependency file: /pom.xml</p>
<p>Path to vulnerable library: /home/wss-scanner/.m2/repository/com/fasterxml/jackson/core/jackson-databind/2.9.8/jackson-databind-2.9.8.jar</p>
<p>
Dependency Hierarchy:
- spring-boot-starter-web-2.1.2.RELEASE.jar (Root Library)
- spring-boot-starter-json-2.1.2.RELEASE.jar
- :x: **jackson-databind-2.9.8.jar** (Vulnerable Library)
<p>Found in HEAD commit: <a href="https://github.com/sast-automation-dev/vulnado-46/commit/bbbdc414743ce0d1eacca72de56770d0c21f8a4f">bbbdc414743ce0d1eacca72de56770d0c21f8a4f</a></p>
<p>Found in base branch: <b>master</b></p>
</p>
<p></p>
### Vulnerability Details
<p>
SubTypeValidator.java in FasterXML jackson-databind before 2.9.9.2 mishandles default typing when ehcache is used (because of net.sf.ehcache.transaction.manager.DefaultTransactionManagerLookup), leading to remote code execution.
<p>Publish Date: 2019-07-29
<p>URL: <a href=https://www.mend.io/vulnerability-database/CVE-2019-14379>CVE-2019-14379</a></p>
</p>
<p></p>
### CVSS 3 Score Details (<b>9.8</b>)
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: High
- Integrity Impact: High
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
<p></p>
### Suggested Fix
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-14379">https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-14379</a></p>
<p>Release Date: 2019-07-29</p>
<p>Fix Resolution (com.fasterxml.jackson.core:jackson-databind): 2.9.9.2</p>
<p>Direct dependency fix Resolution (org.springframework.boot:spring-boot-starter-web): 2.1.10.RELEASE</p>
</p>
<p></p>
:rescue_worker_helmet: Automatic Remediation is available for this issue
</details><details>
<summary><img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> CVE-2020-9547</summary>
### Vulnerable Library - <b>jackson-databind-2.9.8.jar</b></p>
<p>General data-binding functionality for Jackson: works on core streaming API</p>
<p>Library home page: <a href="http://github.com/FasterXML/jackson">http://github.com/FasterXML/jackson</a></p>
<p>Path to dependency file: /pom.xml</p>
<p>Path to vulnerable library: /home/wss-scanner/.m2/repository/com/fasterxml/jackson/core/jackson-databind/2.9.8/jackson-databind-2.9.8.jar</p>
<p>
Dependency Hierarchy:
- spring-boot-starter-web-2.1.2.RELEASE.jar (Root Library)
- spring-boot-starter-json-2.1.2.RELEASE.jar
- :x: **jackson-databind-2.9.8.jar** (Vulnerable Library)
<p>Found in HEAD commit: <a href="https://github.com/sast-automation-dev/vulnado-46/commit/bbbdc414743ce0d1eacca72de56770d0c21f8a4f">bbbdc414743ce0d1eacca72de56770d0c21f8a4f</a></p>
<p>Found in base branch: <b>master</b></p>
</p>
<p></p>
### Vulnerability Details
<p>
FasterXML jackson-databind 2.x before 2.9.10.4 mishandles the interaction between serialization gadgets and typing, related to com.ibatis.sqlmap.engine.transaction.jta.JtaTransactionConfig (aka ibatis-sqlmap).
<p>Publish Date: 2020-03-02
<p>URL: <a href=https://www.mend.io/vulnerability-database/CVE-2020-9547>CVE-2020-9547</a></p>
</p>
<p></p>
### CVSS 3 Score Details (<b>9.8</b>)
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: High
- Integrity Impact: High
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
<p></p>
### Suggested Fix
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2020-9547">https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2020-9547</a></p>
<p>Release Date: 2020-03-02</p>
<p>Fix Resolution (com.fasterxml.jackson.core:jackson-databind): 2.9.10.redhat-00005</p>
<p>Direct dependency fix Resolution (org.springframework.boot:spring-boot-starter-web): 2.2.0.RELEASE</p>
</p>
<p></p>
:rescue_worker_helmet: Automatic Remediation is available for this issue
</details><details>
<summary><img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> CVE-2020-9548</summary>
### Vulnerable Library - <b>jackson-databind-2.9.8.jar</b></p>
<p>General data-binding functionality for Jackson: works on core streaming API</p>
<p>Library home page: <a href="http://github.com/FasterXML/jackson">http://github.com/FasterXML/jackson</a></p>
<p>Path to dependency file: /pom.xml</p>
<p>Path to vulnerable library: /home/wss-scanner/.m2/repository/com/fasterxml/jackson/core/jackson-databind/2.9.8/jackson-databind-2.9.8.jar</p>
<p>
Dependency Hierarchy:
- spring-boot-starter-web-2.1.2.RELEASE.jar (Root Library)
- spring-boot-starter-json-2.1.2.RELEASE.jar
- :x: **jackson-databind-2.9.8.jar** (Vulnerable Library)
<p>Found in HEAD commit: <a href="https://github.com/sast-automation-dev/vulnado-46/commit/bbbdc414743ce0d1eacca72de56770d0c21f8a4f">bbbdc414743ce0d1eacca72de56770d0c21f8a4f</a></p>
<p>Found in base branch: <b>master</b></p>
</p>
<p></p>
### Vulnerability Details
<p>
FasterXML jackson-databind 2.x before 2.9.10.4 mishandles the interaction between serialization gadgets and typing, related to br.com.anteros.dbcp.AnterosDBCPConfig (aka anteros-core).
<p>Publish Date: 2020-03-02
<p>URL: <a href=https://www.mend.io/vulnerability-database/CVE-2020-9548>CVE-2020-9548</a></p>
</p>
<p></p>
### CVSS 3 Score Details (<b>9.8</b>)
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: High
- Integrity Impact: High
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
<p></p>
### Suggested Fix
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2020-9548">https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2020-9548</a></p>
<p>Release Date: 2020-03-02</p>
<p>Fix Resolution (com.fasterxml.jackson.core:jackson-databind): 2.9.10.redhat-00005</p>
<p>Direct dependency fix Resolution (org.springframework.boot:spring-boot-starter-web): 2.2.0.RELEASE</p>
</p>
<p></p>
:rescue_worker_helmet: Automatic Remediation is available for this issue
</details><details>
<summary><img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> CVE-2019-20330</summary>
### Vulnerable Library - <b>jackson-databind-2.9.8.jar</b></p>
<p>General data-binding functionality for Jackson: works on core streaming API</p>
<p>Library home page: <a href="http://github.com/FasterXML/jackson">http://github.com/FasterXML/jackson</a></p>
<p>Path to dependency file: /pom.xml</p>
<p>Path to vulnerable library: /home/wss-scanner/.m2/repository/com/fasterxml/jackson/core/jackson-databind/2.9.8/jackson-databind-2.9.8.jar</p>
<p>
Dependency Hierarchy:
- spring-boot-starter-web-2.1.2.RELEASE.jar (Root Library)
- spring-boot-starter-json-2.1.2.RELEASE.jar
- :x: **jackson-databind-2.9.8.jar** (Vulnerable Library)
<p>Found in HEAD commit: <a href="https://github.com/sast-automation-dev/vulnado-46/commit/bbbdc414743ce0d1eacca72de56770d0c21f8a4f">bbbdc414743ce0d1eacca72de56770d0c21f8a4f</a></p>
<p>Found in base branch: <b>master</b></p>
</p>
<p></p>
### Vulnerability Details
<p>
FasterXML jackson-databind 2.x before 2.9.10.2 lacks certain net.sf.ehcache blocking.
<p>Publish Date: 2020-01-03
<p>URL: <a href=https://www.mend.io/vulnerability-database/CVE-2019-20330>CVE-2019-20330</a></p>
</p>
<p></p>
### CVSS 3 Score Details (<b>9.8</b>)
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: High
- Integrity Impact: High
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
<p></p>
### Suggested Fix
<p>
<p>Type: Upgrade version</p>
<p>Release Date: 2020-01-03</p>
<p>Fix Resolution (com.fasterxml.jackson.core:jackson-databind): 2.9.10.redhat-00005</p>
<p>Direct dependency fix Resolution (org.springframework.boot:spring-boot-starter-web): 2.2.0.RELEASE</p>
</p>
<p></p>
:rescue_worker_helmet: Automatic Remediation is available for this issue
</details><details>
<summary><img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> CVE-2020-10968</summary>
### Vulnerable Library - <b>jackson-databind-2.9.8.jar</b></p>
<p>General data-binding functionality for Jackson: works on core streaming API</p>
<p>Library home page: <a href="http://github.com/FasterXML/jackson">http://github.com/FasterXML/jackson</a></p>
<p>Path to dependency file: /pom.xml</p>
<p>Path to vulnerable library: /home/wss-scanner/.m2/repository/com/fasterxml/jackson/core/jackson-databind/2.9.8/jackson-databind-2.9.8.jar</p>
<p>
Dependency Hierarchy:
- spring-boot-starter-web-2.1.2.RELEASE.jar (Root Library)
- spring-boot-starter-json-2.1.2.RELEASE.jar
- :x: **jackson-databind-2.9.8.jar** (Vulnerable Library)
<p>Found in HEAD commit: <a href="https://github.com/sast-automation-dev/vulnado-46/commit/bbbdc414743ce0d1eacca72de56770d0c21f8a4f">bbbdc414743ce0d1eacca72de56770d0c21f8a4f</a></p>
<p>Found in base branch: <b>master</b></p>
</p>
<p></p>
### Vulnerability Details
<p>
FasterXML jackson-databind 2.x before 2.9.10.4 mishandles the interaction between serialization gadgets and typing, related to org.aoju.bus.proxy.provider.remoting.RmiProvider (aka bus-proxy).
<p>Publish Date: 2020-03-26
<p>URL: <a href=https://www.mend.io/vulnerability-database/CVE-2020-10968>CVE-2020-10968</a></p>
</p>
<p></p>
### CVSS 3 Score Details (<b>8.8</b>)
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: Required
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: High
- Integrity Impact: High
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
<p></p>
### Suggested Fix
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://nvd.nist.gov/vuln/detail/CVE-2020-10968">https://nvd.nist.gov/vuln/detail/CVE-2020-10968</a></p>
<p>Release Date: 2020-03-26</p>
<p>Fix Resolution (com.fasterxml.jackson.core:jackson-databind): 2.9.8.redhat-00002</p>
<p>Direct dependency fix Resolution (org.springframework.boot:spring-boot-starter-web): 2.1.6.RELEASE</p>
</p>
<p></p>
:rescue_worker_helmet: Automatic Remediation is available for this issue
</details><details>
<summary><img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> CVE-2020-10969</summary>
### Vulnerable Library - <b>jackson-databind-2.9.8.jar</b></p>
<p>General data-binding functionality for Jackson: works on core streaming API</p>
<p>Library home page: <a href="http://github.com/FasterXML/jackson">http://github.com/FasterXML/jackson</a></p>
<p>Path to dependency file: /pom.xml</p>
<p>Path to vulnerable library: /home/wss-scanner/.m2/repository/com/fasterxml/jackson/core/jackson-databind/2.9.8/jackson-databind-2.9.8.jar</p>
<p>
Dependency Hierarchy:
- spring-boot-starter-web-2.1.2.RELEASE.jar (Root Library)
- spring-boot-starter-json-2.1.2.RELEASE.jar
- :x: **jackson-databind-2.9.8.jar** (Vulnerable Library)
<p>Found in HEAD commit: <a href="https://github.com/sast-automation-dev/vulnado-46/commit/bbbdc414743ce0d1eacca72de56770d0c21f8a4f">bbbdc414743ce0d1eacca72de56770d0c21f8a4f</a></p>
<p>Found in base branch: <b>master</b></p>
</p>
<p></p>
### Vulnerability Details
<p>
FasterXML jackson-databind 2.x before 2.9.10.4 mishandles the interaction between serialization gadgets and typing, related to javax.swing.JEditorPane.
<p>Publish Date: 2020-03-26
<p>URL: <a href=https://www.mend.io/vulnerability-database/CVE-2020-10969>CVE-2020-10969</a></p>
</p>
<p></p>
### CVSS 3 Score Details (<b>8.8</b>)
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: Required
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: High
- Integrity Impact: High
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
<p></p>
### Suggested Fix
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2020-10969">https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2020-10969</a></p>
<p>Release Date: 2020-03-26</p>
<p>Fix Resolution (com.fasterxml.jackson.core:jackson-databind): 2.9.10.redhat-00005</p>
<p>Direct dependency fix Resolution (org.springframework.boot:spring-boot-starter-web): 2.2.0.RELEASE</p>
</p>
<p></p>
:rescue_worker_helmet: Automatic Remediation is available for this issue
</details><details>
<summary><img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> CVE-2020-11111</summary>
### Vulnerable Library - <b>jackson-databind-2.9.8.jar</b></p>
<p>General data-binding functionality for Jackson: works on core streaming API</p>
<p>Library home page: <a href="http://github.com/FasterXML/jackson">http://github.com/FasterXML/jackson</a></p>
<p>Path to dependency file: /pom.xml</p>
<p>Path to vulnerable library: /home/wss-scanner/.m2/repository/com/fasterxml/jackson/core/jackson-databind/2.9.8/jackson-databind-2.9.8.jar</p>
<p>
Dependency Hierarchy:
- spring-boot-starter-web-2.1.2.RELEASE.jar (Root Library)
- spring-boot-starter-json-2.1.2.RELEASE.jar
- :x: **jackson-databind-2.9.8.jar** (Vulnerable Library)
<p>Found in HEAD commit: <a href="https://github.com/sast-automation-dev/vulnado-46/commit/bbbdc414743ce0d1eacca72de56770d0c21f8a4f">bbbdc414743ce0d1eacca72de56770d0c21f8a4f</a></p>
<p>Found in base branch: <b>master</b></p>
</p>
<p></p>
### Vulnerability Details
<p>
FasterXML jackson-databind 2.x before 2.9.10.4 mishandles the interaction between serialization gadgets and typing, related to org.apache.activemq.* (aka activemq-jms, activemq-core, activemq-pool, and activemq-pool-jms).
<p>Publish Date: 2020-03-31
<p>URL: <a href=https://www.mend.io/vulnerability-database/CVE-2020-11111>CVE-2020-11111</a></p>
</p>
<p></p>
### CVSS 3 Score Details (<b>8.8</b>)
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: Required
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: High
- Integrity Impact: High
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
<p></p>
### Suggested Fix
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2020-11113">https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2020-11113</a></p>
<p>Release Date: 2020-03-31</p>
<p>Fix Resolution (com.fasterxml.jackson.core:jackson-databind): 2.9.10.redhat-00005</p>
<p>Direct dependency fix Resolution (org.springframework.boot:spring-boot-starter-web): 2.2.0.RELEASE</p>
</p>
<p></p>
:rescue_worker_helmet: Automatic Remediation is available for this issue
</details><details>
<summary><img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> CVE-2020-11113</summary>
### Vulnerable Library - <b>jackson-databind-2.9.8.jar</b></p>
<p>General data-binding functionality for Jackson: works on core streaming API</p>
<p>Library home page: <a href="http://github.com/FasterXML/jackson">http://github.com/FasterXML/jackson</a></p>
<p>Path to dependency file: /pom.xml</p>
<p>Path to vulnerable library: /home/wss-scanner/.m2/repository/com/fasterxml/jackson/core/jackson-databind/2.9.8/jackson-databind-2.9.8.jar</p>
<p>
Dependency Hierarchy:
- spring-boot-starter-web-2.1.2.RELEASE.jar (Root Library)
- spring-boot-starter-json-2.1.2.RELEASE.jar
- :x: **jackson-databind-2.9.8.jar** (Vulnerable Library)
<p>Found in HEAD commit: <a href="https://github.com/sast-automation-dev/vulnado-46/commit/bbbdc414743ce0d1eacca72de56770d0c21f8a4f">bbbdc414743ce0d1eacca72de56770d0c21f8a4f</a></p>
<p>Found in base branch: <b>master</b></p>
</p>
<p></p>
### Vulnerability Details
<p>
FasterXML jackson-databind 2.x before 2.9.10.4 mishandles the interaction between serialization gadgets and typing, related to org.apache.openjpa.ee.WASRegistryManagedRuntime (aka openjpa).
<p>Publish Date: 2020-03-31
<p>URL: <a href=https://www.mend.io/vulnerability-database/CVE-2020-11113>CVE-2020-11113</a></p>
</p>
<p></p>
### CVSS 3 Score Details (<b>8.8</b>)
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: Required
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: High
- Integrity Impact: High
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
<p></p>
### Suggested Fix
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2020-11113">https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2020-11113</a></p>
<p>Release Date: 2020-03-31</p>
<p>Fix Resolution (com.fasterxml.jackson.core:jackson-databind): 2.9.10.redhat-00005</p>
<p>Direct dependency fix Resolution (org.springframework.boot:spring-boot-starter-web): 2.2.0.RELEASE</p>
</p>
<p></p>
:rescue_worker_helmet: Automatic Remediation is available for this issue
</details>
***
<p>:rescue_worker_helmet: Automatic Remediation is available for this issue.</p> | non_priority | spring boot starter web release jar vulnerabilities highest severity is vulnerable library spring boot starter web release jar path to dependency file pom xml path to vulnerable library home wss scanner repository org apache tomcat embed tomcat embed core tomcat embed core jar found in head commit a href vulnerabilities cve severity cvss dependency type fixed in spring boot starter web version remediation available high jackson databind jar transitive release high jackson databind jar transitive release high spring web release jar transitive release high jackson databind jar transitive release high jackson databind jar transitive release high jackson databind jar transitive release high jackson databind jar transitive release high jackson databind jar transitive release high jackson databind jar transitive release high jackson databind jar transitive release high jackson databind jar transitive release high jackson databind jar transitive release high jackson databind jar transitive release high jackson databind jar transitive release high jackson databind jar transitive release high jackson databind jar transitive release high jackson databind jar transitive release high jackson databind jar transitive release high jackson databind jar transitive release high jackson databind jar transitive release high jackson databind jar transitive release high jackson databind jar transitive release high tomcat embed core jar transitive release high jackson databind jar transitive release high jackson databind jar transitive release high jackson databind jar transitive release high jackson databind jar transitive release high jackson databind jar transitive release high jackson databind jar transitive release high jackson databind jar transitive release high jackson databind jar transitive release high jackson databind jar transitive release high jackson databind jar transitive release high jackson databind jar transitive release high jackson databind jar transitive release high jackson databind jar transitive release high jackson databind jar transitive release high jackson databind jar transitive release high jackson databind jar transitive release high jackson databind jar transitive release high jackson databind jar transitive release high jackson databind jar transitive release high jackson databind jar transitive release high jackson databind jar transitive release high jackson databind jar transitive release high jackson databind jar transitive release high jackson databind jar transitive release high jackson databind jar transitive release high spring web release jar transitive release high tomcat embed core jar transitive release high jackson databind jar transitive release high tomcat embed core jar transitive release high tomcat embed core jar transitive release high tomcat embed core jar transitive release high tomcat embed core jar transitive release high tomcat embed websocket jar transitive release high tomcat embed core jar transitive release high tomcat embed core jar transitive release medium spring web release jar transitive release medium tomcat embed core jar transitive release medium hibernate validator final jar transitive release medium jackson databind jar transitive release medium jackson databind jar transitive release medium tomcat embed core jar transitive release medium hibernate validator final jar transitive release medium jackson databind jar transitive n a medium tomcat embed core jar transitive release medium tomcat embed core jar transitive release for some transitive vulnerabilities there is no version of direct dependency with a fix check the section details below to see if there is a version of transitive dependency where vulnerability is fixed details partial details vulnerabilities are displayed below due to a content size limitation in github to view information on the remaining vulnerabilities navigate to the mend application cve vulnerable library jackson databind jar general data binding functionality for jackson works on core streaming api library home page a href path to dependency file pom xml path to vulnerable library home wss scanner repository com fasterxml jackson core jackson databind jackson databind jar dependency hierarchy spring boot starter web release jar root library spring boot starter json release jar x jackson databind jar vulnerable library found in head commit a href found in base branch master vulnerability details a polymorphic typing issue was discovered in fasterxml jackson databind before it is related to com zaxxer hikari hikariconfig publish date url a href cvss score details base score metrics exploitability metrics attack vector network attack complexity low privileges required none user interaction none scope unchanged impact metrics confidentiality impact high integrity impact high availability impact high for more information on scores click a href suggested fix type upgrade version origin a href release date fix resolution com fasterxml jackson core jackson databind redhat direct dependency fix resolution org springframework boot spring boot starter web release rescue worker helmet automatic remediation is available for this issue cve vulnerable library jackson databind jar general data binding functionality for jackson works on core streaming api library home page a href path to dependency file pom xml path to vulnerable library home wss scanner repository com fasterxml jackson core jackson databind jackson databind jar dependency hierarchy spring boot starter web release jar root library spring boot starter json release jar x jackson databind jar vulnerable library found in head commit a href found in base branch master vulnerability details a polymorphic typing issue was discovered in fasterxml jackson databind through when default typing is enabled either globally or for a specific property for an externally exposed json endpoint and the service has the apache extra version x jar in the classpath and an attacker can provide a jndi service to access it is possible to make the service execute a malicious payload publish date url a href cvss score details base score metrics exploitability metrics attack vector network attack complexity low privileges required none user interaction none scope unchanged impact metrics confidentiality impact high integrity impact high availability impact high for more information on scores click a href suggested fix type upgrade version origin a href release date fix resolution com fasterxml jackson core jackson databind redhat direct dependency fix resolution org springframework boot spring boot starter web release rescue worker helmet automatic remediation is available for this issue cve vulnerable library spring web release jar spring web library home page a href path to dependency file pom xml path to vulnerable library home wss scanner repository org springframework spring web release spring web release jar dependency hierarchy spring boot starter web release jar root library x spring web release jar vulnerable library found in head commit a href found in base branch master vulnerability details pivotal spring framework suffers from a potential remote code execution rce issue if used for java deserialization of untrusted data depending on how the library is implemented within a product this issue may or not occur and authentication may be required publish date url a href cvss score details base score metrics exploitability metrics attack vector network attack complexity low privileges required none user interaction none scope unchanged impact metrics confidentiality impact high integrity impact high availability impact high for more information on scores click a href suggested fix type upgrade version release date fix resolution org springframework spring web release direct dependency fix resolution org springframework boot spring boot starter web release rescue worker helmet automatic remediation is available for this issue cve vulnerable library jackson databind jar general data binding functionality for jackson works on core streaming api library home page a href path to dependency file pom xml path to vulnerable library home wss scanner repository com fasterxml jackson core jackson databind jackson databind jar dependency hierarchy spring boot starter web release jar root library spring boot starter json release jar x jackson databind jar vulnerable library found in head commit a href found in base branch master vulnerability details a polymorphic typing issue was discovered in fasterxml jackson databind before it is related to com zaxxer hikari hikaridatasource this is a different vulnerability than cve publish date url a href cvss score details base score metrics exploitability metrics attack vector network attack complexity low privileges required none user interaction none scope unchanged impact metrics confidentiality impact high integrity impact high availability impact high for more information on scores click a href suggested fix type upgrade version release date fix resolution com fasterxml jackson core jackson databind redhat direct dependency fix resolution org springframework boot spring boot starter web release rescue worker helmet automatic remediation is available for this issue cve vulnerable library jackson databind jar general data binding functionality for jackson works on core streaming api library home page a href path to dependency file pom xml path to vulnerable library home wss scanner repository com fasterxml jackson core jackson databind jackson databind jar dependency hierarchy spring boot starter web release jar root library spring boot starter json release jar x jackson databind jar vulnerable library found in head commit a href found in base branch master vulnerability details a polymorphic typing issue was discovered in fasterxml jackson databind before it is related to net sf ehcache hibernate ehcachejtatransactionmanagerlookup publish date url a href cvss score details base score metrics exploitability metrics attack vector network attack complexity low privileges required none user interaction none scope unchanged impact metrics confidentiality impact high integrity impact high availability impact high for more information on scores click a href suggested fix type upgrade version release date fix resolution com fasterxml jackson core jackson databind redhat direct dependency fix resolution org springframework boot spring boot starter web release rescue worker helmet automatic remediation is available for this issue cve vulnerable library jackson databind jar general data binding functionality for jackson works on core streaming api library home page a href path to dependency file pom xml path to vulnerable library home wss scanner repository com fasterxml jackson core jackson databind jackson databind jar dependency hierarchy spring boot starter web release jar root library spring boot starter json release jar x jackson databind jar vulnerable library found in head commit a href found in base branch master vulnerability details fasterxml jackson databind through lacks certain xbean reflect jndi blocking as demonstrated by org apache xbean propertyeditor jndiconverter publish date url a href cvss score details base score metrics exploitability metrics attack vector network attack complexity low privileges required none user interaction none scope unchanged impact metrics confidentiality impact high integrity impact high availability impact high for more information on scores click a href suggested fix type upgrade version release date fix resolution com fasterxml jackson core jackson databind redhat direct dependency fix resolution org springframework boot spring boot starter web release rescue worker helmet automatic remediation is available for this issue cve vulnerable library jackson databind jar general data binding functionality for jackson works on core streaming api library home page a href path to dependency file pom xml path to vulnerable library home wss scanner repository com fasterxml jackson core jackson databind jackson databind jar dependency hierarchy spring boot starter web release jar root library spring boot starter json release jar x jackson databind jar vulnerable library found in head commit a href found in base branch master vulnerability details a polymorphic typing issue was discovered in fasterxml jackson databind through when default typing is enabled either globally or for a specific property for an externally exposed json endpoint and the service has the commons dbcp jar in the classpath and an attacker can find an rmi service endpoint to access it is possible to make the service execute a malicious payload this issue exists because of org apache commons dbcp datasources sharedpooldatasource and org apache commons dbcp datasources peruserpooldatasource mishandling publish date url a href cvss score details base score metrics exploitability metrics attack vector network attack complexity low privileges required none user interaction none scope unchanged impact metrics confidentiality impact high integrity impact high availability impact high for more information on scores click a href suggested fix type upgrade version origin a href release date fix resolution com fasterxml jackson core jackson databind redhat direct dependency fix resolution org springframework boot spring boot starter web release rescue worker helmet automatic remediation is available for this issue cve vulnerable library jackson databind jar general data binding functionality for jackson works on core streaming api library home page a href path to dependency file pom xml path to vulnerable library home wss scanner repository com fasterxml jackson core jackson databind jackson databind jar dependency hierarchy spring boot starter web release jar root library spring boot starter json release jar x jackson databind jar vulnerable library found in head commit a href found in base branch master vulnerability details a polymorphic typing issue was discovered in fasterxml jackson databind through when default typing is enabled either globally or for a specific property for an externally exposed json endpoint and the service has the jar in the classpath and an attacker can find an rmi service endpoint to access it is possible to make the service execute a malicious payload this issue exists because of com engine spy mishandling publish date url a href cvss score details base score metrics exploitability metrics attack vector network attack complexity low privileges required none user interaction none scope unchanged impact metrics confidentiality impact high integrity impact high availability impact high for more information on scores click a href suggested fix type upgrade version origin a href release date fix resolution com fasterxml jackson core jackson databind redhat direct dependency fix resolution org springframework boot spring boot starter web release rescue worker helmet automatic remediation is available for this issue cve vulnerable library jackson databind jar general data binding functionality for jackson works on core streaming api library home page a href path to dependency file pom xml path to vulnerable library home wss scanner repository com fasterxml jackson core jackson databind jackson databind jar dependency hierarchy spring boot starter web release jar root library spring boot starter json release jar x jackson databind jar vulnerable library found in head commit a href found in base branch master vulnerability details a flaw was discovered in fasterxml jackson databind in all versions before and where it would permit polymorphic deserialization of malicious objects using the xalan jndi gadget when used in conjunction with polymorphic type handling methods such as enabledefaulttyping or when jsontypeinfo is using id class or id minimal class or in any other way which objectmapper readvalue might instantiate objects from unsafe sources an attacker could use this flaw to execute arbitrary code publish date url a href cvss score details base score metrics exploitability metrics attack vector network attack complexity low privileges required none user interaction none scope unchanged impact metrics confidentiality impact high integrity impact high availability impact high for more information on scores click a href suggested fix type upgrade version origin a href release date fix resolution com fasterxml jackson core jackson databind direct dependency fix resolution org springframework boot spring boot starter web release rescue worker helmet automatic remediation is available for this issue cve vulnerable library jackson databind jar general data binding functionality for jackson works on core streaming api library home page a href path to dependency file pom xml path to vulnerable library home wss scanner repository com fasterxml jackson core jackson databind jackson databind jar dependency hierarchy spring boot starter web release jar root library spring boot starter json release jar x jackson databind jar vulnerable library found in head commit a href found in base branch master vulnerability details a flaw was discovered in jackson databind in versions before and where it would permit polymorphic deserialization of a malicious object using commons configuration and jndi classes an attacker could use this flaw to execute arbitrary code publish date url a href cvss score details base score metrics exploitability metrics attack vector network attack complexity low privileges required none user interaction none scope unchanged impact metrics confidentiality impact high integrity impact high availability impact high for more information on scores click a href suggested fix type upgrade version release date fix resolution com fasterxml jackson core jackson databind redhat direct dependency fix resolution org springframework boot spring boot starter web release rescue worker helmet automatic remediation is available for this issue cve vulnerable library jackson databind jar general data binding functionality for jackson works on core streaming api library home page a href path to dependency file pom xml path to vulnerable library home wss scanner repository com fasterxml jackson core jackson databind jackson databind jar dependency hierarchy spring boot starter web release jar root library spring boot starter json release jar x jackson databind jar vulnerable library found in head commit a href found in base branch master vulnerability details fasterxml jackson databind x before mishandles the interaction between serialization gadgets and typing related to org apache hadoop shaded com zaxxer hikari hikariconfig aka shaded hikari config publish date url a href cvss score details base score metrics exploitability metrics attack vector network attack complexity low privileges required none user interaction none scope unchanged impact metrics confidentiality impact high integrity impact high availability impact high for more information on scores click a href suggested fix type upgrade version origin a href release date fix resolution com fasterxml jackson core jackson databind redhat direct dependency fix resolution org springframework boot spring boot starter web release rescue worker helmet automatic remediation is available for this issue cve vulnerable library jackson databind jar general data binding functionality for jackson works on core streaming api library home page a href path to dependency file pom xml path to vulnerable library home wss scanner repository com fasterxml jackson core jackson databind jackson databind jar dependency hierarchy spring boot starter web release jar root library spring boot starter json release jar x jackson databind jar vulnerable library found in head commit a href found in base branch master vulnerability details subtypevalidator java in fasterxml jackson databind before mishandles default typing when ehcache is used because of net sf ehcache transaction manager defaulttransactionmanagerlookup leading to remote code execution publish date url a href cvss score details base score metrics exploitability metrics attack vector network attack complexity low privileges required none user interaction none scope unchanged impact metrics confidentiality impact high integrity impact high availability impact high for more information on scores click a href suggested fix type upgrade version origin a href release date fix resolution com fasterxml jackson core jackson databind direct dependency fix resolution org springframework boot spring boot starter web release rescue worker helmet automatic remediation is available for this issue cve vulnerable library jackson databind jar general data binding functionality for jackson works on core streaming api library home page a href path to dependency file pom xml path to vulnerable library home wss scanner repository com fasterxml jackson core jackson databind jackson databind jar dependency hierarchy spring boot starter web release jar root library spring boot starter json release jar x jackson databind jar vulnerable library found in head commit a href found in base branch master vulnerability details fasterxml jackson databind x before mishandles the interaction between serialization gadgets and typing related to com ibatis sqlmap engine transaction jta jtatransactionconfig aka ibatis sqlmap publish date url a href cvss score details base score metrics exploitability metrics attack vector network attack complexity low privileges required none user interaction none scope unchanged impact metrics confidentiality impact high integrity impact high availability impact high for more information on scores click a href suggested fix type upgrade version origin a href release date fix resolution com fasterxml jackson core jackson databind redhat direct dependency fix resolution org springframework boot spring boot starter web release rescue worker helmet automatic remediation is available for this issue cve vulnerable library jackson databind jar general data binding functionality for jackson works on core streaming api library home page a href path to dependency file pom xml path to vulnerable library home wss scanner repository com fasterxml jackson core jackson databind jackson databind jar dependency hierarchy spring boot starter web release jar root library spring boot starter json release jar x jackson databind jar vulnerable library found in head commit a href found in base branch master vulnerability details fasterxml jackson databind x before mishandles the interaction between serialization gadgets and typing related to br com anteros dbcp anterosdbcpconfig aka anteros core publish date url a href cvss score details base score metrics exploitability metrics attack vector network attack complexity low privileges required none user interaction none scope unchanged impact metrics confidentiality impact high integrity impact high availability impact high for more information on scores click a href suggested fix type upgrade version origin a href release date fix resolution com fasterxml jackson core jackson databind redhat direct dependency fix resolution org springframework boot spring boot starter web release rescue worker helmet automatic remediation is available for this issue cve vulnerable library jackson databind jar general data binding functionality for jackson works on core streaming api library home page a href path to dependency file pom xml path to vulnerable library home wss scanner repository com fasterxml jackson core jackson databind jackson databind jar dependency hierarchy spring boot starter web release jar root library spring boot starter json release jar x jackson databind jar vulnerable library found in head commit a href found in base branch master vulnerability details fasterxml jackson databind x before lacks certain net sf ehcache blocking publish date url a href cvss score details base score metrics exploitability metrics attack vector network attack complexity low privileges required none user interaction none scope unchanged impact metrics confidentiality impact high integrity impact high availability impact high for more information on scores click a href suggested fix type upgrade version release date fix resolution com fasterxml jackson core jackson databind redhat direct dependency fix resolution org springframework boot spring boot starter web release rescue worker helmet automatic remediation is available for this issue cve vulnerable library jackson databind jar general data binding functionality for jackson works on core streaming api library home page a href path to dependency file pom xml path to vulnerable library home wss scanner repository com fasterxml jackson core jackson databind jackson databind jar dependency hierarchy spring boot starter web release jar root library spring boot starter json release jar x jackson databind jar vulnerable library found in head commit a href found in base branch master vulnerability details fasterxml jackson databind x before mishandles the interaction between serialization gadgets and typing related to org aoju bus proxy provider remoting rmiprovider aka bus proxy publish date url a href cvss score details base score metrics exploitability metrics attack vector network attack complexity low privileges required none user interaction required scope unchanged impact metrics confidentiality impact high integrity impact high availability impact high for more information on scores click a href suggested fix type upgrade version origin a href release date fix resolution com fasterxml jackson core jackson databind redhat direct dependency fix resolution org springframework boot spring boot starter web release rescue worker helmet automatic remediation is available for this issue cve vulnerable library jackson databind jar general data binding functionality for jackson works on core streaming api library home page a href path to dependency file pom xml path to vulnerable library home wss scanner repository com fasterxml jackson core jackson databind jackson databind jar dependency hierarchy spring boot starter web release jar root library spring boot starter json release jar x jackson databind jar vulnerable library found in head commit a href found in base branch master vulnerability details fasterxml jackson databind x before mishandles the interaction between serialization gadgets and typing related to javax swing jeditorpane publish date url a href cvss score details base score metrics exploitability metrics attack vector network attack complexity low privileges required none user interaction required scope unchanged impact metrics confidentiality impact high integrity impact high availability impact high for more information on scores click a href suggested fix type upgrade version origin a href release date fix resolution com fasterxml jackson core jackson databind redhat direct dependency fix resolution org springframework boot spring boot starter web release rescue worker helmet automatic remediation is available for this issue cve vulnerable library jackson databind jar general data binding functionality for jackson works on core streaming api library home page a href path to dependency file pom xml path to vulnerable library home wss scanner repository com fasterxml jackson core jackson databind jackson databind jar dependency hierarchy spring boot starter web release jar root library spring boot starter json release jar x jackson databind jar vulnerable library found in head commit a href found in base branch master vulnerability details fasterxml jackson databind x before mishandles the interaction between serialization gadgets and typing related to org apache activemq aka activemq jms activemq core activemq pool and activemq pool jms publish date url a href cvss score details base score metrics exploitability metrics attack vector network attack complexity low privileges required none user interaction required scope unchanged impact metrics confidentiality impact high integrity impact high availability impact high for more information on scores click a href suggested fix type upgrade version origin a href release date fix resolution com fasterxml jackson core jackson databind redhat direct dependency fix resolution org springframework boot spring boot starter web release rescue worker helmet automatic remediation is available for this issue cve vulnerable library jackson databind jar general data binding functionality for jackson works on core streaming api library home page a href path to dependency file pom xml path to vulnerable library home wss scanner repository com fasterxml jackson core jackson databind jackson databind jar dependency hierarchy spring boot starter web release jar root library spring boot starter json release jar x jackson databind jar vulnerable library found in head commit a href found in base branch master vulnerability details fasterxml jackson databind x before mishandles the interaction between serialization gadgets and typing related to org apache openjpa ee wasregistrymanagedruntime aka openjpa publish date url a href cvss score details base score metrics exploitability metrics attack vector network attack complexity low privileges required none user interaction required scope unchanged impact metrics confidentiality impact high integrity impact high availability impact high for more information on scores click a href suggested fix type upgrade version origin a href release date fix resolution com fasterxml jackson core jackson databind redhat direct dependency fix resolution org springframework boot spring boot starter web release rescue worker helmet automatic remediation is available for this issue rescue worker helmet automatic remediation is available for this issue | 0 |
92,131 | 8,352,310,251 | IssuesEvent | 2018-10-02 05:46:10 | brave/brave-browser | https://api.github.com/repos/brave/brave-browser | closed | "Tor" label on private windows with Tor | QA/Test-Plan-Specified QA/Yes feature/tor | Instead of the people menu or the incognito hat-and-glasses, Tor windows should have the same simple "Tor" label as Muon tabs with Tor. | 1.0 | "Tor" label on private windows with Tor - Instead of the people menu or the incognito hat-and-glasses, Tor windows should have the same simple "Tor" label as Muon tabs with Tor. | non_priority | tor label on private windows with tor instead of the people menu or the incognito hat and glasses tor windows should have the same simple tor label as muon tabs with tor | 0 |
54,138 | 11,197,355,824 | IssuesEvent | 2020-01-03 13:02:57 | rubinera1n/blog | https://api.github.com/repos/rubinera1n/blog | opened | LeetCode-160-Intersection of Two Linked Lists | Algorithm LCT-Linked List LeetCode-Easy | ERROR: type should be string, got "https://leetcode.com/problems/intersection-of-two-linked-lists/description/\r\n\r\n* algorithms\r\n* Easy (32.92%)\r\n* Source Code: 160.intersection-of-two-linked-lists.py * Total Accepted: 288.9K\r\n* Total Submissions: 873.2K\r\n* Testcase Example: '8\\n[4,1,8,4,5]\\n[5,0,1,8,4,5]\\n2\\n3'\r\n\r\nWrite a program to find the node at which the intersection of two singly linked lists begins.\r\n\r\nFor example, the following two linked lists:\r\n\r\n\r\nbegin to intersect at node c1.\r\n\r\n\r\n\r\nExample 1:\r\n\r\n\r\n```\r\nInput: intersectVal = 8, listA = [4,1,8,4,5], listB = [5,0,1,8,4,5], skipA = 2, skipB = 3\r\nOutput: Reference of the node with value = 8\r\nInput Explanation: The intersected node's value is 8 (note that this must not be 0 if the two lists intersect). From the head of A, it reads as [4,1,8,4,5]. From the head of B, it reads as [5,0,1,8,4,5]. There are 2 nodes before the intersected node in A; There are 3 nodes before the intersected node in B.\r\n```\r\nExample 2:\r\n\r\n\r\n```\r\nInput: intersectVal = 2, listA = [0,9,1,2,4], listB = [3,2,4], skipA = 3, skipB = 1\r\nOutput: Reference of the node with value = 2\r\nInput Explanation: The intersected node's value is 2 (note that this must not be 0 if the two lists intersect). From the head of A, it reads as [0,9,1,2,4]. From the head of B, it reads as [3,2,4]. There are 3 nodes before the intersected node in A; There are 1 node before the intersected node in B.\r\n```\r\n\r\n\r\n\r\nExample 3:\r\n\r\n\r\n```\r\nInput: intersectVal = 0, listA = [2,6,4], listB = [1,5], skipA = 3, skipB = 2\r\nOutput: null\r\nInput Explanation: From the head of A, it reads as [2,6,4]. From the head of B, it reads as [1,5]. Since the two lists do not intersect, intersectVal must be 0, while skipA and skipB can be arbitrary values.\r\nExplanation: The two lists do not intersect, so return null.\r\n```\r\nNotes:\r\n- If the two linked lists have no intersection at all, return null.\r\n- The linked lists must retain their original structure after the function returns.\r\n- You may assume there are no cycles anywhere in the entire linked structure.\r\n- Your code should preferably run in O(n) time and use only O(1) memory.\r\n\r\n### C++\r\n```cpp\r\nclass Solution {\r\npublic:\r\n ListNode *getIntersectionNode(ListNode *headA, ListNode *headB) {\r\n ListNode *p, *q;\r\n\r\n p = headA;\r\n q = headB;\r\n\r\n int aCount = 0;\r\n int bCount = 0;\r\n\r\n while (p != nullptr) {\r\n ++aCount;\r\n p = p->next;\r\n }\r\n\r\n while (q != nullptr) {\r\n ++bCount;\r\n q = q->next;\r\n }\r\n\r\n p = headA;\r\n q = headB;\r\n\r\n if (aCount > bCount) {\r\n int diff = aCount - bCount;\r\n\r\n for (int i = 0;i < diff; ++i)\r\n p = p->next;\r\n }\r\n\r\n if (bCount > aCount) {\r\n int diff = bCount - aCount;\r\n\r\n for (int i = 0;i < diff; ++i)\r\n q = q->next;\r\n }\r\n\r\n while (p != nullptr && q != nullptr) {\r\n if (p == q)\r\n return p;\r\n\r\n p = p->next;\r\n q = q->next;\r\n }\r\n\r\n return nullptr;\r\n\r\n }\r\n};\r\n```\r\n\r\n### Python\r\n```python\r\nclass Solution:\r\n def getIntersectionNode(self, headA: ListNode, headB: ListNode) -> ListNode:\r\n stack1 = []\r\n stack2 = []\r\n while headA:\r\n stack1.append(headA)\r\n headA = headA.next\r\n while headB:\r\n stack2.append(headB)\r\n headB = headB.next\r\n pre = None\r\n while stack1 and stack2:\r\n if stack1[-1] is stack2.pop():\r\n pre = stack1.pop()\r\n else:\r\n return pre\r\n return pre\r\n```" | 1.0 | LeetCode-160-Intersection of Two Linked Lists - https://leetcode.com/problems/intersection-of-two-linked-lists/description/
* algorithms
* Easy (32.92%)
* Source Code: 160.intersection-of-two-linked-lists.py * Total Accepted: 288.9K
* Total Submissions: 873.2K
* Testcase Example: '8\n[4,1,8,4,5]\n[5,0,1,8,4,5]\n2\n3'
Write a program to find the node at which the intersection of two singly linked lists begins.
For example, the following two linked lists:
begin to intersect at node c1.
Example 1:
```
Input: intersectVal = 8, listA = [4,1,8,4,5], listB = [5,0,1,8,4,5], skipA = 2, skipB = 3
Output: Reference of the node with value = 8
Input Explanation: The intersected node's value is 8 (note that this must not be 0 if the two lists intersect). From the head of A, it reads as [4,1,8,4,5]. From the head of B, it reads as [5,0,1,8,4,5]. There are 2 nodes before the intersected node in A; There are 3 nodes before the intersected node in B.
```
Example 2:
```
Input: intersectVal = 2, listA = [0,9,1,2,4], listB = [3,2,4], skipA = 3, skipB = 1
Output: Reference of the node with value = 2
Input Explanation: The intersected node's value is 2 (note that this must not be 0 if the two lists intersect). From the head of A, it reads as [0,9,1,2,4]. From the head of B, it reads as [3,2,4]. There are 3 nodes before the intersected node in A; There are 1 node before the intersected node in B.
```
Example 3:
```
Input: intersectVal = 0, listA = [2,6,4], listB = [1,5], skipA = 3, skipB = 2
Output: null
Input Explanation: From the head of A, it reads as [2,6,4]. From the head of B, it reads as [1,5]. Since the two lists do not intersect, intersectVal must be 0, while skipA and skipB can be arbitrary values.
Explanation: The two lists do not intersect, so return null.
```
Notes:
- If the two linked lists have no intersection at all, return null.
- The linked lists must retain their original structure after the function returns.
- You may assume there are no cycles anywhere in the entire linked structure.
- Your code should preferably run in O(n) time and use only O(1) memory.
### C++
```cpp
class Solution {
public:
ListNode *getIntersectionNode(ListNode *headA, ListNode *headB) {
ListNode *p, *q;
p = headA;
q = headB;
int aCount = 0;
int bCount = 0;
while (p != nullptr) {
++aCount;
p = p->next;
}
while (q != nullptr) {
++bCount;
q = q->next;
}
p = headA;
q = headB;
if (aCount > bCount) {
int diff = aCount - bCount;
for (int i = 0;i < diff; ++i)
p = p->next;
}
if (bCount > aCount) {
int diff = bCount - aCount;
for (int i = 0;i < diff; ++i)
q = q->next;
}
while (p != nullptr && q != nullptr) {
if (p == q)
return p;
p = p->next;
q = q->next;
}
return nullptr;
}
};
```
### Python
```python
class Solution:
def getIntersectionNode(self, headA: ListNode, headB: ListNode) -> ListNode:
stack1 = []
stack2 = []
while headA:
stack1.append(headA)
headA = headA.next
while headB:
stack2.append(headB)
headB = headB.next
pre = None
while stack1 and stack2:
if stack1[-1] is stack2.pop():
pre = stack1.pop()
else:
return pre
return pre
``` | non_priority | leetcode intersection of two linked lists algorithms easy source code intersection of two linked lists py total accepted total submissions testcase example n n write a program to find the node at which the intersection of two singly linked lists begins for example the following two linked lists begin to intersect at node example input intersectval lista listb skipa skipb output reference of the node with value input explanation the intersected node s value is note that this must not be if the two lists intersect from the head of a it reads as from the head of b it reads as there are nodes before the intersected node in a there are nodes before the intersected node in b example input intersectval lista listb skipa skipb output reference of the node with value input explanation the intersected node s value is note that this must not be if the two lists intersect from the head of a it reads as from the head of b it reads as there are nodes before the intersected node in a there are node before the intersected node in b example input intersectval lista listb skipa skipb output null input explanation from the head of a it reads as from the head of b it reads as since the two lists do not intersect intersectval must be while skipa and skipb can be arbitrary values explanation the two lists do not intersect so return null notes if the two linked lists have no intersection at all return null the linked lists must retain their original structure after the function returns you may assume there are no cycles anywhere in the entire linked structure your code should preferably run in o n time and use only o memory c cpp class solution public listnode getintersectionnode listnode heada listnode headb listnode p q p heada q headb int acount int bcount while p nullptr acount p p next while q nullptr bcount q q next p heada q headb if acount bcount int diff acount bcount for int i i diff i p p next if bcount acount int diff bcount acount for int i i diff i q q next while p nullptr q nullptr if p q return p p p next q q next return nullptr python python class solution def getintersectionnode self heada listnode headb listnode listnode while heada append heada heada heada next while headb append headb headb headb next pre none while and if is pop pre pop else return pre return pre | 0 |
1,931 | 21,880,252,630 | IssuesEvent | 2022-05-19 13:47:54 | Azure/azure-sdk-for-java | https://api.github.com/repos/Azure/azure-sdk-for-java | closed | [BUG] Client loses connection with Event Hub and does not recover | question Event Hubs Client customer-reported pillar-reliability | **Describe the bug**
Suddenly, after a period of activity, a consumer client connected to the Event Hub loses connection and never recovers, even though keeps on running.
***Exception or Stack Trace***
```
01:25:26.986 INFO 1 --- [ctor-executor-3] c.a.c.a.i.handler.ReceiveLinkHandler : onLinkRemoteClose connectionId[MF_db4a99_1631152692131], linkName[1_5fce48_1631152692132], errorCondition[null], errorDescription[null]
01:25:26.986 INFO 1 --- [ctor-executor-3] c.a.c.a.i.handler.ReceiveLinkHandler : processOnClose connectionId[MF_db4a99_1631152692131], linkName[1_5fce48_1631152692132], errorCondition[null], errorDescription[null]
01:25:26.986 INFO 1 --- [ctor-executor-3] c.a.c.a.implementation.ReactorSession : linkName[1_5fce48_1631152692132] entityPath[yyyyyyy/ConsumerGroups/zzzzzz/Partitions/1]: Complete. Removing receive link.
01:25:26.986 INFO 1 --- [ctor-executor-3] c.a.m.e.i.AmqpReceiveLinkProcessor : Receive link endpoint states are closed. Requesting another.
01:25:26.986 INFO 1 --- [ctor-executor-3] c.a.m.e.i.AmqpReceiveLinkProcessor : Requesting a new AmqpReceiveLink from upstream.
01:25:26.987 INFO 1 --- [ctor-executor-3] c.a.m.e.i.AmqpReceiveLinkProcessor : linkName[1_5fce48_1631152692132] entityPath[yyyyyyy/ConsumerGroups/zzzzzz/Partitions/1]. Setting next AMQP receive link.
01:25:26.987 INFO 1 --- [ctor-executor-3] c.a.m.e.i.AmqpReceiveLinkProcessor : Receive link endpoint states are closed. Requesting another.
01:25:26.987 INFO 1 --- [ctor-executor-3] c.a.m.e.i.AmqpReceiveLinkProcessor : Requesting a new AmqpReceiveLink from upstream.
01:25:26.987 INFO 1 --- [ctor-executor-3] c.a.m.e.EventHubConsumerAsyncClient : connectionId[MF_db4a99_1631152692131] linkName[1_5fce48_1631152692132]: Creating receive consumer for partition '1'
01:25:26.988 INFO 1 --- [ctor-executor-3] c.a.c.a.i.handler.ReceiveLinkHandler : onLinkLocalClose connectionId[MF_db4a99_1631152692131], linkName[1_5fce48_1631152692132], errorCondition[null], errorDescription[null]
01:25:26.989 INFO 1 --- [ctor-executor-3] c.a.c.a.i.handler.ReceiveLinkHandler : onLinkFinal connectionId[MF_db4a99_1631152692131], linkName[1_5fce48_1631152692132]
01:25:26.989 INFO 1 --- [ctor-executor-3] c.a.c.a.i.handler.SessionHandler : onSessionRemoteClose connectionId[yyyyyyy/ConsumerGroups/zzzzzz/Partitions/1], entityName[MF_db4a99_1631152692131], condition[Error{condition=null, description='null', info=null}]
01:25:26.990 INFO 1 --- [ctor-executor-3] c.a.c.a.i.handler.SessionHandler : onSessionRemoteClose closing a local session for connectionId[MF_db4a99_1631152692131], entityName[yyyyyyy/ConsumerGroups/zzzzzz/Partitions/1], condition[null], description[null]
01:25:26.990 INFO 1 --- [ctor-executor-3] c.a.c.a.i.ReactorConnection : connectionId[MF_db4a99_1631152692131] sessionName[yyyyyyy/ConsumerGroups/zzzzzz/Partitions/1]: Error occurred. Removing and disposing session.
01:25:26.990 INFO 1 --- [ctor-executor-3] c.a.c.a.implementation.ReactorSession : connectionId[MF_db4a99_1631152692131], sessionId[yyyyyyy/ConsumerGroups/zzzzzz/Partitions/1], errorCondition[n/a]: Disposing of session.
01:25:26.990 INFO 1 --- [ctor-executor-3] c.a.c.a.i.handler.SendLinkHandler : onLinkRemoteClose connectionId[MF_db4a99_1631152692131], linkName[cbs:sender], errorCondition[null], errorDescription[null]
01:25:26.990 INFO 1 --- [ctor-executor-3] c.a.c.a.i.handler.SendLinkHandler : processOnClose connectionId[MF_db4a99_1631152692131], linkName[cbs:sender], errorCondition[null], errorDescription[null]
01:25:26.990 INFO 1 --- [ctor-executor-3] c.a.c.a.i.handler.ReceiveLinkHandler : onLinkRemoteClose connectionId[MF_db4a99_1631152692131], linkName[cbs:receiver], errorCondition[null], errorDescription[null]
01:25:26.990 INFO 1 --- [ctor-executor-3] c.a.c.a.i.handler.ReceiveLinkHandler : processOnClose connectionId[MF_db4a99_1631152692131], linkName[cbs:receiver], errorCondition[null], errorDescription[null]
01:25:26.990 INFO 1 --- [ctor-executor-3] c.a.c.a.i.handler.SessionHandler : onSessionRemoteClose connectionId[cbs-session], entityName[MF_db4a99_1631152692131], condition[Error{condition=null, description='null', info=null}]
01:25:26.990 INFO 1 --- [ctor-executor-3] c.a.c.a.i.handler.SessionHandler : onSessionRemoteClose closing a local session for connectionId[MF_db4a99_1631152692131], entityName[cbs-session], condition[null], description[null]
01:25:26.990 INFO 1 --- [ctor-executor-3] c.a.c.a.i.ReactorConnection : connectionId[MF_db4a99_1631152692131] sessionName[cbs-session]: Error occurred. Removing and disposing session.
01:25:26.990 INFO 1 --- [ctor-executor-3] c.a.c.a.implementation.ReactorSession : connectionId[MF_db4a99_1631152692131], sessionId[cbs-session], errorCondition[n/a]: Disposing of session.
01:25:26.990 INFO 1 --- [ctor-executor-3] c.a.c.a.i.handler.ConnectionHandler : onConnectionRemoteClose hostname[iothub-ns-xxxxxxxxx.servicebus.windows.net], connectionId[MF_db4a99_1631152692131], errorCondition[null], errorDescription[null]
01:25:26.991 INFO 1 --- [ctor-executor-3] c.a.c.a.i.handler.SendLinkHandler : onLinkLocalClose connectionId[MF_db4a99_1631152692131], linkName[cbs:sender], errorCondition[null], errorDescription[null]
01:25:26.991 INFO 1 --- [ctor-executor-3] c.a.c.a.i.handler.ReceiveLinkHandler : onLinkLocalClose connectionId[MF_db4a99_1631152692131], linkName[cbs:receiver], errorCondition[null], errorDescription[null]
01:25:26.991 INFO 1 --- [ctor-executor-3] c.a.c.a.i.handler.ConnectionHandler : onConnectionLocalClose hostname[iothub-ns-xxxxxxxxx.servicebus.windows.net], connectionId[MF_db4a99_1631152692131], errorCondition[null], errorDescription[null]
01:25:26.991 INFO 1 --- [ctor-executor-3] c.a.c.a.i.handler.ConnectionHandler : onConnectionUnbound hostname[iothub-ns-xxxxxxxxx.servicebus.windows.net], connectionId[MF_db4a99_1631152692131], state[CLOSED], remoteState[CLOSED]
01:25:26.991 INFO 1 --- [ctor-executor-3] c.a.c.a.i.handler.SessionHandler : onSessionFinal connectionId[MF_db4a99_1631152692131], entityName[yyyyyyy/ConsumerGroups/zzzzzz/Partitions/1], condition[null], description[null]
01:25:26.991 INFO 1 --- [ctor-executor-3] c.a.c.a.i.handler.SendLinkHandler : onLinkFinal connectionId[MF_db4a99_1631152692131], linkName[cbs:sender]
01:25:26.991 INFO 1 --- [ctor-executor-3] c.a.c.a.i.handler.ReceiveLinkHandler : onLinkFinal connectionId[MF_db4a99_1631152692131], linkName[cbs:receiver]
01:25:26.991 INFO 1 --- [ctor-executor-3] c.a.c.a.i.handler.SessionHandler : onSessionFinal connectionId[MF_db4a99_1631152692131], entityName[cbs-session], condition[null], description[null]
01:25:26.991 INFO 1 --- [ctor-executor-3] c.a.c.a.i.handler.ConnectionHandler : onConnectionFinal hostname[iothub-ns-xxxxxxxxx.servicebus.windows.net], connectionId[MF_db4a99_1631152692131], errorCondition[null], errorDescription[null]
01:25:26.994 INFO 1 --- [ctor-executor-3] c.a.m.e.i.EventHubConnectionProcessor : namespace[iothub-ns-xxxxxxxxx.servicebus.windows.net] entityPath[yyyyyyy]: Channel is closed.
01:25:26.994 INFO 1 --- [ctor-executor-3] c.a.m.e.i.EventHubReactorAmqpConnection : connectionId[MF_db4a99_1631152692131]: Disposing of connection.
01:25:26.994 INFO 1 --- [ctor-executor-3] c.a.c.a.i.ReactorConnection : connectionId[MF_db4a99_1631152692131], errorCondition[n/a]: Disposing of ReactorConnection.
...
01:26:26.994 INFO 1 --- [ctor-executor-3] c.a.c.a.implementation.ReactorExecutor : Unable to acquire dispose reactor semaphore within timeout.
01:26:26.994 INFO 1 --- [ctor-executor-3] c.a.c.a.i.AmqpExceptionHandler : Shutdown received: ReactorExecutor.close() was called., isTransient[false], initiatedByClient[true]
01:26:26.996 WARN 1 --- [ctor-executor-3] c.a.c.a.implementation.ReactorExecutor : connectionId[MF_db4a99_1631152692131], message[Scheduling reactor failed because the scheduler has been shut down.]
01:26:26.996 INFO 1 --- [ctor-executor-3] c.a.c.a.implementation.ReactorExecutor : connectionId[MF_db4a99_1631152692131], message[Stopping the reactor because thread was interrupted or the reactor has no more events to process.]
```
**To Reproduce**
It looks a random issue after a period of activity for some hours or days. It would be a big help to know how to produce that the event hub decides to closes the link, session and connection.
***Code Snippet***
It is the normal connection from examples:
BlobContainerAsyncClient blobContainerAsyncClient = new BlobContainerClientBuilder()
.connectionString(_STORAGE_CONNECTION_STRING_)
.containerName(_STORAGE_CONTAINER_NAME_)
.buildAsyncClient();
EventProcessorClientBuilder eventProcessorClientBuilder = new EventProcessorClientBuilder()
.connectionString(_EH_NAMESPACE_CONNECTION_STRING_)
.consumerGroup(_CONSUMERGROUP_NAME_)
.processEvent(_PARTITION_PROCESSOR_)
.processError(_ERROR_HANDLER_)
.checkpointStore(new BlobCheckpointStore(blobContainerAsyncClient));
**Expected behavior**
I would expect not to receive such events from the Event Hub (close of link, session and connection) and, if received, the client should recover opening a new connection. Or at least being able to manage this error. I would like also to have a description telling why the Event Hub decides to close the connection.
**Setup (please complete the following information):**
- OS: Linux RHEL
- Library/Libraries: com.azure:azure-messaging-eventhubs:5.5.0
- Java version: 8
- App Server/Environment: openjdk:8 docker base image
- Frameworks: Spring Boot
**Additional context**
It is actually the built-in Event Hub for the IoT Hub service.
**Information Checklist**
Kindly make sure that you have added all the following information above and checkoff the required fields otherwise we will treat the issuer as an incomplete report
- [X] Bug Description Added
- [X] Repro Steps Added
- [X] Setup information Added
| True | [BUG] Client loses connection with Event Hub and does not recover - **Describe the bug**
Suddenly, after a period of activity, a consumer client connected to the Event Hub loses connection and never recovers, even though keeps on running.
***Exception or Stack Trace***
```
01:25:26.986 INFO 1 --- [ctor-executor-3] c.a.c.a.i.handler.ReceiveLinkHandler : onLinkRemoteClose connectionId[MF_db4a99_1631152692131], linkName[1_5fce48_1631152692132], errorCondition[null], errorDescription[null]
01:25:26.986 INFO 1 --- [ctor-executor-3] c.a.c.a.i.handler.ReceiveLinkHandler : processOnClose connectionId[MF_db4a99_1631152692131], linkName[1_5fce48_1631152692132], errorCondition[null], errorDescription[null]
01:25:26.986 INFO 1 --- [ctor-executor-3] c.a.c.a.implementation.ReactorSession : linkName[1_5fce48_1631152692132] entityPath[yyyyyyy/ConsumerGroups/zzzzzz/Partitions/1]: Complete. Removing receive link.
01:25:26.986 INFO 1 --- [ctor-executor-3] c.a.m.e.i.AmqpReceiveLinkProcessor : Receive link endpoint states are closed. Requesting another.
01:25:26.986 INFO 1 --- [ctor-executor-3] c.a.m.e.i.AmqpReceiveLinkProcessor : Requesting a new AmqpReceiveLink from upstream.
01:25:26.987 INFO 1 --- [ctor-executor-3] c.a.m.e.i.AmqpReceiveLinkProcessor : linkName[1_5fce48_1631152692132] entityPath[yyyyyyy/ConsumerGroups/zzzzzz/Partitions/1]. Setting next AMQP receive link.
01:25:26.987 INFO 1 --- [ctor-executor-3] c.a.m.e.i.AmqpReceiveLinkProcessor : Receive link endpoint states are closed. Requesting another.
01:25:26.987 INFO 1 --- [ctor-executor-3] c.a.m.e.i.AmqpReceiveLinkProcessor : Requesting a new AmqpReceiveLink from upstream.
01:25:26.987 INFO 1 --- [ctor-executor-3] c.a.m.e.EventHubConsumerAsyncClient : connectionId[MF_db4a99_1631152692131] linkName[1_5fce48_1631152692132]: Creating receive consumer for partition '1'
01:25:26.988 INFO 1 --- [ctor-executor-3] c.a.c.a.i.handler.ReceiveLinkHandler : onLinkLocalClose connectionId[MF_db4a99_1631152692131], linkName[1_5fce48_1631152692132], errorCondition[null], errorDescription[null]
01:25:26.989 INFO 1 --- [ctor-executor-3] c.a.c.a.i.handler.ReceiveLinkHandler : onLinkFinal connectionId[MF_db4a99_1631152692131], linkName[1_5fce48_1631152692132]
01:25:26.989 INFO 1 --- [ctor-executor-3] c.a.c.a.i.handler.SessionHandler : onSessionRemoteClose connectionId[yyyyyyy/ConsumerGroups/zzzzzz/Partitions/1], entityName[MF_db4a99_1631152692131], condition[Error{condition=null, description='null', info=null}]
01:25:26.990 INFO 1 --- [ctor-executor-3] c.a.c.a.i.handler.SessionHandler : onSessionRemoteClose closing a local session for connectionId[MF_db4a99_1631152692131], entityName[yyyyyyy/ConsumerGroups/zzzzzz/Partitions/1], condition[null], description[null]
01:25:26.990 INFO 1 --- [ctor-executor-3] c.a.c.a.i.ReactorConnection : connectionId[MF_db4a99_1631152692131] sessionName[yyyyyyy/ConsumerGroups/zzzzzz/Partitions/1]: Error occurred. Removing and disposing session.
01:25:26.990 INFO 1 --- [ctor-executor-3] c.a.c.a.implementation.ReactorSession : connectionId[MF_db4a99_1631152692131], sessionId[yyyyyyy/ConsumerGroups/zzzzzz/Partitions/1], errorCondition[n/a]: Disposing of session.
01:25:26.990 INFO 1 --- [ctor-executor-3] c.a.c.a.i.handler.SendLinkHandler : onLinkRemoteClose connectionId[MF_db4a99_1631152692131], linkName[cbs:sender], errorCondition[null], errorDescription[null]
01:25:26.990 INFO 1 --- [ctor-executor-3] c.a.c.a.i.handler.SendLinkHandler : processOnClose connectionId[MF_db4a99_1631152692131], linkName[cbs:sender], errorCondition[null], errorDescription[null]
01:25:26.990 INFO 1 --- [ctor-executor-3] c.a.c.a.i.handler.ReceiveLinkHandler : onLinkRemoteClose connectionId[MF_db4a99_1631152692131], linkName[cbs:receiver], errorCondition[null], errorDescription[null]
01:25:26.990 INFO 1 --- [ctor-executor-3] c.a.c.a.i.handler.ReceiveLinkHandler : processOnClose connectionId[MF_db4a99_1631152692131], linkName[cbs:receiver], errorCondition[null], errorDescription[null]
01:25:26.990 INFO 1 --- [ctor-executor-3] c.a.c.a.i.handler.SessionHandler : onSessionRemoteClose connectionId[cbs-session], entityName[MF_db4a99_1631152692131], condition[Error{condition=null, description='null', info=null}]
01:25:26.990 INFO 1 --- [ctor-executor-3] c.a.c.a.i.handler.SessionHandler : onSessionRemoteClose closing a local session for connectionId[MF_db4a99_1631152692131], entityName[cbs-session], condition[null], description[null]
01:25:26.990 INFO 1 --- [ctor-executor-3] c.a.c.a.i.ReactorConnection : connectionId[MF_db4a99_1631152692131] sessionName[cbs-session]: Error occurred. Removing and disposing session.
01:25:26.990 INFO 1 --- [ctor-executor-3] c.a.c.a.implementation.ReactorSession : connectionId[MF_db4a99_1631152692131], sessionId[cbs-session], errorCondition[n/a]: Disposing of session.
01:25:26.990 INFO 1 --- [ctor-executor-3] c.a.c.a.i.handler.ConnectionHandler : onConnectionRemoteClose hostname[iothub-ns-xxxxxxxxx.servicebus.windows.net], connectionId[MF_db4a99_1631152692131], errorCondition[null], errorDescription[null]
01:25:26.991 INFO 1 --- [ctor-executor-3] c.a.c.a.i.handler.SendLinkHandler : onLinkLocalClose connectionId[MF_db4a99_1631152692131], linkName[cbs:sender], errorCondition[null], errorDescription[null]
01:25:26.991 INFO 1 --- [ctor-executor-3] c.a.c.a.i.handler.ReceiveLinkHandler : onLinkLocalClose connectionId[MF_db4a99_1631152692131], linkName[cbs:receiver], errorCondition[null], errorDescription[null]
01:25:26.991 INFO 1 --- [ctor-executor-3] c.a.c.a.i.handler.ConnectionHandler : onConnectionLocalClose hostname[iothub-ns-xxxxxxxxx.servicebus.windows.net], connectionId[MF_db4a99_1631152692131], errorCondition[null], errorDescription[null]
01:25:26.991 INFO 1 --- [ctor-executor-3] c.a.c.a.i.handler.ConnectionHandler : onConnectionUnbound hostname[iothub-ns-xxxxxxxxx.servicebus.windows.net], connectionId[MF_db4a99_1631152692131], state[CLOSED], remoteState[CLOSED]
01:25:26.991 INFO 1 --- [ctor-executor-3] c.a.c.a.i.handler.SessionHandler : onSessionFinal connectionId[MF_db4a99_1631152692131], entityName[yyyyyyy/ConsumerGroups/zzzzzz/Partitions/1], condition[null], description[null]
01:25:26.991 INFO 1 --- [ctor-executor-3] c.a.c.a.i.handler.SendLinkHandler : onLinkFinal connectionId[MF_db4a99_1631152692131], linkName[cbs:sender]
01:25:26.991 INFO 1 --- [ctor-executor-3] c.a.c.a.i.handler.ReceiveLinkHandler : onLinkFinal connectionId[MF_db4a99_1631152692131], linkName[cbs:receiver]
01:25:26.991 INFO 1 --- [ctor-executor-3] c.a.c.a.i.handler.SessionHandler : onSessionFinal connectionId[MF_db4a99_1631152692131], entityName[cbs-session], condition[null], description[null]
01:25:26.991 INFO 1 --- [ctor-executor-3] c.a.c.a.i.handler.ConnectionHandler : onConnectionFinal hostname[iothub-ns-xxxxxxxxx.servicebus.windows.net], connectionId[MF_db4a99_1631152692131], errorCondition[null], errorDescription[null]
01:25:26.994 INFO 1 --- [ctor-executor-3] c.a.m.e.i.EventHubConnectionProcessor : namespace[iothub-ns-xxxxxxxxx.servicebus.windows.net] entityPath[yyyyyyy]: Channel is closed.
01:25:26.994 INFO 1 --- [ctor-executor-3] c.a.m.e.i.EventHubReactorAmqpConnection : connectionId[MF_db4a99_1631152692131]: Disposing of connection.
01:25:26.994 INFO 1 --- [ctor-executor-3] c.a.c.a.i.ReactorConnection : connectionId[MF_db4a99_1631152692131], errorCondition[n/a]: Disposing of ReactorConnection.
...
01:26:26.994 INFO 1 --- [ctor-executor-3] c.a.c.a.implementation.ReactorExecutor : Unable to acquire dispose reactor semaphore within timeout.
01:26:26.994 INFO 1 --- [ctor-executor-3] c.a.c.a.i.AmqpExceptionHandler : Shutdown received: ReactorExecutor.close() was called., isTransient[false], initiatedByClient[true]
01:26:26.996 WARN 1 --- [ctor-executor-3] c.a.c.a.implementation.ReactorExecutor : connectionId[MF_db4a99_1631152692131], message[Scheduling reactor failed because the scheduler has been shut down.]
01:26:26.996 INFO 1 --- [ctor-executor-3] c.a.c.a.implementation.ReactorExecutor : connectionId[MF_db4a99_1631152692131], message[Stopping the reactor because thread was interrupted or the reactor has no more events to process.]
```
**To Reproduce**
It looks a random issue after a period of activity for some hours or days. It would be a big help to know how to produce that the event hub decides to closes the link, session and connection.
***Code Snippet***
It is the normal connection from examples:
BlobContainerAsyncClient blobContainerAsyncClient = new BlobContainerClientBuilder()
.connectionString(_STORAGE_CONNECTION_STRING_)
.containerName(_STORAGE_CONTAINER_NAME_)
.buildAsyncClient();
EventProcessorClientBuilder eventProcessorClientBuilder = new EventProcessorClientBuilder()
.connectionString(_EH_NAMESPACE_CONNECTION_STRING_)
.consumerGroup(_CONSUMERGROUP_NAME_)
.processEvent(_PARTITION_PROCESSOR_)
.processError(_ERROR_HANDLER_)
.checkpointStore(new BlobCheckpointStore(blobContainerAsyncClient));
**Expected behavior**
I would expect not to receive such events from the Event Hub (close of link, session and connection) and, if received, the client should recover opening a new connection. Or at least being able to manage this error. I would like also to have a description telling why the Event Hub decides to close the connection.
**Setup (please complete the following information):**
- OS: Linux RHEL
- Library/Libraries: com.azure:azure-messaging-eventhubs:5.5.0
- Java version: 8
- App Server/Environment: openjdk:8 docker base image
- Frameworks: Spring Boot
**Additional context**
It is actually the built-in Event Hub for the IoT Hub service.
**Information Checklist**
Kindly make sure that you have added all the following information above and checkoff the required fields otherwise we will treat the issuer as an incomplete report
- [X] Bug Description Added
- [X] Repro Steps Added
- [X] Setup information Added
| non_priority | client loses connection with event hub and does not recover describe the bug suddenly after a period of activity a consumer client connected to the event hub loses connection and never recovers even though keeps on running exception or stack trace info c a c a i handler receivelinkhandler onlinkremoteclose connectionid linkname errorcondition errordescription info c a c a i handler receivelinkhandler processonclose connectionid linkname errorcondition errordescription info c a c a implementation reactorsession linkname entitypath complete removing receive link info c a m e i amqpreceivelinkprocessor receive link endpoint states are closed requesting another info c a m e i amqpreceivelinkprocessor requesting a new amqpreceivelink from upstream info c a m e i amqpreceivelinkprocessor linkname entitypath setting next amqp receive link info c a m e i amqpreceivelinkprocessor receive link endpoint states are closed requesting another info c a m e i amqpreceivelinkprocessor requesting a new amqpreceivelink from upstream info c a m e eventhubconsumerasyncclient connectionid linkname creating receive consumer for partition info c a c a i handler receivelinkhandler onlinklocalclose connectionid linkname errorcondition errordescription info c a c a i handler receivelinkhandler onlinkfinal connectionid linkname info c a c a i handler sessionhandler onsessionremoteclose connectionid entityname condition info c a c a i handler sessionhandler onsessionremoteclose closing a local session for connectionid entityname condition description info c a c a i reactorconnection connectionid sessionname error occurred removing and disposing session info c a c a implementation reactorsession connectionid sessionid errorcondition disposing of session info c a c a i handler sendlinkhandler onlinkremoteclose connectionid linkname errorcondition errordescription info c a c a i handler sendlinkhandler processonclose connectionid linkname errorcondition errordescription info c a c a i handler receivelinkhandler onlinkremoteclose connectionid linkname errorcondition errordescription info c a c a i handler receivelinkhandler processonclose connectionid linkname errorcondition errordescription info c a c a i handler sessionhandler onsessionremoteclose connectionid entityname condition info c a c a i handler sessionhandler onsessionremoteclose closing a local session for connectionid entityname condition description info c a c a i reactorconnection connectionid sessionname error occurred removing and disposing session info c a c a implementation reactorsession connectionid sessionid errorcondition disposing of session info c a c a i handler connectionhandler onconnectionremoteclose hostname connectionid errorcondition errordescription info c a c a i handler sendlinkhandler onlinklocalclose connectionid linkname errorcondition errordescription info c a c a i handler receivelinkhandler onlinklocalclose connectionid linkname errorcondition errordescription info c a c a i handler connectionhandler onconnectionlocalclose hostname connectionid errorcondition errordescription info c a c a i handler connectionhandler onconnectionunbound hostname connectionid state remotestate info c a c a i handler sessionhandler onsessionfinal connectionid entityname condition description info c a c a i handler sendlinkhandler onlinkfinal connectionid linkname info c a c a i handler receivelinkhandler onlinkfinal connectionid linkname info c a c a i handler sessionhandler onsessionfinal connectionid entityname condition description info c a c a i handler connectionhandler onconnectionfinal hostname connectionid errorcondition errordescription info c a m e i eventhubconnectionprocessor namespace entitypath channel is closed info c a m e i eventhubreactoramqpconnection connectionid disposing of connection info c a c a i reactorconnection connectionid errorcondition disposing of reactorconnection info c a c a implementation reactorexecutor unable to acquire dispose reactor semaphore within timeout info c a c a i amqpexceptionhandler shutdown received reactorexecutor close was called istransient initiatedbyclient warn c a c a implementation reactorexecutor connectionid message info c a c a implementation reactorexecutor connectionid message to reproduce it looks a random issue after a period of activity for some hours or days it would be a big help to know how to produce that the event hub decides to closes the link session and connection code snippet it is the normal connection from examples blobcontainerasyncclient blobcontainerasyncclient new blobcontainerclientbuilder connectionstring storage connection string containername storage container name buildasyncclient eventprocessorclientbuilder eventprocessorclientbuilder new eventprocessorclientbuilder connectionstring eh namespace connection string consumergroup consumergroup name processevent partition processor processerror error handler checkpointstore new blobcheckpointstore blobcontainerasyncclient expected behavior i would expect not to receive such events from the event hub close of link session and connection and if received the client should recover opening a new connection or at least being able to manage this error i would like also to have a description telling why the event hub decides to close the connection setup please complete the following information os linux rhel library libraries com azure azure messaging eventhubs java version app server environment openjdk docker base image frameworks spring boot additional context it is actually the built in event hub for the iot hub service information checklist kindly make sure that you have added all the following information above and checkoff the required fields otherwise we will treat the issuer as an incomplete report bug description added repro steps added setup information added | 0 |
267,282 | 23,290,528,207 | IssuesEvent | 2022-08-05 22:06:09 | danbudris/vulnerabilityProcessor | https://api.github.com/repos/danbudris/vulnerabilityProcessor | opened | HIGH vulnerability CVE-2020-25648 - nss-sysinit, nss and 1 more affecting 1 resources | hey there test severity/HIGH | Issue auto cut by Vulnerability Processor
Processor Version: `v0.0.0-dev`
Message Source: `EventBridge`
Finding Source: `inspectorV2`
HIGH vulnerability CVE-2020-25648 detected in 1 resources
- arn:aws:ecr:us-west-2:338155784195:repository/test-inspector/sha256:7585bd31388fb7584260436e613c871868fd1509a728bf0c60bfe3f792e43aff
Affected Packages:
- nss-sysinit
- nss
- nss-tools
Associated Pull Requests:
- https://github.com/danbudris/vulnerabilityProcessor/pull/1145
| 1.0 | HIGH vulnerability CVE-2020-25648 - nss-sysinit, nss and 1 more affecting 1 resources - Issue auto cut by Vulnerability Processor
Processor Version: `v0.0.0-dev`
Message Source: `EventBridge`
Finding Source: `inspectorV2`
HIGH vulnerability CVE-2020-25648 detected in 1 resources
- arn:aws:ecr:us-west-2:338155784195:repository/test-inspector/sha256:7585bd31388fb7584260436e613c871868fd1509a728bf0c60bfe3f792e43aff
Affected Packages:
- nss-sysinit
- nss
- nss-tools
Associated Pull Requests:
- https://github.com/danbudris/vulnerabilityProcessor/pull/1145
| non_priority | high vulnerability cve nss sysinit nss and more affecting resources issue auto cut by vulnerability processor processor version dev message source eventbridge finding source high vulnerability cve detected in resources arn aws ecr us west repository test inspector affected packages nss sysinit nss nss tools associated pull requests | 0 |
261,501 | 22,747,618,965 | IssuesEvent | 2022-07-07 10:32:44 | zephyrproject-rtos/test_results | https://api.github.com/repos/zephyrproject-rtos/test_results | opened |
IPv4 Framing Receive RFC-1042 encapsulation. error
| area: Tests |
**Describe the bug**
Receive RFC-1042 encapsulation. test is Fail on Zephyr3.0.0 on qemu_x86
**References**
RFC 1122: section 2.3.3 {Receive RFC-1042 encapsulation}
RFC 1122: section 2.3.3 {Send K1=6 encapsulation}
**Results**
FAIL: icmp.v4 returned "No echo response", which is not an expected result.
**Environment (please complete the following information):**
- OS: (e.g. Linux )
- Toolchain (e.g Zephyr SDK)
- Commit SHA or Version used: Zephyr3.0.0
| 1.0 |
IPv4 Framing Receive RFC-1042 encapsulation. error
-
**Describe the bug**
Receive RFC-1042 encapsulation. test is Fail on Zephyr3.0.0 on qemu_x86
**References**
RFC 1122: section 2.3.3 {Receive RFC-1042 encapsulation}
RFC 1122: section 2.3.3 {Send K1=6 encapsulation}
**Results**
FAIL: icmp.v4 returned "No echo response", which is not an expected result.
**Environment (please complete the following information):**
- OS: (e.g. Linux )
- Toolchain (e.g Zephyr SDK)
- Commit SHA or Version used: Zephyr3.0.0
| non_priority | framing receive rfc encapsulation error describe the bug receive rfc encapsulation test is fail on on qemu references rfc section receive rfc encapsulation rfc section send encapsulation results fail icmp returned no echo response which is not an expected result environment please complete the following information os e g linux toolchain e g zephyr sdk commit sha or version used | 0 |
135,823 | 12,691,901,120 | IssuesEvent | 2020-06-21 19:26:55 | Rickecr/PyElit | https://api.github.com/repos/Rickecr/PyElit | closed | Adicionar o CONTRIBUTING.md | documentation help wanted | Esse arquivo será útil para novos desenvolvedores que desejem contribuir no projeto ou até mesmo entender o funcionamento para usar em seu projeto específico. | 1.0 | Adicionar o CONTRIBUTING.md - Esse arquivo será útil para novos desenvolvedores que desejem contribuir no projeto ou até mesmo entender o funcionamento para usar em seu projeto específico. | non_priority | adicionar o contributing md esse arquivo será útil para novos desenvolvedores que desejem contribuir no projeto ou até mesmo entender o funcionamento para usar em seu projeto específico | 0 |
26,862 | 11,410,630,333 | IssuesEvent | 2020-02-01 00:12:06 | Azure/iotedge | https://api.github.com/repos/Azure/iotedge | closed | Increasing auto_generated_ca_lifetime_days dosn't work in release 1.0.9RC4 | area:security needinfo | Hi Team,
I am using the default certificate generated by the Edge runtime. And I want to increase the expiry date for that certificate as it is default 90 days only. So I have read in the release that you have given feature their to add the days in the expiry and I did the same but it doesn't work.
So could you tell me how to use in the config.yml file. I have used it like given below and when I see the logs then it is still showing 90 days expiry in the edgeHub logs.
certificates:
# device_ca_cert: "<ADD URI TO DEVICE CA CERTIFICATE HERE>"
# device_ca_pk: "<ADD URI TO DEVICE CA PRIVATE KEY HERE>"
# trusted_ca_certs: "<ADD URI TO TRUSTED CA CERTIFICATES HERE>"
auto_generated_ca_lifetime_days: 1000
| True | Increasing auto_generated_ca_lifetime_days dosn't work in release 1.0.9RC4 - Hi Team,
I am using the default certificate generated by the Edge runtime. And I want to increase the expiry date for that certificate as it is default 90 days only. So I have read in the release that you have given feature their to add the days in the expiry and I did the same but it doesn't work.
So could you tell me how to use in the config.yml file. I have used it like given below and when I see the logs then it is still showing 90 days expiry in the edgeHub logs.
certificates:
# device_ca_cert: "<ADD URI TO DEVICE CA CERTIFICATE HERE>"
# device_ca_pk: "<ADD URI TO DEVICE CA PRIVATE KEY HERE>"
# trusted_ca_certs: "<ADD URI TO TRUSTED CA CERTIFICATES HERE>"
auto_generated_ca_lifetime_days: 1000
| non_priority | increasing auto generated ca lifetime days dosn t work in release hi team i am using the default certificate generated by the edge runtime and i want to increase the expiry date for that certificate as it is default days only so i have read in the release that you have given feature their to add the days in the expiry and i did the same but it doesn t work so could you tell me how to use in the config yml file i have used it like given below and when i see the logs then it is still showing days expiry in the edgehub logs certificates device ca cert device ca pk trusted ca certs auto generated ca lifetime days | 0 |
358,149 | 25,179,155,659 | IssuesEvent | 2022-11-11 12:03:27 | savushkin-r-d/ptusa_main | https://api.github.com/repos/savushkin-r-d/ptusa_main | closed | Описать архитектуру системы | documentation | В общем виде описать как работает система - основные компоненты, протоколы и т.п. | 1.0 | Описать архитектуру системы - В общем виде описать как работает система - основные компоненты, протоколы и т.п. | non_priority | описать архитектуру системы в общем виде описать как работает система основные компоненты протоколы и т п | 0 |
205,762 | 23,357,305,480 | IssuesEvent | 2022-08-10 08:35:44 | Gal-Doron/Baragon | https://api.github.com/repos/Gal-Doron/Baragon | opened | CVE-2020-13956 (Medium) detected in httpclient-4.5.5.jar | security vulnerability | ## CVE-2020-13956 - Medium Severity Vulnerability
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Library - <b>httpclient-4.5.5.jar</b></p></summary>
<p>Apache HttpComponents Client</p>
<p>Path to dependency file: /BaragonServiceIntegrationTests/pom.xml</p>
<p>Path to vulnerable library: /home/wss-scanner/.m2/repository/org/apache/httpcomponents/httpclient/4.5.5/httpclient-4.5.5.jar,/home/wss-scanner/.m2/repository/org/apache/httpcomponents/httpclient/4.5.5/httpclient-4.5.5.jar,/home/wss-scanner/.m2/repository/org/apache/httpcomponents/httpclient/4.5.5/httpclient-4.5.5.jar,/home/wss-scanner/.m2/repository/org/apache/httpcomponents/httpclient/4.5.5/httpclient-4.5.5.jar,/home/wss-scanner/.m2/repository/org/apache/httpcomponents/httpclient/4.5.5/httpclient-4.5.5.jar,/home/wss-scanner/.m2/repository/org/apache/httpcomponents/httpclient/4.5.5/httpclient-4.5.5.jar,/home/wss-scanner/.m2/repository/org/apache/httpcomponents/httpclient/4.5.5/httpclient-4.5.5.jar</p>
<p>
Dependency Hierarchy:
- aws-java-sdk-core-1.11.497.jar (Root Library)
- :x: **httpclient-4.5.5.jar** (Vulnerable Library)
<p>Found in HEAD commit: <a href="https://github.com/Gal-Doron/Baragon/commit/0c8c20a56ba1202331e3630a50a3a82dc3b881fe">0c8c20a56ba1202331e3630a50a3a82dc3b881fe</a></p>
<p>Found in base branch: <b>master</b></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/medium_vul.png' width=19 height=20> Vulnerability Details</summary>
<p>
Apache HttpClient versions prior to version 4.5.13 and 5.0.3 can misinterpret malformed authority component in request URIs passed to the library as java.net.URI object and pick the wrong target host for request execution.
<p>Publish Date: 2020-12-02
<p>URL: <a href=https://vuln.whitesourcesoftware.com/vulnerability/CVE-2020-13956>CVE-2020-13956</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/cvss3.png' width=19 height=20> CVSS 3 Score Details (<b>5.3</b>)</summary>
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: None
- Integrity Impact: Low
- Availability Impact: None
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/suggested_fix.png' width=19 height=20> Suggested Fix</summary>
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://bugzilla.redhat.com/show_bug.cgi?id=CVE-2020-13956">https://bugzilla.redhat.com/show_bug.cgi?id=CVE-2020-13956</a></p>
<p>Release Date: 2020-12-02</p>
<p>Fix Resolution (org.apache.httpcomponents:httpclient): 4.5.13</p>
<p>Direct dependency fix Resolution (com.amazonaws:aws-java-sdk-core): 1.11.893</p>
</p>
</details>
<p></p>
***
:rescue_worker_helmet: Automatic Remediation is available for this issue | True | CVE-2020-13956 (Medium) detected in httpclient-4.5.5.jar - ## CVE-2020-13956 - Medium Severity Vulnerability
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Library - <b>httpclient-4.5.5.jar</b></p></summary>
<p>Apache HttpComponents Client</p>
<p>Path to dependency file: /BaragonServiceIntegrationTests/pom.xml</p>
<p>Path to vulnerable library: /home/wss-scanner/.m2/repository/org/apache/httpcomponents/httpclient/4.5.5/httpclient-4.5.5.jar,/home/wss-scanner/.m2/repository/org/apache/httpcomponents/httpclient/4.5.5/httpclient-4.5.5.jar,/home/wss-scanner/.m2/repository/org/apache/httpcomponents/httpclient/4.5.5/httpclient-4.5.5.jar,/home/wss-scanner/.m2/repository/org/apache/httpcomponents/httpclient/4.5.5/httpclient-4.5.5.jar,/home/wss-scanner/.m2/repository/org/apache/httpcomponents/httpclient/4.5.5/httpclient-4.5.5.jar,/home/wss-scanner/.m2/repository/org/apache/httpcomponents/httpclient/4.5.5/httpclient-4.5.5.jar,/home/wss-scanner/.m2/repository/org/apache/httpcomponents/httpclient/4.5.5/httpclient-4.5.5.jar</p>
<p>
Dependency Hierarchy:
- aws-java-sdk-core-1.11.497.jar (Root Library)
- :x: **httpclient-4.5.5.jar** (Vulnerable Library)
<p>Found in HEAD commit: <a href="https://github.com/Gal-Doron/Baragon/commit/0c8c20a56ba1202331e3630a50a3a82dc3b881fe">0c8c20a56ba1202331e3630a50a3a82dc3b881fe</a></p>
<p>Found in base branch: <b>master</b></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/medium_vul.png' width=19 height=20> Vulnerability Details</summary>
<p>
Apache HttpClient versions prior to version 4.5.13 and 5.0.3 can misinterpret malformed authority component in request URIs passed to the library as java.net.URI object and pick the wrong target host for request execution.
<p>Publish Date: 2020-12-02
<p>URL: <a href=https://vuln.whitesourcesoftware.com/vulnerability/CVE-2020-13956>CVE-2020-13956</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/cvss3.png' width=19 height=20> CVSS 3 Score Details (<b>5.3</b>)</summary>
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: None
- Integrity Impact: Low
- Availability Impact: None
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/suggested_fix.png' width=19 height=20> Suggested Fix</summary>
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://bugzilla.redhat.com/show_bug.cgi?id=CVE-2020-13956">https://bugzilla.redhat.com/show_bug.cgi?id=CVE-2020-13956</a></p>
<p>Release Date: 2020-12-02</p>
<p>Fix Resolution (org.apache.httpcomponents:httpclient): 4.5.13</p>
<p>Direct dependency fix Resolution (com.amazonaws:aws-java-sdk-core): 1.11.893</p>
</p>
</details>
<p></p>
***
:rescue_worker_helmet: Automatic Remediation is available for this issue | non_priority | cve medium detected in httpclient jar cve medium severity vulnerability vulnerable library httpclient jar apache httpcomponents client path to dependency file baragonserviceintegrationtests pom xml path to vulnerable library home wss scanner repository org apache httpcomponents httpclient httpclient jar home wss scanner repository org apache httpcomponents httpclient httpclient jar home wss scanner repository org apache httpcomponents httpclient httpclient jar home wss scanner repository org apache httpcomponents httpclient httpclient jar home wss scanner repository org apache httpcomponents httpclient httpclient jar home wss scanner repository org apache httpcomponents httpclient httpclient jar home wss scanner repository org apache httpcomponents httpclient httpclient jar dependency hierarchy aws java sdk core jar root library x httpclient jar vulnerable library found in head commit a href found in base branch master vulnerability details apache httpclient versions prior to version and can misinterpret malformed authority component in request uris passed to the library as java net uri object and pick the wrong target host for request execution publish date url a href cvss score details base score metrics exploitability metrics attack vector network attack complexity low privileges required none user interaction none scope unchanged impact metrics confidentiality impact none integrity impact low availability impact none for more information on scores click a href suggested fix type upgrade version origin a href release date fix resolution org apache httpcomponents httpclient direct dependency fix resolution com amazonaws aws java sdk core rescue worker helmet automatic remediation is available for this issue | 0 |
201,194 | 15,802,021,808 | IssuesEvent | 2021-04-03 07:39:08 | rachelljt/ped | https://api.github.com/repos/rachelljt/ped | opened | typos in UG | severity.VeryLow type.DocumentationBug |

Small issue here but i realised there were many instances of address book being mentioned. I think it would be best to change to Module Planner which is the name of the app.
<!--session: 1617435104577-1eaf30cc-d705-4441-bbe1-396c90e57a7c--> | 1.0 | typos in UG -

Small issue here but i realised there were many instances of address book being mentioned. I think it would be best to change to Module Planner which is the name of the app.
<!--session: 1617435104577-1eaf30cc-d705-4441-bbe1-396c90e57a7c--> | non_priority | typos in ug small issue here but i realised there were many instances of address book being mentioned i think it would be best to change to module planner which is the name of the app | 0 |
96,745 | 16,164,581,678 | IssuesEvent | 2021-05-01 08:16:05 | AlexRogalskiy/github-action-random-proverb | https://api.github.com/repos/AlexRogalskiy/github-action-random-proverb | opened | WS-2020-0218 (High) detected in merge-1.2.1.tgz | security vulnerability | ## WS-2020-0218 - High Severity Vulnerability
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Library - <b>merge-1.2.1.tgz</b></p></summary>
<p>Merge multiple objects into one, optionally creating a new cloned object. Similar to the jQuery.extend but more flexible. Works in Node.js and the browser.</p>
<p>Library home page: <a href="https://registry.npmjs.org/merge/-/merge-1.2.1.tgz">https://registry.npmjs.org/merge/-/merge-1.2.1.tgz</a></p>
<p>Path to dependency file: github-action-random-proverb/package.json</p>
<p>Path to vulnerable library: github-action-random-proverb/node_modules/merge/package.json</p>
<p>
Dependency Hierarchy:
- cz-conventional-changelog-3.3.0.tgz (Root Library)
- commitizen-4.2.3.tgz
- find-node-modules-2.0.0.tgz
- :x: **merge-1.2.1.tgz** (Vulnerable Library)
<p>Found in HEAD commit: <a href="https://github.com/AlexRogalskiy/github-action-random-proverb/commit/d7edbd8ba39391c25a2b5e766d006c3de936474b">d7edbd8ba39391c25a2b5e766d006c3de936474b</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> Vulnerability Details</summary>
<p>
A Prototype Pollution vulnerability was found in merge before 2.1.0 via the merge.recursive function. It can be tricked into adding or modifying properties of the Object prototype. These properties will be present on all objects.
<p>Publish Date: 2020-10-09
<p>URL: <a href=https://github.com/yeikos/js.merge/pull/38>WS-2020-0218</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/cvss3.png' width=19 height=20> CVSS 3 Score Details (<b>7.5</b>)</summary>
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: None
- Integrity Impact: None
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/suggested_fix.png' width=19 height=20> Suggested Fix</summary>
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://github.com/yeikos/js.merge/pull/38">https://github.com/yeikos/js.merge/pull/38</a></p>
<p>Release Date: 2020-10-09</p>
<p>Fix Resolution: merge - 2.1.0</p>
</p>
</details>
<p></p>
***
Step up your Open Source Security Game with WhiteSource [here](https://www.whitesourcesoftware.com/full_solution_bolt_github) | True | WS-2020-0218 (High) detected in merge-1.2.1.tgz - ## WS-2020-0218 - High Severity Vulnerability
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Library - <b>merge-1.2.1.tgz</b></p></summary>
<p>Merge multiple objects into one, optionally creating a new cloned object. Similar to the jQuery.extend but more flexible. Works in Node.js and the browser.</p>
<p>Library home page: <a href="https://registry.npmjs.org/merge/-/merge-1.2.1.tgz">https://registry.npmjs.org/merge/-/merge-1.2.1.tgz</a></p>
<p>Path to dependency file: github-action-random-proverb/package.json</p>
<p>Path to vulnerable library: github-action-random-proverb/node_modules/merge/package.json</p>
<p>
Dependency Hierarchy:
- cz-conventional-changelog-3.3.0.tgz (Root Library)
- commitizen-4.2.3.tgz
- find-node-modules-2.0.0.tgz
- :x: **merge-1.2.1.tgz** (Vulnerable Library)
<p>Found in HEAD commit: <a href="https://github.com/AlexRogalskiy/github-action-random-proverb/commit/d7edbd8ba39391c25a2b5e766d006c3de936474b">d7edbd8ba39391c25a2b5e766d006c3de936474b</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> Vulnerability Details</summary>
<p>
A Prototype Pollution vulnerability was found in merge before 2.1.0 via the merge.recursive function. It can be tricked into adding or modifying properties of the Object prototype. These properties will be present on all objects.
<p>Publish Date: 2020-10-09
<p>URL: <a href=https://github.com/yeikos/js.merge/pull/38>WS-2020-0218</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/cvss3.png' width=19 height=20> CVSS 3 Score Details (<b>7.5</b>)</summary>
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: None
- Integrity Impact: None
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/suggested_fix.png' width=19 height=20> Suggested Fix</summary>
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://github.com/yeikos/js.merge/pull/38">https://github.com/yeikos/js.merge/pull/38</a></p>
<p>Release Date: 2020-10-09</p>
<p>Fix Resolution: merge - 2.1.0</p>
</p>
</details>
<p></p>
***
Step up your Open Source Security Game with WhiteSource [here](https://www.whitesourcesoftware.com/full_solution_bolt_github) | non_priority | ws high detected in merge tgz ws high severity vulnerability vulnerable library merge tgz merge multiple objects into one optionally creating a new cloned object similar to the jquery extend but more flexible works in node js and the browser library home page a href path to dependency file github action random proverb package json path to vulnerable library github action random proverb node modules merge package json dependency hierarchy cz conventional changelog tgz root library commitizen tgz find node modules tgz x merge tgz vulnerable library found in head commit a href vulnerability details a prototype pollution vulnerability was found in merge before via the merge recursive function it can be tricked into adding or modifying properties of the object prototype these properties will be present on all objects publish date url a href cvss score details base score metrics exploitability metrics attack vector network attack complexity low privileges required none user interaction none scope unchanged impact metrics confidentiality impact none integrity impact none availability impact high for more information on scores click a href suggested fix type upgrade version origin a href release date fix resolution merge step up your open source security game with whitesource | 0 |
118,569 | 9,995,230,559 | IssuesEvent | 2019-07-11 19:43:09 | warfare-plugins/social-warfare | https://api.github.com/repos/warfare-plugins/social-warfare | closed | Metabox SM images need to show in the previews in post editor. | READY FOR TESTING | When a user saves their post, the social media images are not showing up in the post editor. Sometimes updating the post will set them back to how they should be. | 1.0 | Metabox SM images need to show in the previews in post editor. - When a user saves their post, the social media images are not showing up in the post editor. Sometimes updating the post will set them back to how they should be. | non_priority | metabox sm images need to show in the previews in post editor when a user saves their post the social media images are not showing up in the post editor sometimes updating the post will set them back to how they should be | 0 |
62,968 | 14,656,652,317 | IssuesEvent | 2020-12-28 13:54:19 | fu1771695yongxie/node | https://api.github.com/repos/fu1771695yongxie/node | opened | CVE-2019-19919 (High) detected in handlebars-4.0.11.tgz | security vulnerability | ## CVE-2019-19919 - High Severity Vulnerability
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Library - <b>handlebars-4.0.11.tgz</b></p></summary>
<p>Handlebars provides the power necessary to let you build semantic templates effectively with no frustration</p>
<p>Library home page: <a href="https://registry.npmjs.org/handlebars/-/handlebars-4.0.11.tgz">https://registry.npmjs.org/handlebars/-/handlebars-4.0.11.tgz</a></p>
<p>Path to dependency file: node/deps/node-inspect/package.json</p>
<p>Path to vulnerable library: node/deps/node-inspect/node_modules/nyc/node_modules/handlebars/package.json</p>
<p>
Dependency Hierarchy:
- tap-10.7.3.tgz (Root Library)
- nyc-11.9.0.tgz
- istanbul-reports-1.4.0.tgz
- :x: **handlebars-4.0.11.tgz** (Vulnerable Library)
<p>Found in HEAD commit: <a href="https://github.com/fu1771695yongxie/node/commit/e8880d405b1130ab16334d72a55c6c02d0575609">e8880d405b1130ab16334d72a55c6c02d0575609</a></p>
<p>Found in base branch: <b>master</b></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> Vulnerability Details</summary>
<p>
Versions of handlebars prior to 4.3.0 are vulnerable to Prototype Pollution leading to Remote Code Execution. Templates may alter an Object's __proto__ and __defineGetter__ properties, which may allow an attacker to execute arbitrary code through crafted payloads.
<p>Publish Date: 2019-12-20
<p>URL: <a href=https://vuln.whitesourcesoftware.com/vulnerability/CVE-2019-19919>CVE-2019-19919</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/cvss3.png' width=19 height=20> CVSS 3 Score Details (<b>9.8</b>)</summary>
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: High
- Integrity Impact: High
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/suggested_fix.png' width=19 height=20> Suggested Fix</summary>
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://www.npmjs.com/advisories/1164">https://www.npmjs.com/advisories/1164</a></p>
<p>Release Date: 2019-12-20</p>
<p>Fix Resolution: 4.3.0</p>
</p>
</details>
<p></p>
***
Step up your Open Source Security Game with WhiteSource [here](https://www.whitesourcesoftware.com/full_solution_bolt_github) | True | CVE-2019-19919 (High) detected in handlebars-4.0.11.tgz - ## CVE-2019-19919 - High Severity Vulnerability
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Library - <b>handlebars-4.0.11.tgz</b></p></summary>
<p>Handlebars provides the power necessary to let you build semantic templates effectively with no frustration</p>
<p>Library home page: <a href="https://registry.npmjs.org/handlebars/-/handlebars-4.0.11.tgz">https://registry.npmjs.org/handlebars/-/handlebars-4.0.11.tgz</a></p>
<p>Path to dependency file: node/deps/node-inspect/package.json</p>
<p>Path to vulnerable library: node/deps/node-inspect/node_modules/nyc/node_modules/handlebars/package.json</p>
<p>
Dependency Hierarchy:
- tap-10.7.3.tgz (Root Library)
- nyc-11.9.0.tgz
- istanbul-reports-1.4.0.tgz
- :x: **handlebars-4.0.11.tgz** (Vulnerable Library)
<p>Found in HEAD commit: <a href="https://github.com/fu1771695yongxie/node/commit/e8880d405b1130ab16334d72a55c6c02d0575609">e8880d405b1130ab16334d72a55c6c02d0575609</a></p>
<p>Found in base branch: <b>master</b></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> Vulnerability Details</summary>
<p>
Versions of handlebars prior to 4.3.0 are vulnerable to Prototype Pollution leading to Remote Code Execution. Templates may alter an Object's __proto__ and __defineGetter__ properties, which may allow an attacker to execute arbitrary code through crafted payloads.
<p>Publish Date: 2019-12-20
<p>URL: <a href=https://vuln.whitesourcesoftware.com/vulnerability/CVE-2019-19919>CVE-2019-19919</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/cvss3.png' width=19 height=20> CVSS 3 Score Details (<b>9.8</b>)</summary>
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: High
- Integrity Impact: High
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/suggested_fix.png' width=19 height=20> Suggested Fix</summary>
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://www.npmjs.com/advisories/1164">https://www.npmjs.com/advisories/1164</a></p>
<p>Release Date: 2019-12-20</p>
<p>Fix Resolution: 4.3.0</p>
</p>
</details>
<p></p>
***
Step up your Open Source Security Game with WhiteSource [here](https://www.whitesourcesoftware.com/full_solution_bolt_github) | non_priority | cve high detected in handlebars tgz cve high severity vulnerability vulnerable library handlebars tgz handlebars provides the power necessary to let you build semantic templates effectively with no frustration library home page a href path to dependency file node deps node inspect package json path to vulnerable library node deps node inspect node modules nyc node modules handlebars package json dependency hierarchy tap tgz root library nyc tgz istanbul reports tgz x handlebars tgz vulnerable library found in head commit a href found in base branch master vulnerability details versions of handlebars prior to are vulnerable to prototype pollution leading to remote code execution templates may alter an object s proto and definegetter properties which may allow an attacker to execute arbitrary code through crafted payloads publish date url a href cvss score details base score metrics exploitability metrics attack vector network attack complexity low privileges required none user interaction none scope unchanged impact metrics confidentiality impact high integrity impact high availability impact high for more information on scores click a href suggested fix type upgrade version origin a href release date fix resolution step up your open source security game with whitesource | 0 |
250,541 | 27,099,555,065 | IssuesEvent | 2023-02-15 07:25:25 | rsoreq/django-DefectDojo | https://api.github.com/repos/rsoreq/django-DefectDojo | opened | CVE-2023-0286 (High) detected in cryptography-3.2.1-cp27-cp27mu-manylinux2010_x86_64.whl | security vulnerability | ## CVE-2023-0286 - High Severity Vulnerability
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Library - <b>cryptography-3.2.1-cp27-cp27mu-manylinux2010_x86_64.whl</b></p></summary>
<p>cryptography is a package which provides cryptographic recipes and primitives to Python developers.</p>
<p>Library home page: <a href="https://files.pythonhosted.org/packages/08/ef/e98bc93bfa2527cb954efde5f3c7538a40fe0e7a2e55d68707783fcdab5d/cryptography-3.2.1-cp27-cp27mu-manylinux2010_x86_64.whl">https://files.pythonhosted.org/packages/08/ef/e98bc93bfa2527cb954efde5f3c7538a40fe0e7a2e55d68707783fcdab5d/cryptography-3.2.1-cp27-cp27mu-manylinux2010_x86_64.whl</a></p>
<p>Path to dependency file: /tmp/ws-scm/django-DefectDojo</p>
<p>Path to vulnerable library: /django-DefectDojo,/requirements.txt</p>
<p>
Dependency Hierarchy:
- :x: **cryptography-3.2.1-cp27-cp27mu-manylinux2010_x86_64.whl** (Vulnerable Library)
<p>Found in HEAD commit: <a href="https://github.com/rsoreq/django-DefectDojo/commit/778bcf0b3400f30c71d722f50e221c2eec64ea95">778bcf0b3400f30c71d722f50e221c2eec64ea95</a></p>
<p>Found in base branch: <b>master</b></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> Vulnerability Details</summary>
<p>
There is a type confusion vulnerability relating to X.400 address processing inside an X.509 GeneralName. X.400 addresses were parsed as an ASN1_STRING but the public structure definition for GENERAL_NAME incorrectly specified the type of the x400Address field as ASN1_TYPE. This field is subsequently interpreted by the OpenSSL function GENERAL_NAME_cmp as an ASN1_TYPE rather than an ASN1_STRING. When CRL checking is enabled (i.e. the application sets the X509_V_FLAG_CRL_CHECK flag), this vulnerability may allow an attacker to pass arbitrary pointers to a memcmp call, enabling them to read memory contents or enact a denial of service. In most cases, the attack requires the attacker to provide both the certificate chain and CRL, neither of which need to have a valid signature. If the attacker only controls one of these inputs, the other input must already contain an X.400 address as a CRL distribution point, which is uncommon. As such, this vulnerability is most likely to only affect applications which have implemented their own functionality for retrieving CRLs over a network.
<p>Publish Date: 2023-02-08
<p>URL: <a href=https://www.mend.io/vulnerability-database/CVE-2023-0286>CVE-2023-0286</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/cvss3.png' width=19 height=20> CVSS 3 Score Details (<b>7.4</b>)</summary>
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: High
- Privileges Required: None
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: High
- Integrity Impact: None
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/suggested_fix.png' width=19 height=20> Suggested Fix</summary>
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://www.openssl.org/news/vulnerabilities.html">https://www.openssl.org/news/vulnerabilities.html</a></p>
<p>Release Date: 2023-02-08</p>
<p>Fix Resolution: openssl-3.0.8</p>
</p>
</details>
<p></p>
***
:rescue_worker_helmet: Automatic Remediation is available for this issue | True | CVE-2023-0286 (High) detected in cryptography-3.2.1-cp27-cp27mu-manylinux2010_x86_64.whl - ## CVE-2023-0286 - High Severity Vulnerability
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Library - <b>cryptography-3.2.1-cp27-cp27mu-manylinux2010_x86_64.whl</b></p></summary>
<p>cryptography is a package which provides cryptographic recipes and primitives to Python developers.</p>
<p>Library home page: <a href="https://files.pythonhosted.org/packages/08/ef/e98bc93bfa2527cb954efde5f3c7538a40fe0e7a2e55d68707783fcdab5d/cryptography-3.2.1-cp27-cp27mu-manylinux2010_x86_64.whl">https://files.pythonhosted.org/packages/08/ef/e98bc93bfa2527cb954efde5f3c7538a40fe0e7a2e55d68707783fcdab5d/cryptography-3.2.1-cp27-cp27mu-manylinux2010_x86_64.whl</a></p>
<p>Path to dependency file: /tmp/ws-scm/django-DefectDojo</p>
<p>Path to vulnerable library: /django-DefectDojo,/requirements.txt</p>
<p>
Dependency Hierarchy:
- :x: **cryptography-3.2.1-cp27-cp27mu-manylinux2010_x86_64.whl** (Vulnerable Library)
<p>Found in HEAD commit: <a href="https://github.com/rsoreq/django-DefectDojo/commit/778bcf0b3400f30c71d722f50e221c2eec64ea95">778bcf0b3400f30c71d722f50e221c2eec64ea95</a></p>
<p>Found in base branch: <b>master</b></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> Vulnerability Details</summary>
<p>
There is a type confusion vulnerability relating to X.400 address processing inside an X.509 GeneralName. X.400 addresses were parsed as an ASN1_STRING but the public structure definition for GENERAL_NAME incorrectly specified the type of the x400Address field as ASN1_TYPE. This field is subsequently interpreted by the OpenSSL function GENERAL_NAME_cmp as an ASN1_TYPE rather than an ASN1_STRING. When CRL checking is enabled (i.e. the application sets the X509_V_FLAG_CRL_CHECK flag), this vulnerability may allow an attacker to pass arbitrary pointers to a memcmp call, enabling them to read memory contents or enact a denial of service. In most cases, the attack requires the attacker to provide both the certificate chain and CRL, neither of which need to have a valid signature. If the attacker only controls one of these inputs, the other input must already contain an X.400 address as a CRL distribution point, which is uncommon. As such, this vulnerability is most likely to only affect applications which have implemented their own functionality for retrieving CRLs over a network.
<p>Publish Date: 2023-02-08
<p>URL: <a href=https://www.mend.io/vulnerability-database/CVE-2023-0286>CVE-2023-0286</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/cvss3.png' width=19 height=20> CVSS 3 Score Details (<b>7.4</b>)</summary>
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: High
- Privileges Required: None
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: High
- Integrity Impact: None
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/suggested_fix.png' width=19 height=20> Suggested Fix</summary>
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://www.openssl.org/news/vulnerabilities.html">https://www.openssl.org/news/vulnerabilities.html</a></p>
<p>Release Date: 2023-02-08</p>
<p>Fix Resolution: openssl-3.0.8</p>
</p>
</details>
<p></p>
***
:rescue_worker_helmet: Automatic Remediation is available for this issue | non_priority | cve high detected in cryptography whl cve high severity vulnerability vulnerable library cryptography whl cryptography is a package which provides cryptographic recipes and primitives to python developers library home page a href path to dependency file tmp ws scm django defectdojo path to vulnerable library django defectdojo requirements txt dependency hierarchy x cryptography whl vulnerable library found in head commit a href found in base branch master vulnerability details there is a type confusion vulnerability relating to x address processing inside an x generalname x addresses were parsed as an string but the public structure definition for general name incorrectly specified the type of the field as type this field is subsequently interpreted by the openssl function general name cmp as an type rather than an string when crl checking is enabled i e the application sets the v flag crl check flag this vulnerability may allow an attacker to pass arbitrary pointers to a memcmp call enabling them to read memory contents or enact a denial of service in most cases the attack requires the attacker to provide both the certificate chain and crl neither of which need to have a valid signature if the attacker only controls one of these inputs the other input must already contain an x address as a crl distribution point which is uncommon as such this vulnerability is most likely to only affect applications which have implemented their own functionality for retrieving crls over a network publish date url a href cvss score details base score metrics exploitability metrics attack vector network attack complexity high privileges required none user interaction none scope unchanged impact metrics confidentiality impact high integrity impact none availability impact high for more information on scores click a href suggested fix type upgrade version origin a href release date fix resolution openssl rescue worker helmet automatic remediation is available for this issue | 0 |
398,606 | 27,203,567,311 | IssuesEvent | 2023-02-20 11:24:45 | scylladb/terraform-provider-scylladbcloud | https://api.github.com/repos/scylladb/terraform-provider-scylladbcloud | closed | docs: improve resource documentation and add examples | documentation | The commit https://github.com/scylladb/terraform-provider-scylladbcloud/commit/895264835e1ffc64b9ffcd35e50b019fadd5e257 made it possible to customize documentation per resource or data source.
Currently all resources have a basic example usages.
Let's add more end-to-end examples to the resources:
- add end-to-end vpc peering for both GCP and AWS (`scylladbcloud_vpc_peering`)
an example for end-to-end AWS vpc peering:
```terraform
resource "aws_vpc" "app" {
cidr_block = "10.0.0.0/16"
}
data "aws_caller_identity" "current" {}
resource "scylladbcloud_vpc_peering" "db" {
cluster_id = 1337
datacenter = "AWS_EAST_1"
peer_vpc_id = aws_vpc.app.id
peer_cidr_block = aws_vpc.app.cidr_block
peer_region = "us-east-1"
peer_account_id = data.aws_caller_identity.current.account_id
allow_cql = true
}
resource "aws_vpc_peering_connection_accepter" "bench" {
vpc_peering_connection_id = scylladbcloud_vpc_peering.db.connection_id
auto_accept = true
}
resource "aws_route_table" "bench" {
vpc_id = aws_vpc.app.id
route {
cidr_block = scylladbcloud_cluster.db.cidr_block
vpc_peering_connection_id = aws_vpc_peering_connection_accepter.app.vpc_peering_connection_id
}
depends_on = [aws_vpc_peering_connection_accepter.app]
}
```
- an example for GCP cluster (`scylladbcloud_cluster`)
The new examples should be put under respective paths here:
https://github.com/scylladb/terraform-provider-scylladbcloud/tree/main/examples/resources
https://github.com/scylladb/terraform-provider-scylladbcloud/tree/main/examples/data-sources
And in order to display new example add proper go/template expressions, e.g. in order to display new example for `scylladbcloud_vpc_peering` drop new `aws-example.tf` file at [examples/resources/scylladbcloud_vpc_peering](https://github.com/scylladb/terraform-provider-scylladbcloud/tree/main/examples/resources/scylladbcloud_vpc_peering) and do:
```diff
diff --git a/templates/resources/vpc_peering.md.tmpl b/templates/resources/vpc_peering.md.tmpl
index 03db4db..c0a5d0b 100644
--- a/templates/resources/vpc_peering.md.tmpl
+++ b/templates/resources/vpc_peering.md.tmpl
@@ -12,6 +12,7 @@ description: |-
## Example Usage
{{ tffile (printf "examples/resources/%s/resource.tf" .Name)}}
+{{ tffile (printf "examples/resources/%s/aws-example.tf" .Name)}}
{{ .SchemaMarkdown | trimspace }}
```
| 1.0 | docs: improve resource documentation and add examples - The commit https://github.com/scylladb/terraform-provider-scylladbcloud/commit/895264835e1ffc64b9ffcd35e50b019fadd5e257 made it possible to customize documentation per resource or data source.
Currently all resources have a basic example usages.
Let's add more end-to-end examples to the resources:
- add end-to-end vpc peering for both GCP and AWS (`scylladbcloud_vpc_peering`)
an example for end-to-end AWS vpc peering:
```terraform
resource "aws_vpc" "app" {
cidr_block = "10.0.0.0/16"
}
data "aws_caller_identity" "current" {}
resource "scylladbcloud_vpc_peering" "db" {
cluster_id = 1337
datacenter = "AWS_EAST_1"
peer_vpc_id = aws_vpc.app.id
peer_cidr_block = aws_vpc.app.cidr_block
peer_region = "us-east-1"
peer_account_id = data.aws_caller_identity.current.account_id
allow_cql = true
}
resource "aws_vpc_peering_connection_accepter" "bench" {
vpc_peering_connection_id = scylladbcloud_vpc_peering.db.connection_id
auto_accept = true
}
resource "aws_route_table" "bench" {
vpc_id = aws_vpc.app.id
route {
cidr_block = scylladbcloud_cluster.db.cidr_block
vpc_peering_connection_id = aws_vpc_peering_connection_accepter.app.vpc_peering_connection_id
}
depends_on = [aws_vpc_peering_connection_accepter.app]
}
```
- an example for GCP cluster (`scylladbcloud_cluster`)
The new examples should be put under respective paths here:
https://github.com/scylladb/terraform-provider-scylladbcloud/tree/main/examples/resources
https://github.com/scylladb/terraform-provider-scylladbcloud/tree/main/examples/data-sources
And in order to display new example add proper go/template expressions, e.g. in order to display new example for `scylladbcloud_vpc_peering` drop new `aws-example.tf` file at [examples/resources/scylladbcloud_vpc_peering](https://github.com/scylladb/terraform-provider-scylladbcloud/tree/main/examples/resources/scylladbcloud_vpc_peering) and do:
```diff
diff --git a/templates/resources/vpc_peering.md.tmpl b/templates/resources/vpc_peering.md.tmpl
index 03db4db..c0a5d0b 100644
--- a/templates/resources/vpc_peering.md.tmpl
+++ b/templates/resources/vpc_peering.md.tmpl
@@ -12,6 +12,7 @@ description: |-
## Example Usage
{{ tffile (printf "examples/resources/%s/resource.tf" .Name)}}
+{{ tffile (printf "examples/resources/%s/aws-example.tf" .Name)}}
{{ .SchemaMarkdown | trimspace }}
```
| non_priority | docs improve resource documentation and add examples the commit made it possible to customize documentation per resource or data source currently all resources have a basic example usages let s add more end to end examples to the resources add end to end vpc peering for both gcp and aws scylladbcloud vpc peering an example for end to end aws vpc peering terraform resource aws vpc app cidr block data aws caller identity current resource scylladbcloud vpc peering db cluster id datacenter aws east peer vpc id aws vpc app id peer cidr block aws vpc app cidr block peer region us east peer account id data aws caller identity current account id allow cql true resource aws vpc peering connection accepter bench vpc peering connection id scylladbcloud vpc peering db connection id auto accept true resource aws route table bench vpc id aws vpc app id route cidr block scylladbcloud cluster db cidr block vpc peering connection id aws vpc peering connection accepter app vpc peering connection id depends on an example for gcp cluster scylladbcloud cluster the new examples should be put under respective paths here and in order to display new example add proper go template expressions e g in order to display new example for scylladbcloud vpc peering drop new aws example tf file at and do diff diff git a templates resources vpc peering md tmpl b templates resources vpc peering md tmpl index a templates resources vpc peering md tmpl b templates resources vpc peering md tmpl description example usage tffile printf examples resources s resource tf name tffile printf examples resources s aws example tf name schemamarkdown trimspace | 0 |
138,722 | 11,212,598,591 | IssuesEvent | 2020-01-06 17:58:39 | SAP/cloud-commerce-spartacus-storefront | https://api.github.com/repos/SAP/cloud-commerce-spartacus-storefront | opened | E2e product search failing since dev-17 restart | CRITICAL bug e2e-tests | The smoke test for product search is failing because it is expecting **144** results for `camera` but it returns **145**.
Also, the sort by highest price should return `DSLR-A900, body` first but returns a strange product with no name and `$48,557.00` price. | 1.0 | E2e product search failing since dev-17 restart - The smoke test for product search is failing because it is expecting **144** results for `camera` but it returns **145**.
Also, the sort by highest price should return `DSLR-A900, body` first but returns a strange product with no name and `$48,557.00` price. | non_priority | product search failing since dev restart the smoke test for product search is failing because it is expecting results for camera but it returns also the sort by highest price should return dslr body first but returns a strange product with no name and price | 0 |
307,847 | 23,219,486,705 | IssuesEvent | 2022-08-02 16:46:39 | Legohead259/Thetis-CAD | https://api.github.com/repos/Legohead259/Thetis-CAD | opened | Clean Up and Better Document This repo | documentation | Need to clean this up and make it a bit easier to use
- [ ] Publish official versions as releases (Schematic and PCB source, Schematic PDF, Gerber files zip, related docs)
- [ ] Rev F1
- [ ] Rev F2
- [ ] Rev F3
- [ ] Rev F4
- [ ] Make milestones
- [ ] Rev F5
- [ ] Rev G1
- [ ] Make branches
- [ ] Rev F5
- [ ] Rev G1
- [ ] Make Issue Templates
- [ ] Bug
- [ ] Feature Tracking | 1.0 | Clean Up and Better Document This repo - Need to clean this up and make it a bit easier to use
- [ ] Publish official versions as releases (Schematic and PCB source, Schematic PDF, Gerber files zip, related docs)
- [ ] Rev F1
- [ ] Rev F2
- [ ] Rev F3
- [ ] Rev F4
- [ ] Make milestones
- [ ] Rev F5
- [ ] Rev G1
- [ ] Make branches
- [ ] Rev F5
- [ ] Rev G1
- [ ] Make Issue Templates
- [ ] Bug
- [ ] Feature Tracking | non_priority | clean up and better document this repo need to clean this up and make it a bit easier to use publish official versions as releases schematic and pcb source schematic pdf gerber files zip related docs rev rev rev rev make milestones rev rev make branches rev rev make issue templates bug feature tracking | 0 |
32,408 | 13,804,567,729 | IssuesEvent | 2020-10-11 09:37:08 | geraldoyudo/mmadu | https://api.github.com/repos/geraldoyudo/mmadu | closed | JWK Set Uri Not Persisted for Default Configuration | bug user-service | The jwk set uri property does not reflect in the domain configuration when a domain is initialized using the /domains api in the user service.
Steps to Reproduce:
1. Make a call to the /domains api on userservice to configure a domain with the jwkSetUri property.
````
POST /domains HTTP/1.1
Host: localhost:15551
Authorization: Bearer <token>
Content-Type: application/json
[
{
"id": "app",
"name": "A Sample App",
"jwkSetUri": "http://localhost:15553/metadata/app/jwks.json",
"users": [
{
"username": "admin",
"password": "admin-password",
"externalId": 1111111111,
"properties": {
"nickname": "admin",
"email": "admin@myapp.com"
}
},
{
"username": "user1",
"password": "password",
"externalId": 2222222222,
"properties": {
"nickname": "admin",
"email": "user.one@myapp.com"
}
}
],
"authorities": [
{
"identifier": "view",
"name": "View",
"description": "View Data"
},
{
"identifier": "edit",
"name": "Edit",
"description": "Edit Data"
}
],
"roles": [
{
"identifier": "admin",
"name": "Admin",
"description": "A My App Admin"
},
{
"identifier": "user",
"name": "User",
"description": "A My App User"
}
],
"roleAuthorities": [
{
"role": "admin",
"authority": "edit"
},
{
"role": "admin",
"authority": "view"
},
{
"role": "user",
"authority": "view"
}
],
"userAuthorities": [],
"userRoles": [
{
"user": "admin",
"role": "admin"
},
{
"user": "user1",
"role": "user"
}
],
"groups": [
{
"identifier": "diaspora",
"name": "Diaspora",
"description": "Diaspora Group"
}
],
"userGroups": []
}
]
````
| 1.0 | JWK Set Uri Not Persisted for Default Configuration - The jwk set uri property does not reflect in the domain configuration when a domain is initialized using the /domains api in the user service.
Steps to Reproduce:
1. Make a call to the /domains api on userservice to configure a domain with the jwkSetUri property.
````
POST /domains HTTP/1.1
Host: localhost:15551
Authorization: Bearer <token>
Content-Type: application/json
[
{
"id": "app",
"name": "A Sample App",
"jwkSetUri": "http://localhost:15553/metadata/app/jwks.json",
"users": [
{
"username": "admin",
"password": "admin-password",
"externalId": 1111111111,
"properties": {
"nickname": "admin",
"email": "admin@myapp.com"
}
},
{
"username": "user1",
"password": "password",
"externalId": 2222222222,
"properties": {
"nickname": "admin",
"email": "user.one@myapp.com"
}
}
],
"authorities": [
{
"identifier": "view",
"name": "View",
"description": "View Data"
},
{
"identifier": "edit",
"name": "Edit",
"description": "Edit Data"
}
],
"roles": [
{
"identifier": "admin",
"name": "Admin",
"description": "A My App Admin"
},
{
"identifier": "user",
"name": "User",
"description": "A My App User"
}
],
"roleAuthorities": [
{
"role": "admin",
"authority": "edit"
},
{
"role": "admin",
"authority": "view"
},
{
"role": "user",
"authority": "view"
}
],
"userAuthorities": [],
"userRoles": [
{
"user": "admin",
"role": "admin"
},
{
"user": "user1",
"role": "user"
}
],
"groups": [
{
"identifier": "diaspora",
"name": "Diaspora",
"description": "Diaspora Group"
}
],
"userGroups": []
}
]
````
| non_priority | jwk set uri not persisted for default configuration the jwk set uri property does not reflect in the domain configuration when a domain is initialized using the domains api in the user service steps to reproduce make a call to the domains api on userservice to configure a domain with the jwkseturi property post domains http host localhost authorization bearer content type application json id app name a sample app jwkseturi users username admin password admin password externalid properties nickname admin email admin myapp com username password password externalid properties nickname admin email user one myapp com authorities identifier view name view description view data identifier edit name edit description edit data roles identifier admin name admin description a my app admin identifier user name user description a my app user roleauthorities role admin authority edit role admin authority view role user authority view userauthorities userroles user admin role admin user role user groups identifier diaspora name diaspora description diaspora group usergroups | 0 |
73,131 | 31,880,305,415 | IssuesEvent | 2023-09-16 09:43:15 | Source-Graphics-GmbH/upptime | https://api.github.com/repos/Source-Graphics-GmbH/upptime | closed | 🛑 Webmail for SG Services is down | status webmail-for-sg-services | In [`3a81626`](https://github.com/Source-Graphics-GmbH/upptime/commit/3a816262b6820887d8fff4ab5747450fd9ee2311
), Webmail for SG Services (https://webmail.services.source-graphics.ch/) was **down**:
- HTTP code: 0
- Response time: 0 ms
| 1.0 | 🛑 Webmail for SG Services is down - In [`3a81626`](https://github.com/Source-Graphics-GmbH/upptime/commit/3a816262b6820887d8fff4ab5747450fd9ee2311
), Webmail for SG Services (https://webmail.services.source-graphics.ch/) was **down**:
- HTTP code: 0
- Response time: 0 ms
| non_priority | 🛑 webmail for sg services is down in webmail for sg services was down http code response time ms | 0 |
37,846 | 6,649,709,274 | IssuesEvent | 2017-09-28 14:06:24 | neuropoly/qMRLab | https://api.github.com/repos/neuropoly/qMRLab | closed | wrong URL for documentation in Readme | bug documentation | @tanguyduval sorry, I gave you the wrong one, please change to: http://qmrlab.readthedocs.io/en/master/documentation.html | 1.0 | wrong URL for documentation in Readme - @tanguyduval sorry, I gave you the wrong one, please change to: http://qmrlab.readthedocs.io/en/master/documentation.html | non_priority | wrong url for documentation in readme tanguyduval sorry i gave you the wrong one please change to | 0 |
253,781 | 27,319,604,252 | IssuesEvent | 2023-02-24 18:33:28 | JoshRMendDemo/webgoat | https://api.github.com/repos/JoshRMendDemo/webgoat | opened | commons-text-1.9.jar: 1 vulnerabilities (highest severity is: 9.8) | security vulnerability | <details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Library - <b>commons-text-1.9.jar</b></p></summary>
<p>Apache Commons Text is a library focused on algorithms working on strings.</p>
<p>Library home page: <a href="https://commons.apache.org/proper/commons-text">https://commons.apache.org/proper/commons-text</a></p>
<p>Path to dependency file: /pom.xml</p>
<p>Path to vulnerable library: /home/wss-scanner/.m2/repository/org/apache/commons/commons-text/1.9/commons-text-1.9.jar</p>
<p>
<p>Found in HEAD commit: <a href="https://github.com/JoshRMendDemo/webgoat/commit/56db7061ff606d796cd153a83169b5c23c169d36">56db7061ff606d796cd153a83169b5c23c169d36</a></p></details>
## Vulnerabilities
| CVE | Severity | <img src='https://whitesource-resources.whitesourcesoftware.com/cvss3.png' width=19 height=20> CVSS | Dependency | Type | Fixed in (commons-text version) | Remediation Available |
| ------------- | ------------- | ----- | ----- | ----- | ------------- | --- |
| [CVE-2022-42889](https://www.mend.io/vulnerability-database/CVE-2022-42889) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 9.8 | commons-text-1.9.jar | Direct | 1.10.0 | ✅ |
## Details
<details>
<summary><img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> CVE-2022-42889</summary>
### Vulnerable Library - <b>commons-text-1.9.jar</b></p>
<p>Apache Commons Text is a library focused on algorithms working on strings.</p>
<p>Library home page: <a href="https://commons.apache.org/proper/commons-text">https://commons.apache.org/proper/commons-text</a></p>
<p>Path to dependency file: /pom.xml</p>
<p>Path to vulnerable library: /home/wss-scanner/.m2/repository/org/apache/commons/commons-text/1.9/commons-text-1.9.jar</p>
<p>
Dependency Hierarchy:
- :x: **commons-text-1.9.jar** (Vulnerable Library)
<p>Found in HEAD commit: <a href="https://github.com/JoshRMendDemo/webgoat/commit/56db7061ff606d796cd153a83169b5c23c169d36">56db7061ff606d796cd153a83169b5c23c169d36</a></p>
<p>Found in base branch: <b>main</b></p>
</p>
<p></p>
### Vulnerability Details
<p>
Apache Commons Text performs variable interpolation, allowing properties to be dynamically evaluated and expanded. The standard format for interpolation is "${prefix:name}", where "prefix" is used to locate an instance of org.apache.commons.text.lookup.StringLookup that performs the interpolation. Starting with version 1.5 and continuing through 1.9, the set of default Lookup instances included interpolators that could result in arbitrary code execution or contact with remote servers. These lookups are: - "script" - execute expressions using the JVM script execution engine (javax.script) - "dns" - resolve dns records - "url" - load values from urls, including from remote servers Applications using the interpolation defaults in the affected versions may be vulnerable to remote code execution or unintentional contact with remote servers if untrusted configuration values are used. Users are recommended to upgrade to Apache Commons Text 1.10.0, which disables the problematic interpolators by default.
<p>Publish Date: 2022-10-13
<p>URL: <a href=https://www.mend.io/vulnerability-database/CVE-2022-42889>CVE-2022-42889</a></p>
</p>
<p></p>
### CVSS 3 Score Details (<b>9.8</b>)
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: High
- Integrity Impact: High
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
<p></p>
### Suggested Fix
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://www.openwall.com/lists/oss-security/2022/10/13/4">https://www.openwall.com/lists/oss-security/2022/10/13/4</a></p>
<p>Release Date: 2022-10-13</p>
<p>Fix Resolution: 1.10.0</p>
</p>
<p></p>
:rescue_worker_helmet: Automatic Remediation is available for this issue
</details>
***
<p>:rescue_worker_helmet: Automatic Remediation is available for this issue.</p> | True | commons-text-1.9.jar: 1 vulnerabilities (highest severity is: 9.8) - <details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Library - <b>commons-text-1.9.jar</b></p></summary>
<p>Apache Commons Text is a library focused on algorithms working on strings.</p>
<p>Library home page: <a href="https://commons.apache.org/proper/commons-text">https://commons.apache.org/proper/commons-text</a></p>
<p>Path to dependency file: /pom.xml</p>
<p>Path to vulnerable library: /home/wss-scanner/.m2/repository/org/apache/commons/commons-text/1.9/commons-text-1.9.jar</p>
<p>
<p>Found in HEAD commit: <a href="https://github.com/JoshRMendDemo/webgoat/commit/56db7061ff606d796cd153a83169b5c23c169d36">56db7061ff606d796cd153a83169b5c23c169d36</a></p></details>
## Vulnerabilities
| CVE | Severity | <img src='https://whitesource-resources.whitesourcesoftware.com/cvss3.png' width=19 height=20> CVSS | Dependency | Type | Fixed in (commons-text version) | Remediation Available |
| ------------- | ------------- | ----- | ----- | ----- | ------------- | --- |
| [CVE-2022-42889](https://www.mend.io/vulnerability-database/CVE-2022-42889) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 9.8 | commons-text-1.9.jar | Direct | 1.10.0 | ✅ |
## Details
<details>
<summary><img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> CVE-2022-42889</summary>
### Vulnerable Library - <b>commons-text-1.9.jar</b></p>
<p>Apache Commons Text is a library focused on algorithms working on strings.</p>
<p>Library home page: <a href="https://commons.apache.org/proper/commons-text">https://commons.apache.org/proper/commons-text</a></p>
<p>Path to dependency file: /pom.xml</p>
<p>Path to vulnerable library: /home/wss-scanner/.m2/repository/org/apache/commons/commons-text/1.9/commons-text-1.9.jar</p>
<p>
Dependency Hierarchy:
- :x: **commons-text-1.9.jar** (Vulnerable Library)
<p>Found in HEAD commit: <a href="https://github.com/JoshRMendDemo/webgoat/commit/56db7061ff606d796cd153a83169b5c23c169d36">56db7061ff606d796cd153a83169b5c23c169d36</a></p>
<p>Found in base branch: <b>main</b></p>
</p>
<p></p>
### Vulnerability Details
<p>
Apache Commons Text performs variable interpolation, allowing properties to be dynamically evaluated and expanded. The standard format for interpolation is "${prefix:name}", where "prefix" is used to locate an instance of org.apache.commons.text.lookup.StringLookup that performs the interpolation. Starting with version 1.5 and continuing through 1.9, the set of default Lookup instances included interpolators that could result in arbitrary code execution or contact with remote servers. These lookups are: - "script" - execute expressions using the JVM script execution engine (javax.script) - "dns" - resolve dns records - "url" - load values from urls, including from remote servers Applications using the interpolation defaults in the affected versions may be vulnerable to remote code execution or unintentional contact with remote servers if untrusted configuration values are used. Users are recommended to upgrade to Apache Commons Text 1.10.0, which disables the problematic interpolators by default.
<p>Publish Date: 2022-10-13
<p>URL: <a href=https://www.mend.io/vulnerability-database/CVE-2022-42889>CVE-2022-42889</a></p>
</p>
<p></p>
### CVSS 3 Score Details (<b>9.8</b>)
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: High
- Integrity Impact: High
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
<p></p>
### Suggested Fix
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://www.openwall.com/lists/oss-security/2022/10/13/4">https://www.openwall.com/lists/oss-security/2022/10/13/4</a></p>
<p>Release Date: 2022-10-13</p>
<p>Fix Resolution: 1.10.0</p>
</p>
<p></p>
:rescue_worker_helmet: Automatic Remediation is available for this issue
</details>
***
<p>:rescue_worker_helmet: Automatic Remediation is available for this issue.</p> | non_priority | commons text jar vulnerabilities highest severity is vulnerable library commons text jar apache commons text is a library focused on algorithms working on strings library home page a href path to dependency file pom xml path to vulnerable library home wss scanner repository org apache commons commons text commons text jar found in head commit a href vulnerabilities cve severity cvss dependency type fixed in commons text version remediation available high commons text jar direct details cve vulnerable library commons text jar apache commons text is a library focused on algorithms working on strings library home page a href path to dependency file pom xml path to vulnerable library home wss scanner repository org apache commons commons text commons text jar dependency hierarchy x commons text jar vulnerable library found in head commit a href found in base branch main vulnerability details apache commons text performs variable interpolation allowing properties to be dynamically evaluated and expanded the standard format for interpolation is prefix name where prefix is used to locate an instance of org apache commons text lookup stringlookup that performs the interpolation starting with version and continuing through the set of default lookup instances included interpolators that could result in arbitrary code execution or contact with remote servers these lookups are script execute expressions using the jvm script execution engine javax script dns resolve dns records url load values from urls including from remote servers applications using the interpolation defaults in the affected versions may be vulnerable to remote code execution or unintentional contact with remote servers if untrusted configuration values are used users are recommended to upgrade to apache commons text which disables the problematic interpolators by default publish date url a href cvss score details base score metrics exploitability metrics attack vector network attack complexity low privileges required none user interaction none scope unchanged impact metrics confidentiality impact high integrity impact high availability impact high for more information on scores click a href suggested fix type upgrade version origin a href release date fix resolution rescue worker helmet automatic remediation is available for this issue rescue worker helmet automatic remediation is available for this issue | 0 |
431,977 | 30,261,111,938 | IssuesEvent | 2023-07-07 08:17:44 | Anglepi/My-Many-Reads | https://api.github.com/repos/Anglepi/My-Many-Reads | closed | El estado del arte debería reflejar aspectos parciales del trabajo | documentation | Tales como
* Frameworks usados
* Tecnologías usadas en general, o disponibles.
* Algoritmos de recomendación
Por otro lado, otras plataformas de blogs permiten publicar las lecturas con un
apuntuación o un hashtag; Wordpress por ejemplo lo permite (seguramente con un
plugin o algún tema).
Por otro lado, hay sitios, como el NY Times, que ofrece API para
desarrolladores: https://developer.nytimes.com/docs/books-product/1/overview
incluyendo las reviews. Sitios de reviews quizás deberían considerarse, o
mencionarse aunque sea de pasada, en el estado del arte.
| 1.0 | El estado del arte debería reflejar aspectos parciales del trabajo - Tales como
* Frameworks usados
* Tecnologías usadas en general, o disponibles.
* Algoritmos de recomendación
Por otro lado, otras plataformas de blogs permiten publicar las lecturas con un
apuntuación o un hashtag; Wordpress por ejemplo lo permite (seguramente con un
plugin o algún tema).
Por otro lado, hay sitios, como el NY Times, que ofrece API para
desarrolladores: https://developer.nytimes.com/docs/books-product/1/overview
incluyendo las reviews. Sitios de reviews quizás deberían considerarse, o
mencionarse aunque sea de pasada, en el estado del arte.
| non_priority | el estado del arte debería reflejar aspectos parciales del trabajo tales como frameworks usados tecnologías usadas en general o disponibles algoritmos de recomendación por otro lado otras plataformas de blogs permiten publicar las lecturas con un apuntuación o un hashtag wordpress por ejemplo lo permite seguramente con un plugin o algún tema por otro lado hay sitios como el ny times que ofrece api para desarrolladores incluyendo las reviews sitios de reviews quizás deberían considerarse o mencionarse aunque sea de pasada en el estado del arte | 0 |
70,659 | 23,279,752,682 | IssuesEvent | 2022-08-05 10:49:13 | vector-im/element-web | https://api.github.com/repos/vector-im/element-web | closed | matrix.to link for already joined room sends you to matrix.to only on Desktop | T-Defect | ### Steps to reproduce
Only applies to Element Desktop. The same link works as expected on Element Web.
1. Share a matrix.to link to a room by ID. Be sure that you are already member of this room.
2. Click the link
### Outcome
#### What did you expect?
Go to the room on click
#### What happened instead?
- Send to matrix.to
- Click „Continue“ there
- Send back to the room in Element Desktop
### Operating system
Ubuntu 22.04 LTS
### Application version
Element version: 1.11.1 Olm version: 3.2.8
### How did you install the app?
deb
### Homeserver
_No response_
### Will you send logs?
No | 1.0 | matrix.to link for already joined room sends you to matrix.to only on Desktop - ### Steps to reproduce
Only applies to Element Desktop. The same link works as expected on Element Web.
1. Share a matrix.to link to a room by ID. Be sure that you are already member of this room.
2. Click the link
### Outcome
#### What did you expect?
Go to the room on click
#### What happened instead?
- Send to matrix.to
- Click „Continue“ there
- Send back to the room in Element Desktop
### Operating system
Ubuntu 22.04 LTS
### Application version
Element version: 1.11.1 Olm version: 3.2.8
### How did you install the app?
deb
### Homeserver
_No response_
### Will you send logs?
No | non_priority | matrix to link for already joined room sends you to matrix to only on desktop steps to reproduce only applies to element desktop the same link works as expected on element web share a matrix to link to a room by id be sure that you are already member of this room click the link outcome what did you expect go to the room on click what happened instead send to matrix to click „continue“ there send back to the room in element desktop operating system ubuntu lts application version element version olm version how did you install the app deb homeserver no response will you send logs no | 0 |
405,794 | 27,534,203,814 | IssuesEvent | 2023-03-07 01:25:18 | RalphHightower/SouthernGothicTaleMoneyMurderMystery | https://api.github.com/repos/RalphHightower/SouthernGothicTaleMoneyMurderMystery | closed | MurdaughAlex_TimelineWeek7PostJudgmentDay: add header | documentation | # Judgement Day (Post) for Alex Murdaugh — Week 7 (Mar 6, 2023)
## Boss Hogg of Hampton County
| 1.0 | MurdaughAlex_TimelineWeek7PostJudgmentDay: add header - # Judgement Day (Post) for Alex Murdaugh — Week 7 (Mar 6, 2023)
## Boss Hogg of Hampton County
| non_priority | murdaughalex add header judgement day post for alex murdaugh — week mar boss hogg of hampton county | 0 |
204,328 | 15,438,791,434 | IssuesEvent | 2021-03-07 21:40:59 | trevorNgo/Measure2.0 | https://api.github.com/repos/trevorNgo/Measure2.0 | opened | CS4ZP6 Tester Feedback: Typo on Admin HomePage | tester | **Description:** There is a typo on one of the section titles on the homepage when logged in as an **Admin**. Where it says **Faculty Recomendations Report**, it _should_ say **Faculty Recommendations Report**.
**OS:** Windows 10 Enterprise
**Browser:** Chrome Version 89.0.4389.82
**Reproduction steps:**
* Sign in as an **Admin**
* Scroll down to **Faculty Recommendations Report**

| 1.0 | CS4ZP6 Tester Feedback: Typo on Admin HomePage - **Description:** There is a typo on one of the section titles on the homepage when logged in as an **Admin**. Where it says **Faculty Recomendations Report**, it _should_ say **Faculty Recommendations Report**.
**OS:** Windows 10 Enterprise
**Browser:** Chrome Version 89.0.4389.82
**Reproduction steps:**
* Sign in as an **Admin**
* Scroll down to **Faculty Recommendations Report**

| non_priority | tester feedback typo on admin homepage description there is a typo on one of the section titles on the homepage when logged in as an admin where it says faculty recomendations report it should say faculty recommendations report os windows enterprise browser chrome version reproduction steps sign in as an admin scroll down to faculty recommendations report | 0 |
425,189 | 29,210,576,570 | IssuesEvent | 2023-05-22 00:02:05 | lemurheavy/coveralls-public | https://api.github.com/repos/lemurheavy/coveralls-public | closed | GitLab Support ETA? | documentation potential-bug marked-for-closure coverage-merging permissions-related gitlab | I've been reading "Gitlab support coming very soon!" on the front page for quite a while now.
Is there any ETA? | 1.0 | GitLab Support ETA? - I've been reading "Gitlab support coming very soon!" on the front page for quite a while now.
Is there any ETA? | non_priority | gitlab support eta i ve been reading gitlab support coming very soon on the front page for quite a while now is there any eta | 0 |
3,340 | 6,474,890,092 | IssuesEvent | 2017-08-17 19:06:52 | Azure/azure-event-hubs-java | https://api.github.com/repos/Azure/azure-event-hubs-java | closed | log exceptions in one line | EventProcessorHost | This is an issue filed by customer in an internal thread:
Logging stack traces
– when the EPH logs error messages, it logs every line of the stack trace separately, Instead of logging everything in one log message. Why?
This makes is harder to understand what happened, especially when there are multiple partitions and each partition may log errors in parallel.
 | 1.0 | log exceptions in one line - This is an issue filed by customer in an internal thread:
Logging stack traces
– when the EPH logs error messages, it logs every line of the stack trace separately, Instead of logging everything in one log message. Why?
This makes is harder to understand what happened, especially when there are multiple partitions and each partition may log errors in parallel.
 | non_priority | log exceptions in one line this is an issue filed by customer in an internal thread logging stack traces – when the eph logs error messages it logs every line of the stack trace separately instead of logging everything in one log message why this makes is harder to understand what happened especially when there are multiple partitions and each partition may log errors in parallel | 0 |
1,799 | 6,735,225,159 | IssuesEvent | 2017-10-18 20:56:58 | deSagaz/java-sparrow | https://api.github.com/repos/deSagaz/java-sparrow | closed | Implement coding challenge event type | architecture frontend | Gives a coding-related question and allows executing code locally to generate e.g. number sequences.
- Has option to disallow for and while loops to force recursive answers.
- Has option to take existing code as framework, to allow having to code an inner (game) loop. | 1.0 | Implement coding challenge event type - Gives a coding-related question and allows executing code locally to generate e.g. number sequences.
- Has option to disallow for and while loops to force recursive answers.
- Has option to take existing code as framework, to allow having to code an inner (game) loop. | non_priority | implement coding challenge event type gives a coding related question and allows executing code locally to generate e g number sequences has option to disallow for and while loops to force recursive answers has option to take existing code as framework to allow having to code an inner game loop | 0 |
4,121 | 2,823,307,901 | IssuesEvent | 2015-05-21 07:59:27 | owncloud/core | https://api.github.com/repos/owncloud/core | reopened | User Already Exists Error | documentation | When I try to create a user in ownCloud, it says that the user already exists, when it clearly doesn't. Screenshot of JS Console below.

| 1.0 | User Already Exists Error - When I try to create a user in ownCloud, it says that the user already exists, when it clearly doesn't. Screenshot of JS Console below.

| non_priority | user already exists error when i try to create a user in owncloud it says that the user already exists when it clearly doesn t screenshot of js console below | 0 |
154,421 | 12,213,872,461 | IssuesEvent | 2020-05-01 08:21:55 | sbstnkr/sportsnewsapp | https://api.github.com/repos/sbstnkr/sportsnewsapp | closed | Brak opisu druzyny - nic nie zostaje wyświetlone | Awaiting Test enhancement idea question | Znalazłam kilka zespołów które da się wyszukać u nas w programie i które są w API, ale nie posiadają żadnego opisu, w związku z tym nic się nie dzieje po kliknięciu przycisku Search.
Co myślicie żeby obsługiwać taką sytuacje?
Można dodać do alertu sprawdzanie czy selectedTeam.strDescriptionEN jest nullem, albo dodać po prostu informacje w miejscu opisu zespołu typu "Obecnie nie posiadamy opisu zespołu".
Macie jakieś pomysły jak można rozwiązać tą sytuacje?
Przykłady zapytań:


| 1.0 | Brak opisu druzyny - nic nie zostaje wyświetlone - Znalazłam kilka zespołów które da się wyszukać u nas w programie i które są w API, ale nie posiadają żadnego opisu, w związku z tym nic się nie dzieje po kliknięciu przycisku Search.
Co myślicie żeby obsługiwać taką sytuacje?
Można dodać do alertu sprawdzanie czy selectedTeam.strDescriptionEN jest nullem, albo dodać po prostu informacje w miejscu opisu zespołu typu "Obecnie nie posiadamy opisu zespołu".
Macie jakieś pomysły jak można rozwiązać tą sytuacje?
Przykłady zapytań:


| non_priority | brak opisu druzyny nic nie zostaje wyświetlone znalazłam kilka zespołów które da się wyszukać u nas w programie i które są w api ale nie posiadają żadnego opisu w związku z tym nic się nie dzieje po kliknięciu przycisku search co myślicie żeby obsługiwać taką sytuacje można dodać do alertu sprawdzanie czy selectedteam strdescriptionen jest nullem albo dodać po prostu informacje w miejscu opisu zespołu typu obecnie nie posiadamy opisu zespołu macie jakieś pomysły jak można rozwiązać tą sytuacje przykłady zapytań | 0 |
4,892 | 5,375,861,412 | IssuesEvent | 2017-02-23 06:55:53 | w3c/browser-payment-api | https://api.github.com/repos/w3c/browser-payment-api | closed | Collect Privacy and Security considerations | help wanted HR: Privacy HR: Regulatory HR: Security | Discussed some with @pauljt... would be great to collect more here... please suggest more:
* [ ] Protecting the wallet - making sure "data at rest" can't be easily attacked by, for example, other applications.
* [ ] Don't store CVV
Payment sheet considerations:
* [ ] what numbers to show from stored credit cards (i.e., maybe first 4 and last 4).
* [ ] how to deal with too many Display Items in the sheet.
* [ ] how to deal with unicode strings and log URLs or origins (specially ones that try to flip the text display).
* [ ] Require user interaction bring up payment sheet (e.g., activate a button)
* [ ] Maybe delay activation of the "Pay" button in the sheet - so to give more time for the user to understand what is being asked of them.
| True | Collect Privacy and Security considerations - Discussed some with @pauljt... would be great to collect more here... please suggest more:
* [ ] Protecting the wallet - making sure "data at rest" can't be easily attacked by, for example, other applications.
* [ ] Don't store CVV
Payment sheet considerations:
* [ ] what numbers to show from stored credit cards (i.e., maybe first 4 and last 4).
* [ ] how to deal with too many Display Items in the sheet.
* [ ] how to deal with unicode strings and log URLs or origins (specially ones that try to flip the text display).
* [ ] Require user interaction bring up payment sheet (e.g., activate a button)
* [ ] Maybe delay activation of the "Pay" button in the sheet - so to give more time for the user to understand what is being asked of them.
| non_priority | collect privacy and security considerations discussed some with pauljt would be great to collect more here please suggest more protecting the wallet making sure data at rest can t be easily attacked by for example other applications don t store cvv payment sheet considerations what numbers to show from stored credit cards i e maybe first and last how to deal with too many display items in the sheet how to deal with unicode strings and log urls or origins specially ones that try to flip the text display require user interaction bring up payment sheet e g activate a button maybe delay activation of the pay button in the sheet so to give more time for the user to understand what is being asked of them | 0 |
187,284 | 22,044,255,072 | IssuesEvent | 2022-05-29 20:36:35 | jgeraigery/sql-maven-plugin | https://api.github.com/repos/jgeraigery/sql-maven-plugin | opened | CVE-2022-29599 (High) detected in maven-shared-utils-3.0.0.jar | security vulnerability | ## CVE-2022-29599 - High Severity Vulnerability
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Library - <b>maven-shared-utils-3.0.0.jar</b></p></summary>
<p>Shared utils without any further dependencies</p>
<p>Path to dependency file: /pom.xml</p>
<p>Path to vulnerable library: /home/wss-scanner/.m2/repository/org/apache/maven/shared/maven-shared-utils/3.0.0/maven-shared-utils-3.0.0.jar</p>
<p>
Dependency Hierarchy:
- maven-filtering-3.1.1.jar (Root Library)
- :x: **maven-shared-utils-3.0.0.jar** (Vulnerable Library)
<p>Found in base branch: <b>master</b></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> Vulnerability Details</summary>
<p>
In Apache Maven maven-shared-utils prior to version 3.3.3, the Commandline class can emit double-quoted strings without proper escaping, allowing shell injection attacks.
<p>Publish Date: 2022-05-23
<p>URL: <a href=https://vuln.whitesourcesoftware.com/vulnerability/CVE-2022-29599>CVE-2022-29599</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/cvss3.png' width=19 height=20> CVSS 3 Score Details (<b>9.8</b>)</summary>
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: High
- Integrity Impact: High
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/suggested_fix.png' width=19 height=20> Suggested Fix</summary>
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://github.com/advisories/GHSA-rhgr-952r-6p8q">https://github.com/advisories/GHSA-rhgr-952r-6p8q</a></p>
<p>Release Date: 2022-05-23</p>
<p>Fix Resolution: org.apache.maven.shared:maven-shared-utils:3.3.3</p>
</p>
</details>
<p></p>
<!-- <REMEDIATE>{"isOpenPROnVulnerability":true,"isPackageBased":true,"isDefaultBranch":true,"packages":[{"packageType":"Java","groupId":"org.apache.maven.shared","packageName":"maven-shared-utils","packageVersion":"3.0.0","packageFilePaths":["/pom.xml"],"isTransitiveDependency":true,"dependencyTree":"org.apache.maven.shared:maven-filtering:3.1.1;org.apache.maven.shared:maven-shared-utils:3.0.0","isMinimumFixVersionAvailable":true,"minimumFixVersion":"org.apache.maven.shared:maven-shared-utils:3.3.3","isBinary":false}],"baseBranches":["master"],"vulnerabilityIdentifier":"CVE-2022-29599","vulnerabilityDetails":"In Apache Maven maven-shared-utils prior to version 3.3.3, the Commandline class can emit double-quoted strings without proper escaping, allowing shell injection attacks.","vulnerabilityUrl":"https://vuln.whitesourcesoftware.com/vulnerability/CVE-2022-29599","cvss3Severity":"high","cvss3Score":"9.8","cvss3Metrics":{"A":"High","AC":"Low","PR":"None","S":"Unchanged","C":"High","UI":"None","AV":"Network","I":"High"},"extraData":{}}</REMEDIATE> --> | True | CVE-2022-29599 (High) detected in maven-shared-utils-3.0.0.jar - ## CVE-2022-29599 - High Severity Vulnerability
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Library - <b>maven-shared-utils-3.0.0.jar</b></p></summary>
<p>Shared utils without any further dependencies</p>
<p>Path to dependency file: /pom.xml</p>
<p>Path to vulnerable library: /home/wss-scanner/.m2/repository/org/apache/maven/shared/maven-shared-utils/3.0.0/maven-shared-utils-3.0.0.jar</p>
<p>
Dependency Hierarchy:
- maven-filtering-3.1.1.jar (Root Library)
- :x: **maven-shared-utils-3.0.0.jar** (Vulnerable Library)
<p>Found in base branch: <b>master</b></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> Vulnerability Details</summary>
<p>
In Apache Maven maven-shared-utils prior to version 3.3.3, the Commandline class can emit double-quoted strings without proper escaping, allowing shell injection attacks.
<p>Publish Date: 2022-05-23
<p>URL: <a href=https://vuln.whitesourcesoftware.com/vulnerability/CVE-2022-29599>CVE-2022-29599</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/cvss3.png' width=19 height=20> CVSS 3 Score Details (<b>9.8</b>)</summary>
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: High
- Integrity Impact: High
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/suggested_fix.png' width=19 height=20> Suggested Fix</summary>
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://github.com/advisories/GHSA-rhgr-952r-6p8q">https://github.com/advisories/GHSA-rhgr-952r-6p8q</a></p>
<p>Release Date: 2022-05-23</p>
<p>Fix Resolution: org.apache.maven.shared:maven-shared-utils:3.3.3</p>
</p>
</details>
<p></p>
<!-- <REMEDIATE>{"isOpenPROnVulnerability":true,"isPackageBased":true,"isDefaultBranch":true,"packages":[{"packageType":"Java","groupId":"org.apache.maven.shared","packageName":"maven-shared-utils","packageVersion":"3.0.0","packageFilePaths":["/pom.xml"],"isTransitiveDependency":true,"dependencyTree":"org.apache.maven.shared:maven-filtering:3.1.1;org.apache.maven.shared:maven-shared-utils:3.0.0","isMinimumFixVersionAvailable":true,"minimumFixVersion":"org.apache.maven.shared:maven-shared-utils:3.3.3","isBinary":false}],"baseBranches":["master"],"vulnerabilityIdentifier":"CVE-2022-29599","vulnerabilityDetails":"In Apache Maven maven-shared-utils prior to version 3.3.3, the Commandline class can emit double-quoted strings without proper escaping, allowing shell injection attacks.","vulnerabilityUrl":"https://vuln.whitesourcesoftware.com/vulnerability/CVE-2022-29599","cvss3Severity":"high","cvss3Score":"9.8","cvss3Metrics":{"A":"High","AC":"Low","PR":"None","S":"Unchanged","C":"High","UI":"None","AV":"Network","I":"High"},"extraData":{}}</REMEDIATE> --> | non_priority | cve high detected in maven shared utils jar cve high severity vulnerability vulnerable library maven shared utils jar shared utils without any further dependencies path to dependency file pom xml path to vulnerable library home wss scanner repository org apache maven shared maven shared utils maven shared utils jar dependency hierarchy maven filtering jar root library x maven shared utils jar vulnerable library found in base branch master vulnerability details in apache maven maven shared utils prior to version the commandline class can emit double quoted strings without proper escaping allowing shell injection attacks publish date url a href cvss score details base score metrics exploitability metrics attack vector network attack complexity low privileges required none user interaction none scope unchanged impact metrics confidentiality impact high integrity impact high availability impact high for more information on scores click a href suggested fix type upgrade version origin a href release date fix resolution org apache maven shared maven shared utils isopenpronvulnerability true ispackagebased true isdefaultbranch true packages istransitivedependency true dependencytree org apache maven shared maven filtering org apache maven shared maven shared utils isminimumfixversionavailable true minimumfixversion org apache maven shared maven shared utils isbinary false basebranches vulnerabilityidentifier cve vulnerabilitydetails in apache maven maven shared utils prior to version the commandline class can emit double quoted strings without proper escaping allowing shell injection attacks vulnerabilityurl | 0 |
95,224 | 11,961,515,477 | IssuesEvent | 2020-04-05 08:42:49 | mischkadb/lidarts | https://api.github.com/repos/mischkadb/lidarts | closed | Re-Design Chat-Page | design enhancement | I would re-design the chat page.
One big container for the chat and sending a message,
one smaller container for the notification of ended matches
and one container for the "Players online"-list.
At least for me its kind of annoying to see all the "New game" and "Match ended" messages between the normal user chats. | 1.0 | Re-Design Chat-Page - I would re-design the chat page.
One big container for the chat and sending a message,
one smaller container for the notification of ended matches
and one container for the "Players online"-list.
At least for me its kind of annoying to see all the "New game" and "Match ended" messages between the normal user chats. | non_priority | re design chat page i would re design the chat page one big container for the chat and sending a message one smaller container for the notification of ended matches and one container for the players online list at least for me its kind of annoying to see all the new game and match ended messages between the normal user chats | 0 |
391,824 | 26,909,848,909 | IssuesEvent | 2023-02-06 22:25:45 | ryanmichaelcurry/group1 | https://api.github.com/repos/ryanmichaelcurry/group1 | closed | User Stories | documentation | Create high-level user stories for the features in version 1. Each user story must have a user story ID, title, and details. These user stories will be placed in the Wiki. | 1.0 | User Stories - Create high-level user stories for the features in version 1. Each user story must have a user story ID, title, and details. These user stories will be placed in the Wiki. | non_priority | user stories create high level user stories for the features in version each user story must have a user story id title and details these user stories will be placed in the wiki | 0 |
104,846 | 16,622,398,814 | IssuesEvent | 2021-06-03 04:21:25 | gms-ws-sandbox/NodeGoat | https://api.github.com/repos/gms-ws-sandbox/NodeGoat | opened | CVE-2018-16492 (High) detected in extend-3.0.0.tgz | security vulnerability | ## CVE-2018-16492 - High Severity Vulnerability
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Library - <b>extend-3.0.0.tgz</b></p></summary>
<p>Port of jQuery.extend for node.js and the browser</p>
<p>Library home page: <a href="https://registry.npmjs.org/extend/-/extend-3.0.0.tgz">https://registry.npmjs.org/extend/-/extend-3.0.0.tgz</a></p>
<p>Path to dependency file: NodeGoat/package.json</p>
<p>Path to vulnerable library: NodeGoat/node_modules/npm/node_modules/request/node_modules/extend/package.json</p>
<p>
Dependency Hierarchy:
- grunt-npm-install-0.3.1.tgz (Root Library)
- npm-3.10.10.tgz
- request-2.75.0.tgz
- :x: **extend-3.0.0.tgz** (Vulnerable Library)
<p>Found in HEAD commit: <a href="https://github.com/gms-ws-sandbox/NodeGoat/commit/c221163763b7f2f5d9c526f553b11a21602caa30">c221163763b7f2f5d9c526f553b11a21602caa30</a></p>
<p>Found in base branch: <b>master</b></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> Vulnerability Details</summary>
<p>
A prototype pollution vulnerability was found in module extend <2.0.2, ~<3.0.2 that allows an attacker to inject arbitrary properties onto Object.prototype.
<p>Publish Date: 2019-02-01
<p>URL: <a href=https://vuln.whitesourcesoftware.com/vulnerability/CVE-2018-16492>CVE-2018-16492</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/cvss3.png' width=19 height=20> CVSS 3 Score Details (<b>9.8</b>)</summary>
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: High
- Integrity Impact: High
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/suggested_fix.png' width=19 height=20> Suggested Fix</summary>
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://hackerone.com/reports/381185">https://hackerone.com/reports/381185</a></p>
<p>Release Date: 2019-02-01</p>
<p>Fix Resolution: extend - v3.0.2,v2.0.2</p>
</p>
</details>
<p></p>
<!-- <REMEDIATE>{"isOpenPROnVulnerability":true,"isPackageBased":true,"isDefaultBranch":true,"packages":[{"packageType":"javascript/Node.js","packageName":"extend","packageVersion":"3.0.0","packageFilePaths":["/package.json"],"isTransitiveDependency":true,"dependencyTree":"grunt-npm-install:0.3.1;npm:3.10.10;request:2.75.0;extend:3.0.0","isMinimumFixVersionAvailable":true,"minimumFixVersion":"extend - v3.0.2,v2.0.2"}],"baseBranches":["master"],"vulnerabilityIdentifier":"CVE-2018-16492","vulnerabilityDetails":"A prototype pollution vulnerability was found in module extend \u003c2.0.2, ~\u003c3.0.2 that allows an attacker to inject arbitrary properties onto Object.prototype.","vulnerabilityUrl":"https://vuln.whitesourcesoftware.com/vulnerability/CVE-2018-16492","cvss3Severity":"high","cvss3Score":"9.8","cvss3Metrics":{"A":"High","AC":"Low","PR":"None","S":"Unchanged","C":"High","UI":"None","AV":"Network","I":"High"},"extraData":{}}</REMEDIATE> --> | True | CVE-2018-16492 (High) detected in extend-3.0.0.tgz - ## CVE-2018-16492 - High Severity Vulnerability
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Library - <b>extend-3.0.0.tgz</b></p></summary>
<p>Port of jQuery.extend for node.js and the browser</p>
<p>Library home page: <a href="https://registry.npmjs.org/extend/-/extend-3.0.0.tgz">https://registry.npmjs.org/extend/-/extend-3.0.0.tgz</a></p>
<p>Path to dependency file: NodeGoat/package.json</p>
<p>Path to vulnerable library: NodeGoat/node_modules/npm/node_modules/request/node_modules/extend/package.json</p>
<p>
Dependency Hierarchy:
- grunt-npm-install-0.3.1.tgz (Root Library)
- npm-3.10.10.tgz
- request-2.75.0.tgz
- :x: **extend-3.0.0.tgz** (Vulnerable Library)
<p>Found in HEAD commit: <a href="https://github.com/gms-ws-sandbox/NodeGoat/commit/c221163763b7f2f5d9c526f553b11a21602caa30">c221163763b7f2f5d9c526f553b11a21602caa30</a></p>
<p>Found in base branch: <b>master</b></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> Vulnerability Details</summary>
<p>
A prototype pollution vulnerability was found in module extend <2.0.2, ~<3.0.2 that allows an attacker to inject arbitrary properties onto Object.prototype.
<p>Publish Date: 2019-02-01
<p>URL: <a href=https://vuln.whitesourcesoftware.com/vulnerability/CVE-2018-16492>CVE-2018-16492</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/cvss3.png' width=19 height=20> CVSS 3 Score Details (<b>9.8</b>)</summary>
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: High
- Integrity Impact: High
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/suggested_fix.png' width=19 height=20> Suggested Fix</summary>
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://hackerone.com/reports/381185">https://hackerone.com/reports/381185</a></p>
<p>Release Date: 2019-02-01</p>
<p>Fix Resolution: extend - v3.0.2,v2.0.2</p>
</p>
</details>
<p></p>
<!-- <REMEDIATE>{"isOpenPROnVulnerability":true,"isPackageBased":true,"isDefaultBranch":true,"packages":[{"packageType":"javascript/Node.js","packageName":"extend","packageVersion":"3.0.0","packageFilePaths":["/package.json"],"isTransitiveDependency":true,"dependencyTree":"grunt-npm-install:0.3.1;npm:3.10.10;request:2.75.0;extend:3.0.0","isMinimumFixVersionAvailable":true,"minimumFixVersion":"extend - v3.0.2,v2.0.2"}],"baseBranches":["master"],"vulnerabilityIdentifier":"CVE-2018-16492","vulnerabilityDetails":"A prototype pollution vulnerability was found in module extend \u003c2.0.2, ~\u003c3.0.2 that allows an attacker to inject arbitrary properties onto Object.prototype.","vulnerabilityUrl":"https://vuln.whitesourcesoftware.com/vulnerability/CVE-2018-16492","cvss3Severity":"high","cvss3Score":"9.8","cvss3Metrics":{"A":"High","AC":"Low","PR":"None","S":"Unchanged","C":"High","UI":"None","AV":"Network","I":"High"},"extraData":{}}</REMEDIATE> --> | non_priority | cve high detected in extend tgz cve high severity vulnerability vulnerable library extend tgz port of jquery extend for node js and the browser library home page a href path to dependency file nodegoat package json path to vulnerable library nodegoat node modules npm node modules request node modules extend package json dependency hierarchy grunt npm install tgz root library npm tgz request tgz x extend tgz vulnerable library found in head commit a href found in base branch master vulnerability details a prototype pollution vulnerability was found in module extend that allows an attacker to inject arbitrary properties onto object prototype publish date url a href cvss score details base score metrics exploitability metrics attack vector network attack complexity low privileges required none user interaction none scope unchanged impact metrics confidentiality impact high integrity impact high availability impact high for more information on scores click a href suggested fix type upgrade version origin a href release date fix resolution extend isopenpronvulnerability true ispackagebased true isdefaultbranch true packages istransitivedependency true dependencytree grunt npm install npm request extend isminimumfixversionavailable true minimumfixversion extend basebranches vulnerabilityidentifier cve vulnerabilitydetails a prototype pollution vulnerability was found in module extend that allows an attacker to inject arbitrary properties onto object prototype vulnerabilityurl | 0 |
365,089 | 25,519,812,469 | IssuesEvent | 2022-11-28 19:25:40 | jrp1004/GESPRO_GESTIONTAREAS_Nicolas_Juan | https://api.github.com/repos/jrp1004/GESPRO_GESTIONTAREAS_Nicolas_Juan | opened | Modificar formato del pdf | bug documentation | ### Formato:
- [ ] Tamaño de la letra en 12 puntos en el desarrollo
- [ ] Tipo de letra Times Roman o Arial
- [ ] Interlineado de 1,5
- [ ] Vigilar la extensión del documento. | 1.0 | Modificar formato del pdf - ### Formato:
- [ ] Tamaño de la letra en 12 puntos en el desarrollo
- [ ] Tipo de letra Times Roman o Arial
- [ ] Interlineado de 1,5
- [ ] Vigilar la extensión del documento. | non_priority | modificar formato del pdf formato tamaño de la letra en puntos en el desarrollo tipo de letra times roman o arial interlineado de vigilar la extensión del documento | 0 |
417,573 | 28,110,641,613 | IssuesEvent | 2023-03-31 06:52:08 | 9fc70c892/ped | https://api.github.com/repos/9fc70c892/ped | opened | Example command returns error for event_create | severity.Medium type.DocumentationBug | event_create 1 ie/CS2101 Presentation f/28/02/2023 16:00 t/28/02/2023 18:00

<!--session: 1680243477664-1b5bef3d-f1e2-4bd2-907a-0b59f3b4aa90-->
<!--Version: Web v3.4.7--> | 1.0 | Example command returns error for event_create - event_create 1 ie/CS2101 Presentation f/28/02/2023 16:00 t/28/02/2023 18:00

<!--session: 1680243477664-1b5bef3d-f1e2-4bd2-907a-0b59f3b4aa90-->
<!--Version: Web v3.4.7--> | non_priority | example command returns error for event create event create ie presentation f t | 0 |
53,908 | 13,890,061,002 | IssuesEvent | 2020-10-19 08:46:38 | edwardhu/yarn | https://api.github.com/repos/edwardhu/yarn | opened | CVE-2020-15168 (Medium) detected in node-fetch-1.6.3.tgz | security vulnerability | ## CVE-2020-15168 - Medium Severity Vulnerability
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Library - <b>node-fetch-1.6.3.tgz</b></p></summary>
<p>A light-weight module that brings window.fetch to node.js and io.js</p>
<p>Library home page: <a href="https://registry.npmjs.org/node-fetch/-/node-fetch-1.6.3.tgz">https://registry.npmjs.org/node-fetch/-/node-fetch-1.6.3.tgz</a></p>
<p>Path to dependency file: yarn/node_modules/node-fetch/package.json</p>
<p>Path to vulnerable library: yarn/node_modules/node-fetch/package.json</p>
<p>
Dependency Hierarchy:
- commitizen-2.10.1.tgz (Root Library)
- opencollective-1.0.3.tgz
- :x: **node-fetch-1.6.3.tgz** (Vulnerable Library)
<p>Found in HEAD commit: <a href="https://github.com/edwardhu/yarn/commit/2ee054bb235ddfee52d2edbc5ea95cd8becdb9c9">2ee054bb235ddfee52d2edbc5ea95cd8becdb9c9</a></p>
<p>Found in base branch: <b>master</b></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/medium_vul.png' width=19 height=20> Vulnerability Details</summary>
<p>
node-fetch before versions 2.6.1 and 3.0.0-beta.9 did not honor the size option after following a redirect, which means that when a content size was over the limit, a FetchError would never get thrown and the process would end without failure. For most people, this fix will have a little or no impact. However, if you are relying on node-fetch to gate files above a size, the impact could be significant, for example: If you don't double-check the size of the data after fetch() has completed, your JS thread could get tied up doing work on a large file (DoS) and/or cost you money in computing.
<p>Publish Date: 2020-09-10
<p>URL: <a href=https://vuln.whitesourcesoftware.com/vulnerability/CVE-2020-15168>CVE-2020-15168</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/cvss3.png' width=19 height=20> CVSS 3 Score Details (<b>5.3</b>)</summary>
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: None
- Integrity Impact: None
- Availability Impact: Low
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/suggested_fix.png' width=19 height=20> Suggested Fix</summary>
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://github.com/node-fetch/node-fetch/security/advisories/GHSA-w7rc-rwvf-8q5r">https://github.com/node-fetch/node-fetch/security/advisories/GHSA-w7rc-rwvf-8q5r</a></p>
<p>Release Date: 2020-07-21</p>
<p>Fix Resolution: 2.6.1,3.0.0-beta.9</p>
</p>
</details>
<p></p>
<!-- <REMEDIATE>{"isOpenPROnVulnerability":false,"isPackageBased":true,"isDefaultBranch":true,"packages":[{"packageType":"javascript/Node.js","packageName":"node-fetch","packageVersion":"1.6.3","isTransitiveDependency":true,"dependencyTree":"commitizen:2.10.1;opencollective:1.0.3;node-fetch:1.6.3","isMinimumFixVersionAvailable":true,"minimumFixVersion":"2.6.1,3.0.0-beta.9"}],"vulnerabilityIdentifier":"CVE-2020-15168","vulnerabilityDetails":"node-fetch before versions 2.6.1 and 3.0.0-beta.9 did not honor the size option after following a redirect, which means that when a content size was over the limit, a FetchError would never get thrown and the process would end without failure. For most people, this fix will have a little or no impact. However, if you are relying on node-fetch to gate files above a size, the impact could be significant, for example: If you don\u0027t double-check the size of the data after fetch() has completed, your JS thread could get tied up doing work on a large file (DoS) and/or cost you money in computing.","vulnerabilityUrl":"https://vuln.whitesourcesoftware.com/vulnerability/CVE-2020-15168","cvss3Severity":"medium","cvss3Score":"5.3","cvss3Metrics":{"A":"Low","AC":"Low","PR":"None","S":"Unchanged","C":"None","UI":"None","AV":"Network","I":"None"},"extraData":{}}</REMEDIATE> --> | True | CVE-2020-15168 (Medium) detected in node-fetch-1.6.3.tgz - ## CVE-2020-15168 - Medium Severity Vulnerability
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Library - <b>node-fetch-1.6.3.tgz</b></p></summary>
<p>A light-weight module that brings window.fetch to node.js and io.js</p>
<p>Library home page: <a href="https://registry.npmjs.org/node-fetch/-/node-fetch-1.6.3.tgz">https://registry.npmjs.org/node-fetch/-/node-fetch-1.6.3.tgz</a></p>
<p>Path to dependency file: yarn/node_modules/node-fetch/package.json</p>
<p>Path to vulnerable library: yarn/node_modules/node-fetch/package.json</p>
<p>
Dependency Hierarchy:
- commitizen-2.10.1.tgz (Root Library)
- opencollective-1.0.3.tgz
- :x: **node-fetch-1.6.3.tgz** (Vulnerable Library)
<p>Found in HEAD commit: <a href="https://github.com/edwardhu/yarn/commit/2ee054bb235ddfee52d2edbc5ea95cd8becdb9c9">2ee054bb235ddfee52d2edbc5ea95cd8becdb9c9</a></p>
<p>Found in base branch: <b>master</b></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/medium_vul.png' width=19 height=20> Vulnerability Details</summary>
<p>
node-fetch before versions 2.6.1 and 3.0.0-beta.9 did not honor the size option after following a redirect, which means that when a content size was over the limit, a FetchError would never get thrown and the process would end without failure. For most people, this fix will have a little or no impact. However, if you are relying on node-fetch to gate files above a size, the impact could be significant, for example: If you don't double-check the size of the data after fetch() has completed, your JS thread could get tied up doing work on a large file (DoS) and/or cost you money in computing.
<p>Publish Date: 2020-09-10
<p>URL: <a href=https://vuln.whitesourcesoftware.com/vulnerability/CVE-2020-15168>CVE-2020-15168</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/cvss3.png' width=19 height=20> CVSS 3 Score Details (<b>5.3</b>)</summary>
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: None
- Integrity Impact: None
- Availability Impact: Low
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/suggested_fix.png' width=19 height=20> Suggested Fix</summary>
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://github.com/node-fetch/node-fetch/security/advisories/GHSA-w7rc-rwvf-8q5r">https://github.com/node-fetch/node-fetch/security/advisories/GHSA-w7rc-rwvf-8q5r</a></p>
<p>Release Date: 2020-07-21</p>
<p>Fix Resolution: 2.6.1,3.0.0-beta.9</p>
</p>
</details>
<p></p>
<!-- <REMEDIATE>{"isOpenPROnVulnerability":false,"isPackageBased":true,"isDefaultBranch":true,"packages":[{"packageType":"javascript/Node.js","packageName":"node-fetch","packageVersion":"1.6.3","isTransitiveDependency":true,"dependencyTree":"commitizen:2.10.1;opencollective:1.0.3;node-fetch:1.6.3","isMinimumFixVersionAvailable":true,"minimumFixVersion":"2.6.1,3.0.0-beta.9"}],"vulnerabilityIdentifier":"CVE-2020-15168","vulnerabilityDetails":"node-fetch before versions 2.6.1 and 3.0.0-beta.9 did not honor the size option after following a redirect, which means that when a content size was over the limit, a FetchError would never get thrown and the process would end without failure. For most people, this fix will have a little or no impact. However, if you are relying on node-fetch to gate files above a size, the impact could be significant, for example: If you don\u0027t double-check the size of the data after fetch() has completed, your JS thread could get tied up doing work on a large file (DoS) and/or cost you money in computing.","vulnerabilityUrl":"https://vuln.whitesourcesoftware.com/vulnerability/CVE-2020-15168","cvss3Severity":"medium","cvss3Score":"5.3","cvss3Metrics":{"A":"Low","AC":"Low","PR":"None","S":"Unchanged","C":"None","UI":"None","AV":"Network","I":"None"},"extraData":{}}</REMEDIATE> --> | non_priority | cve medium detected in node fetch tgz cve medium severity vulnerability vulnerable library node fetch tgz a light weight module that brings window fetch to node js and io js library home page a href path to dependency file yarn node modules node fetch package json path to vulnerable library yarn node modules node fetch package json dependency hierarchy commitizen tgz root library opencollective tgz x node fetch tgz vulnerable library found in head commit a href found in base branch master vulnerability details node fetch before versions and beta did not honor the size option after following a redirect which means that when a content size was over the limit a fetcherror would never get thrown and the process would end without failure for most people this fix will have a little or no impact however if you are relying on node fetch to gate files above a size the impact could be significant for example if you don t double check the size of the data after fetch has completed your js thread could get tied up doing work on a large file dos and or cost you money in computing publish date url a href cvss score details base score metrics exploitability metrics attack vector network attack complexity low privileges required none user interaction none scope unchanged impact metrics confidentiality impact none integrity impact none availability impact low for more information on scores click a href suggested fix type upgrade version origin a href release date fix resolution beta isopenpronvulnerability false ispackagebased true isdefaultbranch true packages vulnerabilityidentifier cve vulnerabilitydetails node fetch before versions and beta did not honor the size option after following a redirect which means that when a content size was over the limit a fetcherror would never get thrown and the process would end without failure for most people this fix will have a little or no impact however if you are relying on node fetch to gate files above a size the impact could be significant for example if you don double check the size of the data after fetch has completed your js thread could get tied up doing work on a large file dos and or cost you money in computing vulnerabilityurl | 0 |
91,423 | 8,304,771,506 | IssuesEvent | 2018-09-21 22:47:38 | mozilla/iris | https://api.github.com/repos/mozilla/iris | closed | Fix the failing 'toolbars_window_controls' tests | test case | The following tests did not pass:
about_firefox_controls
web_console_controls
web_developer_menu
drag_space
save_image_controls
browser_controls_upper_corner
sidebar_controls
| 1.0 | Fix the failing 'toolbars_window_controls' tests - The following tests did not pass:
about_firefox_controls
web_console_controls
web_developer_menu
drag_space
save_image_controls
browser_controls_upper_corner
sidebar_controls
| non_priority | fix the failing toolbars window controls tests the following tests did not pass about firefox controls web console controls web developer menu drag space save image controls browser controls upper corner sidebar controls | 0 |
107,013 | 9,200,155,972 | IssuesEvent | 2019-03-07 16:26:16 | rancher/rancher | https://api.github.com/repos/rancher/rancher | closed | Should not show custom cloud driver's page while the driver is not active | area/kontainer-engine area/ui kind/bug-qa status/ready-for-review status/resolved status/to-test team/cn version/2.0 | In master 3/7, I am using Huawei CCE cloud driver as an example:
While I am still downloading the driver:
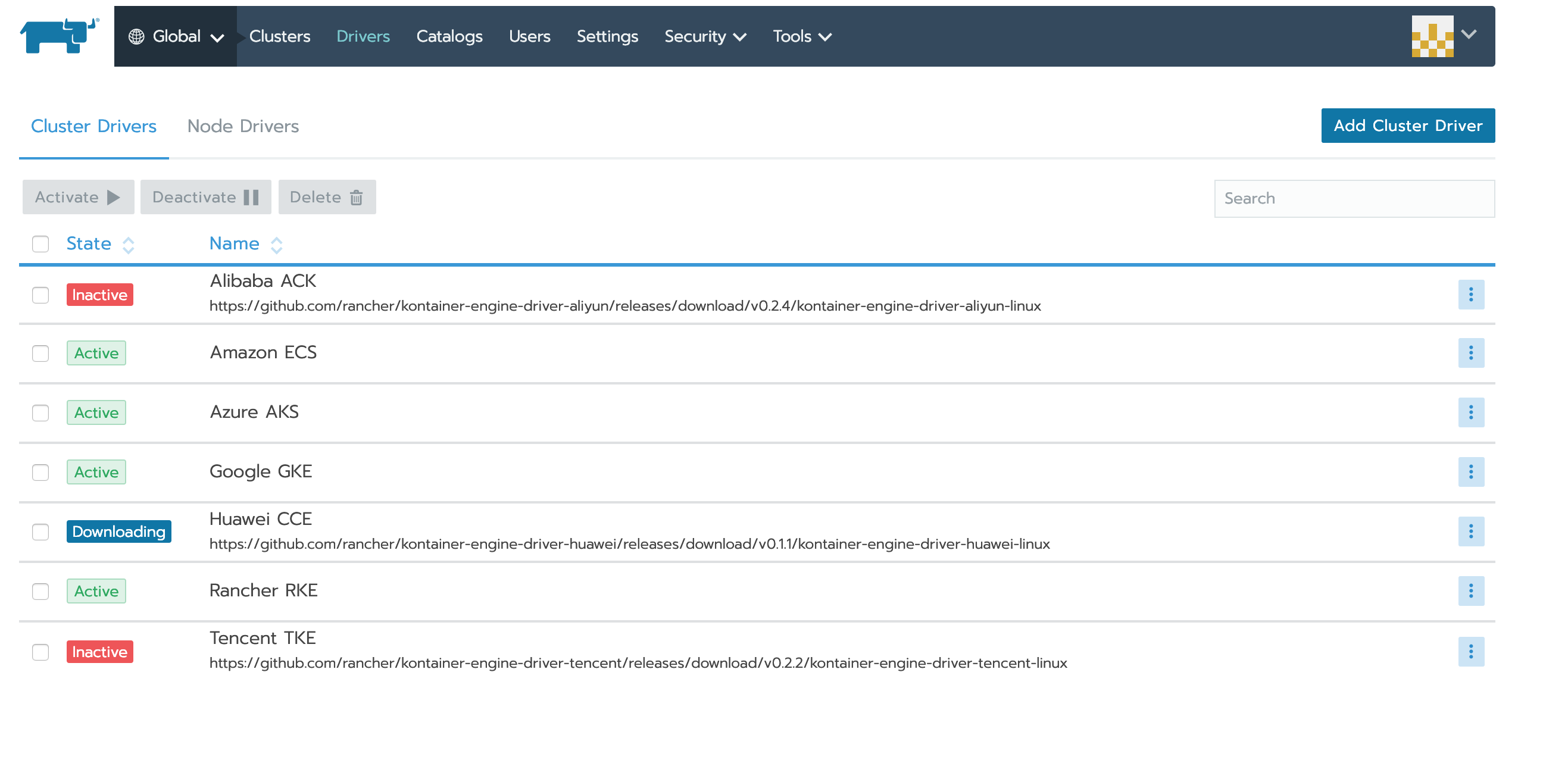
I can see the Huawei CCE in adding cluster page:

I don't think it is a good UX. | 1.0 | Should not show custom cloud driver's page while the driver is not active - In master 3/7, I am using Huawei CCE cloud driver as an example:
While I am still downloading the driver:

I can see the Huawei CCE in adding cluster page:

I don't think it is a good UX. | non_priority | should not show custom cloud driver s page while the driver is not active in master i am using huawei cce cloud driver as an example while i am still downloading the driver i can see the huawei cce in adding cluster page i don t think it is a good ux | 0 |
2,252 | 7,567,029,991 | IssuesEvent | 2018-04-22 04:27:02 | se-edu/addressbook-level4 | https://api.github.com/repos/se-edu/addressbook-level4 | closed | Use java.nio.file for file/path handling | a-Architecture a-CodeQuality c.Epic d.Committers p.Low | Constructing paths using string operations is error prone, but there's lots of areas in the code base where this is done, which sets a bad example.
Lots of APIs in the code base also take in Strings as file paths, which further encourages this kind of code. | 1.0 | Use java.nio.file for file/path handling - Constructing paths using string operations is error prone, but there's lots of areas in the code base where this is done, which sets a bad example.
Lots of APIs in the code base also take in Strings as file paths, which further encourages this kind of code. | non_priority | use java nio file for file path handling constructing paths using string operations is error prone but there s lots of areas in the code base where this is done which sets a bad example lots of apis in the code base also take in strings as file paths which further encourages this kind of code | 0 |
280,924 | 21,315,277,328 | IssuesEvent | 2022-04-16 06:51:59 | ovidharshini/pe | https://api.github.com/repos/ovidharshini/pe | opened | Undefined behaviour for adding tag when name matches an index | severity.Low type.DocumentationBug | UG:

Behaviour is unclear when name matches an index. E.g.

This is a documentation bug that can cause occasional inconvenience to users.
<!--session: 1650087535568-6111e44c-dfe1-4b82-811a-90932af1b148-->
<!--Version: Web v3.4.2--> | 1.0 | Undefined behaviour for adding tag when name matches an index - UG:

Behaviour is unclear when name matches an index. E.g.

This is a documentation bug that can cause occasional inconvenience to users.
<!--session: 1650087535568-6111e44c-dfe1-4b82-811a-90932af1b148-->
<!--Version: Web v3.4.2--> | non_priority | undefined behaviour for adding tag when name matches an index ug behaviour is unclear when name matches an index e g this is a documentation bug that can cause occasional inconvenience to users | 0 |
103,466 | 8,915,390,911 | IssuesEvent | 2019-01-19 05:15:49 | apache/incubator-mxnet | https://api.github.com/repos/apache/incubator-mxnet | reopened | C++ test Core dump DROPOUT_PERF.TimingGPU | C++ Flaky Test | http://jenkins.mxnet-ci.amazon-ml.com/blue/organizations/jenkins/incubator-mxnet/detail/master/399/pipeline
```
Timing: 50 iterations of 10 calls, shape = [50,3,18,32] = 86,400 items
Dropout Operator CPU: Timing [Forward] 28.45100 ms, avg: 0.05690 ms X 500 passes
[ OK ] DROPOUT_PERF.TimingCPU (2745 ms)
[ RUN ] DROPOUT_PERF.TimingGPU
Timing: 50 iterations of 10 calls, shape = [1,1,28,28] = 784 items
terminate called after throwing an instance of 'dmlc::Error'
what(): [22:22:55] ../mshadow/mshadow/./stream_gpu-inl.h:182: Check failed: e == cudaSuccess CUDA: an illegal memory access was encountered
Stack trace returned 10 entries:
[bt] (0) build/tests/mxnet_unit_tests(dmlc::StackTrace[abi:cxx11]()+0x56) [0xe15776]
[bt] (1) build/tests/mxnet_unit_tests(dmlc::LogMessageFatal::~LogMessageFatal()+0x28) [0xe15d78]
[bt] (2) build/tests/mxnet_unit_tests(void mshadow::DeleteStream<mshadow::gpu>(mshadow::Stream<mshadow::gpu>*)+0xb9) [0xe183f9]
[bt] (3) build/tests/mxnet_unit_tests(mxnet::test::op::CoreOpExecutor<float, float>::~CoreOpExecutor()+0x151) [0xe5f321]
[bt] (4) build/tests/mxnet_unit_tests(std::_Sp_counted_base<(__gnu_cxx::_Lock_policy)2>::_M_release()+0x46) [0xe1b316]
[bt] (5) build/tests/mxnet_unit_tests() [0xf0435e]
[bt] (6) build/tests/mxnet_unit_tests(DROPOUT_PERF_TimingGPU_Test::TestBody()+0x5e1) [0xf06401]
[bt] (7) build/tests/mxnet_unit_tests(void testing::internal::HandleExceptionsInMethodIfSupported<testing::Test, void>(testing::Test*, void (testing::Test::*)(), char const*)+0x43) [0xf36f03]
[bt] (8) build/tests/mxnet_unit_tests(testing::Test::Run()+0xba) [0xf27f3a]
[bt] (9) build/tests/mxnet_unit_tests(testing::TestInfo::Run()+0x118) [0xf28088]
/workspace/tests/ci_build/with_the_same_user: line 47: 83345 Aborted (core dumped) sudo -u "#${CI_BUILD_UID}" --preserve-env "LD_LIBRARY_PATH=${LD_LIBRARY_PATH}" "HOME=${CI_BUILD_HOME}" ${COMMAND[@]}
script returned exit code 134
``` | 1.0 | C++ test Core dump DROPOUT_PERF.TimingGPU - http://jenkins.mxnet-ci.amazon-ml.com/blue/organizations/jenkins/incubator-mxnet/detail/master/399/pipeline
```
Timing: 50 iterations of 10 calls, shape = [50,3,18,32] = 86,400 items
Dropout Operator CPU: Timing [Forward] 28.45100 ms, avg: 0.05690 ms X 500 passes
[ OK ] DROPOUT_PERF.TimingCPU (2745 ms)
[ RUN ] DROPOUT_PERF.TimingGPU
Timing: 50 iterations of 10 calls, shape = [1,1,28,28] = 784 items
terminate called after throwing an instance of 'dmlc::Error'
what(): [22:22:55] ../mshadow/mshadow/./stream_gpu-inl.h:182: Check failed: e == cudaSuccess CUDA: an illegal memory access was encountered
Stack trace returned 10 entries:
[bt] (0) build/tests/mxnet_unit_tests(dmlc::StackTrace[abi:cxx11]()+0x56) [0xe15776]
[bt] (1) build/tests/mxnet_unit_tests(dmlc::LogMessageFatal::~LogMessageFatal()+0x28) [0xe15d78]
[bt] (2) build/tests/mxnet_unit_tests(void mshadow::DeleteStream<mshadow::gpu>(mshadow::Stream<mshadow::gpu>*)+0xb9) [0xe183f9]
[bt] (3) build/tests/mxnet_unit_tests(mxnet::test::op::CoreOpExecutor<float, float>::~CoreOpExecutor()+0x151) [0xe5f321]
[bt] (4) build/tests/mxnet_unit_tests(std::_Sp_counted_base<(__gnu_cxx::_Lock_policy)2>::_M_release()+0x46) [0xe1b316]
[bt] (5) build/tests/mxnet_unit_tests() [0xf0435e]
[bt] (6) build/tests/mxnet_unit_tests(DROPOUT_PERF_TimingGPU_Test::TestBody()+0x5e1) [0xf06401]
[bt] (7) build/tests/mxnet_unit_tests(void testing::internal::HandleExceptionsInMethodIfSupported<testing::Test, void>(testing::Test*, void (testing::Test::*)(), char const*)+0x43) [0xf36f03]
[bt] (8) build/tests/mxnet_unit_tests(testing::Test::Run()+0xba) [0xf27f3a]
[bt] (9) build/tests/mxnet_unit_tests(testing::TestInfo::Run()+0x118) [0xf28088]
/workspace/tests/ci_build/with_the_same_user: line 47: 83345 Aborted (core dumped) sudo -u "#${CI_BUILD_UID}" --preserve-env "LD_LIBRARY_PATH=${LD_LIBRARY_PATH}" "HOME=${CI_BUILD_HOME}" ${COMMAND[@]}
script returned exit code 134
``` | non_priority | c test core dump dropout perf timinggpu timing iterations of calls shape items dropout operator cpu timing ms avg ms x passes dropout perf timingcpu ms dropout perf timinggpu timing iterations of calls shape items terminate called after throwing an instance of dmlc error what mshadow mshadow stream gpu inl h check failed e cudasuccess cuda an illegal memory access was encountered stack trace returned entries build tests mxnet unit tests dmlc stacktrace build tests mxnet unit tests dmlc logmessagefatal logmessagefatal build tests mxnet unit tests void mshadow deletestream mshadow stream build tests mxnet unit tests mxnet test op coreopexecutor coreopexecutor build tests mxnet unit tests std sp counted base m release build tests mxnet unit tests build tests mxnet unit tests dropout perf timinggpu test testbody build tests mxnet unit tests void testing internal handleexceptionsinmethodifsupported testing test void testing test char const build tests mxnet unit tests testing test run build tests mxnet unit tests testing testinfo run workspace tests ci build with the same user line aborted core dumped sudo u ci build uid preserve env ld library path ld library path home ci build home command script returned exit code | 0 |
51,735 | 21,788,757,549 | IssuesEvent | 2022-05-14 15:10:56 | localstack/localstack | https://api.github.com/repos/localstack/localstack | closed | bug: Service discovery return missing Namespace ID | bug needs-triaging should-be-fixed aws:servicediscovery | ### Is there an existing issue for this?
- [X] I have searched the existing issues
### Current Behavior
Same problem with happen again #4833 in latest release
### Expected Behavior
_No response_
### How are you starting LocalStack?
With a docker-compose file
### Steps To Reproduce
#### How are you starting localstack (e.g., `bin/localstack` command, arguments, or `docker-compose.yml`)
docker run localstack/localstack
#### Client commands (e.g., AWS SDK code snippet, or sequence of "awslocal" commands)
awslocal s3 mb s3://mybucket
### Environment
```markdown
- OS:
- LocalStack:
```
### Anything else?
_No response_ | 1.0 | bug: Service discovery return missing Namespace ID - ### Is there an existing issue for this?
- [X] I have searched the existing issues
### Current Behavior
Same problem with happen again #4833 in latest release
### Expected Behavior
_No response_
### How are you starting LocalStack?
With a docker-compose file
### Steps To Reproduce
#### How are you starting localstack (e.g., `bin/localstack` command, arguments, or `docker-compose.yml`)
docker run localstack/localstack
#### Client commands (e.g., AWS SDK code snippet, or sequence of "awslocal" commands)
awslocal s3 mb s3://mybucket
### Environment
```markdown
- OS:
- LocalStack:
```
### Anything else?
_No response_ | non_priority | bug service discovery return missing namespace id is there an existing issue for this i have searched the existing issues current behavior same problem with happen again in latest release expected behavior no response how are you starting localstack with a docker compose file steps to reproduce how are you starting localstack e g bin localstack command arguments or docker compose yml docker run localstack localstack client commands e g aws sdk code snippet or sequence of awslocal commands awslocal mb mybucket environment markdown os localstack anything else no response | 0 |
177,063 | 21,464,532,263 | IssuesEvent | 2022-04-26 01:19:31 | panasalap/linux-4.1.15 | https://api.github.com/repos/panasalap/linux-4.1.15 | closed | CVE-2016-5400 (Medium) detected in linux-stable-rtv4.1.33 - autoclosed | security vulnerability | ## CVE-2016-5400 - Medium Severity Vulnerability
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Library - <b>linux-stable-rtv4.1.33</b></p></summary>
<p>
<p>Julia Cartwright's fork of linux-stable-rt.git</p>
<p>Library home page: <a href=https://git.kernel.org/pub/scm/linux/kernel/git/julia/linux-stable-rt.git>https://git.kernel.org/pub/scm/linux/kernel/git/julia/linux-stable-rt.git</a></p>
<p>Found in HEAD commit: <a href="https://github.com/panasalap/linux-4.1.15/commit/aae4c2fa46027fd4c477372871df090c6b94f3f1">aae4c2fa46027fd4c477372871df090c6b94f3f1</a></p>
<p>Found in base branch: <b>master</b></p></p>
</details>
</p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Source Files (2)</summary>
<p></p>
<p>
<img src='https://s3.amazonaws.com/wss-public/bitbucketImages/xRedImage.png' width=19 height=20> <b>/drivers/media/usb/airspy/airspy.c</b>
<img src='https://s3.amazonaws.com/wss-public/bitbucketImages/xRedImage.png' width=19 height=20> <b>/drivers/media/usb/airspy/airspy.c</b>
</p>
</details>
<p></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/medium_vul.png' width=19 height=20> Vulnerability Details</summary>
<p>
Memory leak in the airspy_probe function in drivers/media/usb/airspy/airspy.c in the airspy USB driver in the Linux kernel before 4.7 allows local users to cause a denial of service (memory consumption) via a crafted USB device that emulates many VFL_TYPE_SDR or VFL_TYPE_SUBDEV devices and performs many connect and disconnect operations.
<p>Publish Date: 2016-08-06
<p>URL: <a href=https://vuln.whitesourcesoftware.com/vulnerability/CVE-2016-5400>CVE-2016-5400</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/cvss3.png' width=19 height=20> CVSS 3 Score Details (<b>4.3</b>)</summary>
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Physical
- Attack Complexity: Low
- Privileges Required: Low
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: None
- Integrity Impact: None
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/suggested_fix.png' width=19 height=20> Suggested Fix</summary>
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://nvd.nist.gov/vuln/detail/CVE-2016-5400">https://nvd.nist.gov/vuln/detail/CVE-2016-5400</a></p>
<p>Release Date: 2016-08-06</p>
<p>Fix Resolution: 4.7</p>
</p>
</details>
<p></p>
***
Step up your Open Source Security Game with WhiteSource [here](https://www.whitesourcesoftware.com/full_solution_bolt_github) | True | CVE-2016-5400 (Medium) detected in linux-stable-rtv4.1.33 - autoclosed - ## CVE-2016-5400 - Medium Severity Vulnerability
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Library - <b>linux-stable-rtv4.1.33</b></p></summary>
<p>
<p>Julia Cartwright's fork of linux-stable-rt.git</p>
<p>Library home page: <a href=https://git.kernel.org/pub/scm/linux/kernel/git/julia/linux-stable-rt.git>https://git.kernel.org/pub/scm/linux/kernel/git/julia/linux-stable-rt.git</a></p>
<p>Found in HEAD commit: <a href="https://github.com/panasalap/linux-4.1.15/commit/aae4c2fa46027fd4c477372871df090c6b94f3f1">aae4c2fa46027fd4c477372871df090c6b94f3f1</a></p>
<p>Found in base branch: <b>master</b></p></p>
</details>
</p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Source Files (2)</summary>
<p></p>
<p>
<img src='https://s3.amazonaws.com/wss-public/bitbucketImages/xRedImage.png' width=19 height=20> <b>/drivers/media/usb/airspy/airspy.c</b>
<img src='https://s3.amazonaws.com/wss-public/bitbucketImages/xRedImage.png' width=19 height=20> <b>/drivers/media/usb/airspy/airspy.c</b>
</p>
</details>
<p></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/medium_vul.png' width=19 height=20> Vulnerability Details</summary>
<p>
Memory leak in the airspy_probe function in drivers/media/usb/airspy/airspy.c in the airspy USB driver in the Linux kernel before 4.7 allows local users to cause a denial of service (memory consumption) via a crafted USB device that emulates many VFL_TYPE_SDR or VFL_TYPE_SUBDEV devices and performs many connect and disconnect operations.
<p>Publish Date: 2016-08-06
<p>URL: <a href=https://vuln.whitesourcesoftware.com/vulnerability/CVE-2016-5400>CVE-2016-5400</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/cvss3.png' width=19 height=20> CVSS 3 Score Details (<b>4.3</b>)</summary>
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Physical
- Attack Complexity: Low
- Privileges Required: Low
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: None
- Integrity Impact: None
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/suggested_fix.png' width=19 height=20> Suggested Fix</summary>
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://nvd.nist.gov/vuln/detail/CVE-2016-5400">https://nvd.nist.gov/vuln/detail/CVE-2016-5400</a></p>
<p>Release Date: 2016-08-06</p>
<p>Fix Resolution: 4.7</p>
</p>
</details>
<p></p>
***
Step up your Open Source Security Game with WhiteSource [here](https://www.whitesourcesoftware.com/full_solution_bolt_github) | non_priority | cve medium detected in linux stable autoclosed cve medium severity vulnerability vulnerable library linux stable julia cartwright s fork of linux stable rt git library home page a href found in head commit a href found in base branch master vulnerable source files drivers media usb airspy airspy c drivers media usb airspy airspy c vulnerability details memory leak in the airspy probe function in drivers media usb airspy airspy c in the airspy usb driver in the linux kernel before allows local users to cause a denial of service memory consumption via a crafted usb device that emulates many vfl type sdr or vfl type subdev devices and performs many connect and disconnect operations publish date url a href cvss score details base score metrics exploitability metrics attack vector physical attack complexity low privileges required low user interaction none scope unchanged impact metrics confidentiality impact none integrity impact none availability impact high for more information on scores click a href suggested fix type upgrade version origin a href release date fix resolution step up your open source security game with whitesource | 0 |
104,805 | 13,123,923,070 | IssuesEvent | 2020-08-06 02:08:06 | Public-Tree-Map/public-tree-map | https://api.github.com/repos/Public-Tree-Map/public-tree-map | opened | reset initial zoom level and center map to view all of LA county | county expansion design enhancement help wanted | **AS A/AN**:
user<!-- for example: user, reviewer, developer -->
**WHEN I**:
view the full extent of the map <!-- please describe the context -->
**I WANT TO**:
see trees in cities across LA county
as we expand coverage to other parts of LA county, we need to expand the extent of the the county visible when the map initially loads.
the visible map should include the full extent of the county - Matt Stiles collected data for cities as far east as Pomona, west to Malibu, north to San Fernando, south to Rancho Palos Verdes | 1.0 | reset initial zoom level and center map to view all of LA county - **AS A/AN**:
user<!-- for example: user, reviewer, developer -->
**WHEN I**:
view the full extent of the map <!-- please describe the context -->
**I WANT TO**:
see trees in cities across LA county
as we expand coverage to other parts of LA county, we need to expand the extent of the the county visible when the map initially loads.
the visible map should include the full extent of the county - Matt Stiles collected data for cities as far east as Pomona, west to Malibu, north to San Fernando, south to Rancho Palos Verdes | non_priority | reset initial zoom level and center map to view all of la county as a an user when i view the full extent of the map i want to see trees in cities across la county as we expand coverage to other parts of la county we need to expand the extent of the the county visible when the map initially loads the visible map should include the full extent of the county matt stiles collected data for cities as far east as pomona west to malibu north to san fernando south to rancho palos verdes | 0 |
117,362 | 15,091,249,709 | IssuesEvent | 2021-02-06 14:44:50 | 3box/3box-dapp | https://api.github.com/repos/3box/3box-dapp | closed | Spec out custom 3Box loading animation | Design Front End enhancement | Used for loading screens:
Box Object
Activity Feed
User Profile data | 1.0 | Spec out custom 3Box loading animation - Used for loading screens:
Box Object
Activity Feed
User Profile data | non_priority | spec out custom loading animation used for loading screens box object activity feed user profile data | 0 |
25,553 | 3,940,709,565 | IssuesEvent | 2016-04-27 02:41:43 | PositiveSpaceDevelopment/Grupr | https://api.github.com/repos/PositiveSpaceDevelopment/Grupr | closed | Design Registration Screen | BUG Design(Make it Pretty) GUI Registration Screen | Make it pretty!
The registration screen asks the user for their information, in order to make a new user.
- [ ] Name
- [ ] SMU Email
- [ ] Password
- [ ] Add Classes button | 1.0 | Design Registration Screen - Make it pretty!
The registration screen asks the user for their information, in order to make a new user.
- [ ] Name
- [ ] SMU Email
- [ ] Password
- [ ] Add Classes button | non_priority | design registration screen make it pretty the registration screen asks the user for their information in order to make a new user name smu email password add classes button | 0 |
344,059 | 30,711,407,042 | IssuesEvent | 2023-07-27 10:02:17 | kiali/kiali | https://api.github.com/repos/kiali/kiali | closed | Automate this scenario around Graph Display in Cypress | enhancement test-cypress :robot: test-add-coverage :paperclip: | I turned on operation nodes and turned off service nodes in app-graph:

I then switched to service graph and those options are the same, but grayed out to indicate they are unused for this graph type:

_Originally posted by @jmazzitelli in https://github.com/kiali/kiali/issues/6188#issuecomment-1562916608_
| 2.0 | Automate this scenario around Graph Display in Cypress - I turned on operation nodes and turned off service nodes in app-graph:

I then switched to service graph and those options are the same, but grayed out to indicate they are unused for this graph type:

_Originally posted by @jmazzitelli in https://github.com/kiali/kiali/issues/6188#issuecomment-1562916608_
| non_priority | automate this scenario around graph display in cypress i turned on operation nodes and turned off service nodes in app graph i then switched to service graph and those options are the same but grayed out to indicate they are unused for this graph type originally posted by jmazzitelli in | 0 |
8,639 | 7,541,466,311 | IssuesEvent | 2018-04-17 09:51:19 | viatra/v4md | https://api.github.com/repos/viatra/v4md | opened | Use separate classloader for V4MD | infrastructure | In order to avoid potential classpath conflicts, we should use separate classloader in MagicDraw. | 1.0 | Use separate classloader for V4MD - In order to avoid potential classpath conflicts, we should use separate classloader in MagicDraw. | non_priority | use separate classloader for in order to avoid potential classpath conflicts we should use separate classloader in magicdraw | 0 |
67,561 | 9,071,950,925 | IssuesEvent | 2019-02-15 00:36:17 | Azure/Azure-Functions | https://api.github.com/repos/Azure/Azure-Functions | closed | CFC: App Insights analytics queries for Functions | community documentation feature:application-insights question | # Call for content! - *Example queries*
We're looking to get a bunch of App Insights analytics queries put together for Functions. Leave a comment here with any samples/etc. you might have (either pasted directly or a link). I'll try to get them all in a wiki and we'll use some of them in our docs on docs.microsoft.com. | 1.0 | CFC: App Insights analytics queries for Functions - # Call for content! - *Example queries*
We're looking to get a bunch of App Insights analytics queries put together for Functions. Leave a comment here with any samples/etc. you might have (either pasted directly or a link). I'll try to get them all in a wiki and we'll use some of them in our docs on docs.microsoft.com. | non_priority | cfc app insights analytics queries for functions call for content example queries we re looking to get a bunch of app insights analytics queries put together for functions leave a comment here with any samples etc you might have either pasted directly or a link i ll try to get them all in a wiki and we ll use some of them in our docs on docs microsoft com | 0 |
13,888 | 3,785,415,132 | IssuesEvent | 2016-03-20 14:06:29 | eslint/eslint | https://api.github.com/repos/eslint/eslint | closed | linebreak-style without an argument seems to default to 'unix' | accepted documentation rule | I have a Git project which I contribute to on a Windows system. The general consensus seems to be that we should use `core.autocrlf` to deal with any line-ending issues that might arise. Therefore we need to configure ESLint (actually XO, which uses ESLint) to allow either CRLF line-endings or LF line-endings as long as we're being consistent.
I have a project which I've configured like this:
```
"xo": {
"esnext": true,
"rules": {
"linebreak-style": 2,
"camelcase": 1,
"no-useless-constructor": 1
}
}
```
Now I get this error for every single line of my project:
`131:16 error Expected linebreaks to be 'LF' but found 'CRLF' linebreak-style`
[The documentation](http://eslint.org/docs/rules/linebreak-style) talks about disallowing mixing of CRs and LFs, but it doesn't say explicitly whether my use case is supported. The [test cases](https://github.com/eslint/eslint/blob/83a9c9dd638434a79c4e2b3ba123cf9b5d307aa5/tests/lib/rules/linebreak-style.js) just leave me more confused, because their implementation seems to suggest that defaulting to LF-only is the intended behavior.
Is this a bug? How is this option meant to be used? | 1.0 | linebreak-style without an argument seems to default to 'unix' - I have a Git project which I contribute to on a Windows system. The general consensus seems to be that we should use `core.autocrlf` to deal with any line-ending issues that might arise. Therefore we need to configure ESLint (actually XO, which uses ESLint) to allow either CRLF line-endings or LF line-endings as long as we're being consistent.
I have a project which I've configured like this:
```
"xo": {
"esnext": true,
"rules": {
"linebreak-style": 2,
"camelcase": 1,
"no-useless-constructor": 1
}
}
```
Now I get this error for every single line of my project:
`131:16 error Expected linebreaks to be 'LF' but found 'CRLF' linebreak-style`
[The documentation](http://eslint.org/docs/rules/linebreak-style) talks about disallowing mixing of CRs and LFs, but it doesn't say explicitly whether my use case is supported. The [test cases](https://github.com/eslint/eslint/blob/83a9c9dd638434a79c4e2b3ba123cf9b5d307aa5/tests/lib/rules/linebreak-style.js) just leave me more confused, because their implementation seems to suggest that defaulting to LF-only is the intended behavior.
Is this a bug? How is this option meant to be used? | non_priority | linebreak style without an argument seems to default to unix i have a git project which i contribute to on a windows system the general consensus seems to be that we should use core autocrlf to deal with any line ending issues that might arise therefore we need to configure eslint actually xo which uses eslint to allow either crlf line endings or lf line endings as long as we re being consistent i have a project which i ve configured like this xo esnext true rules linebreak style camelcase no useless constructor now i get this error for every single line of my project error expected linebreaks to be lf but found crlf linebreak style talks about disallowing mixing of crs and lfs but it doesn t say explicitly whether my use case is supported the just leave me more confused because their implementation seems to suggest that defaulting to lf only is the intended behavior is this a bug how is this option meant to be used | 0 |
158,072 | 20,007,572,393 | IssuesEvent | 2022-02-01 00:01:49 | timf-app-sandbox/t1 | https://api.github.com/repos/timf-app-sandbox/t1 | opened | CVE-2020-8116 (High) detected in dot-prop-4.2.0.tgz | security vulnerability | ## CVE-2020-8116 - High Severity Vulnerability
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Library - <b>dot-prop-4.2.0.tgz</b></p></summary>
<p>Get, set, or delete a property from a nested object using a dot path</p>
<p>Library home page: <a href="https://registry.npmjs.org/dot-prop/-/dot-prop-4.2.0.tgz">https://registry.npmjs.org/dot-prop/-/dot-prop-4.2.0.tgz</a></p>
<p>Path to dependency file: /package.json</p>
<p>Path to vulnerable library: /node_modules/dot-prop/package.json</p>
<p>
Dependency Hierarchy:
- nodemon-1.19.1.tgz (Root Library)
- update-notifier-2.5.0.tgz
- configstore-3.1.2.tgz
- :x: **dot-prop-4.2.0.tgz** (Vulnerable Library)
<p>Found in HEAD commit: <a href="https://github.com/timf-app-sandbox/t1/commit/ade63e4d4d7f78775fe064056f81c5da1b53aecf">ade63e4d4d7f78775fe064056f81c5da1b53aecf</a></p>
<p>Found in base branch: <b>dev</b></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> Vulnerability Details</summary>
<p>
Prototype pollution vulnerability in dot-prop npm package versions before 4.2.1 and versions 5.x before 5.1.1 allows an attacker to add arbitrary properties to JavaScript language constructs such as objects.
<p>Publish Date: 2020-02-04
<p>URL: <a href=https://vuln.whitesourcesoftware.com/vulnerability/CVE-2020-8116>CVE-2020-8116</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/cvss3.png' width=19 height=20> CVSS 3 Score Details (<b>7.3</b>)</summary>
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: Low
- Integrity Impact: Low
- Availability Impact: Low
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/suggested_fix.png' width=19 height=20> Suggested Fix</summary>
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2020-8116">https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2020-8116</a></p>
<p>Release Date: 2020-02-04</p>
<p>Fix Resolution (dot-prop): 4.2.1</p>
<p>Direct dependency fix Resolution (nodemon): 1.19.2</p>
</p>
</details>
<p></p>
***
:rescue_worker_helmet: Automatic Remediation is available for this issue
<!-- <REMEDIATE>{"isOpenPROnVulnerability":true,"isPackageBased":true,"isDefaultBranch":true,"packages":[{"packageType":"javascript/Node.js","packageName":"nodemon","packageVersion":"1.19.1","packageFilePaths":["/package.json"],"isTransitiveDependency":false,"dependencyTree":"nodemon:1.19.1","isMinimumFixVersionAvailable":true,"minimumFixVersion":"1.19.2","isBinary":false}],"baseBranches":["dev"],"vulnerabilityIdentifier":"CVE-2020-8116","vulnerabilityDetails":"Prototype pollution vulnerability in dot-prop npm package versions before 4.2.1 and versions 5.x before 5.1.1 allows an attacker to add arbitrary properties to JavaScript language constructs such as objects.","vulnerabilityUrl":"https://vuln.whitesourcesoftware.com/vulnerability/CVE-2020-8116","cvss3Severity":"high","cvss3Score":"7.3","cvss3Metrics":{"A":"Low","AC":"Low","PR":"None","S":"Unchanged","C":"Low","UI":"None","AV":"Network","I":"Low"},"extraData":{}}</REMEDIATE> --> | True | CVE-2020-8116 (High) detected in dot-prop-4.2.0.tgz - ## CVE-2020-8116 - High Severity Vulnerability
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Library - <b>dot-prop-4.2.0.tgz</b></p></summary>
<p>Get, set, or delete a property from a nested object using a dot path</p>
<p>Library home page: <a href="https://registry.npmjs.org/dot-prop/-/dot-prop-4.2.0.tgz">https://registry.npmjs.org/dot-prop/-/dot-prop-4.2.0.tgz</a></p>
<p>Path to dependency file: /package.json</p>
<p>Path to vulnerable library: /node_modules/dot-prop/package.json</p>
<p>
Dependency Hierarchy:
- nodemon-1.19.1.tgz (Root Library)
- update-notifier-2.5.0.tgz
- configstore-3.1.2.tgz
- :x: **dot-prop-4.2.0.tgz** (Vulnerable Library)
<p>Found in HEAD commit: <a href="https://github.com/timf-app-sandbox/t1/commit/ade63e4d4d7f78775fe064056f81c5da1b53aecf">ade63e4d4d7f78775fe064056f81c5da1b53aecf</a></p>
<p>Found in base branch: <b>dev</b></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> Vulnerability Details</summary>
<p>
Prototype pollution vulnerability in dot-prop npm package versions before 4.2.1 and versions 5.x before 5.1.1 allows an attacker to add arbitrary properties to JavaScript language constructs such as objects.
<p>Publish Date: 2020-02-04
<p>URL: <a href=https://vuln.whitesourcesoftware.com/vulnerability/CVE-2020-8116>CVE-2020-8116</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/cvss3.png' width=19 height=20> CVSS 3 Score Details (<b>7.3</b>)</summary>
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: Low
- Integrity Impact: Low
- Availability Impact: Low
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/suggested_fix.png' width=19 height=20> Suggested Fix</summary>
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2020-8116">https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2020-8116</a></p>
<p>Release Date: 2020-02-04</p>
<p>Fix Resolution (dot-prop): 4.2.1</p>
<p>Direct dependency fix Resolution (nodemon): 1.19.2</p>
</p>
</details>
<p></p>
***
:rescue_worker_helmet: Automatic Remediation is available for this issue
<!-- <REMEDIATE>{"isOpenPROnVulnerability":true,"isPackageBased":true,"isDefaultBranch":true,"packages":[{"packageType":"javascript/Node.js","packageName":"nodemon","packageVersion":"1.19.1","packageFilePaths":["/package.json"],"isTransitiveDependency":false,"dependencyTree":"nodemon:1.19.1","isMinimumFixVersionAvailable":true,"minimumFixVersion":"1.19.2","isBinary":false}],"baseBranches":["dev"],"vulnerabilityIdentifier":"CVE-2020-8116","vulnerabilityDetails":"Prototype pollution vulnerability in dot-prop npm package versions before 4.2.1 and versions 5.x before 5.1.1 allows an attacker to add arbitrary properties to JavaScript language constructs such as objects.","vulnerabilityUrl":"https://vuln.whitesourcesoftware.com/vulnerability/CVE-2020-8116","cvss3Severity":"high","cvss3Score":"7.3","cvss3Metrics":{"A":"Low","AC":"Low","PR":"None","S":"Unchanged","C":"Low","UI":"None","AV":"Network","I":"Low"},"extraData":{}}</REMEDIATE> --> | non_priority | cve high detected in dot prop tgz cve high severity vulnerability vulnerable library dot prop tgz get set or delete a property from a nested object using a dot path library home page a href path to dependency file package json path to vulnerable library node modules dot prop package json dependency hierarchy nodemon tgz root library update notifier tgz configstore tgz x dot prop tgz vulnerable library found in head commit a href found in base branch dev vulnerability details prototype pollution vulnerability in dot prop npm package versions before and versions x before allows an attacker to add arbitrary properties to javascript language constructs such as objects publish date url a href cvss score details base score metrics exploitability metrics attack vector network attack complexity low privileges required none user interaction none scope unchanged impact metrics confidentiality impact low integrity impact low availability impact low for more information on scores click a href suggested fix type upgrade version origin a href release date fix resolution dot prop direct dependency fix resolution nodemon rescue worker helmet automatic remediation is available for this issue isopenpronvulnerability true ispackagebased true isdefaultbranch true packages istransitivedependency false dependencytree nodemon isminimumfixversionavailable true minimumfixversion isbinary false basebranches vulnerabilityidentifier cve vulnerabilitydetails prototype pollution vulnerability in dot prop npm package versions before and versions x before allows an attacker to add arbitrary properties to javascript language constructs such as objects vulnerabilityurl | 0 |
81,557 | 10,149,039,873 | IssuesEvent | 2019-08-05 14:25:52 | 18F/civil-rights-complaints | https://api.github.com/repos/18F/civil-rights-complaints | closed | Schedule form feedback sessions w Public deep dive group | Design | ## Description
## Definition of done
- [x] Daisy (Friday)
- [x] Tulip (haven't heard back)
- [x] Daffodil (next Friday August 2) need time
- [x] Jasmine (next Tuesday Jul 30)
- [x] Clover (next Wednesday Jul 31)
- [x] Lavender (next Tuesday Jul 30)
## Attachments
[title](URL)
| 1.0 | Schedule form feedback sessions w Public deep dive group - ## Description
## Definition of done
- [x] Daisy (Friday)
- [x] Tulip (haven't heard back)
- [x] Daffodil (next Friday August 2) need time
- [x] Jasmine (next Tuesday Jul 30)
- [x] Clover (next Wednesday Jul 31)
- [x] Lavender (next Tuesday Jul 30)
## Attachments
[title](URL)
| non_priority | schedule form feedback sessions w public deep dive group description definition of done daisy friday tulip haven t heard back daffodil next friday august need time jasmine next tuesday jul clover next wednesday jul lavender next tuesday jul attachments url | 0 |
45,827 | 11,740,288,122 | IssuesEvent | 2020-03-11 19:18:35 | mlpack/mlpack | https://api.github.com/repos/mlpack/mlpack | closed | Use common/simpler FindArmadilo.cmake (and BLAS/LAPACK) | c: build system good first issue help wanted s: keep open | This is related to #2113, at least in the sense that it would help simplify CMakeLists.txt
Armadillo, BLAS, and LAPACK have nice and simple preexisting cross-platform FindX.cmake files in the cmake repo (and thus shipped with most newer versions of Cmake) which would help remove some special configuration done.
Note that this would also involve slight modifications to the test pipeline related changes made in https://github.com/mlpack/models/pull/52 so that it would no longer have to patch CMakeLists.txt | 1.0 | Use common/simpler FindArmadilo.cmake (and BLAS/LAPACK) - This is related to #2113, at least in the sense that it would help simplify CMakeLists.txt
Armadillo, BLAS, and LAPACK have nice and simple preexisting cross-platform FindX.cmake files in the cmake repo (and thus shipped with most newer versions of Cmake) which would help remove some special configuration done.
Note that this would also involve slight modifications to the test pipeline related changes made in https://github.com/mlpack/models/pull/52 so that it would no longer have to patch CMakeLists.txt | non_priority | use common simpler findarmadilo cmake and blas lapack this is related to at least in the sense that it would help simplify cmakelists txt armadillo blas and lapack have nice and simple preexisting cross platform findx cmake files in the cmake repo and thus shipped with most newer versions of cmake which would help remove some special configuration done note that this would also involve slight modifications to the test pipeline related changes made in so that it would no longer have to patch cmakelists txt | 0 |
163,062 | 20,257,769,403 | IssuesEvent | 2022-02-15 02:10:22 | CMSgov/cms-carts-seds | https://api.github.com/repos/CMSgov/cms-carts-seds | opened | SHF - macpro - master - HIGH - RHEL 7 : aide (RHSA-2022:0473) | security-hub production | **************************************************************
__This issue was generated from Security Hub data and is managed through automation.__
Please do not edit the title or body of this issue, or remove the security-hub tag. All other edits/comments are welcome.
Finding Id: 730373213083/us-east-1/i-0feb83a383f4f6158/10.245.19.126/Nessus/157454
**************************************************************
## Type of Issue:
- [x] Security Hub Finding
## Title:
RHEL 7 : aide (RHSA-2022:0473)
## Id:
730373213083/us-east-1/i-0feb83a383f4f6158/10.245.19.126/Nessus/157454
(You may use this ID to lookup this finding's details in Security Hub)
## Description
The remote Redhat Enterprise Linux 7 host has a package installed that is affected by a vulnerability as referenced in the RHSA-2022:0473 advisory.
- aide: heap-based buffer overflow on outputs larger than B64_BUF (CVE-2021-45417)
Note that Nessus has not tested for this issue but has instead relied only on the application's self-reported version number.
## Remediation
undefined
## AC:
- The security hub finding is resolved or suppressed, indicated by a Workflow Status of Resolved or Suppressed.
| True | SHF - macpro - master - HIGH - RHEL 7 : aide (RHSA-2022:0473) - **************************************************************
__This issue was generated from Security Hub data and is managed through automation.__
Please do not edit the title or body of this issue, or remove the security-hub tag. All other edits/comments are welcome.
Finding Id: 730373213083/us-east-1/i-0feb83a383f4f6158/10.245.19.126/Nessus/157454
**************************************************************
## Type of Issue:
- [x] Security Hub Finding
## Title:
RHEL 7 : aide (RHSA-2022:0473)
## Id:
730373213083/us-east-1/i-0feb83a383f4f6158/10.245.19.126/Nessus/157454
(You may use this ID to lookup this finding's details in Security Hub)
## Description
The remote Redhat Enterprise Linux 7 host has a package installed that is affected by a vulnerability as referenced in the RHSA-2022:0473 advisory.
- aide: heap-based buffer overflow on outputs larger than B64_BUF (CVE-2021-45417)
Note that Nessus has not tested for this issue but has instead relied only on the application's self-reported version number.
## Remediation
undefined
## AC:
- The security hub finding is resolved or suppressed, indicated by a Workflow Status of Resolved or Suppressed.
| non_priority | shf macpro master high rhel aide rhsa this issue was generated from security hub data and is managed through automation please do not edit the title or body of this issue or remove the security hub tag all other edits comments are welcome finding id us east i nessus type of issue security hub finding title rhel aide rhsa id us east i nessus you may use this id to lookup this finding s details in security hub description the remote redhat enterprise linux host has a package installed that is affected by a vulnerability as referenced in the rhsa advisory aide heap based buffer overflow on outputs larger than buf cve note that nessus has not tested for this issue but has instead relied only on the application s self reported version number remediation undefined ac the security hub finding is resolved or suppressed indicated by a workflow status of resolved or suppressed | 0 |
129,741 | 12,417,898,288 | IssuesEvent | 2020-05-22 22:01:07 | glasgowcompbio/PALS | https://api.github.com/repos/glasgowcompbio/PALS | closed | Update readme | documentation manuscript | Following changes to the manuscript, the readme (and the website) needs to be updated to mention 'metabolite set', not just pathways. | 1.0 | Update readme - Following changes to the manuscript, the readme (and the website) needs to be updated to mention 'metabolite set', not just pathways. | non_priority | update readme following changes to the manuscript the readme and the website needs to be updated to mention metabolite set not just pathways | 0 |
406,349 | 27,560,660,347 | IssuesEvent | 2023-03-07 21:42:40 | glygener/glygen-issues | https://api.github.com/repos/glygener/glygen-issues | closed | Checking group of datasets in comparison to old release | documentation backend | I have created a script on how to check a group of datasets (glycan/protein/proteoform), please document and use
$ cd /software/glygen/
$ python3 check-dataset-group.py -m glycan -r 1.12.3
Output
=====
id_count_diff,id_count_new,id_count_old,row_count_diff,row_count_new,row_count_old,field_count_diff,field_count_new,field_count_old,dataset_file_name
0,364,364,0,364,364,0,2,2,glycan_glytoucan_accession_history.csv
0,123404,123404,0,123404,123404,0,1,1,glycan_glytoucanidlist.csv
0,9276,9276,0,280375,280375,0,12,12,glycan_enzyme.csv
0,1475,1475,0,5446,5446,0,9,9,glycan_citations_glytoucan.csv
0,0,0,0,0,0,0,0,0,glycan_citations_biomarkers.csv
-115,0,115,-274,0,274,-9,0,9,glycan_citations_glycomotif.csv
866,8625,7759,866,8625,7759,0,1,1,glycan_fully_determined.csv
4704,22941,18237,26143,98073,71930,0,10,10,glycan_species.csv
6996,30941,23945,10869,52875,42006,0,7,7,glycan_classification.csv
11437,45192,33755,11437,45192,33755,0,10,10,glycan_masterlist.csv
| 1.0 | Checking group of datasets in comparison to old release - I have created a script on how to check a group of datasets (glycan/protein/proteoform), please document and use
$ cd /software/glygen/
$ python3 check-dataset-group.py -m glycan -r 1.12.3
Output
=====
id_count_diff,id_count_new,id_count_old,row_count_diff,row_count_new,row_count_old,field_count_diff,field_count_new,field_count_old,dataset_file_name
0,364,364,0,364,364,0,2,2,glycan_glytoucan_accession_history.csv
0,123404,123404,0,123404,123404,0,1,1,glycan_glytoucanidlist.csv
0,9276,9276,0,280375,280375,0,12,12,glycan_enzyme.csv
0,1475,1475,0,5446,5446,0,9,9,glycan_citations_glytoucan.csv
0,0,0,0,0,0,0,0,0,glycan_citations_biomarkers.csv
-115,0,115,-274,0,274,-9,0,9,glycan_citations_glycomotif.csv
866,8625,7759,866,8625,7759,0,1,1,glycan_fully_determined.csv
4704,22941,18237,26143,98073,71930,0,10,10,glycan_species.csv
6996,30941,23945,10869,52875,42006,0,7,7,glycan_classification.csv
11437,45192,33755,11437,45192,33755,0,10,10,glycan_masterlist.csv
| non_priority | checking group of datasets in comparison to old release i have created a script on how to check a group of datasets glycan protein proteoform please document and use cd software glygen check dataset group py m glycan r output id count diff id count new id count old row count diff row count new row count old field count diff field count new field count old dataset file name glycan glytoucan accession history csv glycan glytoucanidlist csv glycan enzyme csv glycan citations glytoucan csv glycan citations biomarkers csv glycan citations glycomotif csv glycan fully determined csv glycan species csv glycan classification csv glycan masterlist csv | 0 |
143,170 | 21,952,247,128 | IssuesEvent | 2022-05-24 08:57:02 | stores-cedcommerce/Internal---Maana-Creation-StoreRedes--29-April-22 | https://api.github.com/repos/stores-cedcommerce/Internal---Maana-Creation-StoreRedes--29-April-22 | closed | Add wishlist popup UI issue on Desktop tab, and Mobile | Open Ready to test Mobile Tab Design / UI / UX Desktop Product page | Bug - Wishlist popup UI issue on responsive. desktop, tab and mobile UI
Exp - Wishlist popup text should be aligned properly and clear visible on desktop and on responsive.
Ref Link - https://nimb.ws/4xNslA
- https://nimb.ws/EOkJu5 | 1.0 | Add wishlist popup UI issue on Desktop tab, and Mobile - Bug - Wishlist popup UI issue on responsive. desktop, tab and mobile UI
Exp - Wishlist popup text should be aligned properly and clear visible on desktop and on responsive.
Ref Link - https://nimb.ws/4xNslA
- https://nimb.ws/EOkJu5 | non_priority | add wishlist popup ui issue on desktop tab and mobile bug wishlist popup ui issue on responsive desktop tab and mobile ui exp wishlist popup text should be aligned properly and clear visible on desktop and on responsive ref link | 0 |
46,569 | 7,267,355,165 | IssuesEvent | 2018-02-20 04:24:59 | kubernetes/kops | https://api.github.com/repos/kubernetes/kops | closed | AWS uses AWS_PROFILE | P2 area/documentation lifecycle/rotten | AWS switched their env variables in a non backwards compatible way:
https://blogs.aws.amazon.com/security/post/Tx3D6U6WSFGOK2H/A-New-and-Standardized-Way-to-Manage-Credentials-in-the-AWS-SDKs
We should probably warn if AWS_DEFAULT_PROFILE is set but not AWS_PROFILE, or something along those lines.
| 1.0 | AWS uses AWS_PROFILE - AWS switched their env variables in a non backwards compatible way:
https://blogs.aws.amazon.com/security/post/Tx3D6U6WSFGOK2H/A-New-and-Standardized-Way-to-Manage-Credentials-in-the-AWS-SDKs
We should probably warn if AWS_DEFAULT_PROFILE is set but not AWS_PROFILE, or something along those lines.
| non_priority | aws uses aws profile aws switched their env variables in a non backwards compatible way we should probably warn if aws default profile is set but not aws profile or something along those lines | 0 |
78,471 | 15,016,779,529 | IssuesEvent | 2021-02-01 10:01:06 | RihardsJ/mindCoach | https://api.github.com/repos/RihardsJ/mindCoach | opened | Accessability | code review | - [ ] Colour contrast;
- [ ] Tab indexes;
- [ ] Assisting device support (area labels, semantic tags, etc); | 1.0 | Accessability - - [ ] Colour contrast;
- [ ] Tab indexes;
- [ ] Assisting device support (area labels, semantic tags, etc); | non_priority | accessability colour contrast tab indexes assisting device support area labels semantic tags etc | 0 |
21,592 | 6,192,229,776 | IssuesEvent | 2017-07-05 00:15:54 | se-edu/addressbook-level4 | https://api.github.com/repos/se-edu/addressbook-level4 | closed | Shift event handling methods out of UiManager | a-CodeQuality d.Contributors | `UiManager` is catching events such as `JumpToListRequestEvent` which then calls methods to cause the `PersonListPanel` to scroll to the corresponding location.
There is no need for a high-level component such as `UiManager` to catch these events. Rather, the individual components ought to catch these events, as they are already currently handling these events. Using the example given above, the `PersonListPanel` ought to catch the event instead. | 1.0 | Shift event handling methods out of UiManager - `UiManager` is catching events such as `JumpToListRequestEvent` which then calls methods to cause the `PersonListPanel` to scroll to the corresponding location.
There is no need for a high-level component such as `UiManager` to catch these events. Rather, the individual components ought to catch these events, as they are already currently handling these events. Using the example given above, the `PersonListPanel` ought to catch the event instead. | non_priority | shift event handling methods out of uimanager uimanager is catching events such as jumptolistrequestevent which then calls methods to cause the personlistpanel to scroll to the corresponding location there is no need for a high level component such as uimanager to catch these events rather the individual components ought to catch these events as they are already currently handling these events using the example given above the personlistpanel ought to catch the event instead | 0 |
279,035 | 30,702,439,127 | IssuesEvent | 2023-07-27 01:30:17 | artsking/packages_apps_settings_10.0.0_r33 | https://api.github.com/repos/artsking/packages_apps_settings_10.0.0_r33 | reopened | CVE-2021-0434 (High) detected in Settingsandroid-10.0.0_r33, Settingsandroid-10.0.0_r33 | Mend: dependency security vulnerability | ## CVE-2021-0434 - High Severity Vulnerability
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Libraries - <b>Settingsandroid-10.0.0_r33</b>, <b>Settingsandroid-10.0.0_r33</b></p></summary>
<p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png?' width=19 height=20> Vulnerability Details</summary>
<p>
In onReceive of BluetoothPermissionRequest.java, there is a possible phishing attack allowing a malicious Bluetooth device to acquire permissions based on insufficient information presented to the user in the consent dialog. This could lead to local escalation of privilege with no additional execution privileges needed. User interaction is needed for exploitation.Product: AndroidVersions: Android-10 Android-11 Android-9Android ID: A-167403112
<p>Publish Date: 2021-12-15
<p>URL: <a href=https://www.mend.io/vulnerability-database/CVE-2021-0434>CVE-2021-0434</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/cvss3.png' width=19 height=20> CVSS 3 Score Details (<b>7.3</b>)</summary>
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Local
- Attack Complexity: Low
- Privileges Required: Low
- User Interaction: Required
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: High
- Integrity Impact: High
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/suggested_fix.png' width=19 height=20> Suggested Fix</summary>
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://source.android.com/security/bulletin/2021-11-01">https://source.android.com/security/bulletin/2021-11-01</a></p>
<p>Release Date: 2021-12-15</p>
<p>Fix Resolution: android-11.0.0_r43</p>
</p>
</details>
<p></p>
***
Step up your Open Source Security Game with Mend [here](https://www.whitesourcesoftware.com/full_solution_bolt_github) | True | CVE-2021-0434 (High) detected in Settingsandroid-10.0.0_r33, Settingsandroid-10.0.0_r33 - ## CVE-2021-0434 - High Severity Vulnerability
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Libraries - <b>Settingsandroid-10.0.0_r33</b>, <b>Settingsandroid-10.0.0_r33</b></p></summary>
<p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png?' width=19 height=20> Vulnerability Details</summary>
<p>
In onReceive of BluetoothPermissionRequest.java, there is a possible phishing attack allowing a malicious Bluetooth device to acquire permissions based on insufficient information presented to the user in the consent dialog. This could lead to local escalation of privilege with no additional execution privileges needed. User interaction is needed for exploitation.Product: AndroidVersions: Android-10 Android-11 Android-9Android ID: A-167403112
<p>Publish Date: 2021-12-15
<p>URL: <a href=https://www.mend.io/vulnerability-database/CVE-2021-0434>CVE-2021-0434</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/cvss3.png' width=19 height=20> CVSS 3 Score Details (<b>7.3</b>)</summary>
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Local
- Attack Complexity: Low
- Privileges Required: Low
- User Interaction: Required
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: High
- Integrity Impact: High
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/suggested_fix.png' width=19 height=20> Suggested Fix</summary>
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://source.android.com/security/bulletin/2021-11-01">https://source.android.com/security/bulletin/2021-11-01</a></p>
<p>Release Date: 2021-12-15</p>
<p>Fix Resolution: android-11.0.0_r43</p>
</p>
</details>
<p></p>
***
Step up your Open Source Security Game with Mend [here](https://www.whitesourcesoftware.com/full_solution_bolt_github) | non_priority | cve high detected in settingsandroid settingsandroid cve high severity vulnerability vulnerable libraries settingsandroid settingsandroid vulnerability details in onreceive of bluetoothpermissionrequest java there is a possible phishing attack allowing a malicious bluetooth device to acquire permissions based on insufficient information presented to the user in the consent dialog this could lead to local escalation of privilege with no additional execution privileges needed user interaction is needed for exploitation product androidversions android android android id a publish date url a href cvss score details base score metrics exploitability metrics attack vector local attack complexity low privileges required low user interaction required scope unchanged impact metrics confidentiality impact high integrity impact high availability impact high for more information on scores click a href suggested fix type upgrade version origin a href release date fix resolution android step up your open source security game with mend | 0 |
243,777 | 20,573,350,396 | IssuesEvent | 2022-03-04 00:04:08 | yugabyte/yugabyte-db | https://api.github.com/repos/yugabyte/yugabyte-db | opened | [flaky test] TabletSplitITest.TestBackfillDuringSplit and TabletSplitITest.TestSplitDuringBackfill | kind/failing-test area/docdb | ### Description
https://detective-gcp.dev.yugabyte.com/stability/test?branch=master&build_type=all&class=TabletSplitITest&name=TestBackfillDuringSplit&platform=centos
https://detective-gcp.dev.yugabyte.com/stability/test?branch=master&build_type=all&class=TabletSplitITest&name=TestSplitDuringBackfill&platform=centos | 1.0 | [flaky test] TabletSplitITest.TestBackfillDuringSplit and TabletSplitITest.TestSplitDuringBackfill - ### Description
https://detective-gcp.dev.yugabyte.com/stability/test?branch=master&build_type=all&class=TabletSplitITest&name=TestBackfillDuringSplit&platform=centos
https://detective-gcp.dev.yugabyte.com/stability/test?branch=master&build_type=all&class=TabletSplitITest&name=TestSplitDuringBackfill&platform=centos | non_priority | tabletsplititest testbackfillduringsplit and tabletsplititest testsplitduringbackfill description | 0 |
173,210 | 27,400,642,907 | IssuesEvent | 2023-03-01 00:11:26 | hackforla/CivicTechJobs | https://api.github.com/repos/hackforla/CivicTechJobs | closed | Qualifier Page - Role Prototype | role: UI/UX - Design size: 1pt feature: User Research | ### Dependency
- [x] #293
- [x] #308
### Overview
As a designer, we need to figure out which way to select roles is better/easier for users. For this issue, we will create a clickable Figma prototype to test with users to decide.
### Action Items
- [x] Create prototype in Figma
- [x] Send prototype link to UXR team for review
- [ ] Help UXRs with leading/transcribing usability sessions (if needed)
### Resources/Instructions
TBD | 1.0 | Qualifier Page - Role Prototype - ### Dependency
- [x] #293
- [x] #308
### Overview
As a designer, we need to figure out which way to select roles is better/easier for users. For this issue, we will create a clickable Figma prototype to test with users to decide.
### Action Items
- [x] Create prototype in Figma
- [x] Send prototype link to UXR team for review
- [ ] Help UXRs with leading/transcribing usability sessions (if needed)
### Resources/Instructions
TBD | non_priority | qualifier page role prototype dependency overview as a designer we need to figure out which way to select roles is better easier for users for this issue we will create a clickable figma prototype to test with users to decide action items create prototype in figma send prototype link to uxr team for review help uxrs with leading transcribing usability sessions if needed resources instructions tbd | 0 |
23,895 | 5,002,703,535 | IssuesEvent | 2016-12-11 14:53:59 | PhilippBaschke/acf-pro-installer | https://api.github.com/repos/PhilippBaschke/acf-pro-installer | closed | "no matches found: advanced-custom-fields/advanced-custom-fields-pro:*" | status: in progress type: documentation type: question | I think included everything correctly. Have a version number specified - `5.5.1` - but when I require with the wildcard version, I get...
```bash
composer require advanced-custom-fields/advanced-custom-fields-pro:*
zsh: no matches found: advanced-custom-fields/advanced-custom-fields-pro:*
```
When I define the version number
```bash
composer require advanced-custom-fields/advanced-custom-fields-pro:5.5.1
```
it works.
| 1.0 | "no matches found: advanced-custom-fields/advanced-custom-fields-pro:*" - I think included everything correctly. Have a version number specified - `5.5.1` - but when I require with the wildcard version, I get...
```bash
composer require advanced-custom-fields/advanced-custom-fields-pro:*
zsh: no matches found: advanced-custom-fields/advanced-custom-fields-pro:*
```
When I define the version number
```bash
composer require advanced-custom-fields/advanced-custom-fields-pro:5.5.1
```
it works.
| non_priority | no matches found advanced custom fields advanced custom fields pro i think included everything correctly have a version number specified but when i require with the wildcard version i get bash composer require advanced custom fields advanced custom fields pro zsh no matches found advanced custom fields advanced custom fields pro when i define the version number bash composer require advanced custom fields advanced custom fields pro it works | 0 |
2,135 | 2,882,158,478 | IssuesEvent | 2015-06-11 01:50:02 | mitchellh/packer | https://api.github.com/repos/mitchellh/packer | closed | Digital Ocean NYC2 build error | bug builder/digitalocean | On LON1, NYC3 I have no problems building a droplet and creating the snapshot, however on NYC2 after the build process completes I seem to run into a shutdown/snapshot race issue
NYC2
```
==> digitalocean: Gracefully shutting down droplet...
==> digitalocean: Creating snapshot: staging-14.10-snap
==> digitalocean: Error creating snapshot: digitalocean request error: map[id:unprocessable_entity message:Droplet already has a pending event.]
==> digitalocean: Destroying droplet...
==> digitalocean: Error destroying droplet. Please destroy it manually: curl 'https://api.digitalocean.com/droplets/[droplet_id_redacted]/destroy?client_id=&api_key='
==> digitalocean: Deleting temporary ssh key...
Build 'digitalocean' errored: Error creating snapshot: digitalocean request error: map[id:unprocessable_entity message:Droplet already has a pending event.]
```
NYC3
```
==> digitalocean: Gracefully shutting down droplet...
==> digitalocean: Creating snapshot: staging-14.10-snap
==> digitalocean: Waiting for snapshot to complete...
==> digitalocean: Destroying droplet...
==> digitalocean: Deleting temporary ssh key...
Build 'digitalocean' finished.
```
I originally ask this over at the [DO API](https://github.com/digitalocean/api-v2/issues/129) repo but they seem to think it's a packer issue, that packer isn't waiting for the shutdown to finish before running the snapshot action. | 1.0 | Digital Ocean NYC2 build error - On LON1, NYC3 I have no problems building a droplet and creating the snapshot, however on NYC2 after the build process completes I seem to run into a shutdown/snapshot race issue
NYC2
```
==> digitalocean: Gracefully shutting down droplet...
==> digitalocean: Creating snapshot: staging-14.10-snap
==> digitalocean: Error creating snapshot: digitalocean request error: map[id:unprocessable_entity message:Droplet already has a pending event.]
==> digitalocean: Destroying droplet...
==> digitalocean: Error destroying droplet. Please destroy it manually: curl 'https://api.digitalocean.com/droplets/[droplet_id_redacted]/destroy?client_id=&api_key='
==> digitalocean: Deleting temporary ssh key...
Build 'digitalocean' errored: Error creating snapshot: digitalocean request error: map[id:unprocessable_entity message:Droplet already has a pending event.]
```
NYC3
```
==> digitalocean: Gracefully shutting down droplet...
==> digitalocean: Creating snapshot: staging-14.10-snap
==> digitalocean: Waiting for snapshot to complete...
==> digitalocean: Destroying droplet...
==> digitalocean: Deleting temporary ssh key...
Build 'digitalocean' finished.
```
I originally ask this over at the [DO API](https://github.com/digitalocean/api-v2/issues/129) repo but they seem to think it's a packer issue, that packer isn't waiting for the shutdown to finish before running the snapshot action. | non_priority | digital ocean build error on i have no problems building a droplet and creating the snapshot however on after the build process completes i seem to run into a shutdown snapshot race issue digitalocean gracefully shutting down droplet digitalocean creating snapshot staging snap digitalocean error creating snapshot digitalocean request error map digitalocean destroying droplet digitalocean error destroying droplet please destroy it manually curl destroy client id api key digitalocean deleting temporary ssh key build digitalocean errored error creating snapshot digitalocean request error map digitalocean gracefully shutting down droplet digitalocean creating snapshot staging snap digitalocean waiting for snapshot to complete digitalocean destroying droplet digitalocean deleting temporary ssh key build digitalocean finished i originally ask this over at the repo but they seem to think it s a packer issue that packer isn t waiting for the shutdown to finish before running the snapshot action | 0 |
287,660 | 24,849,299,574 | IssuesEvent | 2022-10-26 18:33:56 | rapidsai/cudf | https://api.github.com/repos/rapidsai/cudf | closed | [BUG] Arrow S3 tests don't throw an error when CUDF_ENABLE_ARROW_S3 is off | bug tests libcudf CMake inactive-30d | **Describe the bug**
The C++ test `ArrowIOTest.S3URIWhenNotEnabled` expects that if the CMake variable `CUDF_ENABLE_ARROW_S3` is off, creating an `cudf::io::arrow_io_source` from an S3 path will throw a `cudf::logic_error`. However, that isn't necessarily the case. The new default setting of `CUDF_ENABLE_ARROW_S3=OFF` means that Arrow S3 support is not enabled _if Arrow is built from source_. If a pre-built Arrow library is found, it will be used and the value of `CUDF_ENABLE_ARROW_S3` is irrelevant. In most cases, I expect that pre-built Arrow libraries will have S3 support enabled (Arrow conda packages have it turned on).
```
[ RUN ] ArrowIOTest.S3URIWhenNotEnabled
/home/bdice/rapids1/cudf/cpp/tests/io/arrow_io_source_test.cpp:91: Failure
Expected: std::make_unique<cudf::io::arrow_io_source>(s3_uri) throws an exception of type cudf::logic_error.
Actual: it throws nothing.
[ FAILED ] ArrowIOTest.S3URIWhenNotEnabled (6740 ms)
```
**Expected behavior**
This test should not fail. I'm not sure if we can determine at runtime whether the Arrow library being used has S3 support or not, but that's what we should be checking against rather than the [compile-time definition of `S3_ENABLED`](https://github.com/rapidsai/cudf/blob/abd4302d6d57c080323068f7b58f26b2d76e26fb/cpp/tests/io/arrow_io_source_test.cpp#L64).
We can't know from `CUDF_ENABLE_ARROW_S3` alone if the Arrow library will be able to read S3 files or not, unless we know that libcudf's CMake also built Arrow from source. We could have the opposite problem with `S3FileSystem` when the `CUDF_ENABLE_ARROW_S3` flag is enabled, if the found Arrow library wasn't built with S3 support.
**Environment overview (please complete the following information)**
- Environment location: rapids-compose container, cudf 22.10 development branch, Arrow from conda package
- Method of cuDF install: source | 1.0 | [BUG] Arrow S3 tests don't throw an error when CUDF_ENABLE_ARROW_S3 is off - **Describe the bug**
The C++ test `ArrowIOTest.S3URIWhenNotEnabled` expects that if the CMake variable `CUDF_ENABLE_ARROW_S3` is off, creating an `cudf::io::arrow_io_source` from an S3 path will throw a `cudf::logic_error`. However, that isn't necessarily the case. The new default setting of `CUDF_ENABLE_ARROW_S3=OFF` means that Arrow S3 support is not enabled _if Arrow is built from source_. If a pre-built Arrow library is found, it will be used and the value of `CUDF_ENABLE_ARROW_S3` is irrelevant. In most cases, I expect that pre-built Arrow libraries will have S3 support enabled (Arrow conda packages have it turned on).
```
[ RUN ] ArrowIOTest.S3URIWhenNotEnabled
/home/bdice/rapids1/cudf/cpp/tests/io/arrow_io_source_test.cpp:91: Failure
Expected: std::make_unique<cudf::io::arrow_io_source>(s3_uri) throws an exception of type cudf::logic_error.
Actual: it throws nothing.
[ FAILED ] ArrowIOTest.S3URIWhenNotEnabled (6740 ms)
```
**Expected behavior**
This test should not fail. I'm not sure if we can determine at runtime whether the Arrow library being used has S3 support or not, but that's what we should be checking against rather than the [compile-time definition of `S3_ENABLED`](https://github.com/rapidsai/cudf/blob/abd4302d6d57c080323068f7b58f26b2d76e26fb/cpp/tests/io/arrow_io_source_test.cpp#L64).
We can't know from `CUDF_ENABLE_ARROW_S3` alone if the Arrow library will be able to read S3 files or not, unless we know that libcudf's CMake also built Arrow from source. We could have the opposite problem with `S3FileSystem` when the `CUDF_ENABLE_ARROW_S3` flag is enabled, if the found Arrow library wasn't built with S3 support.
**Environment overview (please complete the following information)**
- Environment location: rapids-compose container, cudf 22.10 development branch, Arrow from conda package
- Method of cuDF install: source | non_priority | arrow tests don t throw an error when cudf enable arrow is off describe the bug the c test arrowiotest expects that if the cmake variable cudf enable arrow is off creating an cudf io arrow io source from an path will throw a cudf logic error however that isn t necessarily the case the new default setting of cudf enable arrow off means that arrow support is not enabled if arrow is built from source if a pre built arrow library is found it will be used and the value of cudf enable arrow is irrelevant in most cases i expect that pre built arrow libraries will have support enabled arrow conda packages have it turned on arrowiotest home bdice cudf cpp tests io arrow io source test cpp failure expected std make unique uri throws an exception of type cudf logic error actual it throws nothing arrowiotest ms expected behavior this test should not fail i m not sure if we can determine at runtime whether the arrow library being used has support or not but that s what we should be checking against rather than the we can t know from cudf enable arrow alone if the arrow library will be able to read files or not unless we know that libcudf s cmake also built arrow from source we could have the opposite problem with when the cudf enable arrow flag is enabled if the found arrow library wasn t built with support environment overview please complete the following information environment location rapids compose container cudf development branch arrow from conda package method of cudf install source | 0 |
43,631 | 9,476,315,909 | IssuesEvent | 2019-04-19 14:41:28 | istio/istio | https://api.github.com/repos/istio/istio | opened | Multicluster E2E test needs to be on test grid | area/test and release code mauve | https://testgrid.k8s.io/istio-presubmits#Summary&width=20 no multicluster test present
@utka @john-a-joyce | 1.0 | Multicluster E2E test needs to be on test grid - https://testgrid.k8s.io/istio-presubmits#Summary&width=20 no multicluster test present
@utka @john-a-joyce | non_priority | multicluster test needs to be on test grid no multicluster test present utka john a joyce | 0 |
5,034 | 2,900,267,870 | IssuesEvent | 2015-06-17 15:37:39 | Microsoft/Office-Online-Test-Tools-and-Documentation | https://api.github.com/repos/Microsoft/Office-Online-Test-Tools-and-Documentation | opened | Describe functional differences between actions in more detail | documentation enhancement | For example, embedview makes some assumptions about how it should behave and is less customizable/doesn't support some functionality. We need to describe these differences/limitations in more detail.
Related to #9. | 1.0 | Describe functional differences between actions in more detail - For example, embedview makes some assumptions about how it should behave and is less customizable/doesn't support some functionality. We need to describe these differences/limitations in more detail.
Related to #9. | non_priority | describe functional differences between actions in more detail for example embedview makes some assumptions about how it should behave and is less customizable doesn t support some functionality we need to describe these differences limitations in more detail related to | 0 |
385,689 | 26,649,351,845 | IssuesEvent | 2023-01-25 12:32:18 | lumapu/ahoy | https://api.github.com/repos/lumapu/ahoy | closed | MQTT -> Mosquitto -> Telegraf -> InfluxDB | documentation question resolved | Hi, habe Probleme mit der Konfiguration von Telegraf betreffend JSON Objekte der Ahoy. Ich würde ja gerne das Plugin im Telegraf Consumer erstellen. Mir fehlt aber die Basis wie die JSON Strukturen am Input von Telegraf aussehen. Ich sehe zwar Strukturen im MQTTFx, weiss aber nicht wirklich ob diese passen. Hat jemand schon mal das telegraf.conf File entsprechend konfiguriert? Wäre für Hinweise, Tipps, oder gar einen Auszug aus einem telegraf.conf File dankbar. | 1.0 | MQTT -> Mosquitto -> Telegraf -> InfluxDB - Hi, habe Probleme mit der Konfiguration von Telegraf betreffend JSON Objekte der Ahoy. Ich würde ja gerne das Plugin im Telegraf Consumer erstellen. Mir fehlt aber die Basis wie die JSON Strukturen am Input von Telegraf aussehen. Ich sehe zwar Strukturen im MQTTFx, weiss aber nicht wirklich ob diese passen. Hat jemand schon mal das telegraf.conf File entsprechend konfiguriert? Wäre für Hinweise, Tipps, oder gar einen Auszug aus einem telegraf.conf File dankbar. | non_priority | mqtt mosquitto telegraf influxdb hi habe probleme mit der konfiguration von telegraf betreffend json objekte der ahoy ich würde ja gerne das plugin im telegraf consumer erstellen mir fehlt aber die basis wie die json strukturen am input von telegraf aussehen ich sehe zwar strukturen im mqttfx weiss aber nicht wirklich ob diese passen hat jemand schon mal das telegraf conf file entsprechend konfiguriert wäre für hinweise tipps oder gar einen auszug aus einem telegraf conf file dankbar | 0 |
5,674 | 29,507,751,979 | IssuesEvent | 2023-06-03 14:24:45 | jupyter-naas/awesome-notebooks | https://api.github.com/repos/jupyter-naas/awesome-notebooks | closed | Naas - Send image asset to Notion page | templates maintainer | This notebook sends an naas image asset to a Notion page. If your page is in a notion database, you will be able to vizualise the chart in Gallery (display page content). The image asset will be updated (deleted and added) to make sure the graph display is always up to date in Notion.
| True | Naas - Send image asset to Notion page - This notebook sends an naas image asset to a Notion page. If your page is in a notion database, you will be able to vizualise the chart in Gallery (display page content). The image asset will be updated (deleted and added) to make sure the graph display is always up to date in Notion.
| non_priority | naas send image asset to notion page this notebook sends an naas image asset to a notion page if your page is in a notion database you will be able to vizualise the chart in gallery display page content the image asset will be updated deleted and added to make sure the graph display is always up to date in notion | 0 |
117,009 | 11,945,622,993 | IssuesEvent | 2020-04-03 06:19:03 | fatin99/ped | https://api.github.com/repos/fatin99/ped | opened | Diet command not working | severity.Medium type.DocumentationBug | 
Entering diet does not allow the user to go to the diet content page. Was only able to do so after entering "1" as shown by the programme output, however the instructions were not made clear in the user guide.
| 1.0 | Diet command not working - 
Entering diet does not allow the user to go to the diet content page. Was only able to do so after entering "1" as shown by the programme output, however the instructions were not made clear in the user guide.
| non_priority | diet command not working entering diet does not allow the user to go to the diet content page was only able to do so after entering as shown by the programme output however the instructions were not made clear in the user guide | 0 |
132,746 | 28,314,021,541 | IssuesEvent | 2023-04-10 17:57:20 | anegostudios/VintageStory-Issues | https://api.github.com/repos/anegostudios/VintageStory-Issues | opened | ovenFuelShape is hardcoded for items with isClayOvenFuel attribute | status: confirmed department: code version: 1.18 | ### Game Version
1.18.0-rc.2
### Platform
Windows
### Modded
None
### SP/MP
None
### Description
_No response_
### How to reproduce
_No response_
### Screenshots
_No response_
### Logs
_No response_ | 1.0 | ovenFuelShape is hardcoded for items with isClayOvenFuel attribute - ### Game Version
1.18.0-rc.2
### Platform
Windows
### Modded
None
### SP/MP
None
### Description
_No response_
### How to reproduce
_No response_
### Screenshots
_No response_
### Logs
_No response_ | non_priority | ovenfuelshape is hardcoded for items with isclayovenfuel attribute game version rc platform windows modded none sp mp none description no response how to reproduce no response screenshots no response logs no response | 0 |
68,777 | 29,509,096,276 | IssuesEvent | 2023-06-03 17:42:07 | hashicorp/terraform-provider-aws | https://api.github.com/repos/hashicorp/terraform-provider-aws | closed | aws_acm_certificate updates statefile during re-import even if action was rejected by AWS | bug service/acm stale | <!---
Please note the following potential times when an issue might be in Terraform core:
* [Configuration Language](https://www.terraform.io/docs/configuration/index.html) or resource ordering issues
* [State](https://www.terraform.io/docs/state/index.html) and [State Backend](https://www.terraform.io/docs/backends/index.html) issues
* [Provisioner](https://www.terraform.io/docs/provisioners/index.html) issues
* [Registry](https://registry.terraform.io/) issues
* Spans resources across multiple providers
If you are running into one of these scenarios, we recommend opening an issue in the [Terraform core repository](https://github.com/hashicorp/terraform/) instead.
--->
<!--- Please keep this note for the community --->
### Community Note
* Please vote on this issue by adding a 👍 [reaction](https://blog.github.com/2016-03-10-add-reactions-to-pull-requests-issues-and-comments/) to the original issue to help the community and maintainers prioritize this request
* Please do not leave "+1" or other comments that do not add relevant new information or questions, they generate extra noise for issue followers and do not help prioritize the request
* If you are interested in working on this issue or have submitted a pull request, please leave a comment
<!--- Thank you for keeping this note for the community --->
### Terraform CLI and Terraform AWS Provider Version
<!--- Please run `terraform -v` to show the Terraform core version and provider version(s). If you are not running the latest version of Terraform or the provider, please upgrade because your issue may have already been fixed. [Terraform documentation on provider versioning](https://www.terraform.io/docs/configuration/providers.html#provider-versions). --->
Terraform version: 0.13.5
AWS Provider: 3.37.0
### Affected Resource(s)
<!--- Please list the affected resources and data sources. --->
* aws_acm_certificate
### Terraform Configuration Files
<!--- Information about code formatting: https://help.github.com/articles/basic-writing-and-formatting-syntax/#quoting-code --->
Please include all Terraform configurations required to reproduce the bug. Bug reports without a functional reproduction may be closed without investigation.
```hcl
module "acm" {
source = "../source-dir/acm"
acmName = var.sslNetwork
acmCert = local.ssl.crt
acmKey = local.ssl.key
acmChain = local.ssl.ca
ourtags = local.Tags
}
resource "aws_acm_certificate" "cert" {
private_key = var.acmKey
certificate_body = var.acmCert
certificate_chain = var.acmChain
tags = merge(
var.ourtags,
map(
"Name",var.acmName
)
)
}
```
### Expected Behavior
<!--- What should have happened? --->
When re-importing a certificate, AWS has a requirement that Extended Key Usage extensions cannot be removed in the cert being imported (https://docs.aws.amazon.com/acm/latest/userguide/import-reimport.html). If the cert being re-imported has fewer extensions than the existing cert in AWS Certificate Manager, the following error occurs:
Error: error re-importing ACM Certificate (arn:aws:acm:<rest of ARN obfuscated>): ValidationException: New certificate is missing one or more Extended Key Usages supported by the currently imported certificate
No changes to the statefile should occur related to the Cert as the new cert was not successfully imported.
### Actual Behavior
<!--- What actually happened? --->
When this error is encountered, the statefile is still updated with the new certificate information even though no update has actually occurred in AWS Certificate Manager.
### Steps to Reproduce
<!--- Please list the steps required to reproduce the issue. --->
1. Import a Certificate in to AWS Certificate Manager with 2 or more Extended Usage Key extensions (ex: TLS Web server authentication, and TLS Web client authentication)
2. Obtain a new certificate with 1 fewer extension
3. Re-import the certificate with the new cert (which should error)
4. Review cert in statefile (which will be the new cert that failed to import)
* #0000
| 1.0 | aws_acm_certificate updates statefile during re-import even if action was rejected by AWS - <!---
Please note the following potential times when an issue might be in Terraform core:
* [Configuration Language](https://www.terraform.io/docs/configuration/index.html) or resource ordering issues
* [State](https://www.terraform.io/docs/state/index.html) and [State Backend](https://www.terraform.io/docs/backends/index.html) issues
* [Provisioner](https://www.terraform.io/docs/provisioners/index.html) issues
* [Registry](https://registry.terraform.io/) issues
* Spans resources across multiple providers
If you are running into one of these scenarios, we recommend opening an issue in the [Terraform core repository](https://github.com/hashicorp/terraform/) instead.
--->
<!--- Please keep this note for the community --->
### Community Note
* Please vote on this issue by adding a 👍 [reaction](https://blog.github.com/2016-03-10-add-reactions-to-pull-requests-issues-and-comments/) to the original issue to help the community and maintainers prioritize this request
* Please do not leave "+1" or other comments that do not add relevant new information or questions, they generate extra noise for issue followers and do not help prioritize the request
* If you are interested in working on this issue or have submitted a pull request, please leave a comment
<!--- Thank you for keeping this note for the community --->
### Terraform CLI and Terraform AWS Provider Version
<!--- Please run `terraform -v` to show the Terraform core version and provider version(s). If you are not running the latest version of Terraform or the provider, please upgrade because your issue may have already been fixed. [Terraform documentation on provider versioning](https://www.terraform.io/docs/configuration/providers.html#provider-versions). --->
Terraform version: 0.13.5
AWS Provider: 3.37.0
### Affected Resource(s)
<!--- Please list the affected resources and data sources. --->
* aws_acm_certificate
### Terraform Configuration Files
<!--- Information about code formatting: https://help.github.com/articles/basic-writing-and-formatting-syntax/#quoting-code --->
Please include all Terraform configurations required to reproduce the bug. Bug reports without a functional reproduction may be closed without investigation.
```hcl
module "acm" {
source = "../source-dir/acm"
acmName = var.sslNetwork
acmCert = local.ssl.crt
acmKey = local.ssl.key
acmChain = local.ssl.ca
ourtags = local.Tags
}
resource "aws_acm_certificate" "cert" {
private_key = var.acmKey
certificate_body = var.acmCert
certificate_chain = var.acmChain
tags = merge(
var.ourtags,
map(
"Name",var.acmName
)
)
}
```
### Expected Behavior
<!--- What should have happened? --->
When re-importing a certificate, AWS has a requirement that Extended Key Usage extensions cannot be removed in the cert being imported (https://docs.aws.amazon.com/acm/latest/userguide/import-reimport.html). If the cert being re-imported has fewer extensions than the existing cert in AWS Certificate Manager, the following error occurs:
Error: error re-importing ACM Certificate (arn:aws:acm:<rest of ARN obfuscated>): ValidationException: New certificate is missing one or more Extended Key Usages supported by the currently imported certificate
No changes to the statefile should occur related to the Cert as the new cert was not successfully imported.
### Actual Behavior
<!--- What actually happened? --->
When this error is encountered, the statefile is still updated with the new certificate information even though no update has actually occurred in AWS Certificate Manager.
### Steps to Reproduce
<!--- Please list the steps required to reproduce the issue. --->
1. Import a Certificate in to AWS Certificate Manager with 2 or more Extended Usage Key extensions (ex: TLS Web server authentication, and TLS Web client authentication)
2. Obtain a new certificate with 1 fewer extension
3. Re-import the certificate with the new cert (which should error)
4. Review cert in statefile (which will be the new cert that failed to import)
* #0000
| non_priority | aws acm certificate updates statefile during re import even if action was rejected by aws please note the following potential times when an issue might be in terraform core or resource ordering issues and issues issues issues spans resources across multiple providers if you are running into one of these scenarios we recommend opening an issue in the instead community note please vote on this issue by adding a 👍 to the original issue to help the community and maintainers prioritize this request please do not leave or other comments that do not add relevant new information or questions they generate extra noise for issue followers and do not help prioritize the request if you are interested in working on this issue or have submitted a pull request please leave a comment terraform cli and terraform aws provider version terraform version aws provider affected resource s aws acm certificate terraform configuration files please include all terraform configurations required to reproduce the bug bug reports without a functional reproduction may be closed without investigation hcl module acm source source dir acm acmname var sslnetwork acmcert local ssl crt acmkey local ssl key acmchain local ssl ca ourtags local tags resource aws acm certificate cert private key var acmkey certificate body var acmcert certificate chain var acmchain tags merge var ourtags map name var acmname expected behavior when re importing a certificate aws has a requirement that extended key usage extensions cannot be removed in the cert being imported if the cert being re imported has fewer extensions than the existing cert in aws certificate manager the following error occurs error error re importing acm certificate arn aws acm validationexception new certificate is missing one or more extended key usages supported by the currently imported certificate no changes to the statefile should occur related to the cert as the new cert was not successfully imported actual behavior when this error is encountered the statefile is still updated with the new certificate information even though no update has actually occurred in aws certificate manager steps to reproduce import a certificate in to aws certificate manager with or more extended usage key extensions ex tls web server authentication and tls web client authentication obtain a new certificate with fewer extension re import the certificate with the new cert which should error review cert in statefile which will be the new cert that failed to import | 0 |
348,145 | 24,907,428,751 | IssuesEvent | 2022-10-29 12:41:03 | DeveloperAcademy-POSTECH/MacC-Team-EarthValley80-Server | https://api.github.com/repos/DeveloperAcademy-POSTECH/MacC-Team-EarthValley80-Server | opened | [Config] 프로젝트 이름 변경 | 📕Documentation 🛠Configuration | ## 💡 무엇을/어떻게/왜 설정하나요?
<!-- 이슈에 대한 내용을 설명해주세요. -->
`nier` -> `yomojomo` 로 gradle 프로젝트 이름 변경
## 📝 todo
- [ ] gradle 프로젝트 이름 변경!
<!-- 해야 할 일들을 적어주세요. -->
| 1.0 | [Config] 프로젝트 이름 변경 - ## 💡 무엇을/어떻게/왜 설정하나요?
<!-- 이슈에 대한 내용을 설명해주세요. -->
`nier` -> `yomojomo` 로 gradle 프로젝트 이름 변경
## 📝 todo
- [ ] gradle 프로젝트 이름 변경!
<!-- 해야 할 일들을 적어주세요. -->
| non_priority | 프로젝트 이름 변경 💡 무엇을 어떻게 왜 설정하나요 nier yomojomo 로 gradle 프로젝트 이름 변경 📝 todo gradle 프로젝트 이름 변경 | 0 |
250,061 | 21,259,230,407 | IssuesEvent | 2022-04-13 00:59:54 | RamiMustafa/WAF_Sec_Test | https://api.github.com/repos/RamiMustafa/WAF_Sec_Test | opened | Mitigate DDoS attacks | WARP-Import WAF_Sec_Test Security Networking & Connectivity Endpoints | <a href="https://docs.microsoft.com/azure/architecture/framework/security/design-network-endpoints#mitigate-ddos-attacks">Mitigate DDoS attacks</a>
<p><b>Why Consider This?</b></p>
DDoS attacks can be debilitating and completely block access to, or take down, your services. The worst time to plan a DDoS strategy is while under DDoS attack.
<p><b>Context</b></p>
<p><span>The major cloud service providers offer DDoS protection of services of varying effectiveness and capacity. The cloud service providers typically provide two DDoS protection options:</span></p><ul style="list-style-type:disc"><li value="1" style="text-indent: 0px;"><span>DDoS protection at the cloud network fabric level - all customers of the cloud service provider benefit from these protections. The protection is usually focused at the network (layer 3) level.</span></li><li value="2" style="margin-right: 0px;text-indent: 0px;"><span>DDoS protection at higher levels that profile your services - this kind of protection will baseline your deployments and then use machine learning techniques to detect anomalous traffic and proactively protect based on their protection before there is service degradation</span></li></ul><p><span>It's recommended to adopt advanced protection for any services where downtime will have negative impact on the business.</span></p>
<p><b>Suggested Actions</b></p>
<p><span>Identify critical workloads that are susceptible to DDoS attacks and enable Distributed Denial of Service (DDoS) mitigations for all business-critical web applications and services.</span></p>
<p><b>Learn More</b></p>
<p><a href="https://azure.microsoft.com/en-us/services/ddos-protection" target="_blank"><span>Mitigate DDoS attacks</span></a><span /></p> | 1.0 | Mitigate DDoS attacks - <a href="https://docs.microsoft.com/azure/architecture/framework/security/design-network-endpoints#mitigate-ddos-attacks">Mitigate DDoS attacks</a>
<p><b>Why Consider This?</b></p>
DDoS attacks can be debilitating and completely block access to, or take down, your services. The worst time to plan a DDoS strategy is while under DDoS attack.
<p><b>Context</b></p>
<p><span>The major cloud service providers offer DDoS protection of services of varying effectiveness and capacity. The cloud service providers typically provide two DDoS protection options:</span></p><ul style="list-style-type:disc"><li value="1" style="text-indent: 0px;"><span>DDoS protection at the cloud network fabric level - all customers of the cloud service provider benefit from these protections. The protection is usually focused at the network (layer 3) level.</span></li><li value="2" style="margin-right: 0px;text-indent: 0px;"><span>DDoS protection at higher levels that profile your services - this kind of protection will baseline your deployments and then use machine learning techniques to detect anomalous traffic and proactively protect based on their protection before there is service degradation</span></li></ul><p><span>It's recommended to adopt advanced protection for any services where downtime will have negative impact on the business.</span></p>
<p><b>Suggested Actions</b></p>
<p><span>Identify critical workloads that are susceptible to DDoS attacks and enable Distributed Denial of Service (DDoS) mitigations for all business-critical web applications and services.</span></p>
<p><b>Learn More</b></p>
<p><a href="https://azure.microsoft.com/en-us/services/ddos-protection" target="_blank"><span>Mitigate DDoS attacks</span></a><span /></p> | non_priority | mitigate ddos attacks why consider this ddos attacks can be debilitating and completely block access to or take down your services the worst time to plan a ddos strategy is while under ddos attack context the major cloud service providers offer ddos protection of services of varying effectiveness and capacity the cloud service providers typically provide two ddos protection options ddos protection at the cloud network fabric level all customers of the cloud service provider benefit from these protections the protection is usually focused at the network layer level ddos protection at higher levels that profile your services this kind of protection will baseline your deployments and then use machine learning techniques to detect anomalous traffic and proactively protect based on their protection before there is service degradation it s recommended to adopt advanced protection for any services where downtime will have negative impact on the business suggested actions identify critical workloads that are susceptible to ddos attacks and enable distributed denial of service ddos mitigations for all business critical web applications and services learn more mitigate ddos attacks | 0 |
297,233 | 25,712,121,944 | IssuesEvent | 2022-12-07 07:36:31 | OpenRefine/OpenRefine | https://api.github.com/repos/OpenRefine/OpenRefine | closed | XLSX test failure | bug tests | A test instability seems to have been uncovered by the CI: https://github.com/OpenRefine/OpenRefine/actions/runs/3627223760/jobs/6116914771
```
Error: Tests run: 704, Failures: 1, Errors: 0, Skipped: 0, Time elapsed: 38.319 s <<< FAILURE! - in TestSuite
Error: readXlsxAsText(com.google.refine.importers.ExcelImporterTests) Time elapsed: 0.04 s <<< FAILURE!
java.lang.AssertionError: expected [2022-12-06 06:55] but found [2022-12-06 06:56]
at com.google.refine.importers.ExcelImporterTests.readXlsxAsText(ExcelImporterTests.java:274)
```
The same problem appears in a different job of the same run:
https://github.com/OpenRefine/OpenRefine/actions/runs/3627223760/jobs/6116914844 | 1.0 | XLSX test failure - A test instability seems to have been uncovered by the CI: https://github.com/OpenRefine/OpenRefine/actions/runs/3627223760/jobs/6116914771
```
Error: Tests run: 704, Failures: 1, Errors: 0, Skipped: 0, Time elapsed: 38.319 s <<< FAILURE! - in TestSuite
Error: readXlsxAsText(com.google.refine.importers.ExcelImporterTests) Time elapsed: 0.04 s <<< FAILURE!
java.lang.AssertionError: expected [2022-12-06 06:55] but found [2022-12-06 06:56]
at com.google.refine.importers.ExcelImporterTests.readXlsxAsText(ExcelImporterTests.java:274)
```
The same problem appears in a different job of the same run:
https://github.com/OpenRefine/OpenRefine/actions/runs/3627223760/jobs/6116914844 | non_priority | xlsx test failure a test instability seems to have been uncovered by the ci error tests run failures errors skipped time elapsed s failure in testsuite error readxlsxastext com google refine importers excelimportertests time elapsed s failure java lang assertionerror expected but found at com google refine importers excelimportertests readxlsxastext excelimportertests java the same problem appears in a different job of the same run | 0 |
54,919 | 6,417,616,804 | IssuesEvent | 2017-08-08 17:08:56 | cockroachdb/cockroach | https://api.github.com/repos/cockroachdb/cockroach | closed | teamcity: failed tests on master: acceptance/TestDockerReadWriteBidirectionalReferenceVersion | Robot test-failure | The following tests appear to have failed:
[#317353](https://teamcity.cockroachdb.com/viewLog.html?buildId=317353):
```
--- FAIL: acceptance/TestDockerReadWriteBidirectionalReferenceVersion (0.000s)
Test ended in panic.
------- Stdout: -------
xenial-20170214: Pulling from library/ubuntu
Digest: sha256:dd7808d8792c9841d0b460122f1acf0a2dd1f56404f8d1e56298048885e45535
Status: Image is up to date for ubuntu:xenial-20170214
20170423-1100: Pulling from cockroachdb/postgres-test
Digest: sha256:1fd869a88a4316aa1e464501fdff364aef43512ca8aa12914ebc0790f37a58c6
Status: Image is up to date for cockroachdb/postgres-test:20170423-1100
File: ���/cockroach/cockroach���
Size: 42379944 Blocks: 82776 IO Block: 4096 regular file
Device: 801h/2049d Inode: 270670 Links: 1
Access: (0755/-rwxr-xr-x) Uid: ( 1001/ UNKNOWN) Gid: ( 1001/ UNKNOWN)
Access: 2017-08-07 17:14:13.140447892 +0000
Modify: 2017-08-07 17:13:41.552359286 +0000
Change: 2017-08-07 17:13:41.592359399 +0000
Birth: -
xenial-20170214: Pulling from library/ubuntu
Digest: sha256:dd7808d8792c9841d0b460122f1acf0a2dd1f56404f8d1e56298048885e45535
Status: Image is up to date for ubuntu:xenial-20170214
20170423-1100: Pulling from cockroachdb/postgres-test
Digest: sha256:1fd869a88a4316aa1e464501fdff364aef43512ca8aa12914ebc0790f37a58c6
Status: Image is up to date for cockroachdb/postgres-test:20170423-1100
panic: test timed out after 10m0s
goroutine 10171 [running]:
testing.startAlarm.func1()
/usr/local/go/src/testing/testing.go:1023 +0xf9
created by time.goFunc
/usr/local/go/src/time/sleep.go:170 +0x44
goroutine 1 [chan receive]:
testing.(*T).Run(0xc420280750, 0x1a8e147, 0x30, 0x1b105f8, 0xc420525c01)
/usr/local/go/src/testing/testing.go:698 +0x2f4
testing.runTests.func1(0xc420280750)
/usr/local/go/src/testing/testing.go:882 +0x67
testing.tRunner(0xc420280750, 0xc420525d38)
/usr/local/go/src/testing/testing.go:657 +0x96
testing.runTests(0xc42023ab20, 0x2659640, 0x26, 0x26, 0x285eec0)
/usr/local/go/src/testing/testing.go:888 +0x2c1
testing.(*M).Run(0xc420687f20, 0x1b10560)
/usr/local/go/src/testing/testing.go:822 +0xfc
github.com/cockroachdb/cockroach/pkg/acceptance.RunTests(0xc420525f20)
/go/src/github.com/cockroachdb/cockroach/pkg/acceptance/util.go:148 +0x48
github.com/cockroachdb/cockroach/pkg/acceptance.MainTest(0xc420525f20)
/go/src/github.com/cockroachdb/cockroach/pkg/acceptance/test_acceptance.go:35 +0x3d
github.com/cockroachdb/cockroach/pkg/acceptance.TestMain(0xc420525f20)
/go/src/github.com/cockroachdb/cockroach/pkg/acceptance/main_test.go:22 +0x2b
main.main()
github.com/cockroachdb/cockroach/pkg/acceptance/_test/_testmain.go:114 +0xf7
goroutine 17 [syscall, 10 minutes, locked to thread]:
runtime.goexit()
/usr/local/go/src/runtime/asm_amd64.s:2197 +0x1
goroutine 6 [chan receive]:
github.com/cockroachdb/cockroach/pkg/util/log.(*loggingT).flushDaemon(0x28607c0)
/go/src/github.com/cockroachdb/cockroach/pkg/util/log/clog.go:988 +0x77
created by github.com/cockroachdb/cockroach/pkg/util/log.init.1
/go/src/github.com/cockroachdb/cockroach/pkg/util/log/clog.go:575 +0xd9
goroutine 18 [syscall, 10 minutes]:
os/signal.signal_recv(0xf02696593)
/usr/local/go/src/runtime/sigqueue.go:116 +0x104
os/signal.loop()
/usr/local/go/src/os/signal/signal_unix.go:22 +0x22
created by os/signal.init.1
/usr/local/go/src/os/signal/signal_unix.go:28 +0x41
goroutine 15 [chan receive, 10 minutes]:
github.com/cockroachdb/cockroach/pkg/acceptance.RunTests.func1()
/go/src/github.com/cockroachdb/cockroach/pkg/acceptance/util.go:139 +0xb6
created by github.com/cockroachdb/cockroach/pkg/acceptance.RunTests
/go/src/github.com/cockroachdb/cockroach/pkg/acceptance/util.go:147 +0x3a
goroutine 9738 [select]:
net/http.(*persistConn).roundTrip(0xc42063c360, 0xc4203c5920, 0x0, 0x0, 0x0)
/usr/local/go/src/net/http/transport.go:1898 +0x974
net/http.(*Transport).RoundTrip(0xc4207fa960, 0xc42114f200, 0xc4207fa960, 0x0, 0x0)
/usr/local/go/src/net/http/transport.go:391 +0x74c
net/http.send(0xc42114f200, 0x2669100, 0xc4207fa960, 0x0, 0x0, 0x0, 0x0, 0x8, 0xc420778688, 0x5be648)
/usr/local/go/src/net/http/client.go:249 +0x162
net/http.(*Client).send(0xc421417a10, 0xc42114f200, 0x0, 0x0, 0x0, 0xc420778688, 0x0, 0x1, 0x30)
/usr/local/go/src/net/http/client.go:173 +0x108
net/http.(*Client).Do(0xc421417a10, 0xc42114f200, 0xc4213c7da0, 0xc42114f200, 0xc4213c7da0)
/usr/local/go/src/net/http/client.go:595 +0x254
github.com/cockroachdb/cockroach/vendor/golang.org/x/net/context/ctxhttp.Do(0x7f4af8010c40, 0xc4213c7da0, 0xc421417a10, 0xc42114f100, 0xc4203d6fe0, 0xc421296580, 0x87a9bb)
/go/src/github.com/cockroachdb/cockroach/vendor/golang.org/x/net/context/ctxhttp/ctxhttp.go:30 +0x92
github.com/cockroachdb/cockroach/vendor/github.com/docker/docker/client.(*Client).doRequest(0xc421315880, 0x7f4af8010c40, 0xc4213c7da0, 0xc42114f100, 0x57, 0x0, 0x0, 0x0, 0xc42114f100, 0x0)
/go/src/github.com/cockroachdb/cockroach/vendor/github.com/docker/docker/client/request.go:127 +0x6e
github.com/cockroachdb/cockroach/vendor/github.com/docker/docker/client.(*Client).sendRequest(0xc421315880, 0x7f4af8010c40, 0xc4213c7da0, 0x1a4a97a, 0x4, 0xc4213c7e00, 0x51, 0x0, 0x0, 0x0, ...)
/go/src/github.com/cockroachdb/cockroach/vendor/github.com/docker/docker/client/request.go:121 +0x14a
github.com/cockroachdb/cockroach/vendor/github.com/docker/docker/client.(*Client).post(0xc421315880, 0x7f4af8010c40, 0xc4213c7da0, 0xc4213c7e00, 0x51, 0x0, 0x0, 0x0, 0x0, 0x0, ...)
/go/src/github.com/cockroachdb/cockroach/vendor/github.com/docker/docker/client/request.go:45 +0x14a
github.com/cockroachdb/cockroach/vendor/github.com/docker/docker/client.(*Client).ContainerWait(0xc421315880, 0x7f4af8010c40, 0xc4213c7da0, 0xc420f06ac0, 0x40, 0x0, 0x0, 0x0)
/go/src/github.com/cockroachdb/cockroach/vendor/github.com/docker/docker/client/container_wait.go:14 +0x107
github.com/cockroachdb/cockroach/pkg/acceptance/cluster.retryingDockerClient.ContainerWait.func1(0x7f4af8010c40, 0xc4213c7da0, 0x2540be400, 0x7f4af8010c40)
/go/src/github.com/cockroachdb/cockroach/pkg/acceptance/cluster/docker.go:479 +0x61
github.com/cockroachdb/cockroach/pkg/acceptance/cluster.retry(0x7f4af805d118, 0xc420018de8, 0xa, 0x2540be400, 0x1a56de2, 0xd, 0x1a49c29, 0x2, 0xc4212969a0, 0x0, ...)
/go/src/github.com/cockroachdb/cockroach/pkg/acceptance/cluster/docker.go:410 +0x92
github.com/cockroachdb/cockroach/pkg/acceptance/cluster.retryingDockerClient.ContainerWait(0x26957c0, 0xc421315880, 0xa, 0x2540be400, 0x7f4af805d118, 0xc420018de8, 0xc420f06ac0, 0x40, 0x0, 0x0, ...)
/go/src/github.com/cockroachdb/cockroach/pkg/acceptance/cluster/docker.go:482 +0x11f
github.com/cockroachdb/cockroach/pkg/acceptance/cluster.(*retryingDockerClient).ContainerWait(0xc4203251e0, 0x7f4af805d118, 0xc420018de8, 0xc420f06ac0, 0x40, 0x0, 0x0, 0x0)
<autogenerated>:318 +0x9a
github.com/cockroachdb/cockroach/pkg/acceptance/cluster.(*Container).Wait(0xc4202b9650, 0x7f4af805d118, 0xc420018de8, 0x0, 0x0)
/go/src/github.com/cockroachdb/cockroach/pkg/acceptance/cluster/docker.go:233 +0x95
github.com/cockroachdb/cockroach/pkg/acceptance/cluster.(*LocalCluster).OneShot(0xc42063c240, 0x7f4af805d118, 0xc420018de8, 0x1a9077b, 0x31, 0xc4203f3100, 0x0, 0x0, 0x0, 0x0, ...)
/go/src/github.com/cockroachdb/cockroach/pkg/acceptance/cluster/localcluster.go:264 +0x2bd
github.com/cockroachdb/cockroach/pkg/acceptance.testDocker(0x7f4af805d118, 0xc420018de8, 0xc420af9ad0, 0xc400000000, 0x1a528cb, 0x9, 0x0, 0x0, 0x0, 0x0, ...)
/go/src/github.com/cockroachdb/cockroach/pkg/acceptance/util.go:563 +0x399
github.com/cockroachdb/cockroach/pkg/acceptance.testDockerOneShot(0x7f4af805d118, 0xc420018de8, 0xc420af9ad0, 0x1a528cb, 0x9, 0x0, 0x0, 0x0, 0x0, 0x0, ...)
/go/src/github.com/cockroachdb/cockroach/pkg/acceptance/util.go:580 +0x9f
github.com/cockroachdb/cockroach/pkg/acceptance.runReferenceTestWithScript(0x7f4af805d118, 0xc420018de8, 0xc420af9ad0, 0xc42076c880, 0xceb)
/go/src/github.com/cockroachdb/cockroach/pkg/acceptance/reference_test.go:38 +0x2ca
github.com/cockroachdb/cockroach/pkg/acceptance.runReadWriteReferenceTest(0x7f4af805d118, 0xc420018de8, 0xc420af9ad0, 0x1a6ed50, 0x1f, 0x1ab5201, 0x2ad)
/go/src/github.com/cockroachdb/cockroach/pkg/acceptance/reference_test.go:97 +0x193
github.com/cockroachdb/cockroach/pkg/acceptance.TestDockerReadWriteBidirectionalReferenceVersion(0xc420af9ad0)
/go/src/github.com/cockroachdb/cockroach/pkg/acceptance/reference_test.go:125 +0xef
testing.tRunner(0xc420af9ad0, 0x1b105f8)
/usr/local/go/src/testing/testing.go:657 +0x96
created by testing.(*T).Run
/usr/local/go/src/testing/testing.go:697 +0x2ca
goroutine 19 [select, 10 minutes, locked to thread]:
runtime.gopark(0x1b137e8, 0x0, 0x1a4df60, 0x6, 0x18, 0x2)
/usr/local/go/src/runtime/proc.go:271 +0x13a
runtime.selectgoImpl(0xc4205e5f50, 0x0, 0x18)
/usr/local/go/src/runtime/select.go:423 +0x1364
runtime.selectgo(0xc4205e5f50)
/usr/local/go/src/runtime/select.go:238 +0x1c
runtime.ensureSigM.func1()
/usr/local/go/src/runtime/signal_unix.go:434 +0x2dd
runtime.goexit()
/usr/local/go/src/runtime/asm_amd64.s:2197 +0x1
goroutine 176 [chan receive, 9 minutes]:
database/sql.(*DB).connectionOpener(0xc420942000)
/usr/local/go/src/database/sql/sql.go:837 +0x4a
created by database/sql.Open
/usr/local/go/src/database/sql/sql.go:582 +0x212
goroutine 188 [chan receive, 9 minutes]:
github.com/cockroachdb/cockroach/pkg/rpc.NewContext.func1(0x7f4af7f29238, 0xc4207a1470)
/go/src/github.com/cockroachdb/cockroach/pkg/rpc/context.go:209 +0x5d
github.com/cockroachdb/cockroach/pkg/util/stop.(*Stopper).RunWorker.func1(0xc4203111c0, 0xc42001cea0, 0xc4203121e0)
/go/src/github.com/cockroachdb/cockroach/pkg/util/stop/stopper.go:193 +0xf7
created by github.com/cockroachdb/cockroach/pkg/util/stop.(*Stopper).RunWorker
/go/src/github.com/cockroachdb/cockroach/pkg/util/stop/stopper.go:194 +0xad
goroutine 138 [select, 9 minutes]:
net/http.(*persistConn).writeLoop(0xc4209a2240)
/usr/local/go/src/net/http/transport.go:1704 +0x43a
created by net/http.(*Transport).dialConn
/usr/local/go/src/net/http/transport.go:1118 +0xa5a
goroutine 85 [select]:
github.com/cockroachdb/cockroach/pkg/rpc.(*Context).runHeartbeat(0xc4207d6000, 0xc4204169c0, 0xc4201f4370, 0xf, 0x0, 0x0)
/go/src/github.com/cockroachdb/cockroach/pkg/rpc/context.go:412 +0x7ef
github.com/cockroachdb/cockroach/pkg/rpc.(*Context).GRPCDial.func1.2.1(0x7f4af7f29238, 0xc4201dc990)
/go/src/github.com/cockroachdb/cockroach/pkg/rpc/context.go:346 +0x6b
github.com/cockroachdb/cockroach/pkg/util/stop.(*Stopper).RunWorker.func1(0xc42021af90, 0xc42001cea0, 0xc4201dc810)
/go/src/github.com/cockroachdb/cockroach/pkg/util/stop/stopper.go:193 +0xf7
created by github.com/cockroachdb/cockroach/pkg/util/stop.(*Stopper).RunWorker
/go/src/github.com/cockroachdb/cockroach/pkg/util/stop/stopper.go:194 +0xad
goroutine 69 [chan receive, 9 minutes]:
github.com/cockroachdb/cockroach/pkg/rpc.NewContext.func1(0x7f4af7f29238, 0xc420413b00)
/go/src/github.com/cockroachdb/cockroach/pkg/rpc/context.go:209 +0x5d
github.com/cockroachdb/cockroach/pkg/util/stop.(*Stopper).RunWorker.func1(0xc420266700, 0xc42001cea0, 0xc420277a00)
/go/src/github.com/cockroachdb/cockroach/pkg/util/stop/stopper.go:193 +0xf7
created by github.com/cockroachdb/cockroach/pkg/util/stop.(*Stopper).RunWorker
/go/src/github.com/cockroachdb/cockroach/pkg/util/stop/stopper.go:194 +0xad
goroutine 116 [select]:
github.com/cockroachdb/cockroach/pkg/rpc.(*Context).runHeartbeat(0xc4208e8270, 0xc4207934c0, 0xc420270110, 0xf, 0x0, 0x0)
/go/src/github.com/cockroachdb/cockroach/pkg/rpc/context.go:412 +0x7ef
github.com/cockroachdb/cockroach/pkg/rpc.(*Context).GRPCDial.func1.2.1(0x7f4af7f29238, 0xc420822b40)
/go/src/github.com/cockroachdb/cockroach/pkg/rpc/context.go:346 +0x6b
github.com/cockroachdb/cockroach/pkg/util/stop.(*Stopper).RunWorker.func1(0xc42027d170, 0xc42001cea0, 0xc420822ab0)
/go/src/github.com/cockroachdb/cockroach/pkg/util/stop/stopper.go:193 +0xf7
created by github.com/cockroachdb/cockroach/pkg/util/stop.(*Stopper).RunWorker
/go/src/github.com/cockroachdb/cockroach/pkg/util/stop/stopper.go:194 +0xad
goroutine 435 [chan receive, 8 minutes]:
github.com/cockroachdb/cockroach/pkg/rpc.NewContext.func1(0x7f4af7f29238, 0xc42035b590)
/go/src/github.com/cockroachdb/cockroach/pkg/rpc/context.go:209 +0x5d
github.com/cockroachdb/cockroach/pkg/util/stop.(*Stopper).RunWorker.func1(0xc420311080, 0xc42001cea0, 0xc42025bb40)
/go/src/github.com/cockroachdb/cockroach/pkg/util/stop/stopper.go:193 +0xf7
created by github.com/cockroachdb/cockroach/pkg/util/stop.(*Stopper).RunWorker
/go/src/github.com/cockroachdb/cockroach/pkg/util/stop/stopper.go:194 +0xad
goroutine 137 [IO wait, 9 minutes]:
net.runtime_pollWait(0x7f4af805e928, 0x72, 0x9)
/usr/local/go/src/runtime/netpoll.go:164 +0x59
net.(*pollDesc).wait(0xc420464298, 0x72, 0x266c700, 0x2661ba8)
/usr/local/go/src/net/fd_poll_runtime.go:75 +0x38
net.(*pollDesc).waitRead(0xc420464298, 0xc42055a000, 0x1000)
/usr/local/go/src/net/fd_poll_runtime.go:80 +0x34
net.(*netFD).Read(0xc420464230, 0xc42055a000, 0x1000, 0x1000, 0x0, 0x266c700, 0x2661ba8)
/usr/local/go/src/net/fd_unix.go:250 +0x1b7
net.(*conn).Read(0xc42000e180, 0xc42055a000, 0x1000, 0x1000, 0x0, 0x0, 0x0)
/usr/local/go/src/net/net.go:181 +0x70
net/http.(*persistConn).Read(0xc4209a2240, 0xc42055a000, 0x1000, 0x1000, 0x4, 0xc4202531a0, 0x17)
/usr/local/go/src/net/http/transport.go:1316 +0x14b
bufio.(*Reader).fill(0xc420b48cc0)
/usr/local/go/src/bufio/bufio.go:97 +0x117
bufio.(*Reader).Peek(0xc420b48cc0, 0x1, 0x0, 0x1, 0x0, 0xc4204c8720, 0x0)
/usr/local/go/src/bufio/bufio.go:129 +0x67
net/http.(*persistConn).readLoop(0xc4209a2240)
/usr/local/go/src/net/http/transport.go:1474 +0x196
created by net/http.(*Transport).dialConn
/usr/local/go/src/net/http/transport.go:1117 +0xa35
goroutine 84 [select]:
github.com/cockroachdb/cockroach/vendor/google.golang.org/grpc.(*addrConn).resetTransport(0xc4200a3180, 0xc4202c0000, 0x0, 0x0)
/go/src/github.com/cockroachdb/cockroach/vendor/google.golang.org/grpc/clientconn.go:888 +0x8e5
github.com/cockroachdb/cockroach/vendor/google.golang.org/grpc.(*addrConn).transportMonitor(0xc4200a3180)
/go/src/github.com/cockroachdb/cockroach/vendor/google.golang.org/grpc/clientconn.go:972 +0x362
github.com/cockroachdb/cockroach/vendor/google.golang.org/grpc.(*ClientConn).resetAddrConn.func1(0xc4200a3180)
/go/src/github.com/cockroachdb/cockroach/vendor/google.golang.org/grpc/clientconn.go:642 +0x1d9
created by github.com/cockroachdb/cockroach/vendor/google.golang.org/grpc.(*ClientConn).resetAddrConn
/go/src/github.com/cockroachdb/cockroach/vendor/google.golang.org/grpc/clientconn.go:643 +0x786
goroutine 23 [chan receive, 9 minutes]:
github.com/cockroachdb/cockroach/pkg/rpc.NewContext.func1(0x7f4af7f29238, 0xc42038f440)
/go/src/github.com/cockroachdb/cockroach/pkg/rpc/context.go:209 +0x5d
github.com/cockroachdb/cockroach/pkg/util/stop.(*Stopper).RunWorker.func1(0xc420018490, 0xc42001cea0, 0xc4200fb560)
/go/src/github.com/cockroachdb/cockroach/pkg/util/stop/stopper.go:193 +0xf7
created by github.com/cockroachdb/cockroach/pkg/util/stop.(*Stopper).RunWorker
/go/src/github.com/cockroachdb/cockroach/pkg/util/stop/stopper.go:194 +0xad
goroutine 5386 [select]:
github.com/cockroachdb/cockroach/pkg/rpc.(*Context).runHeartbeat(0xc420af8a90, 0xc420ad0540, 0xc420369480, 0xf, 0x0, 0x0)
/go/src/github.com/cockroachdb/cockroach/pkg/rpc/context.go:412 +0x7ef
github.com/cockroachdb/cockroach/pkg/rpc.(*Context).GRPCDial.func1.2.1(0x7f4af7f29238, 0xc4201c6f00)
/go/src/github.com/cockroachdb/cockroach/pkg/rpc/context.go:346 +0x6b
github.com/cockroachdb/cockroach/pkg/util/stop.(*Stopper).RunWorker.func1(0xc42031e7e0, 0xc42001cea0, 0xc4201c6e70)
/go/src/github.com/cockroachdb/cockroach/pkg/util/stop/stopper.go:193 +0xf7
created by github.com/cockroachdb/cockroach/pkg/util/stop.(*Stopper).RunWorker
/go/src/github.com/cockroachdb/cockroach/pkg/util/stop/stopper.go:194 +0xad
goroutine 49 [IO wait, 9 minutes]:
net.runtime_pollWait(0x7f4af805f168, 0x72, 0x8)
/usr/local/go/src/runtime/netpoll.go:164 +0x59
net.(*pollDesc).wait(0xc4201b9568, 0x72, 0x266c700, 0x2661ba8)
/usr/local/go/src/net/fd_poll_runtime.go:75 +0x38
net.(*pollDesc).waitRead(0xc4201b9568, 0xc4206bc000, 0x1000)
/usr/local/go/src/net/fd_poll_runtime.go:80 +0x34
net.(*netFD).Read(0xc4201b9500, 0xc4206bc000, 0x1000, 0x1000, 0x0, 0x266c700, 0x2661ba8)
/usr/local/go/src/net/fd_unix.go:250 +0x1b7
net.(*conn).Read(0xc420474128, 0xc4206bc000, 0x1000, 0x1000, 0x0, 0x0, 0x0)
/usr/local/go/src/net/net.go:181 +0x70
net/http.(*persistConn).Read(0xc4202a9b00, 0xc4206bc000, 0x1000, 0x1000, 0x4, 0xc42025bbe0, 0x17)
/usr/local/go/src/net/http/transport.go:1316 +0x14b
bufio.(*Reader).fill(0xc4208bf380)
/usr/local/go/src/bufio/bufio.go:97 +0x117
bufio.(*Reader).Peek(0xc4208bf380, 0x1, 0x0, 0x1, 0x0, 0xc4208feb40, 0x0)
/usr/local/go/src/bufio/bufio.go:129 +0x67
net/http.(*persistConn).readLoop(0xc4202a9b00)
/usr/local/go/src/net/http/transport.go:1474 +0x196
created by net/http.(*Transport).dialConn
/usr/local/go/src/net/http/transport.go:1117 +0xa35
goroutine 82 [select, 9 minutes]:
net/http.(*persistConn).writeLoop(0xc4202a9b00)
/usr/local/go/src/net/http/transport.go:1704 +0x43a
created by net/http.(*Transport).dialConn
/usr/local/go/src/net/http/transport.go:1118 +0xa5a
goroutine 102 [select]:
github.com/cockroachdb/cockroach/vendor/google.golang.org/grpc.(*addrConn).resetTransport(0xc42040e540, 0xc4207c8300, 0x0, 0x0)
/go/src/github.com/cockroachdb/cockroach/vendor/google.golang.org/grpc/clientconn.go:888 +0x8e5
github.com/cockroachdb/cockroach/vendor/google.golang.org/grpc.(*addrConn).transportMonitor(0xc42040e540)
/go/src/github.com/cockroachdb/cockroach/vendor/google.golang.org/grpc/clientconn.go:972 +0x362
github.com/cockroachdb/cockroach/vendor/google.golang.org/grpc.(*ClientConn).resetAddrConn.func1(0xc42040e540)
/go/src/github.com/cockroachdb/cockroach/vendor/google.golang.org/grpc/clientconn.go:642 +0x1d9
created by github.com/cockroachdb/cockroach/vendor/google.golang.org/grpc.(*ClientConn).resetAddrConn
/go/src/github.com/cockroachdb/cockroach/vendor/google.golang.org/grpc/clientconn.go:643 +0x786
goroutine 103 [select]:
github.com/cockroachdb/cockroach/pkg/rpc.(*Context).runHeartbeat(0xc4207d6340, 0xc420422480, 0xc4202703f0, 0xf, 0x0, 0x0)
/go/src/github.com/cockroachdb/cockroach/pkg/rpc/context.go:412 +0x7ef
github.com/cockroachdb/cockroach/pkg/rpc.(*Context).GRPCDial.func1.2.1(0x7f4af7f29238, 0xc4202b8ff0)
/go/src/github.com/cockroachdb/cockroach/pkg/rpc/context.go:346 +0x6b
github.com/cockroachdb/cockroach/pkg/util/stop.(*Stopper).RunWorker.func1(0xc42027c160, 0xc42001cea0, 0xc4202b8e10)
/go/src/github.com/cockroachdb/cockroach/pkg/util/stop/stopper.go:193 +0xf7
created by github.com/cockroachdb/cockroach/pkg/util/stop.(*Stopper).RunWorker
/go/src/github.com/cockroachdb/cockroach/pkg/util/stop/stopper.go:194 +0xad
goroutine 67 [IO wait, 9 minutes]:
net.runtime_pollWait(0x7f4af805efe8, 0x72, 0xa)
/usr/local/go/src/runtime/netpoll.go:164 +0x59
net.(*pollDesc).wait(0xc420562308, 0x72, 0x266c700, 0x2661ba8)
/usr/local/go/src/net/fd_poll_runtime.go:75 +0x38
net.(*pollDesc).waitRead(0xc420562308, 0xc42069c000, 0x1000)
/usr/local/go/src/net/fd_poll_runtime.go:80 +0x34
net.(*netFD).Read(0xc4205622a0, 0xc42069c000, 0x1000, 0x1000, 0x0, 0x266c700, 0x2661ba8)
/usr/local/go/src/net/fd_unix.go:250 +0x1b7
net.(*conn).Read(0xc420778028, 0xc42069c000, 0x1000, 0x1000, 0x0, 0x0, 0x0)
/usr/local/go/src/net/net.go:181 +0x70
net/http.(*persistConn).Read(0xc420772240, 0xc42069c000, 0x1000, 0x1000, 0x4, 0x602890, 0xc4208fe6c0)
/usr/local/go/src/net/http/transport.go:1316 +0x14b
bufio.(*Reader).fill(0xc4208fe540)
/usr/local/go/src/bufio/bufio.go:97 +0x117
bufio.(*Reader).Peek(0xc4208fe540, 0x1, 0xc4208d2be5, 0x1, 0x0, 0xc4208fe8a0, 0x0)
/usr/local/go/src/bufio/bufio.go:129 +0x67
net/http.(*persistConn).readLoop(0xc420772240)
/usr/local/go/src/net/http/transport.go:1474 +0x196
created by net/http.(*Transport).dialConn
/usr/local/go/src/net/http/transport.go:1117 +0xa35
goroutine 68 [select, 9 minutes]:
net/http.(*persistConn).writeLoop(0xc420772240)
/usr/local/go/src/net/http/transport.go:1704 +0x43a
created by net/http.(*Transport).dialConn
/usr/local/go/src/net/http/transport.go:1118 +0xa5a
goroutine 708 [select, 8 minutes]:
net/http.(*persistConn).writeLoop(0xc4209a2120)
/usr/local/go/src/net/http/transport.go:1704 +0x43a
created by net/http.(*Transport).dialConn
/usr/local/go/src/net/http/transport.go:1118 +0xa5a
goroutine 437 [select]:
github.com/cockroachdb/cockroach/vendor/google.golang.org/grpc.(*addrConn).resetTransport(0xc420242c40, 0xc4207ac400, 0x0, 0x0)
/go/src/github.com/cockroachdb/cockroach/vendor/google.golang.org/grpc/clientconn.go:888 +0x8e5
github.com/cockroachdb/cockroach/vendor/google.golang.org/grpc.(*addrConn).transportMonitor(0xc420242c40)
/go/src/github.com/cockroachdb/cockroach/vendor/google.golang.org/grpc/clientconn.go:972 +0x362
github.com/cockroachdb/cockroach/vendor/google.golang.org/grpc.(*ClientConn).resetAddrConn.func1(0xc420242c40)
/go/src/github.com/cockroachdb/cockroach/vendor/google.golang.org/grpc/clientconn.go:642 +0x1d9
created by github.com/cockroachdb/cockroach/vendor/google.golang.org/grpc.(*ClientConn).resetAddrConn
/go/src/github.com/cockroachdb/cockroach/vendor/google.golang.org/grpc/clientconn.go:643 +0x786
goroutine 707 [IO wait, 8 minutes]:
net.runtime_pollWait(0x7f4af805eaa8, 0x72, 0x15)
/usr/local/go/src/runtime/netpoll.go:164 +0x59
net.(*pollDesc).wait(0xc4204faa08, 0x72, 0x266c700, 0x2661ba8)
/usr/local/go/src/net/fd_poll_runtime.go:75 +0x38
net.(*pollDesc).waitRead(0xc4204faa08, 0xc420ac9000, 0x1000)
/usr/local/go/src/net/fd_poll_runtime.go:80 +0x34
net.(*netFD).Read(0xc4204fa9a0, 0xc420ac9000, 0x1000, 0x1000, 0x0, 0x266c700, 0x2661ba8)
/usr/local/go/src/net/fd_unix.go:250 +0x1b7
net.(*conn).Read(0xc42000e1f0, 0xc420ac9000, 0x1000, 0x1000, 0x0, 0x0, 0x0)
/usr/local/go/src/net/net.go:181 +0x70
net/http.(*persistConn).Read(0xc4209a2120, 0xc420ac9000, 0x1000, 0x1000, 0x4, 0xc4202974e0, 0x17)
/usr/local/go/src/net/http/transport.go:1316 +0x14b
bufio.(*Reader).fill(0xc420b5fce0)
/usr/local/go/src/bufio/bufio.go:97 +0x117
bufio.(*Reader).Peek(0xc420b5fce0, 0x1, 0x0, 0x1, 0x0, 0xc4207e0660, 0x0)
/usr/local/go/src/bufio/bufio.go:129 +0x67
net/http.(*persistConn).readLoop(0xc4209a2120)
/usr/local/go/src/net/http/transport.go:1474 +0x196
created by net/http.(*Transport).dialConn
/usr/local/go/src/net/http/transport.go:1117 +0xa35
goroutine 115 [select]:
github.com/cockroachdb/cockroach/vendor/google.golang.org/grpc.(*addrConn).resetTransport(0xc4208148c0, 0xc420900e00, 0x0, 0x0)
/go/src/github.com/cockroachdb/cockroach/vendor/google.golang.org/grpc/clientconn.go:888 +0x8e5
github.com/cockroachdb/cockroach/vendor/google.golang.org/grpc.(*addrConn).transportMonitor(0xc4208148c0)
/go/src/github.com/cockroachdb/cockroach/vendor/google.golang.org/grpc/clientconn.go:972 +0x362
github.com/cockroachdb/cockroach/vendor/google.golang.org/grpc.(*ClientConn).resetAddrConn.func1(0xc4208148c0)
/go/src/github.com/cockroachdb/cockroach/vendor/google.golang.org/grpc/clientconn.go:642 +0x1d9
created by github.com/cockroachdb/cockroach/vendor/google.golang.org/grpc.(*ClientConn).resetAddrConn
/go/src/github.com/cockroachdb/cockroach/vendor/google.golang.org/grpc/clientconn.go:643 +0x786
goroutine 644 [chan receive, 8 minutes]:
database/sql.(*DB).connectionOpener(0xc420b10dc0)
/usr/local/go/src/database/sql/sql.go:837 +0x4a
created by database/sql.Open
/usr/local/go/src/database/sql/sql.go:582 +0x212
goroutine 2131 [select, 5 minutes]:
net/http.(*persistConn).writeLoop(0xc4206606c0)
/usr/local/go/src/net/http/transport.go:1704 +0x43a
created by net/http.(*Transport).dialConn
/usr/local/go/src/net/http/transport.go:1118 +0xa5a
goroutine 596 [IO wait, 8 minutes]:
net.runtime_pollWait(0x7f4af805ef28, 0x72, 0x13)
/usr/local/go/src/runtime/netpoll.go:164 +0x59
net.(*pollDesc).wait(0xc420419a38, 0x72, 0x266c700, 0x2661ba8)
/usr/local/go/src/net/fd_poll_runtime.go:75 +0x38
net.(*pollDesc).waitRead(0xc420419a38, 0xc4204fd000, 0x1000)
/usr/local/go/src/net/fd_poll_runtime.go:80 +0x34
net.(*netFD).Read(0xc4204199d0, 0xc4204fd000, 0x1000, 0x1000, 0x0, 0x266c700, 0x2661ba8)
/usr/local/go/src/net/fd_unix.go:250 +0x1b7
net.(*conn).Read(0xc420778178, 0xc4204fd000, 0x1000, 0x1000, 0x0, 0x0, 0x0)
/usr/local/go/src/net/net.go:181 +0x70
net/http.(*persistConn).Read(0xc4202a8d80, 0xc4204fd000, 0x1000, 0x1000, 0x4, 0xc4202769c0, 0x17)
/usr/local/go/src/net/http/transport.go:1316 +0x14b
bufio.(*Reader).fill(0xc42073d980)
/usr/local/go/src/bufio/bufio.go:97 +0x117
bufio.(*Reader).Peek(0xc42073d980, 0x1, 0x0, 0x1, 0x0, 0xc4209b5c80, 0x0)
/usr/local/go/src/bufio/bufio.go:129 +0x67
net/http.(*persistConn).readLoop(0xc4202a8d80)
/usr/local/go/src/net/http/transport.go:1474 +0x196
created by net/http.(*Transport).dialConn
/usr/local/go/src/net/http/transport.go:1117 +0xa35
goroutine 27 [chan receive, 9 minutes]:
github.com/cockroachdb/cockroach/pkg/rpc.NewContext.func1(0x7f4af7f29238, 0xc420262060)
/go/src/github.com/cockroachdb/cockroach/pkg/rpc/context.go:209 +0x5d
github.com/cockroachdb/cockroach/pkg/util/stop.(*Stopper).RunWorker.func1(0xc420259a50, 0xc42001cea0, 0xc42025bae0)
/go/src/github.com/cockroachdb/cockroach/pkg/util/stop/stopper.go:193 +0xf7
created by github.com/cockroachdb/cockroach/pkg/util/stop.(*Stopper).RunWorker
/go/src/github.com/cockroachdb/cockroach/pkg/util/stop/stopper.go:194 +0xad
goroutine 4565 [chan receive, 2 minutes]:
github.com/cockroachdb/cockroach/pkg/rpc.NewContext.func1(0x7f4af7f29238, 0xc420986e40)
/go/src/github.com/cockroachdb/cockroach/pkg/rpc/context.go:209 +0x5d
github.com/cockroachdb/cockroach/pkg/util/stop.(*Stopper).RunWorker.func1(0xc42033fad0, 0xc42001cea0, 0xc42035d8a0)
/go/src/github.com/cockroachdb/cockroach/pkg/util/stop/stopper.go:193 +0xf7
created by github.com/cockroachdb/cockroach/pkg/util/stop.(*Stopper).RunWorker
/go/src/github.com/cockroachdb/cockroach/pkg/util/stop/stopper.go:194 +0xad
goroutine 31 [chan receive, 9 minutes]:
database/sql.(*DB).connectionOpener(0xc420398dc0)
/usr/local/go/src/database/sql/sql.go:837 +0x4a
created by database/sql.Open
/usr/local/go/src/database/sql/sql.go:582 +0x212
goroutine 32 [chan receive, 9 minutes]:
database/sql.(*DB).connectionOpener(0xc4203f6a00)
/usr/local/go/src/database/sql/sql.go:837 +0x4a
created by database/sql.Open
/usr/local/go/src/database/sql/sql.go:582 +0x212
goroutine 88 [chan receive, 9 minutes]:
database/sql.(*DB).connectionOpener(0xc4201a8d20)
/usr/local/go/src/database/sql/sql.go:837 +0x4a
created by database/sql.Open
/usr/local/go/src/database/sql/sql.go:582 +0x212
goroutine 33 [chan receive, 9 minutes]:
database/sql.(*DB).connectionOpener(0xc4203f74a0)
/usr/local/go/src/database/sql/sql.go:837 +0x4a
created by database/sql.Open
/usr/local/go/src/database/sql/sql.go:582 +0x212
goroutine 438 [select]:
github.com/cockroachdb/cockroach/pkg/rpc.(*Context).runHeartbeat(0xc4207d6750, 0xc42079f380, 0xc420311500, 0xf, 0x0, 0x0)
/go/src/github.com/cockroachdb/cockroach/pkg/rpc/context.go:412 +0x7ef
github.com/cockroachdb/cockroach/pkg/rpc.(*Context).GRPCDial.func1.2.1(0x7f4af7f29238, 0xc4201dd2c0)
/go/src/github.com/cockroachdb/cockroach/pkg/rpc/context.go:346 +0x6b
github.com/cockroachdb/cockroach/pkg/util/stop.(*Stopper).RunWorker.func1(0xc4201d6a50, 0xc42001cea0, 0xc4201dd1a0)
/go/src/github.com/cockroachdb/cockroach/pkg/util/stop/stopper.go:193 +0xf7
created by github.com/cockroachdb/cockroach/pkg/util/stop.(*Stopper).RunWorker
/go/src/github.com/cockroachdb/cockroach/pkg/util/stop/stopper.go:194 +0xad
goroutine 1310 [select, 6 minutes]:
net/http.(*persistConn).writeLoop(0xc420772360)
/usr/local/go/src/net/http/transport.go:1704 +0x43a
created by net/http.(*Transport).dialConn
/usr/local/go/src/net/http/transport.go:1118 +0xa5a
goroutine 2181 [IO wait, 5 minutes]:
net.runtime_pollWait(0x7f4af80621f8, 0x72, 0x27)
/usr/local/go/src/runtime/netpoll.go:164 +0x59
net.(*pollDesc).wait(0xc4200a6d88, 0x72, 0x266c700, 0x2661ba8)
/usr/local/go/src/net/fd_poll_runtime.go:75 +0x38
net.(*pollDesc).waitRead(0xc4200a6d88, 0xc42073a000, 0x1000)
/usr/local/go/src/net/fd_poll_runtime.go:80 +0x34
net.(*netFD).Read(0xc4200a6d20, 0xc42073a000, 0x1000, 0x1000, 0x0, 0x266c700, 0x2661ba8)
/usr/local/go/src/net/fd_unix.go:250 +0x1b7
net.(*conn).Read(0xc4207c4108, 0xc42073a000, 0x1000, 0x1000, 0x0, 0x0, 0x0)
/usr/local/go/src/net/net.go:181 +0x70
net/http.(*persistConn).Read(0xc420660a20, 0xc42073a000, 0x1000, 0x1000, 0x4, 0xc4202c91a0, 0x17)
/usr/local/go/src/net/http/transport.go:1316 +0x14b
bufio.(*Reader).fill(0xc4208b5860)
/usr/local/go/src/bufio/bufio.go:97 +0x117
bufio.(*Reader).Peek(0xc4208b5860, 0x1, 0x0, 0x1, 0x0, 0xc4208aaa80, 0x0)
/usr/local/go/src/bufio/bufio.go:129 +0x67
net/http.(*persistConn).readLoop(0xc420660a20)
/usr/local/go/src/net/http/transport.go:1474 +0x196
created by net/http.(*Transport).dialConn
/usr/local/go/src/net/http/transport.go:1117 +0xa35
goroutine 1570 [select, 6 minutes]:
net/http.(*persistConn).writeLoop(0xc4200c3b00)
/usr/local/go/src/net/http/transport.go:1704 +0x43a
created by net/http.(*Transport).dialConn
/usr/local/go/src/net/http/transport.go:1118 +0xa5a
goroutine 6616 [select]:
github.com/cockroachdb/cockroach/pkg/rpc.(*Context).runHeartbeat(0xc420281ad0, 0xc421336ec0, 0xc420018590, 0xf, 0x0, 0x0)
/go/src/github.com/cockroachdb/cockroach/pkg/rpc/context.go:412 +0x7ef
github.com/cockroachdb/cockroach/pkg/rpc.(*Context).GRPCDial.func1.2.1(0x7f4af7f29238, 0xc421195c50)
/go/src/github.com/cockroachdb/cockroach/pkg/rpc/context.go:346 +0x6b
github.com/cockroachdb/cockroach/pkg/util/stop.(*Stopper).RunWorker.func1(0xc4203114b0, 0xc42001cea0, 0xc421195bc0)
/go/src/github.com/cockroachdb/cockroach/pkg/util/stop/stopper.go:193 +0xf7
created by github.com/cockroachdb/cockroach/pkg/util/stop.(*Stopper).RunWorker
/go/src/github.com/cockroachdb/cockroach/pkg/util/stop/stopper.go:194 +0xad
goroutine 668 [select, 8 minutes]:
net/http.(*persistConn).writeLoop(0xc42042f7a0)
/usr/local/go/src/net/http/transport.go:1704 +0x43a
created by net/http.(*Transport).dialConn
/usr/local/go/src/net/http/transport.go:1118 +0xa5a
goroutine 787 [IO wait, 8 minutes]:
net.runtime_pollWait(0x7f4af805e628, 0x72, 0x17)
/usr/local/go/src/runtime/netpoll.go:164 +0x59
net.(*pollDesc).wait(0xc4201b84c8, 0x72, 0x266c700, 0x2661ba8)
/usr/local/go/src/net/fd_poll_runtime.go:75 +0x38
net.(*pollDesc).waitRead(0xc4201b84c8, 0xc4209f8000, 0x1000)
/usr/local/go/src/net/fd_poll_runtime.go:80 +0x34
net.(*netFD).Read(0xc4201b8460, 0xc4209f8000, 0x1000, 0x1000, 0x0, 0x266c700, 0x2661ba8)
/usr/local/go/src/net/fd_unix.go:250 +0x1b7
net.(*conn).Read(0xc4207c4110, 0xc4209f8000, 0x1000, 0x1000, 0x0, 0x0, 0x0)
/usr/local/go/src/net/net.go:181 +0x70
net/http.(*persistConn).Read(0xc420660360, 0xc4209f8000, 0x1000, 0x1000, 0x4, 0xc4202a2140, 0x17)
/usr/local/go/src/net/http/transport.go:1316 +0x14b
bufio.(*Reader).fill(0xc4209fb4a0)
/usr/local/go/src/bufio/bufio.go:97 +0x117
bufio.(*Reader).Peek(0xc4209fb4a0, 0x1, 0x0, 0x1, 0x0, 0xc420bda420, 0x0)
/usr/local/go/src/bufio/bufio.go:129 +0x67
net/http.(*persistConn).readLoop(0xc420660360)
/usr/local/go/src/net/http/transport.go:1474 +0x196
created by net/http.(*Transport).dialConn
/usr/local/go/src/net/http/transport.go:1117 +0xa35
goroutine 197 [select]:
github.com/cockroachdb/cockroach/pkg/rpc.(*Context).runHeartbeat(0xc420281450, 0xc420b45b40, 0xc4202d5d90, 0xf, 0x0, 0x0)
/go/src/github.com/cockroachdb/cockroach/pkg/rpc/context.go:412 +0x7ef
github.com/cockroachdb/cockroach/pkg/rpc.(*Context).GRPCDial.func1.2.1(0x7f4af7f29238, 0xc420288180)
/go/src/github.com/cockroachdb/cockroach/pkg/rpc/context.go:346 +0x6b
github.com/cockroachdb/cockroach/pkg/util/stop.(*Stopper).RunWorker.func1(0xc4202b4d60, 0xc42001cea0, 0xc4202880c0)
/go/src/github.com/cockroachdb/cockroach/pkg/util/stop/stopper.go:193 +0xf7
created by github.com/cockroachdb/cockroach/pkg/util/stop.(*Stopper).RunWorker
/go/src/github.com/cockroachdb/cockroach/pkg/util/stop/stopper.go:194 +0xad
goroutine 196 [select]:
github.com/cockroachdb/cockroach/vendor/google.golang.org/grpc.(*addrConn).resetTransport(0xc420815500, 0xc42091e500, 0x0, 0x0)
/go/src/github.com/cockroachdb/cockroach/vendor/google.golang.org/grpc/clientconn.go:888 +0x8e5
github.com/cockroachdb/cockroach/vendor/google.golang.org/grpc.(*addrConn).transportMonitor(0xc420815500)
/go/src/github.com/cockroachdb/cockroach/vendor/google.golang.org/grpc/clientconn.go:972 +0x362
github.com/cockroachdb/cockroach/vendor/google.golang.org/grpc.(*ClientConn).resetAddrConn.func1(0xc420815500)
/go/src/github.com/cockroachdb/cockroach/vendor/google.golang.org/grpc/clientconn.go:642 +0x1d9
created by github.com/cockroachdb/cockroach/vendor/google.golang.org/grpc.(*ClientConn).resetAddrConn
/go/src/github.com/cockroachdb/cockroach/vendor/google.golang.org/grpc/clientconn.go:643 +0x786
goroutine 516 [select, 8 minutes]:
net/http.(*persistConn).writeLoop(0xc4209d66c0)
/usr/local/go/src/net/http/transport.go:1704 +0x43a
created by net/http.(*Transport).dialConn
/usr/local/go/src/net/http/transport.go:1118 +0xa5a
goroutine 515 [IO wait, 8 minutes]:
net.runtime_pollWait(0x7f4af805e9e8, 0x72, 0x11)
/usr/local/go/src/runtime/netpoll.go:164 +0x59
net.(*pollDesc).wait(0xc4205c1178, 0x72, 0x266c700, 0x2661ba8)
/usr/local/go/src/net/fd_poll_runtime.go:75 +0x38
net.(*pollDesc).waitRead(0xc4205c1178, 0xc42049c000, 0x1000)
/usr/local/go/src/net/fd_poll_runtime.go:80 +0x34
net.(*netFD).Read(0xc4205c1110, 0xc42049c000, 0x1000, 0x1000, 0x0, 0x266c700, 0x2661ba8)
/usr/local/go/src/net/fd_unix.go:250 +0x1b7
net.(*conn).Read(0xc4207c41b0, 0xc42049c000, 0x1000, 0x1000, 0x0, 0x0, 0x0)
/usr/local/go/src/net/net.go:181 +0x70
net/http.(*persistConn).Read(0xc4209d66c0, 0xc42049c000, 0x1000, 0x1000, 0x4, 0xc42027f4c0, 0x17)
/usr/local/go/src/net/http/transport.go:1316 +0x14b
bufio.(*Reader).fill(0xc42085ccc0)
/usr/local/go/src/bufio/bufio.go:97 +0x117
bufio.(*Reader).Peek(0xc42085ccc0, 0x1, 0x0, 0x1, 0x0, 0xc420ab5500, 0x0)
/usr/local/go/src/bufio/bufio.go:129 +0x67
net/http.(*persistConn).readLoop(0xc4209d66c0)
/usr/local/go/src/net/http/transport.go:1474 +0x196
created by net/http.(*Transport).dialConn
/usr/local/go/src/net/http/transport.go:1117 +0xa35
goroutine 5487 [chan receive, 2 minutes]:
database/sql.(*DB).connectionOpener(0xc420b4a1e0)
/usr/local/go/src/database/sql/sql.go:837 +0x4a
created by database/sql.Open
/usr/local/go/src/database/sql/sql.go:582 +0x212
goroutine 397 [select, 8 minutes]:
net/http.(*persistConn).writeLoop(0xc420772a20)
/usr/local/go/src/net/http/transport.go:1704 +0x43a
created by net/http.(*Transport).dialConn
/usr/local/go/src/net/http/transport.go:1118 +0xa5a
goroutine 396 [IO wait, 8 minutes]:
net.runtime_pollWait(0x7f4af805e868, 0x72, 0xb)
/usr/local/go/src/runtime/netpoll.go:164 +0x59
net.(*pollDesc).wait(0xc42019c228, 0x72, 0x266c700, 0x2661ba8)
/usr/local/go/src/net/fd_poll_runtime.go:75 +0x38
net.(*pollDesc).waitRead(0xc42019c228, 0xc4201c3000, 0x1000)
/usr/local/go/src/net/fd_poll_runtime.go:80 +0x34
net.(*netFD).Read(0xc42019c1c0, 0xc4201c3000, 0x1000, 0x1000, 0x0, 0x266c700, 0x2661ba8)
/usr/local/go/src/net/fd_unix.go:250 +0x1b7
net.(*conn).Read(0xc420474050, 0xc4201c3000, 0x1000, 0x1000, 0x0, 0x0, 0x0)
/usr/local/go/src/net/net.go:181 +0x70
net/http.(*persistConn).Read(0xc420772a20, 0xc4201c3000, 0x1000, 0x1000, 0x4, 0xc42020d0e0, 0x17)
/usr/local/go/src/net/http/transport.go:1316 +0x14b
bufio.(*Reader).fill(0xc420b56000)
/usr/local/go/src/bufio/bufio.go:97 +0x117
bufio.(*Reader).Peek(0xc420b56000, 0x1, 0x0, 0x1, 0x0, 0xc4202cfda0, 0x0)
/usr/local/go/src/bufio/bufio.go:129 +0x67
net/http.(*persistConn).readLoop(0xc420772a20)
/usr/local/go/src/net/http/transport.go:1474 +0x196
created by net/http.(*Transport).dialConn
/usr/local/go/src/net/http/transport.go:1117 +0xa35
goroutine 1097 [IO wait, 7 minutes]:
net.runtime_pollWait(0x7f4af805e328, 0x72, 0x1b)
/usr/local/go/src/runtime/netpoll.go:164 +0x59
net.(*pollDesc).wait(0xc420b04a78, 0x72, 0x266c700, 0x2661ba8)
/usr/local/go/src/net/fd_poll_runtime.go:75 +0x38
net.(*pollDesc).waitRead(0xc420b04a78, 0xc4208a0000, 0x1000)
/usr/local/go/src/net/fd_poll_runtime.go:80 +0x34
net.(*netFD).Read(0xc420b04a10, 0xc4208a0000, 0x1000, 0x1000, 0x0, 0x266c700, 0x2661ba8)
/usr/local/go/src/net/fd_unix.go:250 +0x1b7
net.(*conn).Read(0xc420778148, 0xc4208a0000, 0x1000, 0x1000, 0x0, 0x0, 0x0)
/usr/local/go/src/net/net.go:181 +0x70
net/http.(*persistConn).Read(0xc4202a8360, 0xc4208a0000, 0x1000, 0x1000, 0x4, 0xc4202f40e0, 0x17)
/usr/local/go/src/net/http/transport.go:1316 +0x14b
bufio.(*Reader).fill(0xc420c7f380)
/usr/local/go/src/bufio/bufio.go:97 +0x117
bufio.(*Reader).Peek(0xc420c7f380, 0x1, 0x0, 0x1, 0x0, 0xc420530f00, 0x0)
/usr/local/go/src/bufio/bufio.go:129 +0x67
net/http.(*persistConn).readLoop(0xc4202a8360)
/usr/local/go/src/net/http/transport.go:1474 +0x196
created by net/http.(*Transport).dialConn
/usr/local/go/src/net/http/transport.go:1117 +0xa35
goroutine 512 [chan receive, 8 minutes]:
database/sql.(*DB).connectionOpener(0xc4207f2320)
/usr/local/go/src/database/sql/sql.go:837 +0x4a
created by database/sql.Open
/usr/local/go/src/database/sql/sql.go:582 +0x212
goroutine 631 [select]:
github.com/cockroachdb/cockroach/vendor/google.golang.org/grpc.(*addrConn).resetTransport(0xc420242fc0, 0xc420b18800, 0x0, 0x0)
/go/src/github.com/cockroachdb/cockroach/vendor/google.golang.org/grpc/clientconn.go:888 +0x8e5
github.com/cockroachdb/cockroach/vendor/google.golang.org/grpc.(*addrConn).transportMonitor(0xc420242fc0)
/go/src/github.com/cockroachdb/cockroach/vendor/google.golang.org/grpc/clientconn.go:972 +0x362
github.com/cockroachdb/cockroach/vendor/google.golang.org/grpc.(*ClientConn).resetAddrConn.func1(0xc420242fc0)
/go/src/github.com/cockroachdb/cockroach/vendor/google.golang.org/grpc/clientconn.go:642 +0x1d9
created by github.com/cockroachdb/cockroach/vendor/google.golang.org/grpc.(*ClientConn).resetAddrConn
/go/src/github.com/cockroachdb/cockroach/vendor/google.golang.org/grpc/clientconn.go:643 +0x786
goroutine 441 [chan receive, 8 minutes]:
database/sql.(*DB).connectionOpener(0xc420579180)
/usr/local/go/src/database/sql/sql.go:837 +0x4a
created by database/sql.Open
/usr/local/go/src/database/sql/sql.go:582 +0x212
goroutine 2130 [IO wait, 5 minutes]:
net.runtime_pollWait(0x7f4af80622b8, 0x72, 0x26)
/usr/local/go/src/runtime/netpoll.go:164 +0x59
net.(*pollDesc).wait(0xc4204fa8b8, 0x72, 0x266c700, 0x2661ba8)
/usr/local/go/src/net/fd_poll_runtime.go:75 +0x38
net.(*pollDesc).waitRead(0xc4204fa8b8, 0xc420c81000, 0x1000)
/usr/local/go/src/net/fd_poll_runtime.go:80 +0x34
net.(*netFD).Read(0xc4204fa850, 0xc420c81000, 0x1000, 0x1000, 0x0, 0x266c700, 0x2661ba8)
/usr/local/go/src/net/fd_unix.go:250 +0x1b7
net.(*conn).Read(0xc4207c41c0, 0xc420c81000, 0x1000, 0x1000, 0x0, 0x0, 0x0)
/usr/local/go/src/net/net.go:181 +0x70
net/http.(*persistConn).Read(0xc4206606c0, 0xc420c81000, 0x1000, 0x1000, 0x4, 0xc4202a3380, 0x17)
/usr/local/go/src/net/http/transport.go:1316 +0x14b
bufio.(*Reader).fill(0xc420729560)
/usr/local/go/src/bufio/bufio.go:97 +0x117
bufio.(*Reader).Peek(0xc420729560, 0x1, 0x0, 0x1, 0x0, 0xc4208ba780, 0x0)
/usr/local/go/src/bufio/bufio.go:129 +0x67
net/http.(*persistConn).readLoop(0xc4206606c0)
/usr/local/go/src/net/http/transport.go:1474 +0x196
created by net/http.(*Transport).dialConn
/usr/local/go/src/net/http/transport.go:1117 +0xa35
goroutine 1098 [select, 7 minutes]:
net/http.(*persistConn).writeLoop(0xc4202a8360)
/usr/local/go/src/net/http/transport.go:1704 +0x43a
created by net/http.(*Transport).dialConn
/usr/local/go/src/net/http/transport.go:1118 +0xa5a
goroutine 597 [select, 8 minutes]:
net/http.(*persistConn).writeLoop(0xc4202a8d80)
/usr/local/go/src/net/http/transport.go:1704 +0x43a
created by net/http.(*Transport).dialConn
/usr/local/go/src/net/http/transport.go:1118 +0xa5a
goroutine 2680 [chan receive, 4 minutes]:
database/sql.(*DB).connectionOpener(0xc4202726e0)
/usr/local/go/src/database/sql/sql.go:837 +0x4a
created by database/sql.Open
/usr/local/go/src/database/sql/sql.go:582 +0x212
goroutine 632 [select]:
github.com/cockroachdb/cockroach/pkg/rpc.(*Context).runHeartbeat(0xc4207d6820, 0xc4208dfb00, 0xc4201e1b30, 0xf, 0x0, 0x0)
/go/src/github.com/cockroachdb/cockroach/pkg/rpc/context.go:412 +0x7ef
github.com/cockroachdb/cockroach/pkg/rpc.(*Context).GRPCDial.func1.2.1(0x7f4af7f29238, 0xc4207a1ad0)
/go/src/github.com/cockroachdb/cockroach/pkg/rpc/context.go:346 +0x6b
github.com/cockroachdb/cockroach/pkg/util/stop.(*Stopper).RunWorker.func1(0xc420245d70, 0xc42001cea0, 0xc4207a1a40)
/go/src/github.com/cockroachdb/cockroach/pkg/util/stop/stopper.go:193 +0xf7
created by github.com/cockroachdb/cockroach/pkg/util/stop.(*Stopper).RunWorker
/go/src/github.com/cockroachdb/cockroach/pkg/util/stop/stopper.go:194 +0xad
goroutine 629 [chan receive, 8 minutes]:
github.com/cockroachdb/cockroach/pkg/rpc.NewContext.func1(0x7f4af7f29238, 0xc4207a0240)
/go/src/github.com/cockroachdb/cockroach/pkg/rpc/context.go:209 +0x5d
github.com/cockroachdb/cockroach/pkg/util/stop.(*Stopper).RunWorker.func1(0xc4201e1660, 0xc42001cea0, 0xc420296be0)
/go/src/github.com/cockroachdb/cockroach/pkg/util/stop/stopper.go:193 +0xf7
created by github.com/cockroachdb/cockroach/pkg/util/stop.(*Stopper).RunWorker
/go/src/github.com/cockroachdb/cockroach/pkg/util/stop/stopper.go:194 +0xad
goroutine 667 [IO wait, 8 minutes]:
net.runtime_pollWait(0x7f4af805e7a8, 0x72, 0x6)
/usr/local/go/src/runtime/netpoll.go:164 +0x59
net.(*pollDesc).wait(0xc420b02768, 0x72, 0x266c700, 0x2661ba8)
/usr/local/go/src/net/fd_poll_runtime.go:75 +0x38
net.(*pollDesc).waitRead(0xc420b02768, 0xc420a7e000, 0x1000)
/usr/local/go/src/net/fd_poll_runtime.go:80 +0x34
net.(*netFD).Read(0xc420b02700, 0xc420a7e000, 0x1000, 0x1000, 0x0, 0x266c700, 0x2661ba8)
/usr/local/go/src/net/fd_unix.go:250 +0x1b7
net.(*conn).Read(0xc42000e498, 0xc420a7e000, 0x1000, 0x1000, 0x0, 0x0, 0x0)
/usr/local/go/src/net/net.go:181 +0x70
net/http.(*persistConn).Read(0xc42042f7a0, 0xc420a7e000, 0x1000, 0x1000, 0x4, 0xc4202e4660, 0x17)
/usr/local/go/src/net/http/transport.go:1316 +0x14b
bufio.(*Reader).fill(0xc420bdaae0)
/usr/local/go/src/bufio/bufio.go:97 +0x117
bufio.(*Reader).Peek(0xc420bdaae0, 0x1, 0x0, 0x1, 0x0, 0xc42055f1a0, 0x0)
/usr/local/go/src/bufio/bufio.go:129 +0x67
net/http.(*persistConn).readLoop(0xc42042f7a0)
/usr/local/go/src/net/http/transport.go:1474 +0x196
created by net/http.(*Transport).dialConn
/usr/local/go/src/net/http/transport.go:1117 +0xa35
goroutine 1553 [IO wait, 6 minutes]:
net.runtime_pollWait(0x7f4af8062738, 0x72, 0x20)
/usr/local/go/src/runtime/netpoll.go:164 +0x59
net.(*pollDesc).wait(0xc420464768, 0x72, 0x266c700, 0x2661ba8)
/usr/local/go/src/net/fd_poll_runtime.go:75 +0x38
net.(*pollDesc).waitRead(0xc420464768, 0xc4207e5000, 0x1000)
/usr/local/go/src/net/fd_poll_runtime.go:80 +0x34
net.(*netFD).Read(0xc420464700, 0xc4207e5000, 0x1000, 0x1000, 0x0, 0x266c700, 0x2661ba8)
/usr/local/go/src/net/fd_unix.go:250 +0x1b7
net.(*conn).Read(0xc4207c4128, 0xc4207e5000, 0x1000, 0x1000, 0x0, 0x0, 0x0)
/usr/local/go/src/net/net.go:181 +0x70
net/http.(*persistConn).Read(0xc4200c3b00, 0xc4207e5000, 0x1000, 0x1000, 0x4, 0xc42026ece0, 0x17)
/usr/local/go/src/net/http/transport.go:1316 +0x14b
bufio.(*Reader).fill(0xc420531740)
/usr/local/go/src/bufio/bufio.go:97 +0x117
bufio.(*Reader).Peek(0xc420531740, 0x1, 0x0, 0x1, 0x0, 0xc4209fc420, 0x0)
/usr/local/go/src/bufio/bufio.go:129 +0x67
net/http.(*persistConn).readLoop(0xc4200c3b00)
/usr/local/go/src/net/http/transport.go:1474 +0x196
created by net/http.(*Transport).dialConn
/usr/local/go/src/net/http/transport.go:1117 +0xa35
goroutine 2182 [select, 5 minutes]:
net/http.(*persistConn).writeLoop(0xc420660a20)
/usr/local/go/src/net/http/transport.go:1704 +0x43a
created by net/http.(*Transport).dialConn
/usr/local/go/src/net/http/transport.go:1118 +0xa5a
goroutine 509 [select]:
github.com/cockroachdb/cockroach/vendor/google.golang.org/grpc.(*addrConn).resetTransport(0xc4205388c0, 0xc420ab4900, 0x0, 0x0)
/go/src/github.com/cockroachdb/cockroach/vendor/google.golang.org/grpc/clientconn.go:888 +0x8e5
github.com/cockroachdb/cockroach/vendor/google.golang.org/grpc.(*addrConn).transportMonitor(0xc4205388c0)
/go/src/github.com/cockroachdb/cockroach/vendor/google.golang.org/grpc/clientconn.go:972 +0x362
github.com/cockroachdb/cockroach/vendor/google.golang.org/grpc.(*ClientConn).resetAddrConn.func1(0xc4205388c0)
/go/src/github.com/cockroachdb/cockroach/vendor/google.golang.org/grpc/clientconn.go:642 +0x1d9
created by github.com/cockroachdb/cockroach/vendor/google.golang.org/grpc.(*ClientConn).resetAddrConn
/go/src/github.com/cockroachdb/cockroach/vendor/google.golang.org/grpc/clientconn.go:643 +0x786
goroutine 510 [select]:
github.com/cockroachdb/cockroach/pkg/rpc.(*Context).runHeartbeat(0xc4202811e0, 0xc42079ee40, 0xc420a0c5f0, 0xf, 0x0, 0x0)
/go/src/github.com/cockroachdb/cockroach/pkg/rpc/context.go:412 +0x7ef
github.com/cockroachdb/cockroach/pkg/rpc.(*Context).GRPCDial.func1.2.1(0x7f4af7f29238, 0xc4207a0ba0)
/go/src/github.com/cockroachdb/cockroach/pkg/rpc/context.go:346 +0x6b
github.com/cockroachdb/cockroach/pkg/util/stop.(*Stopper).RunWorker.func1(0xc4202453d0, 0xc42001cea0, 0xc4207a0b10)
/go/src/github.com/cockroachdb/cockroach/pkg/util/stop/stopper.go:193 +0xf7
created by github.com/cockroachdb/cockroach/pkg/util/stop.(*Stopper).RunWorker
/go/src/github.com/cockroachdb/cockroach/pkg/util/stop/stopper.go:194 +0xad
goroutine 544 [chan receive, 8 minutes]:
github.com/cockroachdb/cockroach/pkg/rpc.NewContext.func1(0x7f4af7f29238, 0xc420791a10)
/go/src/github.com/cockroachdb/cockroach/pkg/rpc/context.go:209 +0x5d
github.com/cockroachdb/cockroach/pkg/util/stop.(*Stopper).RunWorker.func1(0xc420310ad0, 0xc42001cea0, 0xc420264e60)
/go/src/github.com/cockroachdb/cockroach/pkg/util/stop/stopper.go:193 +0xf7
created by github.com/cockroachdb/cockroach/pkg/util/stop.(*Stopper).RunWorker
/go/src/github.com/cockroachdb/cockroach/pkg/util/stop/stopper.go:194 +0xad
goroutine 1747 [IO wait, 6 minutes]:
net.runtime_pollWait(0x7f4af80625b8, 0x72, 0x22)
/usr/local/go/src/runtime/netpoll.go:164 +0x59
net.(*pollDesc).wait(0xc420b04308, 0x72, 0x266c700, 0x2661ba8)
/usr/local/go/src/net/fd_poll_runtime.go:75 +0x38
net.(*pollDesc).waitRead(0xc420b04308, 0xc42031d000, 0x1000)
/usr/local/go/src/net/fd_poll_runtime.go:80 +0x34
net.(*netFD).Read(0xc420b042a0, 0xc42031d000, 0x1000, 0x1000, 0x0, 0x266c700, 0x2661ba8)
/usr/local/go/src/net/fd_unix.go:250 +0x1b7
net.(*conn).Read(0xc42000e190, 0xc42031d000, 0x1000, 0x1000, 0x0, 0x0, 0x0)
/usr/local/go/src/net/net.go:181 +0x70
net/http.(*persistConn).Read(0xc4209a27e0, 0xc42031d000, 0x1000, 0x1000, 0x4, 0xc4202bace0, 0x17)
/usr/local/go/src/net/http/transport.go:1316 +0x14b
bufio.(*Reader).fill(0xc4208b4de0)
/usr/local/go/src/bufio/bufio.go:97 +0x117
bufio.(*Reader).Peek(0xc4208b4de0, 0x1, 0x0, 0x1, 0x0, 0xc420802960, 0x0)
/usr/local/go/src/bufio/bufio.go:129 +0x67
net/http.(*persistConn).readLoop(0xc4209a27e0)
/usr/local/go/src/net/http/transport.go:1474 +0x196
created by net/http.(*Transport).dialConn
/usr/local/go/src/net/http/transport.go:1117 +0xa35
goroutine 4145 [IO wait, 2 minutes]:
net.runtime_pollWait(0x7f4af8061bf8, 0x72, 0x2d)
/usr/local/go/src/runtime/netpoll.go:164 +0x59
net.(*pollDesc).wait(0xc4210b8228, 0x72, 0x266c700, 0x2661ba8)
/usr/local/go/src/net/fd_poll_runtime.go:75 +0x38
net.(*pollDesc).waitRead(0xc4210b8228, 0xc420c15000, 0x1000)
/usr/local/go/src/net/fd_poll_runtime.go:80 +0x34
net.(*netFD).Read(0xc4210b81c0, 0xc420c15000, 0x1000, 0x1000, 0x0, 0x266c700, 0x2661ba8)
/usr/local/go/src/net/fd_unix.go:250 +0x1b7
net.(*conn).Read(0xc420a8e390, 0xc420c15000, 0x1000, 0x1000, 0x0, 0x0, 0x0)
/usr/local/go/src/net/net.go:181 +0x70
net/http.(*persistConn).Read(0xc4201b0a20, 0xc420c15000, 0x1000, 0x1000, 0x4, 0xc420b87120, 0x17)
/usr/local/go/src/net/http/transport.go:1316 +0x14b
bufio.(*Reader).fill(0xc4210b2f60)
/usr/local/go/src/bufio/bufio.go:97 +0x117
bufio.(*Reader).Peek(0xc4210b2f60, 0x1, 0x0, 0x1, 0x0, 0xc420c41c20, 0x0)
/usr/local/go/src/bufio/bufio.go:129 +0x67
net/http.(*persistConn).readLoop(0xc4201b0a20)
/usr/local/go/src/net/http/transport.go:1474 +0x196
created by net/http.(*Transport).dialConn
/usr/local/go/src/net/http/transport.go:1117 +0xa35
goroutine 2117 [select, 5 minutes]:
net/http.(*persistConn).writeLoop(0xc4202a8a20)
/usr/local/go/src/net/http/transport.go:1704 +0x43a
created by net/http.(*Transport).dialConn
/usr/local/go/src/net/http/transport.go:1118 +0xa5a
goroutine 4534 [select]:
github.com/cockroachdb/cockroach/pkg/rpc.(*Context).runHeartbeat(0xc42073fad0, 0xc42078c400, 0xc420390fa0, 0xf, 0x0, 0x0)
/go/src/github.com/cockroachdb/cockroach/pkg/rpc/context.go:412 +0x7ef
github.com/cockroachdb/cockroach/pkg/rpc.(*Context).GRPCDial.func1.2.1(0x7f4af7f29238, 0xc421359860)
/go/src/github.com/cockroachdb/cockroach/pkg/rpc/context.go:346 +0x6b
github.com/cockroachdb/cockroach/pkg/util/stop.(*Stopper).RunWorker.func1(0xc42033e0e0, 0xc42001cea0, 0xc421359710)
/go/src/github.com/cockroachdb/cockroach/pkg/util/stop/stopper.go:193 +0xf7
created by github.com/cockroachdb/cockroach/pkg/util/stop.(*Stopper).RunWorker
/go/src/github.com/cockroachdb/cockroach/pkg/util/stop/stopper.go:194 +0xad
goroutine 1748 [select, 6 minutes]:
net/http.(*persistConn).writeLoop(0xc4209a27e0)
/usr/local/go/src/net/http/transport.go:1704 +0x43a
created by net/http.(*Transport).dialConn
/usr/local/go/src/net/http/transport.go:1118 +0xa5a
goroutine 2531 [select]:
github.com/cockroachdb/cockroach/vendor/google.golang.org/grpc.(*addrConn).resetTransport(0xc42040ee00, 0xc420743300, 0x0, 0x0)
/go/src/github.com/cockroachdb/cockroach/vendor/google.golang.org/grpc/clientconn.go:888 +0x8e5
github.com/cockroachdb/cockroach/vendor/google.golang.org/grpc.(*addrConn).transportMonitor(0xc42040ee00)
/go/src/github.com/cockroachdb/cockroach/vendor/google.golang.org/grpc/clientconn.go:972 +0x362
github.com/cockroachdb/cockroach/vendor/google.golang.org/grpc.(*ClientConn).resetAddrConn.func1(0xc42040ee00)
/go/src/github.com/cockroachdb/cockroach/vendor/google.golang.org/grpc/clientconn.go:642 +0x1d9
created by github.com/cockroachdb/cockroach/vendor/google.golang.org/grpc.(*ClientConn).resetAddrConn
/go/src/github.com/cockroachdb/cockroach/vendor/google.golang.org/grpc/clientconn.go:643 +0x786
goroutine 788 [select, 8 minutes]:
net/http.(*persistConn).writeLoop(0xc420660360)
/usr/local/go/src/net/http/transport.go:1704 +0x43a
created by net/http.(*Transport).dialConn
/usr/local/go/src/net/http/transport.go:1118 +0xa5a
goroutine 890 [select, 7 minutes]:
net/http.(*persistConn).writeLoop(0xc4206607e0)
/usr/local/go/src/net/http/transport.go:1704 +0x43a
created by net/http.(*Transport).dialConn
/usr/local/go/src/net/http/transport.go:1118 +0xa5a
goroutine 889 [IO wait, 7 minutes]:
net.runtime_pollWait(0x7f4af805e4a8, 0x72, 0x19)
/usr/local/go/src/runtime/netpoll.go:164 +0x59
net.(*pollDesc).wait(0xc420562458, 0x72, 0x266c700, 0x2661ba8)
/usr/local/go/src/net/fd_poll_runtime.go:75 +0x38
net.(*pollDesc).waitRead(0xc420562458, 0xc4207c1000, 0x1000)
/usr/local/go/src/net/fd_poll_runtime.go:80 +0x34
net.(*netFD).Read(0xc4205623f0, 0xc4207c1000, 0x1000, 0x1000, 0x0, 0x266c700, 0x2661ba8)
/usr/local/go/src/net/fd_unix.go:250 +0x1b7
net.(*conn).Read(0xc42000e110, 0xc4207c1000, 0x1000, 0x1000, 0x0, 0x0, 0x0)
/usr/local/go/src/net/net.go:181 +0x70
net/http.(*persistConn).Read(0xc4206607e0, 0xc4207c1000, 0x1000, 0x1000, 0x4, 0xc4202baa40, 0x17)
/usr/local/go/src/net/http/transport.go:1316 +0x14b
bufio.(*Reader).fill(0xc420b497a0)
/usr/local/go/src/bufio/bufio.go:97 +0x117
bufio.(*Reader).Peek(0xc420b497a0, 0x1, 0x0, 0x1, 0x0, 0xc4201c45a0, 0x0)
/usr/local/go/src/bufio/bufio.go:129 +0x67
net/http.(*persistConn).readLoop(0xc4206607e0)
/usr/local/go/src/net/http/transport.go:1474 +0x196
created by net/http.(*Transport).dialConn
/usr/local/go/src/net/http/transport.go:1117 +0xa35
goroutine 1309 [IO wait, 6 minutes]:
net.runtime_pollWait(0x7f4af80628b8, 0x72, 0x1e)
/usr/local/go/src/runtime/netpoll.go:164 +0x59
net.(*pollDesc).wait(0xc4202983e8, 0x72, 0x266c700, 0x2661ba8)
/usr/local/go/src/net/fd_poll_runtime.go:75 +0x38
net.(*pollDesc).waitRead(0xc4202983e8, 0xc420548000, 0x1000)
/usr/local/go/src/net/fd_poll_runtime.go:80 +0x34
net.(*netFD).Read(0xc420298380, 0xc420548000, 0x1000, 0x1000, 0x0, 0x266c700, 0x2661ba8)
/usr/local/go/src/net/fd_unix.go:250 +0x1b7
net.(*conn).Read(0xc4207781e8, 0xc420548000, 0x1000, 0x1000, 0x0, 0x0, 0x0)
/usr/local/go/src/net/net.go:181 +0x70
net/http.(*persistConn).Read(0xc420772360, 0xc420548000, 0x1000, 0x1000, 0x4, 0xc420249200, 0x17)
/usr/local/go/src/net/http/transport.go:1316 +0x14b
bufio.(*Reader).fill(0xc420531620)
/usr/local/go/src/bufio/bufio.go:97 +0x117
bufio.(*Reader).Peek(0xc420531620, 0x1, 0x0, 0x1, 0x0, 0xc4209f6540, 0x0)
/usr/local/go/src/bufio/bufio.go:129 +0x67
net/http.(*persistConn).readLoop(0xc420772360)
/usr/local/go/src/net/http/transport.go:1474 +0x196
created by net/http.(*Transport).dialConn
/usr/local/go/src/net/http/transport.go:1117 +0xa35
goroutine 1166 [IO wait, 7 minutes]:
net.runtime_pollWait(0x7f4af8062a38, 0x72, 0x1c)
/usr/local/go/src/runtime/netpoll.go:164 +0x59
net.(*pollDesc).wait(0xc420b043e8, 0x72, 0x266c700, 0x2661ba8)
/usr/local/go/src/net/fd_poll_runtime.go:75 +0x38
net.(*pollDesc).waitRead(0xc420b043e8, 0xc4206c2000, 0x1000)
/usr/local/go/src/net/fd_poll_runtime.go:80 +0x34
net.(*netFD).Read(0xc420b04380, 0xc4206c2000, 0x1000, 0x1000, 0x0, 0x266c700, 0x2661ba8)
/usr/local/go/src/net/fd_unix.go:250 +0x1b7
net.(*conn).Read(0xc420778070, 0xc4206c2000, 0x1000, 0x1000, 0x0, 0x0, 0x0)
/usr/local/go/src/net/net.go:181 +0x70
net/http.(*persistConn).Read(0xc4202a8900, 0xc4206c2000, 0x1000, 0x1000, 0x4, 0xc4202f4ee0, 0x17)
/usr/local/go/src/net/http/transport.go:1316 +0x14b
bufio.(*Reader).fill(0xc420a73140)
/usr/local/go/src/bufio/bufio.go:97 +0x117
bufio.(*Reader).Peek(0xc420a73140, 0x1, 0x0, 0x1, 0x0, 0xc420530480, 0x0)
/usr/local/go/src/bufio/bufio.go:129 +0x67
net/http.(*persistConn).readLoop(0xc4202a8900)
/usr/local/go/src/net/http/transport.go:1474 +0x196
created by net/http.(*Transport).dialConn
/usr/local/go/src/net/http/transport.go:1117 +0xa35
goroutine 4556 [select]:
github.com/cockroachdb/cockroach/vendor/google.golang.org/grpc.(*addrConn).resetTransport(0xc420c561c0, 0xc420f12500, 0x0, 0x0)
/go/src/github.com/cockroachdb/cockroach/vendor/google.golang.org/grpc/clientconn.go:888 +0x8e5
github.com/cockroachdb/cockroach/vendor/google.golang.org/grpc.(*addrConn).transportMonitor(0xc420c561c0)
/go/src/github.com/cockroachdb/cockroach/vendor/google.golang.org/grpc/clientconn.go:972 +0x362
github.com/cockroachdb/cockroach/vendor/google.golang.org/grpc.(*ClientConn).resetAddrConn.func1(0xc420c561c0)
/go/src/github.com/cockroachdb/cockroach/vendor/google.golang.org/grpc/clientconn.go:642 +0x1d9
created by github.com/cockroachdb/cockroach/vendor/google.golang.org/grpc.(*ClientConn).resetAddrConn
/go/src/github.com/cockroachdb/cockroach/vendor/google.golang.org/grpc/clientconn.go:643 +0x786
goroutine 2425 [IO wait, 5 minutes]:
net.runtime_pollWait(0x7f4af8061fb8, 0x72, 0x2a)
/usr/local/go/src/runtime/netpoll.go:164 +0x59
net.(*pollDesc).wait(0xc4200bd3a8, 0x72, 0x266c700, 0x2661ba8)
/usr/local/go/src/net/fd_poll_runtime.go:75 +0x38
net.(*pollDesc).waitRead(0xc4200bd3a8, 0xc420946000, 0x1000)
/usr/local/go/src/net/fd_poll_runtime.go:80 +0x34
net.(*netFD).Read(0xc4200bd340, 0xc420946000, 0x1000, 0x1000, 0x0, 0x266c700, 0x2661ba8)
/usr/local/go/src/net/fd_unix.go:250 +0x1b7
net.(*conn).Read(0xc4207782e0, 0xc420946000, 0x1000, 0x1000, 0x0, 0x0, 0x0)
/usr/local/go/src/net/net.go:181 +0x70
net/http.(*persistConn).Read(0xc420661d40, 0xc420946000, 0x1000, 0x1000, 0x4, 0xc4201d81c0, 0x17)
/usr/local/go/src/net/http/transport.go:1316 +0x14b
bufio.(*Reader).fill(0xc420c2bb60)
/usr/local/go/src/bufio/bufio.go:97 +0x117
bufio.(*Reader).Peek(0xc420c2bb60, 0x1, 0x0, 0x1, 0x0, 0xc42080cd80, 0x0)
/usr/local/go/src/bufio/bufio.go:129 +0x67
net/http.(*persistConn).readLoop(0xc420661d40)
/usr/local/go/src/net/http/transport.go:1474 +0x196
created by net/http.(*Transport).dialConn
/usr/local/go/src/net/http/transport.go:1117 +0xa35
goroutine 1167 [select, 7 minutes]:
net/http.(*persistConn).writeLoop(0xc4202a8900)
/usr
```
Please assign, take a look and update the issue accordingly. | 1.0 | teamcity: failed tests on master: acceptance/TestDockerReadWriteBidirectionalReferenceVersion - The following tests appear to have failed:
[#317353](https://teamcity.cockroachdb.com/viewLog.html?buildId=317353):
```
--- FAIL: acceptance/TestDockerReadWriteBidirectionalReferenceVersion (0.000s)
Test ended in panic.
------- Stdout: -------
xenial-20170214: Pulling from library/ubuntu
Digest: sha256:dd7808d8792c9841d0b460122f1acf0a2dd1f56404f8d1e56298048885e45535
Status: Image is up to date for ubuntu:xenial-20170214
20170423-1100: Pulling from cockroachdb/postgres-test
Digest: sha256:1fd869a88a4316aa1e464501fdff364aef43512ca8aa12914ebc0790f37a58c6
Status: Image is up to date for cockroachdb/postgres-test:20170423-1100
File: ���/cockroach/cockroach���
Size: 42379944 Blocks: 82776 IO Block: 4096 regular file
Device: 801h/2049d Inode: 270670 Links: 1
Access: (0755/-rwxr-xr-x) Uid: ( 1001/ UNKNOWN) Gid: ( 1001/ UNKNOWN)
Access: 2017-08-07 17:14:13.140447892 +0000
Modify: 2017-08-07 17:13:41.552359286 +0000
Change: 2017-08-07 17:13:41.592359399 +0000
Birth: -
xenial-20170214: Pulling from library/ubuntu
Digest: sha256:dd7808d8792c9841d0b460122f1acf0a2dd1f56404f8d1e56298048885e45535
Status: Image is up to date for ubuntu:xenial-20170214
20170423-1100: Pulling from cockroachdb/postgres-test
Digest: sha256:1fd869a88a4316aa1e464501fdff364aef43512ca8aa12914ebc0790f37a58c6
Status: Image is up to date for cockroachdb/postgres-test:20170423-1100
panic: test timed out after 10m0s
goroutine 10171 [running]:
testing.startAlarm.func1()
/usr/local/go/src/testing/testing.go:1023 +0xf9
created by time.goFunc
/usr/local/go/src/time/sleep.go:170 +0x44
goroutine 1 [chan receive]:
testing.(*T).Run(0xc420280750, 0x1a8e147, 0x30, 0x1b105f8, 0xc420525c01)
/usr/local/go/src/testing/testing.go:698 +0x2f4
testing.runTests.func1(0xc420280750)
/usr/local/go/src/testing/testing.go:882 +0x67
testing.tRunner(0xc420280750, 0xc420525d38)
/usr/local/go/src/testing/testing.go:657 +0x96
testing.runTests(0xc42023ab20, 0x2659640, 0x26, 0x26, 0x285eec0)
/usr/local/go/src/testing/testing.go:888 +0x2c1
testing.(*M).Run(0xc420687f20, 0x1b10560)
/usr/local/go/src/testing/testing.go:822 +0xfc
github.com/cockroachdb/cockroach/pkg/acceptance.RunTests(0xc420525f20)
/go/src/github.com/cockroachdb/cockroach/pkg/acceptance/util.go:148 +0x48
github.com/cockroachdb/cockroach/pkg/acceptance.MainTest(0xc420525f20)
/go/src/github.com/cockroachdb/cockroach/pkg/acceptance/test_acceptance.go:35 +0x3d
github.com/cockroachdb/cockroach/pkg/acceptance.TestMain(0xc420525f20)
/go/src/github.com/cockroachdb/cockroach/pkg/acceptance/main_test.go:22 +0x2b
main.main()
github.com/cockroachdb/cockroach/pkg/acceptance/_test/_testmain.go:114 +0xf7
goroutine 17 [syscall, 10 minutes, locked to thread]:
runtime.goexit()
/usr/local/go/src/runtime/asm_amd64.s:2197 +0x1
goroutine 6 [chan receive]:
github.com/cockroachdb/cockroach/pkg/util/log.(*loggingT).flushDaemon(0x28607c0)
/go/src/github.com/cockroachdb/cockroach/pkg/util/log/clog.go:988 +0x77
created by github.com/cockroachdb/cockroach/pkg/util/log.init.1
/go/src/github.com/cockroachdb/cockroach/pkg/util/log/clog.go:575 +0xd9
goroutine 18 [syscall, 10 minutes]:
os/signal.signal_recv(0xf02696593)
/usr/local/go/src/runtime/sigqueue.go:116 +0x104
os/signal.loop()
/usr/local/go/src/os/signal/signal_unix.go:22 +0x22
created by os/signal.init.1
/usr/local/go/src/os/signal/signal_unix.go:28 +0x41
goroutine 15 [chan receive, 10 minutes]:
github.com/cockroachdb/cockroach/pkg/acceptance.RunTests.func1()
/go/src/github.com/cockroachdb/cockroach/pkg/acceptance/util.go:139 +0xb6
created by github.com/cockroachdb/cockroach/pkg/acceptance.RunTests
/go/src/github.com/cockroachdb/cockroach/pkg/acceptance/util.go:147 +0x3a
goroutine 9738 [select]:
net/http.(*persistConn).roundTrip(0xc42063c360, 0xc4203c5920, 0x0, 0x0, 0x0)
/usr/local/go/src/net/http/transport.go:1898 +0x974
net/http.(*Transport).RoundTrip(0xc4207fa960, 0xc42114f200, 0xc4207fa960, 0x0, 0x0)
/usr/local/go/src/net/http/transport.go:391 +0x74c
net/http.send(0xc42114f200, 0x2669100, 0xc4207fa960, 0x0, 0x0, 0x0, 0x0, 0x8, 0xc420778688, 0x5be648)
/usr/local/go/src/net/http/client.go:249 +0x162
net/http.(*Client).send(0xc421417a10, 0xc42114f200, 0x0, 0x0, 0x0, 0xc420778688, 0x0, 0x1, 0x30)
/usr/local/go/src/net/http/client.go:173 +0x108
net/http.(*Client).Do(0xc421417a10, 0xc42114f200, 0xc4213c7da0, 0xc42114f200, 0xc4213c7da0)
/usr/local/go/src/net/http/client.go:595 +0x254
github.com/cockroachdb/cockroach/vendor/golang.org/x/net/context/ctxhttp.Do(0x7f4af8010c40, 0xc4213c7da0, 0xc421417a10, 0xc42114f100, 0xc4203d6fe0, 0xc421296580, 0x87a9bb)
/go/src/github.com/cockroachdb/cockroach/vendor/golang.org/x/net/context/ctxhttp/ctxhttp.go:30 +0x92
github.com/cockroachdb/cockroach/vendor/github.com/docker/docker/client.(*Client).doRequest(0xc421315880, 0x7f4af8010c40, 0xc4213c7da0, 0xc42114f100, 0x57, 0x0, 0x0, 0x0, 0xc42114f100, 0x0)
/go/src/github.com/cockroachdb/cockroach/vendor/github.com/docker/docker/client/request.go:127 +0x6e
github.com/cockroachdb/cockroach/vendor/github.com/docker/docker/client.(*Client).sendRequest(0xc421315880, 0x7f4af8010c40, 0xc4213c7da0, 0x1a4a97a, 0x4, 0xc4213c7e00, 0x51, 0x0, 0x0, 0x0, ...)
/go/src/github.com/cockroachdb/cockroach/vendor/github.com/docker/docker/client/request.go:121 +0x14a
github.com/cockroachdb/cockroach/vendor/github.com/docker/docker/client.(*Client).post(0xc421315880, 0x7f4af8010c40, 0xc4213c7da0, 0xc4213c7e00, 0x51, 0x0, 0x0, 0x0, 0x0, 0x0, ...)
/go/src/github.com/cockroachdb/cockroach/vendor/github.com/docker/docker/client/request.go:45 +0x14a
github.com/cockroachdb/cockroach/vendor/github.com/docker/docker/client.(*Client).ContainerWait(0xc421315880, 0x7f4af8010c40, 0xc4213c7da0, 0xc420f06ac0, 0x40, 0x0, 0x0, 0x0)
/go/src/github.com/cockroachdb/cockroach/vendor/github.com/docker/docker/client/container_wait.go:14 +0x107
github.com/cockroachdb/cockroach/pkg/acceptance/cluster.retryingDockerClient.ContainerWait.func1(0x7f4af8010c40, 0xc4213c7da0, 0x2540be400, 0x7f4af8010c40)
/go/src/github.com/cockroachdb/cockroach/pkg/acceptance/cluster/docker.go:479 +0x61
github.com/cockroachdb/cockroach/pkg/acceptance/cluster.retry(0x7f4af805d118, 0xc420018de8, 0xa, 0x2540be400, 0x1a56de2, 0xd, 0x1a49c29, 0x2, 0xc4212969a0, 0x0, ...)
/go/src/github.com/cockroachdb/cockroach/pkg/acceptance/cluster/docker.go:410 +0x92
github.com/cockroachdb/cockroach/pkg/acceptance/cluster.retryingDockerClient.ContainerWait(0x26957c0, 0xc421315880, 0xa, 0x2540be400, 0x7f4af805d118, 0xc420018de8, 0xc420f06ac0, 0x40, 0x0, 0x0, ...)
/go/src/github.com/cockroachdb/cockroach/pkg/acceptance/cluster/docker.go:482 +0x11f
github.com/cockroachdb/cockroach/pkg/acceptance/cluster.(*retryingDockerClient).ContainerWait(0xc4203251e0, 0x7f4af805d118, 0xc420018de8, 0xc420f06ac0, 0x40, 0x0, 0x0, 0x0)
<autogenerated>:318 +0x9a
github.com/cockroachdb/cockroach/pkg/acceptance/cluster.(*Container).Wait(0xc4202b9650, 0x7f4af805d118, 0xc420018de8, 0x0, 0x0)
/go/src/github.com/cockroachdb/cockroach/pkg/acceptance/cluster/docker.go:233 +0x95
github.com/cockroachdb/cockroach/pkg/acceptance/cluster.(*LocalCluster).OneShot(0xc42063c240, 0x7f4af805d118, 0xc420018de8, 0x1a9077b, 0x31, 0xc4203f3100, 0x0, 0x0, 0x0, 0x0, ...)
/go/src/github.com/cockroachdb/cockroach/pkg/acceptance/cluster/localcluster.go:264 +0x2bd
github.com/cockroachdb/cockroach/pkg/acceptance.testDocker(0x7f4af805d118, 0xc420018de8, 0xc420af9ad0, 0xc400000000, 0x1a528cb, 0x9, 0x0, 0x0, 0x0, 0x0, ...)
/go/src/github.com/cockroachdb/cockroach/pkg/acceptance/util.go:563 +0x399
github.com/cockroachdb/cockroach/pkg/acceptance.testDockerOneShot(0x7f4af805d118, 0xc420018de8, 0xc420af9ad0, 0x1a528cb, 0x9, 0x0, 0x0, 0x0, 0x0, 0x0, ...)
/go/src/github.com/cockroachdb/cockroach/pkg/acceptance/util.go:580 +0x9f
github.com/cockroachdb/cockroach/pkg/acceptance.runReferenceTestWithScript(0x7f4af805d118, 0xc420018de8, 0xc420af9ad0, 0xc42076c880, 0xceb)
/go/src/github.com/cockroachdb/cockroach/pkg/acceptance/reference_test.go:38 +0x2ca
github.com/cockroachdb/cockroach/pkg/acceptance.runReadWriteReferenceTest(0x7f4af805d118, 0xc420018de8, 0xc420af9ad0, 0x1a6ed50, 0x1f, 0x1ab5201, 0x2ad)
/go/src/github.com/cockroachdb/cockroach/pkg/acceptance/reference_test.go:97 +0x193
github.com/cockroachdb/cockroach/pkg/acceptance.TestDockerReadWriteBidirectionalReferenceVersion(0xc420af9ad0)
/go/src/github.com/cockroachdb/cockroach/pkg/acceptance/reference_test.go:125 +0xef
testing.tRunner(0xc420af9ad0, 0x1b105f8)
/usr/local/go/src/testing/testing.go:657 +0x96
created by testing.(*T).Run
/usr/local/go/src/testing/testing.go:697 +0x2ca
goroutine 19 [select, 10 minutes, locked to thread]:
runtime.gopark(0x1b137e8, 0x0, 0x1a4df60, 0x6, 0x18, 0x2)
/usr/local/go/src/runtime/proc.go:271 +0x13a
runtime.selectgoImpl(0xc4205e5f50, 0x0, 0x18)
/usr/local/go/src/runtime/select.go:423 +0x1364
runtime.selectgo(0xc4205e5f50)
/usr/local/go/src/runtime/select.go:238 +0x1c
runtime.ensureSigM.func1()
/usr/local/go/src/runtime/signal_unix.go:434 +0x2dd
runtime.goexit()
/usr/local/go/src/runtime/asm_amd64.s:2197 +0x1
goroutine 176 [chan receive, 9 minutes]:
database/sql.(*DB).connectionOpener(0xc420942000)
/usr/local/go/src/database/sql/sql.go:837 +0x4a
created by database/sql.Open
/usr/local/go/src/database/sql/sql.go:582 +0x212
goroutine 188 [chan receive, 9 minutes]:
github.com/cockroachdb/cockroach/pkg/rpc.NewContext.func1(0x7f4af7f29238, 0xc4207a1470)
/go/src/github.com/cockroachdb/cockroach/pkg/rpc/context.go:209 +0x5d
github.com/cockroachdb/cockroach/pkg/util/stop.(*Stopper).RunWorker.func1(0xc4203111c0, 0xc42001cea0, 0xc4203121e0)
/go/src/github.com/cockroachdb/cockroach/pkg/util/stop/stopper.go:193 +0xf7
created by github.com/cockroachdb/cockroach/pkg/util/stop.(*Stopper).RunWorker
/go/src/github.com/cockroachdb/cockroach/pkg/util/stop/stopper.go:194 +0xad
goroutine 138 [select, 9 minutes]:
net/http.(*persistConn).writeLoop(0xc4209a2240)
/usr/local/go/src/net/http/transport.go:1704 +0x43a
created by net/http.(*Transport).dialConn
/usr/local/go/src/net/http/transport.go:1118 +0xa5a
goroutine 85 [select]:
github.com/cockroachdb/cockroach/pkg/rpc.(*Context).runHeartbeat(0xc4207d6000, 0xc4204169c0, 0xc4201f4370, 0xf, 0x0, 0x0)
/go/src/github.com/cockroachdb/cockroach/pkg/rpc/context.go:412 +0x7ef
github.com/cockroachdb/cockroach/pkg/rpc.(*Context).GRPCDial.func1.2.1(0x7f4af7f29238, 0xc4201dc990)
/go/src/github.com/cockroachdb/cockroach/pkg/rpc/context.go:346 +0x6b
github.com/cockroachdb/cockroach/pkg/util/stop.(*Stopper).RunWorker.func1(0xc42021af90, 0xc42001cea0, 0xc4201dc810)
/go/src/github.com/cockroachdb/cockroach/pkg/util/stop/stopper.go:193 +0xf7
created by github.com/cockroachdb/cockroach/pkg/util/stop.(*Stopper).RunWorker
/go/src/github.com/cockroachdb/cockroach/pkg/util/stop/stopper.go:194 +0xad
goroutine 69 [chan receive, 9 minutes]:
github.com/cockroachdb/cockroach/pkg/rpc.NewContext.func1(0x7f4af7f29238, 0xc420413b00)
/go/src/github.com/cockroachdb/cockroach/pkg/rpc/context.go:209 +0x5d
github.com/cockroachdb/cockroach/pkg/util/stop.(*Stopper).RunWorker.func1(0xc420266700, 0xc42001cea0, 0xc420277a00)
/go/src/github.com/cockroachdb/cockroach/pkg/util/stop/stopper.go:193 +0xf7
created by github.com/cockroachdb/cockroach/pkg/util/stop.(*Stopper).RunWorker
/go/src/github.com/cockroachdb/cockroach/pkg/util/stop/stopper.go:194 +0xad
goroutine 116 [select]:
github.com/cockroachdb/cockroach/pkg/rpc.(*Context).runHeartbeat(0xc4208e8270, 0xc4207934c0, 0xc420270110, 0xf, 0x0, 0x0)
/go/src/github.com/cockroachdb/cockroach/pkg/rpc/context.go:412 +0x7ef
github.com/cockroachdb/cockroach/pkg/rpc.(*Context).GRPCDial.func1.2.1(0x7f4af7f29238, 0xc420822b40)
/go/src/github.com/cockroachdb/cockroach/pkg/rpc/context.go:346 +0x6b
github.com/cockroachdb/cockroach/pkg/util/stop.(*Stopper).RunWorker.func1(0xc42027d170, 0xc42001cea0, 0xc420822ab0)
/go/src/github.com/cockroachdb/cockroach/pkg/util/stop/stopper.go:193 +0xf7
created by github.com/cockroachdb/cockroach/pkg/util/stop.(*Stopper).RunWorker
/go/src/github.com/cockroachdb/cockroach/pkg/util/stop/stopper.go:194 +0xad
goroutine 435 [chan receive, 8 minutes]:
github.com/cockroachdb/cockroach/pkg/rpc.NewContext.func1(0x7f4af7f29238, 0xc42035b590)
/go/src/github.com/cockroachdb/cockroach/pkg/rpc/context.go:209 +0x5d
github.com/cockroachdb/cockroach/pkg/util/stop.(*Stopper).RunWorker.func1(0xc420311080, 0xc42001cea0, 0xc42025bb40)
/go/src/github.com/cockroachdb/cockroach/pkg/util/stop/stopper.go:193 +0xf7
created by github.com/cockroachdb/cockroach/pkg/util/stop.(*Stopper).RunWorker
/go/src/github.com/cockroachdb/cockroach/pkg/util/stop/stopper.go:194 +0xad
goroutine 137 [IO wait, 9 minutes]:
net.runtime_pollWait(0x7f4af805e928, 0x72, 0x9)
/usr/local/go/src/runtime/netpoll.go:164 +0x59
net.(*pollDesc).wait(0xc420464298, 0x72, 0x266c700, 0x2661ba8)
/usr/local/go/src/net/fd_poll_runtime.go:75 +0x38
net.(*pollDesc).waitRead(0xc420464298, 0xc42055a000, 0x1000)
/usr/local/go/src/net/fd_poll_runtime.go:80 +0x34
net.(*netFD).Read(0xc420464230, 0xc42055a000, 0x1000, 0x1000, 0x0, 0x266c700, 0x2661ba8)
/usr/local/go/src/net/fd_unix.go:250 +0x1b7
net.(*conn).Read(0xc42000e180, 0xc42055a000, 0x1000, 0x1000, 0x0, 0x0, 0x0)
/usr/local/go/src/net/net.go:181 +0x70
net/http.(*persistConn).Read(0xc4209a2240, 0xc42055a000, 0x1000, 0x1000, 0x4, 0xc4202531a0, 0x17)
/usr/local/go/src/net/http/transport.go:1316 +0x14b
bufio.(*Reader).fill(0xc420b48cc0)
/usr/local/go/src/bufio/bufio.go:97 +0x117
bufio.(*Reader).Peek(0xc420b48cc0, 0x1, 0x0, 0x1, 0x0, 0xc4204c8720, 0x0)
/usr/local/go/src/bufio/bufio.go:129 +0x67
net/http.(*persistConn).readLoop(0xc4209a2240)
/usr/local/go/src/net/http/transport.go:1474 +0x196
created by net/http.(*Transport).dialConn
/usr/local/go/src/net/http/transport.go:1117 +0xa35
goroutine 84 [select]:
github.com/cockroachdb/cockroach/vendor/google.golang.org/grpc.(*addrConn).resetTransport(0xc4200a3180, 0xc4202c0000, 0x0, 0x0)
/go/src/github.com/cockroachdb/cockroach/vendor/google.golang.org/grpc/clientconn.go:888 +0x8e5
github.com/cockroachdb/cockroach/vendor/google.golang.org/grpc.(*addrConn).transportMonitor(0xc4200a3180)
/go/src/github.com/cockroachdb/cockroach/vendor/google.golang.org/grpc/clientconn.go:972 +0x362
github.com/cockroachdb/cockroach/vendor/google.golang.org/grpc.(*ClientConn).resetAddrConn.func1(0xc4200a3180)
/go/src/github.com/cockroachdb/cockroach/vendor/google.golang.org/grpc/clientconn.go:642 +0x1d9
created by github.com/cockroachdb/cockroach/vendor/google.golang.org/grpc.(*ClientConn).resetAddrConn
/go/src/github.com/cockroachdb/cockroach/vendor/google.golang.org/grpc/clientconn.go:643 +0x786
goroutine 23 [chan receive, 9 minutes]:
github.com/cockroachdb/cockroach/pkg/rpc.NewContext.func1(0x7f4af7f29238, 0xc42038f440)
/go/src/github.com/cockroachdb/cockroach/pkg/rpc/context.go:209 +0x5d
github.com/cockroachdb/cockroach/pkg/util/stop.(*Stopper).RunWorker.func1(0xc420018490, 0xc42001cea0, 0xc4200fb560)
/go/src/github.com/cockroachdb/cockroach/pkg/util/stop/stopper.go:193 +0xf7
created by github.com/cockroachdb/cockroach/pkg/util/stop.(*Stopper).RunWorker
/go/src/github.com/cockroachdb/cockroach/pkg/util/stop/stopper.go:194 +0xad
goroutine 5386 [select]:
github.com/cockroachdb/cockroach/pkg/rpc.(*Context).runHeartbeat(0xc420af8a90, 0xc420ad0540, 0xc420369480, 0xf, 0x0, 0x0)
/go/src/github.com/cockroachdb/cockroach/pkg/rpc/context.go:412 +0x7ef
github.com/cockroachdb/cockroach/pkg/rpc.(*Context).GRPCDial.func1.2.1(0x7f4af7f29238, 0xc4201c6f00)
/go/src/github.com/cockroachdb/cockroach/pkg/rpc/context.go:346 +0x6b
github.com/cockroachdb/cockroach/pkg/util/stop.(*Stopper).RunWorker.func1(0xc42031e7e0, 0xc42001cea0, 0xc4201c6e70)
/go/src/github.com/cockroachdb/cockroach/pkg/util/stop/stopper.go:193 +0xf7
created by github.com/cockroachdb/cockroach/pkg/util/stop.(*Stopper).RunWorker
/go/src/github.com/cockroachdb/cockroach/pkg/util/stop/stopper.go:194 +0xad
goroutine 49 [IO wait, 9 minutes]:
net.runtime_pollWait(0x7f4af805f168, 0x72, 0x8)
/usr/local/go/src/runtime/netpoll.go:164 +0x59
net.(*pollDesc).wait(0xc4201b9568, 0x72, 0x266c700, 0x2661ba8)
/usr/local/go/src/net/fd_poll_runtime.go:75 +0x38
net.(*pollDesc).waitRead(0xc4201b9568, 0xc4206bc000, 0x1000)
/usr/local/go/src/net/fd_poll_runtime.go:80 +0x34
net.(*netFD).Read(0xc4201b9500, 0xc4206bc000, 0x1000, 0x1000, 0x0, 0x266c700, 0x2661ba8)
/usr/local/go/src/net/fd_unix.go:250 +0x1b7
net.(*conn).Read(0xc420474128, 0xc4206bc000, 0x1000, 0x1000, 0x0, 0x0, 0x0)
/usr/local/go/src/net/net.go:181 +0x70
net/http.(*persistConn).Read(0xc4202a9b00, 0xc4206bc000, 0x1000, 0x1000, 0x4, 0xc42025bbe0, 0x17)
/usr/local/go/src/net/http/transport.go:1316 +0x14b
bufio.(*Reader).fill(0xc4208bf380)
/usr/local/go/src/bufio/bufio.go:97 +0x117
bufio.(*Reader).Peek(0xc4208bf380, 0x1, 0x0, 0x1, 0x0, 0xc4208feb40, 0x0)
/usr/local/go/src/bufio/bufio.go:129 +0x67
net/http.(*persistConn).readLoop(0xc4202a9b00)
/usr/local/go/src/net/http/transport.go:1474 +0x196
created by net/http.(*Transport).dialConn
/usr/local/go/src/net/http/transport.go:1117 +0xa35
goroutine 82 [select, 9 minutes]:
net/http.(*persistConn).writeLoop(0xc4202a9b00)
/usr/local/go/src/net/http/transport.go:1704 +0x43a
created by net/http.(*Transport).dialConn
/usr/local/go/src/net/http/transport.go:1118 +0xa5a
goroutine 102 [select]:
github.com/cockroachdb/cockroach/vendor/google.golang.org/grpc.(*addrConn).resetTransport(0xc42040e540, 0xc4207c8300, 0x0, 0x0)
/go/src/github.com/cockroachdb/cockroach/vendor/google.golang.org/grpc/clientconn.go:888 +0x8e5
github.com/cockroachdb/cockroach/vendor/google.golang.org/grpc.(*addrConn).transportMonitor(0xc42040e540)
/go/src/github.com/cockroachdb/cockroach/vendor/google.golang.org/grpc/clientconn.go:972 +0x362
github.com/cockroachdb/cockroach/vendor/google.golang.org/grpc.(*ClientConn).resetAddrConn.func1(0xc42040e540)
/go/src/github.com/cockroachdb/cockroach/vendor/google.golang.org/grpc/clientconn.go:642 +0x1d9
created by github.com/cockroachdb/cockroach/vendor/google.golang.org/grpc.(*ClientConn).resetAddrConn
/go/src/github.com/cockroachdb/cockroach/vendor/google.golang.org/grpc/clientconn.go:643 +0x786
goroutine 103 [select]:
github.com/cockroachdb/cockroach/pkg/rpc.(*Context).runHeartbeat(0xc4207d6340, 0xc420422480, 0xc4202703f0, 0xf, 0x0, 0x0)
/go/src/github.com/cockroachdb/cockroach/pkg/rpc/context.go:412 +0x7ef
github.com/cockroachdb/cockroach/pkg/rpc.(*Context).GRPCDial.func1.2.1(0x7f4af7f29238, 0xc4202b8ff0)
/go/src/github.com/cockroachdb/cockroach/pkg/rpc/context.go:346 +0x6b
github.com/cockroachdb/cockroach/pkg/util/stop.(*Stopper).RunWorker.func1(0xc42027c160, 0xc42001cea0, 0xc4202b8e10)
/go/src/github.com/cockroachdb/cockroach/pkg/util/stop/stopper.go:193 +0xf7
created by github.com/cockroachdb/cockroach/pkg/util/stop.(*Stopper).RunWorker
/go/src/github.com/cockroachdb/cockroach/pkg/util/stop/stopper.go:194 +0xad
goroutine 67 [IO wait, 9 minutes]:
net.runtime_pollWait(0x7f4af805efe8, 0x72, 0xa)
/usr/local/go/src/runtime/netpoll.go:164 +0x59
net.(*pollDesc).wait(0xc420562308, 0x72, 0x266c700, 0x2661ba8)
/usr/local/go/src/net/fd_poll_runtime.go:75 +0x38
net.(*pollDesc).waitRead(0xc420562308, 0xc42069c000, 0x1000)
/usr/local/go/src/net/fd_poll_runtime.go:80 +0x34
net.(*netFD).Read(0xc4205622a0, 0xc42069c000, 0x1000, 0x1000, 0x0, 0x266c700, 0x2661ba8)
/usr/local/go/src/net/fd_unix.go:250 +0x1b7
net.(*conn).Read(0xc420778028, 0xc42069c000, 0x1000, 0x1000, 0x0, 0x0, 0x0)
/usr/local/go/src/net/net.go:181 +0x70
net/http.(*persistConn).Read(0xc420772240, 0xc42069c000, 0x1000, 0x1000, 0x4, 0x602890, 0xc4208fe6c0)
/usr/local/go/src/net/http/transport.go:1316 +0x14b
bufio.(*Reader).fill(0xc4208fe540)
/usr/local/go/src/bufio/bufio.go:97 +0x117
bufio.(*Reader).Peek(0xc4208fe540, 0x1, 0xc4208d2be5, 0x1, 0x0, 0xc4208fe8a0, 0x0)
/usr/local/go/src/bufio/bufio.go:129 +0x67
net/http.(*persistConn).readLoop(0xc420772240)
/usr/local/go/src/net/http/transport.go:1474 +0x196
created by net/http.(*Transport).dialConn
/usr/local/go/src/net/http/transport.go:1117 +0xa35
goroutine 68 [select, 9 minutes]:
net/http.(*persistConn).writeLoop(0xc420772240)
/usr/local/go/src/net/http/transport.go:1704 +0x43a
created by net/http.(*Transport).dialConn
/usr/local/go/src/net/http/transport.go:1118 +0xa5a
goroutine 708 [select, 8 minutes]:
net/http.(*persistConn).writeLoop(0xc4209a2120)
/usr/local/go/src/net/http/transport.go:1704 +0x43a
created by net/http.(*Transport).dialConn
/usr/local/go/src/net/http/transport.go:1118 +0xa5a
goroutine 437 [select]:
github.com/cockroachdb/cockroach/vendor/google.golang.org/grpc.(*addrConn).resetTransport(0xc420242c40, 0xc4207ac400, 0x0, 0x0)
/go/src/github.com/cockroachdb/cockroach/vendor/google.golang.org/grpc/clientconn.go:888 +0x8e5
github.com/cockroachdb/cockroach/vendor/google.golang.org/grpc.(*addrConn).transportMonitor(0xc420242c40)
/go/src/github.com/cockroachdb/cockroach/vendor/google.golang.org/grpc/clientconn.go:972 +0x362
github.com/cockroachdb/cockroach/vendor/google.golang.org/grpc.(*ClientConn).resetAddrConn.func1(0xc420242c40)
/go/src/github.com/cockroachdb/cockroach/vendor/google.golang.org/grpc/clientconn.go:642 +0x1d9
created by github.com/cockroachdb/cockroach/vendor/google.golang.org/grpc.(*ClientConn).resetAddrConn
/go/src/github.com/cockroachdb/cockroach/vendor/google.golang.org/grpc/clientconn.go:643 +0x786
goroutine 707 [IO wait, 8 minutes]:
net.runtime_pollWait(0x7f4af805eaa8, 0x72, 0x15)
/usr/local/go/src/runtime/netpoll.go:164 +0x59
net.(*pollDesc).wait(0xc4204faa08, 0x72, 0x266c700, 0x2661ba8)
/usr/local/go/src/net/fd_poll_runtime.go:75 +0x38
net.(*pollDesc).waitRead(0xc4204faa08, 0xc420ac9000, 0x1000)
/usr/local/go/src/net/fd_poll_runtime.go:80 +0x34
net.(*netFD).Read(0xc4204fa9a0, 0xc420ac9000, 0x1000, 0x1000, 0x0, 0x266c700, 0x2661ba8)
/usr/local/go/src/net/fd_unix.go:250 +0x1b7
net.(*conn).Read(0xc42000e1f0, 0xc420ac9000, 0x1000, 0x1000, 0x0, 0x0, 0x0)
/usr/local/go/src/net/net.go:181 +0x70
net/http.(*persistConn).Read(0xc4209a2120, 0xc420ac9000, 0x1000, 0x1000, 0x4, 0xc4202974e0, 0x17)
/usr/local/go/src/net/http/transport.go:1316 +0x14b
bufio.(*Reader).fill(0xc420b5fce0)
/usr/local/go/src/bufio/bufio.go:97 +0x117
bufio.(*Reader).Peek(0xc420b5fce0, 0x1, 0x0, 0x1, 0x0, 0xc4207e0660, 0x0)
/usr/local/go/src/bufio/bufio.go:129 +0x67
net/http.(*persistConn).readLoop(0xc4209a2120)
/usr/local/go/src/net/http/transport.go:1474 +0x196
created by net/http.(*Transport).dialConn
/usr/local/go/src/net/http/transport.go:1117 +0xa35
goroutine 115 [select]:
github.com/cockroachdb/cockroach/vendor/google.golang.org/grpc.(*addrConn).resetTransport(0xc4208148c0, 0xc420900e00, 0x0, 0x0)
/go/src/github.com/cockroachdb/cockroach/vendor/google.golang.org/grpc/clientconn.go:888 +0x8e5
github.com/cockroachdb/cockroach/vendor/google.golang.org/grpc.(*addrConn).transportMonitor(0xc4208148c0)
/go/src/github.com/cockroachdb/cockroach/vendor/google.golang.org/grpc/clientconn.go:972 +0x362
github.com/cockroachdb/cockroach/vendor/google.golang.org/grpc.(*ClientConn).resetAddrConn.func1(0xc4208148c0)
/go/src/github.com/cockroachdb/cockroach/vendor/google.golang.org/grpc/clientconn.go:642 +0x1d9
created by github.com/cockroachdb/cockroach/vendor/google.golang.org/grpc.(*ClientConn).resetAddrConn
/go/src/github.com/cockroachdb/cockroach/vendor/google.golang.org/grpc/clientconn.go:643 +0x786
goroutine 644 [chan receive, 8 minutes]:
database/sql.(*DB).connectionOpener(0xc420b10dc0)
/usr/local/go/src/database/sql/sql.go:837 +0x4a
created by database/sql.Open
/usr/local/go/src/database/sql/sql.go:582 +0x212
goroutine 2131 [select, 5 minutes]:
net/http.(*persistConn).writeLoop(0xc4206606c0)
/usr/local/go/src/net/http/transport.go:1704 +0x43a
created by net/http.(*Transport).dialConn
/usr/local/go/src/net/http/transport.go:1118 +0xa5a
goroutine 596 [IO wait, 8 minutes]:
net.runtime_pollWait(0x7f4af805ef28, 0x72, 0x13)
/usr/local/go/src/runtime/netpoll.go:164 +0x59
net.(*pollDesc).wait(0xc420419a38, 0x72, 0x266c700, 0x2661ba8)
/usr/local/go/src/net/fd_poll_runtime.go:75 +0x38
net.(*pollDesc).waitRead(0xc420419a38, 0xc4204fd000, 0x1000)
/usr/local/go/src/net/fd_poll_runtime.go:80 +0x34
net.(*netFD).Read(0xc4204199d0, 0xc4204fd000, 0x1000, 0x1000, 0x0, 0x266c700, 0x2661ba8)
/usr/local/go/src/net/fd_unix.go:250 +0x1b7
net.(*conn).Read(0xc420778178, 0xc4204fd000, 0x1000, 0x1000, 0x0, 0x0, 0x0)
/usr/local/go/src/net/net.go:181 +0x70
net/http.(*persistConn).Read(0xc4202a8d80, 0xc4204fd000, 0x1000, 0x1000, 0x4, 0xc4202769c0, 0x17)
/usr/local/go/src/net/http/transport.go:1316 +0x14b
bufio.(*Reader).fill(0xc42073d980)
/usr/local/go/src/bufio/bufio.go:97 +0x117
bufio.(*Reader).Peek(0xc42073d980, 0x1, 0x0, 0x1, 0x0, 0xc4209b5c80, 0x0)
/usr/local/go/src/bufio/bufio.go:129 +0x67
net/http.(*persistConn).readLoop(0xc4202a8d80)
/usr/local/go/src/net/http/transport.go:1474 +0x196
created by net/http.(*Transport).dialConn
/usr/local/go/src/net/http/transport.go:1117 +0xa35
goroutine 27 [chan receive, 9 minutes]:
github.com/cockroachdb/cockroach/pkg/rpc.NewContext.func1(0x7f4af7f29238, 0xc420262060)
/go/src/github.com/cockroachdb/cockroach/pkg/rpc/context.go:209 +0x5d
github.com/cockroachdb/cockroach/pkg/util/stop.(*Stopper).RunWorker.func1(0xc420259a50, 0xc42001cea0, 0xc42025bae0)
/go/src/github.com/cockroachdb/cockroach/pkg/util/stop/stopper.go:193 +0xf7
created by github.com/cockroachdb/cockroach/pkg/util/stop.(*Stopper).RunWorker
/go/src/github.com/cockroachdb/cockroach/pkg/util/stop/stopper.go:194 +0xad
goroutine 4565 [chan receive, 2 minutes]:
github.com/cockroachdb/cockroach/pkg/rpc.NewContext.func1(0x7f4af7f29238, 0xc420986e40)
/go/src/github.com/cockroachdb/cockroach/pkg/rpc/context.go:209 +0x5d
github.com/cockroachdb/cockroach/pkg/util/stop.(*Stopper).RunWorker.func1(0xc42033fad0, 0xc42001cea0, 0xc42035d8a0)
/go/src/github.com/cockroachdb/cockroach/pkg/util/stop/stopper.go:193 +0xf7
created by github.com/cockroachdb/cockroach/pkg/util/stop.(*Stopper).RunWorker
/go/src/github.com/cockroachdb/cockroach/pkg/util/stop/stopper.go:194 +0xad
goroutine 31 [chan receive, 9 minutes]:
database/sql.(*DB).connectionOpener(0xc420398dc0)
/usr/local/go/src/database/sql/sql.go:837 +0x4a
created by database/sql.Open
/usr/local/go/src/database/sql/sql.go:582 +0x212
goroutine 32 [chan receive, 9 minutes]:
database/sql.(*DB).connectionOpener(0xc4203f6a00)
/usr/local/go/src/database/sql/sql.go:837 +0x4a
created by database/sql.Open
/usr/local/go/src/database/sql/sql.go:582 +0x212
goroutine 88 [chan receive, 9 minutes]:
database/sql.(*DB).connectionOpener(0xc4201a8d20)
/usr/local/go/src/database/sql/sql.go:837 +0x4a
created by database/sql.Open
/usr/local/go/src/database/sql/sql.go:582 +0x212
goroutine 33 [chan receive, 9 minutes]:
database/sql.(*DB).connectionOpener(0xc4203f74a0)
/usr/local/go/src/database/sql/sql.go:837 +0x4a
created by database/sql.Open
/usr/local/go/src/database/sql/sql.go:582 +0x212
goroutine 438 [select]:
github.com/cockroachdb/cockroach/pkg/rpc.(*Context).runHeartbeat(0xc4207d6750, 0xc42079f380, 0xc420311500, 0xf, 0x0, 0x0)
/go/src/github.com/cockroachdb/cockroach/pkg/rpc/context.go:412 +0x7ef
github.com/cockroachdb/cockroach/pkg/rpc.(*Context).GRPCDial.func1.2.1(0x7f4af7f29238, 0xc4201dd2c0)
/go/src/github.com/cockroachdb/cockroach/pkg/rpc/context.go:346 +0x6b
github.com/cockroachdb/cockroach/pkg/util/stop.(*Stopper).RunWorker.func1(0xc4201d6a50, 0xc42001cea0, 0xc4201dd1a0)
/go/src/github.com/cockroachdb/cockroach/pkg/util/stop/stopper.go:193 +0xf7
created by github.com/cockroachdb/cockroach/pkg/util/stop.(*Stopper).RunWorker
/go/src/github.com/cockroachdb/cockroach/pkg/util/stop/stopper.go:194 +0xad
goroutine 1310 [select, 6 minutes]:
net/http.(*persistConn).writeLoop(0xc420772360)
/usr/local/go/src/net/http/transport.go:1704 +0x43a
created by net/http.(*Transport).dialConn
/usr/local/go/src/net/http/transport.go:1118 +0xa5a
goroutine 2181 [IO wait, 5 minutes]:
net.runtime_pollWait(0x7f4af80621f8, 0x72, 0x27)
/usr/local/go/src/runtime/netpoll.go:164 +0x59
net.(*pollDesc).wait(0xc4200a6d88, 0x72, 0x266c700, 0x2661ba8)
/usr/local/go/src/net/fd_poll_runtime.go:75 +0x38
net.(*pollDesc).waitRead(0xc4200a6d88, 0xc42073a000, 0x1000)
/usr/local/go/src/net/fd_poll_runtime.go:80 +0x34
net.(*netFD).Read(0xc4200a6d20, 0xc42073a000, 0x1000, 0x1000, 0x0, 0x266c700, 0x2661ba8)
/usr/local/go/src/net/fd_unix.go:250 +0x1b7
net.(*conn).Read(0xc4207c4108, 0xc42073a000, 0x1000, 0x1000, 0x0, 0x0, 0x0)
/usr/local/go/src/net/net.go:181 +0x70
net/http.(*persistConn).Read(0xc420660a20, 0xc42073a000, 0x1000, 0x1000, 0x4, 0xc4202c91a0, 0x17)
/usr/local/go/src/net/http/transport.go:1316 +0x14b
bufio.(*Reader).fill(0xc4208b5860)
/usr/local/go/src/bufio/bufio.go:97 +0x117
bufio.(*Reader).Peek(0xc4208b5860, 0x1, 0x0, 0x1, 0x0, 0xc4208aaa80, 0x0)
/usr/local/go/src/bufio/bufio.go:129 +0x67
net/http.(*persistConn).readLoop(0xc420660a20)
/usr/local/go/src/net/http/transport.go:1474 +0x196
created by net/http.(*Transport).dialConn
/usr/local/go/src/net/http/transport.go:1117 +0xa35
goroutine 1570 [select, 6 minutes]:
net/http.(*persistConn).writeLoop(0xc4200c3b00)
/usr/local/go/src/net/http/transport.go:1704 +0x43a
created by net/http.(*Transport).dialConn
/usr/local/go/src/net/http/transport.go:1118 +0xa5a
goroutine 6616 [select]:
github.com/cockroachdb/cockroach/pkg/rpc.(*Context).runHeartbeat(0xc420281ad0, 0xc421336ec0, 0xc420018590, 0xf, 0x0, 0x0)
/go/src/github.com/cockroachdb/cockroach/pkg/rpc/context.go:412 +0x7ef
github.com/cockroachdb/cockroach/pkg/rpc.(*Context).GRPCDial.func1.2.1(0x7f4af7f29238, 0xc421195c50)
/go/src/github.com/cockroachdb/cockroach/pkg/rpc/context.go:346 +0x6b
github.com/cockroachdb/cockroach/pkg/util/stop.(*Stopper).RunWorker.func1(0xc4203114b0, 0xc42001cea0, 0xc421195bc0)
/go/src/github.com/cockroachdb/cockroach/pkg/util/stop/stopper.go:193 +0xf7
created by github.com/cockroachdb/cockroach/pkg/util/stop.(*Stopper).RunWorker
/go/src/github.com/cockroachdb/cockroach/pkg/util/stop/stopper.go:194 +0xad
goroutine 668 [select, 8 minutes]:
net/http.(*persistConn).writeLoop(0xc42042f7a0)
/usr/local/go/src/net/http/transport.go:1704 +0x43a
created by net/http.(*Transport).dialConn
/usr/local/go/src/net/http/transport.go:1118 +0xa5a
goroutine 787 [IO wait, 8 minutes]:
net.runtime_pollWait(0x7f4af805e628, 0x72, 0x17)
/usr/local/go/src/runtime/netpoll.go:164 +0x59
net.(*pollDesc).wait(0xc4201b84c8, 0x72, 0x266c700, 0x2661ba8)
/usr/local/go/src/net/fd_poll_runtime.go:75 +0x38
net.(*pollDesc).waitRead(0xc4201b84c8, 0xc4209f8000, 0x1000)
/usr/local/go/src/net/fd_poll_runtime.go:80 +0x34
net.(*netFD).Read(0xc4201b8460, 0xc4209f8000, 0x1000, 0x1000, 0x0, 0x266c700, 0x2661ba8)
/usr/local/go/src/net/fd_unix.go:250 +0x1b7
net.(*conn).Read(0xc4207c4110, 0xc4209f8000, 0x1000, 0x1000, 0x0, 0x0, 0x0)
/usr/local/go/src/net/net.go:181 +0x70
net/http.(*persistConn).Read(0xc420660360, 0xc4209f8000, 0x1000, 0x1000, 0x4, 0xc4202a2140, 0x17)
/usr/local/go/src/net/http/transport.go:1316 +0x14b
bufio.(*Reader).fill(0xc4209fb4a0)
/usr/local/go/src/bufio/bufio.go:97 +0x117
bufio.(*Reader).Peek(0xc4209fb4a0, 0x1, 0x0, 0x1, 0x0, 0xc420bda420, 0x0)
/usr/local/go/src/bufio/bufio.go:129 +0x67
net/http.(*persistConn).readLoop(0xc420660360)
/usr/local/go/src/net/http/transport.go:1474 +0x196
created by net/http.(*Transport).dialConn
/usr/local/go/src/net/http/transport.go:1117 +0xa35
goroutine 197 [select]:
github.com/cockroachdb/cockroach/pkg/rpc.(*Context).runHeartbeat(0xc420281450, 0xc420b45b40, 0xc4202d5d90, 0xf, 0x0, 0x0)
/go/src/github.com/cockroachdb/cockroach/pkg/rpc/context.go:412 +0x7ef
github.com/cockroachdb/cockroach/pkg/rpc.(*Context).GRPCDial.func1.2.1(0x7f4af7f29238, 0xc420288180)
/go/src/github.com/cockroachdb/cockroach/pkg/rpc/context.go:346 +0x6b
github.com/cockroachdb/cockroach/pkg/util/stop.(*Stopper).RunWorker.func1(0xc4202b4d60, 0xc42001cea0, 0xc4202880c0)
/go/src/github.com/cockroachdb/cockroach/pkg/util/stop/stopper.go:193 +0xf7
created by github.com/cockroachdb/cockroach/pkg/util/stop.(*Stopper).RunWorker
/go/src/github.com/cockroachdb/cockroach/pkg/util/stop/stopper.go:194 +0xad
goroutine 196 [select]:
github.com/cockroachdb/cockroach/vendor/google.golang.org/grpc.(*addrConn).resetTransport(0xc420815500, 0xc42091e500, 0x0, 0x0)
/go/src/github.com/cockroachdb/cockroach/vendor/google.golang.org/grpc/clientconn.go:888 +0x8e5
github.com/cockroachdb/cockroach/vendor/google.golang.org/grpc.(*addrConn).transportMonitor(0xc420815500)
/go/src/github.com/cockroachdb/cockroach/vendor/google.golang.org/grpc/clientconn.go:972 +0x362
github.com/cockroachdb/cockroach/vendor/google.golang.org/grpc.(*ClientConn).resetAddrConn.func1(0xc420815500)
/go/src/github.com/cockroachdb/cockroach/vendor/google.golang.org/grpc/clientconn.go:642 +0x1d9
created by github.com/cockroachdb/cockroach/vendor/google.golang.org/grpc.(*ClientConn).resetAddrConn
/go/src/github.com/cockroachdb/cockroach/vendor/google.golang.org/grpc/clientconn.go:643 +0x786
goroutine 516 [select, 8 minutes]:
net/http.(*persistConn).writeLoop(0xc4209d66c0)
/usr/local/go/src/net/http/transport.go:1704 +0x43a
created by net/http.(*Transport).dialConn
/usr/local/go/src/net/http/transport.go:1118 +0xa5a
goroutine 515 [IO wait, 8 minutes]:
net.runtime_pollWait(0x7f4af805e9e8, 0x72, 0x11)
/usr/local/go/src/runtime/netpoll.go:164 +0x59
net.(*pollDesc).wait(0xc4205c1178, 0x72, 0x266c700, 0x2661ba8)
/usr/local/go/src/net/fd_poll_runtime.go:75 +0x38
net.(*pollDesc).waitRead(0xc4205c1178, 0xc42049c000, 0x1000)
/usr/local/go/src/net/fd_poll_runtime.go:80 +0x34
net.(*netFD).Read(0xc4205c1110, 0xc42049c000, 0x1000, 0x1000, 0x0, 0x266c700, 0x2661ba8)
/usr/local/go/src/net/fd_unix.go:250 +0x1b7
net.(*conn).Read(0xc4207c41b0, 0xc42049c000, 0x1000, 0x1000, 0x0, 0x0, 0x0)
/usr/local/go/src/net/net.go:181 +0x70
net/http.(*persistConn).Read(0xc4209d66c0, 0xc42049c000, 0x1000, 0x1000, 0x4, 0xc42027f4c0, 0x17)
/usr/local/go/src/net/http/transport.go:1316 +0x14b
bufio.(*Reader).fill(0xc42085ccc0)
/usr/local/go/src/bufio/bufio.go:97 +0x117
bufio.(*Reader).Peek(0xc42085ccc0, 0x1, 0x0, 0x1, 0x0, 0xc420ab5500, 0x0)
/usr/local/go/src/bufio/bufio.go:129 +0x67
net/http.(*persistConn).readLoop(0xc4209d66c0)
/usr/local/go/src/net/http/transport.go:1474 +0x196
created by net/http.(*Transport).dialConn
/usr/local/go/src/net/http/transport.go:1117 +0xa35
goroutine 5487 [chan receive, 2 minutes]:
database/sql.(*DB).connectionOpener(0xc420b4a1e0)
/usr/local/go/src/database/sql/sql.go:837 +0x4a
created by database/sql.Open
/usr/local/go/src/database/sql/sql.go:582 +0x212
goroutine 397 [select, 8 minutes]:
net/http.(*persistConn).writeLoop(0xc420772a20)
/usr/local/go/src/net/http/transport.go:1704 +0x43a
created by net/http.(*Transport).dialConn
/usr/local/go/src/net/http/transport.go:1118 +0xa5a
goroutine 396 [IO wait, 8 minutes]:
net.runtime_pollWait(0x7f4af805e868, 0x72, 0xb)
/usr/local/go/src/runtime/netpoll.go:164 +0x59
net.(*pollDesc).wait(0xc42019c228, 0x72, 0x266c700, 0x2661ba8)
/usr/local/go/src/net/fd_poll_runtime.go:75 +0x38
net.(*pollDesc).waitRead(0xc42019c228, 0xc4201c3000, 0x1000)
/usr/local/go/src/net/fd_poll_runtime.go:80 +0x34
net.(*netFD).Read(0xc42019c1c0, 0xc4201c3000, 0x1000, 0x1000, 0x0, 0x266c700, 0x2661ba8)
/usr/local/go/src/net/fd_unix.go:250 +0x1b7
net.(*conn).Read(0xc420474050, 0xc4201c3000, 0x1000, 0x1000, 0x0, 0x0, 0x0)
/usr/local/go/src/net/net.go:181 +0x70
net/http.(*persistConn).Read(0xc420772a20, 0xc4201c3000, 0x1000, 0x1000, 0x4, 0xc42020d0e0, 0x17)
/usr/local/go/src/net/http/transport.go:1316 +0x14b
bufio.(*Reader).fill(0xc420b56000)
/usr/local/go/src/bufio/bufio.go:97 +0x117
bufio.(*Reader).Peek(0xc420b56000, 0x1, 0x0, 0x1, 0x0, 0xc4202cfda0, 0x0)
/usr/local/go/src/bufio/bufio.go:129 +0x67
net/http.(*persistConn).readLoop(0xc420772a20)
/usr/local/go/src/net/http/transport.go:1474 +0x196
created by net/http.(*Transport).dialConn
/usr/local/go/src/net/http/transport.go:1117 +0xa35
goroutine 1097 [IO wait, 7 minutes]:
net.runtime_pollWait(0x7f4af805e328, 0x72, 0x1b)
/usr/local/go/src/runtime/netpoll.go:164 +0x59
net.(*pollDesc).wait(0xc420b04a78, 0x72, 0x266c700, 0x2661ba8)
/usr/local/go/src/net/fd_poll_runtime.go:75 +0x38
net.(*pollDesc).waitRead(0xc420b04a78, 0xc4208a0000, 0x1000)
/usr/local/go/src/net/fd_poll_runtime.go:80 +0x34
net.(*netFD).Read(0xc420b04a10, 0xc4208a0000, 0x1000, 0x1000, 0x0, 0x266c700, 0x2661ba8)
/usr/local/go/src/net/fd_unix.go:250 +0x1b7
net.(*conn).Read(0xc420778148, 0xc4208a0000, 0x1000, 0x1000, 0x0, 0x0, 0x0)
/usr/local/go/src/net/net.go:181 +0x70
net/http.(*persistConn).Read(0xc4202a8360, 0xc4208a0000, 0x1000, 0x1000, 0x4, 0xc4202f40e0, 0x17)
/usr/local/go/src/net/http/transport.go:1316 +0x14b
bufio.(*Reader).fill(0xc420c7f380)
/usr/local/go/src/bufio/bufio.go:97 +0x117
bufio.(*Reader).Peek(0xc420c7f380, 0x1, 0x0, 0x1, 0x0, 0xc420530f00, 0x0)
/usr/local/go/src/bufio/bufio.go:129 +0x67
net/http.(*persistConn).readLoop(0xc4202a8360)
/usr/local/go/src/net/http/transport.go:1474 +0x196
created by net/http.(*Transport).dialConn
/usr/local/go/src/net/http/transport.go:1117 +0xa35
goroutine 512 [chan receive, 8 minutes]:
database/sql.(*DB).connectionOpener(0xc4207f2320)
/usr/local/go/src/database/sql/sql.go:837 +0x4a
created by database/sql.Open
/usr/local/go/src/database/sql/sql.go:582 +0x212
goroutine 631 [select]:
github.com/cockroachdb/cockroach/vendor/google.golang.org/grpc.(*addrConn).resetTransport(0xc420242fc0, 0xc420b18800, 0x0, 0x0)
/go/src/github.com/cockroachdb/cockroach/vendor/google.golang.org/grpc/clientconn.go:888 +0x8e5
github.com/cockroachdb/cockroach/vendor/google.golang.org/grpc.(*addrConn).transportMonitor(0xc420242fc0)
/go/src/github.com/cockroachdb/cockroach/vendor/google.golang.org/grpc/clientconn.go:972 +0x362
github.com/cockroachdb/cockroach/vendor/google.golang.org/grpc.(*ClientConn).resetAddrConn.func1(0xc420242fc0)
/go/src/github.com/cockroachdb/cockroach/vendor/google.golang.org/grpc/clientconn.go:642 +0x1d9
created by github.com/cockroachdb/cockroach/vendor/google.golang.org/grpc.(*ClientConn).resetAddrConn
/go/src/github.com/cockroachdb/cockroach/vendor/google.golang.org/grpc/clientconn.go:643 +0x786
goroutine 441 [chan receive, 8 minutes]:
database/sql.(*DB).connectionOpener(0xc420579180)
/usr/local/go/src/database/sql/sql.go:837 +0x4a
created by database/sql.Open
/usr/local/go/src/database/sql/sql.go:582 +0x212
goroutine 2130 [IO wait, 5 minutes]:
net.runtime_pollWait(0x7f4af80622b8, 0x72, 0x26)
/usr/local/go/src/runtime/netpoll.go:164 +0x59
net.(*pollDesc).wait(0xc4204fa8b8, 0x72, 0x266c700, 0x2661ba8)
/usr/local/go/src/net/fd_poll_runtime.go:75 +0x38
net.(*pollDesc).waitRead(0xc4204fa8b8, 0xc420c81000, 0x1000)
/usr/local/go/src/net/fd_poll_runtime.go:80 +0x34
net.(*netFD).Read(0xc4204fa850, 0xc420c81000, 0x1000, 0x1000, 0x0, 0x266c700, 0x2661ba8)
/usr/local/go/src/net/fd_unix.go:250 +0x1b7
net.(*conn).Read(0xc4207c41c0, 0xc420c81000, 0x1000, 0x1000, 0x0, 0x0, 0x0)
/usr/local/go/src/net/net.go:181 +0x70
net/http.(*persistConn).Read(0xc4206606c0, 0xc420c81000, 0x1000, 0x1000, 0x4, 0xc4202a3380, 0x17)
/usr/local/go/src/net/http/transport.go:1316 +0x14b
bufio.(*Reader).fill(0xc420729560)
/usr/local/go/src/bufio/bufio.go:97 +0x117
bufio.(*Reader).Peek(0xc420729560, 0x1, 0x0, 0x1, 0x0, 0xc4208ba780, 0x0)
/usr/local/go/src/bufio/bufio.go:129 +0x67
net/http.(*persistConn).readLoop(0xc4206606c0)
/usr/local/go/src/net/http/transport.go:1474 +0x196
created by net/http.(*Transport).dialConn
/usr/local/go/src/net/http/transport.go:1117 +0xa35
goroutine 1098 [select, 7 minutes]:
net/http.(*persistConn).writeLoop(0xc4202a8360)
/usr/local/go/src/net/http/transport.go:1704 +0x43a
created by net/http.(*Transport).dialConn
/usr/local/go/src/net/http/transport.go:1118 +0xa5a
goroutine 597 [select, 8 minutes]:
net/http.(*persistConn).writeLoop(0xc4202a8d80)
/usr/local/go/src/net/http/transport.go:1704 +0x43a
created by net/http.(*Transport).dialConn
/usr/local/go/src/net/http/transport.go:1118 +0xa5a
goroutine 2680 [chan receive, 4 minutes]:
database/sql.(*DB).connectionOpener(0xc4202726e0)
/usr/local/go/src/database/sql/sql.go:837 +0x4a
created by database/sql.Open
/usr/local/go/src/database/sql/sql.go:582 +0x212
goroutine 632 [select]:
github.com/cockroachdb/cockroach/pkg/rpc.(*Context).runHeartbeat(0xc4207d6820, 0xc4208dfb00, 0xc4201e1b30, 0xf, 0x0, 0x0)
/go/src/github.com/cockroachdb/cockroach/pkg/rpc/context.go:412 +0x7ef
github.com/cockroachdb/cockroach/pkg/rpc.(*Context).GRPCDial.func1.2.1(0x7f4af7f29238, 0xc4207a1ad0)
/go/src/github.com/cockroachdb/cockroach/pkg/rpc/context.go:346 +0x6b
github.com/cockroachdb/cockroach/pkg/util/stop.(*Stopper).RunWorker.func1(0xc420245d70, 0xc42001cea0, 0xc4207a1a40)
/go/src/github.com/cockroachdb/cockroach/pkg/util/stop/stopper.go:193 +0xf7
created by github.com/cockroachdb/cockroach/pkg/util/stop.(*Stopper).RunWorker
/go/src/github.com/cockroachdb/cockroach/pkg/util/stop/stopper.go:194 +0xad
goroutine 629 [chan receive, 8 minutes]:
github.com/cockroachdb/cockroach/pkg/rpc.NewContext.func1(0x7f4af7f29238, 0xc4207a0240)
/go/src/github.com/cockroachdb/cockroach/pkg/rpc/context.go:209 +0x5d
github.com/cockroachdb/cockroach/pkg/util/stop.(*Stopper).RunWorker.func1(0xc4201e1660, 0xc42001cea0, 0xc420296be0)
/go/src/github.com/cockroachdb/cockroach/pkg/util/stop/stopper.go:193 +0xf7
created by github.com/cockroachdb/cockroach/pkg/util/stop.(*Stopper).RunWorker
/go/src/github.com/cockroachdb/cockroach/pkg/util/stop/stopper.go:194 +0xad
goroutine 667 [IO wait, 8 minutes]:
net.runtime_pollWait(0x7f4af805e7a8, 0x72, 0x6)
/usr/local/go/src/runtime/netpoll.go:164 +0x59
net.(*pollDesc).wait(0xc420b02768, 0x72, 0x266c700, 0x2661ba8)
/usr/local/go/src/net/fd_poll_runtime.go:75 +0x38
net.(*pollDesc).waitRead(0xc420b02768, 0xc420a7e000, 0x1000)
/usr/local/go/src/net/fd_poll_runtime.go:80 +0x34
net.(*netFD).Read(0xc420b02700, 0xc420a7e000, 0x1000, 0x1000, 0x0, 0x266c700, 0x2661ba8)
/usr/local/go/src/net/fd_unix.go:250 +0x1b7
net.(*conn).Read(0xc42000e498, 0xc420a7e000, 0x1000, 0x1000, 0x0, 0x0, 0x0)
/usr/local/go/src/net/net.go:181 +0x70
net/http.(*persistConn).Read(0xc42042f7a0, 0xc420a7e000, 0x1000, 0x1000, 0x4, 0xc4202e4660, 0x17)
/usr/local/go/src/net/http/transport.go:1316 +0x14b
bufio.(*Reader).fill(0xc420bdaae0)
/usr/local/go/src/bufio/bufio.go:97 +0x117
bufio.(*Reader).Peek(0xc420bdaae0, 0x1, 0x0, 0x1, 0x0, 0xc42055f1a0, 0x0)
/usr/local/go/src/bufio/bufio.go:129 +0x67
net/http.(*persistConn).readLoop(0xc42042f7a0)
/usr/local/go/src/net/http/transport.go:1474 +0x196
created by net/http.(*Transport).dialConn
/usr/local/go/src/net/http/transport.go:1117 +0xa35
goroutine 1553 [IO wait, 6 minutes]:
net.runtime_pollWait(0x7f4af8062738, 0x72, 0x20)
/usr/local/go/src/runtime/netpoll.go:164 +0x59
net.(*pollDesc).wait(0xc420464768, 0x72, 0x266c700, 0x2661ba8)
/usr/local/go/src/net/fd_poll_runtime.go:75 +0x38
net.(*pollDesc).waitRead(0xc420464768, 0xc4207e5000, 0x1000)
/usr/local/go/src/net/fd_poll_runtime.go:80 +0x34
net.(*netFD).Read(0xc420464700, 0xc4207e5000, 0x1000, 0x1000, 0x0, 0x266c700, 0x2661ba8)
/usr/local/go/src/net/fd_unix.go:250 +0x1b7
net.(*conn).Read(0xc4207c4128, 0xc4207e5000, 0x1000, 0x1000, 0x0, 0x0, 0x0)
/usr/local/go/src/net/net.go:181 +0x70
net/http.(*persistConn).Read(0xc4200c3b00, 0xc4207e5000, 0x1000, 0x1000, 0x4, 0xc42026ece0, 0x17)
/usr/local/go/src/net/http/transport.go:1316 +0x14b
bufio.(*Reader).fill(0xc420531740)
/usr/local/go/src/bufio/bufio.go:97 +0x117
bufio.(*Reader).Peek(0xc420531740, 0x1, 0x0, 0x1, 0x0, 0xc4209fc420, 0x0)
/usr/local/go/src/bufio/bufio.go:129 +0x67
net/http.(*persistConn).readLoop(0xc4200c3b00)
/usr/local/go/src/net/http/transport.go:1474 +0x196
created by net/http.(*Transport).dialConn
/usr/local/go/src/net/http/transport.go:1117 +0xa35
goroutine 2182 [select, 5 minutes]:
net/http.(*persistConn).writeLoop(0xc420660a20)
/usr/local/go/src/net/http/transport.go:1704 +0x43a
created by net/http.(*Transport).dialConn
/usr/local/go/src/net/http/transport.go:1118 +0xa5a
goroutine 509 [select]:
github.com/cockroachdb/cockroach/vendor/google.golang.org/grpc.(*addrConn).resetTransport(0xc4205388c0, 0xc420ab4900, 0x0, 0x0)
/go/src/github.com/cockroachdb/cockroach/vendor/google.golang.org/grpc/clientconn.go:888 +0x8e5
github.com/cockroachdb/cockroach/vendor/google.golang.org/grpc.(*addrConn).transportMonitor(0xc4205388c0)
/go/src/github.com/cockroachdb/cockroach/vendor/google.golang.org/grpc/clientconn.go:972 +0x362
github.com/cockroachdb/cockroach/vendor/google.golang.org/grpc.(*ClientConn).resetAddrConn.func1(0xc4205388c0)
/go/src/github.com/cockroachdb/cockroach/vendor/google.golang.org/grpc/clientconn.go:642 +0x1d9
created by github.com/cockroachdb/cockroach/vendor/google.golang.org/grpc.(*ClientConn).resetAddrConn
/go/src/github.com/cockroachdb/cockroach/vendor/google.golang.org/grpc/clientconn.go:643 +0x786
goroutine 510 [select]:
github.com/cockroachdb/cockroach/pkg/rpc.(*Context).runHeartbeat(0xc4202811e0, 0xc42079ee40, 0xc420a0c5f0, 0xf, 0x0, 0x0)
/go/src/github.com/cockroachdb/cockroach/pkg/rpc/context.go:412 +0x7ef
github.com/cockroachdb/cockroach/pkg/rpc.(*Context).GRPCDial.func1.2.1(0x7f4af7f29238, 0xc4207a0ba0)
/go/src/github.com/cockroachdb/cockroach/pkg/rpc/context.go:346 +0x6b
github.com/cockroachdb/cockroach/pkg/util/stop.(*Stopper).RunWorker.func1(0xc4202453d0, 0xc42001cea0, 0xc4207a0b10)
/go/src/github.com/cockroachdb/cockroach/pkg/util/stop/stopper.go:193 +0xf7
created by github.com/cockroachdb/cockroach/pkg/util/stop.(*Stopper).RunWorker
/go/src/github.com/cockroachdb/cockroach/pkg/util/stop/stopper.go:194 +0xad
goroutine 544 [chan receive, 8 minutes]:
github.com/cockroachdb/cockroach/pkg/rpc.NewContext.func1(0x7f4af7f29238, 0xc420791a10)
/go/src/github.com/cockroachdb/cockroach/pkg/rpc/context.go:209 +0x5d
github.com/cockroachdb/cockroach/pkg/util/stop.(*Stopper).RunWorker.func1(0xc420310ad0, 0xc42001cea0, 0xc420264e60)
/go/src/github.com/cockroachdb/cockroach/pkg/util/stop/stopper.go:193 +0xf7
created by github.com/cockroachdb/cockroach/pkg/util/stop.(*Stopper).RunWorker
/go/src/github.com/cockroachdb/cockroach/pkg/util/stop/stopper.go:194 +0xad
goroutine 1747 [IO wait, 6 minutes]:
net.runtime_pollWait(0x7f4af80625b8, 0x72, 0x22)
/usr/local/go/src/runtime/netpoll.go:164 +0x59
net.(*pollDesc).wait(0xc420b04308, 0x72, 0x266c700, 0x2661ba8)
/usr/local/go/src/net/fd_poll_runtime.go:75 +0x38
net.(*pollDesc).waitRead(0xc420b04308, 0xc42031d000, 0x1000)
/usr/local/go/src/net/fd_poll_runtime.go:80 +0x34
net.(*netFD).Read(0xc420b042a0, 0xc42031d000, 0x1000, 0x1000, 0x0, 0x266c700, 0x2661ba8)
/usr/local/go/src/net/fd_unix.go:250 +0x1b7
net.(*conn).Read(0xc42000e190, 0xc42031d000, 0x1000, 0x1000, 0x0, 0x0, 0x0)
/usr/local/go/src/net/net.go:181 +0x70
net/http.(*persistConn).Read(0xc4209a27e0, 0xc42031d000, 0x1000, 0x1000, 0x4, 0xc4202bace0, 0x17)
/usr/local/go/src/net/http/transport.go:1316 +0x14b
bufio.(*Reader).fill(0xc4208b4de0)
/usr/local/go/src/bufio/bufio.go:97 +0x117
bufio.(*Reader).Peek(0xc4208b4de0, 0x1, 0x0, 0x1, 0x0, 0xc420802960, 0x0)
/usr/local/go/src/bufio/bufio.go:129 +0x67
net/http.(*persistConn).readLoop(0xc4209a27e0)
/usr/local/go/src/net/http/transport.go:1474 +0x196
created by net/http.(*Transport).dialConn
/usr/local/go/src/net/http/transport.go:1117 +0xa35
goroutine 4145 [IO wait, 2 minutes]:
net.runtime_pollWait(0x7f4af8061bf8, 0x72, 0x2d)
/usr/local/go/src/runtime/netpoll.go:164 +0x59
net.(*pollDesc).wait(0xc4210b8228, 0x72, 0x266c700, 0x2661ba8)
/usr/local/go/src/net/fd_poll_runtime.go:75 +0x38
net.(*pollDesc).waitRead(0xc4210b8228, 0xc420c15000, 0x1000)
/usr/local/go/src/net/fd_poll_runtime.go:80 +0x34
net.(*netFD).Read(0xc4210b81c0, 0xc420c15000, 0x1000, 0x1000, 0x0, 0x266c700, 0x2661ba8)
/usr/local/go/src/net/fd_unix.go:250 +0x1b7
net.(*conn).Read(0xc420a8e390, 0xc420c15000, 0x1000, 0x1000, 0x0, 0x0, 0x0)
/usr/local/go/src/net/net.go:181 +0x70
net/http.(*persistConn).Read(0xc4201b0a20, 0xc420c15000, 0x1000, 0x1000, 0x4, 0xc420b87120, 0x17)
/usr/local/go/src/net/http/transport.go:1316 +0x14b
bufio.(*Reader).fill(0xc4210b2f60)
/usr/local/go/src/bufio/bufio.go:97 +0x117
bufio.(*Reader).Peek(0xc4210b2f60, 0x1, 0x0, 0x1, 0x0, 0xc420c41c20, 0x0)
/usr/local/go/src/bufio/bufio.go:129 +0x67
net/http.(*persistConn).readLoop(0xc4201b0a20)
/usr/local/go/src/net/http/transport.go:1474 +0x196
created by net/http.(*Transport).dialConn
/usr/local/go/src/net/http/transport.go:1117 +0xa35
goroutine 2117 [select, 5 minutes]:
net/http.(*persistConn).writeLoop(0xc4202a8a20)
/usr/local/go/src/net/http/transport.go:1704 +0x43a
created by net/http.(*Transport).dialConn
/usr/local/go/src/net/http/transport.go:1118 +0xa5a
goroutine 4534 [select]:
github.com/cockroachdb/cockroach/pkg/rpc.(*Context).runHeartbeat(0xc42073fad0, 0xc42078c400, 0xc420390fa0, 0xf, 0x0, 0x0)
/go/src/github.com/cockroachdb/cockroach/pkg/rpc/context.go:412 +0x7ef
github.com/cockroachdb/cockroach/pkg/rpc.(*Context).GRPCDial.func1.2.1(0x7f4af7f29238, 0xc421359860)
/go/src/github.com/cockroachdb/cockroach/pkg/rpc/context.go:346 +0x6b
github.com/cockroachdb/cockroach/pkg/util/stop.(*Stopper).RunWorker.func1(0xc42033e0e0, 0xc42001cea0, 0xc421359710)
/go/src/github.com/cockroachdb/cockroach/pkg/util/stop/stopper.go:193 +0xf7
created by github.com/cockroachdb/cockroach/pkg/util/stop.(*Stopper).RunWorker
/go/src/github.com/cockroachdb/cockroach/pkg/util/stop/stopper.go:194 +0xad
goroutine 1748 [select, 6 minutes]:
net/http.(*persistConn).writeLoop(0xc4209a27e0)
/usr/local/go/src/net/http/transport.go:1704 +0x43a
created by net/http.(*Transport).dialConn
/usr/local/go/src/net/http/transport.go:1118 +0xa5a
goroutine 2531 [select]:
github.com/cockroachdb/cockroach/vendor/google.golang.org/grpc.(*addrConn).resetTransport(0xc42040ee00, 0xc420743300, 0x0, 0x0)
/go/src/github.com/cockroachdb/cockroach/vendor/google.golang.org/grpc/clientconn.go:888 +0x8e5
github.com/cockroachdb/cockroach/vendor/google.golang.org/grpc.(*addrConn).transportMonitor(0xc42040ee00)
/go/src/github.com/cockroachdb/cockroach/vendor/google.golang.org/grpc/clientconn.go:972 +0x362
github.com/cockroachdb/cockroach/vendor/google.golang.org/grpc.(*ClientConn).resetAddrConn.func1(0xc42040ee00)
/go/src/github.com/cockroachdb/cockroach/vendor/google.golang.org/grpc/clientconn.go:642 +0x1d9
created by github.com/cockroachdb/cockroach/vendor/google.golang.org/grpc.(*ClientConn).resetAddrConn
/go/src/github.com/cockroachdb/cockroach/vendor/google.golang.org/grpc/clientconn.go:643 +0x786
goroutine 788 [select, 8 minutes]:
net/http.(*persistConn).writeLoop(0xc420660360)
/usr/local/go/src/net/http/transport.go:1704 +0x43a
created by net/http.(*Transport).dialConn
/usr/local/go/src/net/http/transport.go:1118 +0xa5a
goroutine 890 [select, 7 minutes]:
net/http.(*persistConn).writeLoop(0xc4206607e0)
/usr/local/go/src/net/http/transport.go:1704 +0x43a
created by net/http.(*Transport).dialConn
/usr/local/go/src/net/http/transport.go:1118 +0xa5a
goroutine 889 [IO wait, 7 minutes]:
net.runtime_pollWait(0x7f4af805e4a8, 0x72, 0x19)
/usr/local/go/src/runtime/netpoll.go:164 +0x59
net.(*pollDesc).wait(0xc420562458, 0x72, 0x266c700, 0x2661ba8)
/usr/local/go/src/net/fd_poll_runtime.go:75 +0x38
net.(*pollDesc).waitRead(0xc420562458, 0xc4207c1000, 0x1000)
/usr/local/go/src/net/fd_poll_runtime.go:80 +0x34
net.(*netFD).Read(0xc4205623f0, 0xc4207c1000, 0x1000, 0x1000, 0x0, 0x266c700, 0x2661ba8)
/usr/local/go/src/net/fd_unix.go:250 +0x1b7
net.(*conn).Read(0xc42000e110, 0xc4207c1000, 0x1000, 0x1000, 0x0, 0x0, 0x0)
/usr/local/go/src/net/net.go:181 +0x70
net/http.(*persistConn).Read(0xc4206607e0, 0xc4207c1000, 0x1000, 0x1000, 0x4, 0xc4202baa40, 0x17)
/usr/local/go/src/net/http/transport.go:1316 +0x14b
bufio.(*Reader).fill(0xc420b497a0)
/usr/local/go/src/bufio/bufio.go:97 +0x117
bufio.(*Reader).Peek(0xc420b497a0, 0x1, 0x0, 0x1, 0x0, 0xc4201c45a0, 0x0)
/usr/local/go/src/bufio/bufio.go:129 +0x67
net/http.(*persistConn).readLoop(0xc4206607e0)
/usr/local/go/src/net/http/transport.go:1474 +0x196
created by net/http.(*Transport).dialConn
/usr/local/go/src/net/http/transport.go:1117 +0xa35
goroutine 1309 [IO wait, 6 minutes]:
net.runtime_pollWait(0x7f4af80628b8, 0x72, 0x1e)
/usr/local/go/src/runtime/netpoll.go:164 +0x59
net.(*pollDesc).wait(0xc4202983e8, 0x72, 0x266c700, 0x2661ba8)
/usr/local/go/src/net/fd_poll_runtime.go:75 +0x38
net.(*pollDesc).waitRead(0xc4202983e8, 0xc420548000, 0x1000)
/usr/local/go/src/net/fd_poll_runtime.go:80 +0x34
net.(*netFD).Read(0xc420298380, 0xc420548000, 0x1000, 0x1000, 0x0, 0x266c700, 0x2661ba8)
/usr/local/go/src/net/fd_unix.go:250 +0x1b7
net.(*conn).Read(0xc4207781e8, 0xc420548000, 0x1000, 0x1000, 0x0, 0x0, 0x0)
/usr/local/go/src/net/net.go:181 +0x70
net/http.(*persistConn).Read(0xc420772360, 0xc420548000, 0x1000, 0x1000, 0x4, 0xc420249200, 0x17)
/usr/local/go/src/net/http/transport.go:1316 +0x14b
bufio.(*Reader).fill(0xc420531620)
/usr/local/go/src/bufio/bufio.go:97 +0x117
bufio.(*Reader).Peek(0xc420531620, 0x1, 0x0, 0x1, 0x0, 0xc4209f6540, 0x0)
/usr/local/go/src/bufio/bufio.go:129 +0x67
net/http.(*persistConn).readLoop(0xc420772360)
/usr/local/go/src/net/http/transport.go:1474 +0x196
created by net/http.(*Transport).dialConn
/usr/local/go/src/net/http/transport.go:1117 +0xa35
goroutine 1166 [IO wait, 7 minutes]:
net.runtime_pollWait(0x7f4af8062a38, 0x72, 0x1c)
/usr/local/go/src/runtime/netpoll.go:164 +0x59
net.(*pollDesc).wait(0xc420b043e8, 0x72, 0x266c700, 0x2661ba8)
/usr/local/go/src/net/fd_poll_runtime.go:75 +0x38
net.(*pollDesc).waitRead(0xc420b043e8, 0xc4206c2000, 0x1000)
/usr/local/go/src/net/fd_poll_runtime.go:80 +0x34
net.(*netFD).Read(0xc420b04380, 0xc4206c2000, 0x1000, 0x1000, 0x0, 0x266c700, 0x2661ba8)
/usr/local/go/src/net/fd_unix.go:250 +0x1b7
net.(*conn).Read(0xc420778070, 0xc4206c2000, 0x1000, 0x1000, 0x0, 0x0, 0x0)
/usr/local/go/src/net/net.go:181 +0x70
net/http.(*persistConn).Read(0xc4202a8900, 0xc4206c2000, 0x1000, 0x1000, 0x4, 0xc4202f4ee0, 0x17)
/usr/local/go/src/net/http/transport.go:1316 +0x14b
bufio.(*Reader).fill(0xc420a73140)
/usr/local/go/src/bufio/bufio.go:97 +0x117
bufio.(*Reader).Peek(0xc420a73140, 0x1, 0x0, 0x1, 0x0, 0xc420530480, 0x0)
/usr/local/go/src/bufio/bufio.go:129 +0x67
net/http.(*persistConn).readLoop(0xc4202a8900)
/usr/local/go/src/net/http/transport.go:1474 +0x196
created by net/http.(*Transport).dialConn
/usr/local/go/src/net/http/transport.go:1117 +0xa35
goroutine 4556 [select]:
github.com/cockroachdb/cockroach/vendor/google.golang.org/grpc.(*addrConn).resetTransport(0xc420c561c0, 0xc420f12500, 0x0, 0x0)
/go/src/github.com/cockroachdb/cockroach/vendor/google.golang.org/grpc/clientconn.go:888 +0x8e5
github.com/cockroachdb/cockroach/vendor/google.golang.org/grpc.(*addrConn).transportMonitor(0xc420c561c0)
/go/src/github.com/cockroachdb/cockroach/vendor/google.golang.org/grpc/clientconn.go:972 +0x362
github.com/cockroachdb/cockroach/vendor/google.golang.org/grpc.(*ClientConn).resetAddrConn.func1(0xc420c561c0)
/go/src/github.com/cockroachdb/cockroach/vendor/google.golang.org/grpc/clientconn.go:642 +0x1d9
created by github.com/cockroachdb/cockroach/vendor/google.golang.org/grpc.(*ClientConn).resetAddrConn
/go/src/github.com/cockroachdb/cockroach/vendor/google.golang.org/grpc/clientconn.go:643 +0x786
goroutine 2425 [IO wait, 5 minutes]:
net.runtime_pollWait(0x7f4af8061fb8, 0x72, 0x2a)
/usr/local/go/src/runtime/netpoll.go:164 +0x59
net.(*pollDesc).wait(0xc4200bd3a8, 0x72, 0x266c700, 0x2661ba8)
/usr/local/go/src/net/fd_poll_runtime.go:75 +0x38
net.(*pollDesc).waitRead(0xc4200bd3a8, 0xc420946000, 0x1000)
/usr/local/go/src/net/fd_poll_runtime.go:80 +0x34
net.(*netFD).Read(0xc4200bd340, 0xc420946000, 0x1000, 0x1000, 0x0, 0x266c700, 0x2661ba8)
/usr/local/go/src/net/fd_unix.go:250 +0x1b7
net.(*conn).Read(0xc4207782e0, 0xc420946000, 0x1000, 0x1000, 0x0, 0x0, 0x0)
/usr/local/go/src/net/net.go:181 +0x70
net/http.(*persistConn).Read(0xc420661d40, 0xc420946000, 0x1000, 0x1000, 0x4, 0xc4201d81c0, 0x17)
/usr/local/go/src/net/http/transport.go:1316 +0x14b
bufio.(*Reader).fill(0xc420c2bb60)
/usr/local/go/src/bufio/bufio.go:97 +0x117
bufio.(*Reader).Peek(0xc420c2bb60, 0x1, 0x0, 0x1, 0x0, 0xc42080cd80, 0x0)
/usr/local/go/src/bufio/bufio.go:129 +0x67
net/http.(*persistConn).readLoop(0xc420661d40)
/usr/local/go/src/net/http/transport.go:1474 +0x196
created by net/http.(*Transport).dialConn
/usr/local/go/src/net/http/transport.go:1117 +0xa35
goroutine 1167 [select, 7 minutes]:
net/http.(*persistConn).writeLoop(0xc4202a8900)
/usr
```
Please assign, take a look and update the issue accordingly. | non_priority | teamcity failed tests on master acceptance testdockerreadwritebidirectionalreferenceversion the following tests appear to have failed fail acceptance testdockerreadwritebidirectionalreferenceversion test ended in panic stdout xenial pulling from library ubuntu digest status image is up to date for ubuntu xenial pulling from cockroachdb postgres test digest status image is up to date for cockroachdb postgres test file ��� cockroach cockroach��� size blocks io block regular file device inode links access rwxr xr x uid unknown gid unknown access modify change birth xenial pulling from library ubuntu digest status image is up to date for ubuntu xenial pulling from cockroachdb postgres test digest status image is up to date for cockroachdb postgres test panic test timed out after goroutine testing startalarm usr local go src testing testing go created by time gofunc usr local go src time sleep go goroutine testing t run usr local go src testing testing go testing runtests usr local go src testing testing go testing trunner usr local go src testing testing go testing runtests usr local go src testing testing go testing m run usr local go src testing testing go github com cockroachdb cockroach pkg acceptance runtests go src github com cockroachdb cockroach pkg acceptance util go github com cockroachdb cockroach pkg acceptance maintest go src github com cockroachdb cockroach pkg acceptance test acceptance go github com cockroachdb cockroach pkg acceptance testmain go src github com cockroachdb cockroach pkg acceptance main test go main main github com cockroachdb cockroach pkg acceptance test testmain go goroutine runtime goexit usr local go src runtime asm s goroutine github com cockroachdb cockroach pkg util log loggingt flushdaemon go src github com cockroachdb cockroach pkg util log clog go created by github com cockroachdb cockroach pkg util log init go src github com cockroachdb cockroach pkg util log clog go goroutine os signal signal recv usr local go src runtime sigqueue go os signal loop usr local go src os signal signal unix go created by os signal init usr local go src os signal signal unix go goroutine github com cockroachdb cockroach pkg acceptance runtests go src github com cockroachdb cockroach pkg acceptance util go created by github com cockroachdb cockroach pkg acceptance runtests go src github com cockroachdb cockroach pkg acceptance util go goroutine net http persistconn roundtrip usr local go src net http transport go net http transport roundtrip usr local go src net http transport go net http send usr local go src net http client go net http client send usr local go src net http client go net http client do usr local go src net http client go github com cockroachdb cockroach vendor golang org x net context ctxhttp do go src github com cockroachdb cockroach vendor golang org x net context ctxhttp ctxhttp go github com cockroachdb cockroach vendor github com docker docker client client dorequest go src github com cockroachdb cockroach vendor github com docker docker client request go github com cockroachdb cockroach vendor github com docker docker client client sendrequest go src github com cockroachdb cockroach vendor github com docker docker client request go github com cockroachdb cockroach vendor github com docker docker client client post go src github com cockroachdb cockroach vendor github com docker docker client request go github com cockroachdb cockroach vendor github com docker docker client client containerwait go src github com cockroachdb cockroach vendor github com docker docker client container wait go github com cockroachdb cockroach pkg acceptance cluster retryingdockerclient containerwait go src github com cockroachdb cockroach pkg acceptance cluster docker go github com cockroachdb cockroach pkg acceptance cluster retry go src github com cockroachdb cockroach pkg acceptance cluster docker go github com cockroachdb cockroach pkg acceptance cluster retryingdockerclient containerwait go src github com cockroachdb cockroach pkg acceptance cluster docker go github com cockroachdb cockroach pkg acceptance cluster retryingdockerclient containerwait github com cockroachdb cockroach pkg acceptance cluster container wait go src github com cockroachdb cockroach pkg acceptance cluster docker go github com cockroachdb cockroach pkg acceptance cluster localcluster oneshot go src github com cockroachdb cockroach pkg acceptance cluster localcluster go github com cockroachdb cockroach pkg acceptance testdocker go src github com cockroachdb cockroach pkg acceptance util go github com cockroachdb cockroach pkg acceptance testdockeroneshot go src github com cockroachdb cockroach pkg acceptance util go github com cockroachdb cockroach pkg acceptance runreferencetestwithscript go src github com cockroachdb cockroach pkg acceptance reference test go github com cockroachdb cockroach pkg acceptance runreadwritereferencetest go src github com cockroachdb cockroach pkg acceptance reference test go github com cockroachdb cockroach pkg acceptance testdockerreadwritebidirectionalreferenceversion go src github com cockroachdb cockroach pkg acceptance reference test go testing trunner usr local go src testing testing go created by testing t run usr local go src testing testing go goroutine runtime gopark usr local go src runtime proc go runtime selectgoimpl usr local go src runtime select go runtime selectgo usr local go src runtime select go runtime ensuresigm usr local go src runtime signal unix go runtime goexit usr local go src runtime asm s goroutine database sql db connectionopener usr local go src database sql sql go created by database sql open usr local go src database sql sql go goroutine github com cockroachdb cockroach pkg rpc newcontext go src github com cockroachdb cockroach pkg rpc context go github com cockroachdb cockroach pkg util stop stopper runworker go src github com cockroachdb cockroach pkg util stop stopper go created by github com cockroachdb cockroach pkg util stop stopper runworker go src github com cockroachdb cockroach pkg util stop stopper go goroutine net http persistconn writeloop usr local go src net http transport go created by net http transport dialconn usr local go src net http transport go goroutine github com cockroachdb cockroach pkg rpc context runheartbeat go src github com cockroachdb cockroach pkg rpc context go github com cockroachdb cockroach pkg rpc context grpcdial go src github com cockroachdb cockroach pkg rpc context go github com cockroachdb cockroach pkg util stop stopper runworker go src github com cockroachdb cockroach pkg util stop stopper go created by github com cockroachdb cockroach pkg util stop stopper runworker go src github com cockroachdb cockroach pkg util stop stopper go goroutine github com cockroachdb cockroach pkg rpc newcontext go src github com cockroachdb cockroach pkg rpc context go github com cockroachdb cockroach pkg util stop stopper runworker go src github com cockroachdb cockroach pkg util stop stopper go created by github com cockroachdb cockroach pkg util stop stopper runworker go src github com cockroachdb cockroach pkg util stop stopper go goroutine github com cockroachdb cockroach pkg rpc context runheartbeat go src github com cockroachdb cockroach pkg rpc context go github com cockroachdb cockroach pkg rpc context grpcdial go src github com cockroachdb cockroach pkg rpc context go github com cockroachdb cockroach pkg util stop stopper runworker go src github com cockroachdb cockroach pkg util stop stopper go created by github com cockroachdb cockroach pkg util stop stopper runworker go src github com cockroachdb cockroach pkg util stop stopper go goroutine github com cockroachdb cockroach pkg rpc newcontext go src github com cockroachdb cockroach pkg rpc context go github com cockroachdb cockroach pkg util stop stopper runworker go src github com cockroachdb cockroach pkg util stop stopper go created by github com cockroachdb cockroach pkg util stop stopper runworker go src github com cockroachdb cockroach pkg util stop stopper go goroutine net runtime pollwait usr local go src runtime netpoll go net polldesc wait usr local go src net fd poll runtime go net polldesc waitread usr local go src net fd poll runtime go net netfd read usr local go src net fd unix go net conn read usr local go src net net go net http persistconn read usr local go src net http transport go bufio reader fill usr local go src bufio bufio go bufio reader peek usr local go src bufio bufio go net http persistconn readloop usr local go src net http transport go created by net http transport dialconn usr local go src net http transport go goroutine github com cockroachdb cockroach vendor google golang org grpc addrconn resettransport go src github com cockroachdb cockroach vendor google golang org grpc clientconn go github com cockroachdb cockroach vendor google golang org grpc addrconn transportmonitor go src github com cockroachdb cockroach vendor google golang org grpc clientconn go github com cockroachdb cockroach vendor google golang org grpc clientconn resetaddrconn go src github com cockroachdb cockroach vendor google golang org grpc clientconn go created by github com cockroachdb cockroach vendor google golang org grpc clientconn resetaddrconn go src github com cockroachdb cockroach vendor google golang org grpc clientconn go goroutine github com cockroachdb cockroach pkg rpc newcontext go src github com cockroachdb cockroach pkg rpc context go github com cockroachdb cockroach pkg util stop stopper runworker go src github com cockroachdb cockroach pkg util stop stopper go created by github com cockroachdb cockroach pkg util stop stopper runworker go src github com cockroachdb cockroach pkg util stop stopper go goroutine github com cockroachdb cockroach pkg rpc context runheartbeat go src github com cockroachdb cockroach pkg rpc context go github com cockroachdb cockroach pkg rpc context grpcdial go src github com cockroachdb cockroach pkg rpc context go github com cockroachdb cockroach pkg util stop stopper runworker go src github com cockroachdb cockroach pkg util stop stopper go created by github com cockroachdb cockroach pkg util stop stopper runworker go src github com cockroachdb cockroach pkg util stop stopper go goroutine net runtime pollwait usr local go src runtime netpoll go net polldesc wait usr local go src net fd poll runtime go net polldesc waitread usr local go src net fd poll runtime go net netfd read usr local go src net fd unix go net conn read usr local go src net net go net http persistconn read usr local go src net http transport go bufio reader fill usr local go src bufio bufio go bufio reader peek usr local go src bufio bufio go net http persistconn readloop usr local go src net http transport go created by net http transport dialconn usr local go src net http transport go goroutine net http persistconn writeloop usr local go src net http transport go created by net http transport dialconn usr local go src net http transport go goroutine github com cockroachdb cockroach vendor google golang org grpc addrconn resettransport go src github com cockroachdb cockroach vendor google golang org grpc clientconn go github com cockroachdb cockroach vendor google golang org grpc addrconn transportmonitor go src github com cockroachdb cockroach vendor google golang org grpc clientconn go github com cockroachdb cockroach vendor google golang org grpc clientconn resetaddrconn go src github com cockroachdb cockroach vendor google golang org grpc clientconn go created by github com cockroachdb cockroach vendor google golang org grpc clientconn resetaddrconn go src github com cockroachdb cockroach vendor google golang org grpc clientconn go goroutine github com cockroachdb cockroach pkg rpc context runheartbeat go src github com cockroachdb cockroach pkg rpc context go github com cockroachdb cockroach pkg rpc context grpcdial go src github com cockroachdb cockroach pkg rpc context go github com cockroachdb cockroach pkg util stop stopper runworker go src github com cockroachdb cockroach pkg util stop stopper go created by github com cockroachdb cockroach pkg util stop stopper runworker go src github com cockroachdb cockroach pkg util stop stopper go goroutine net runtime pollwait usr local go src runtime netpoll go net polldesc wait usr local go src net fd poll runtime go net polldesc waitread usr local go src net fd poll runtime go net netfd read usr local go src net fd unix go net conn read usr local go src net net go net http persistconn read usr local go src net http transport go bufio reader fill usr local go src bufio bufio go bufio reader peek usr local go src bufio bufio go net http persistconn readloop usr local go src net http transport go created by net http transport dialconn usr local go src net http transport go goroutine net http persistconn writeloop usr local go src net http transport go created by net http transport dialconn usr local go src net http transport go goroutine net http persistconn writeloop usr local go src net http transport go created by net http transport dialconn usr local go src net http transport go goroutine github com cockroachdb cockroach vendor google golang org grpc addrconn resettransport go src github com cockroachdb cockroach vendor google golang org grpc clientconn go github com cockroachdb cockroach vendor google golang org grpc addrconn transportmonitor go src github com cockroachdb cockroach vendor google golang org grpc clientconn go github com cockroachdb cockroach vendor google golang org grpc clientconn resetaddrconn go src github com cockroachdb cockroach vendor google golang org grpc clientconn go created by github com cockroachdb cockroach vendor google golang org grpc clientconn resetaddrconn go src github com cockroachdb cockroach vendor google golang org grpc clientconn go goroutine net runtime pollwait usr local go src runtime netpoll go net polldesc wait usr local go src net fd poll runtime go net polldesc waitread usr local go src net fd poll runtime go net netfd read usr local go src net fd unix go net conn read usr local go src net net go net http persistconn read usr local go src net http transport go bufio reader fill usr local go src bufio bufio go bufio reader peek usr local go src bufio bufio go net http persistconn readloop usr local go src net http transport go created by net http transport dialconn usr local go src net http transport go goroutine github com cockroachdb cockroach vendor google golang org grpc addrconn resettransport go src github com cockroachdb cockroach vendor google golang org grpc clientconn go github com cockroachdb cockroach vendor google golang org grpc addrconn transportmonitor go src github com cockroachdb cockroach vendor google golang org grpc clientconn go github com cockroachdb cockroach vendor google golang org grpc clientconn resetaddrconn go src github com cockroachdb cockroach vendor google golang org grpc clientconn go created by github com cockroachdb cockroach vendor google golang org grpc clientconn resetaddrconn go src github com cockroachdb cockroach vendor google golang org grpc clientconn go goroutine database sql db connectionopener usr local go src database sql sql go created by database sql open usr local go src database sql sql go goroutine net http persistconn writeloop usr local go src net http transport go created by net http transport dialconn usr local go src net http transport go goroutine net runtime pollwait usr local go src runtime netpoll go net polldesc wait usr local go src net fd poll runtime go net polldesc waitread usr local go src net fd poll runtime go net netfd read usr local go src net fd unix go net conn read usr local go src net net go net http persistconn read usr local go src net http transport go bufio reader fill usr local go src bufio bufio go bufio reader peek usr local go src bufio bufio go net http persistconn readloop usr local go src net http transport go created by net http transport dialconn usr local go src net http transport go goroutine github com cockroachdb cockroach pkg rpc newcontext go src github com cockroachdb cockroach pkg rpc context go github com cockroachdb cockroach pkg util stop stopper runworker go src github com cockroachdb cockroach pkg util stop stopper go created by github com cockroachdb cockroach pkg util stop stopper runworker go src github com cockroachdb cockroach pkg util stop stopper go goroutine github com cockroachdb cockroach pkg rpc newcontext go src github com cockroachdb cockroach pkg rpc context go github com cockroachdb cockroach pkg util stop stopper runworker go src github com cockroachdb cockroach pkg util stop stopper go created by github com cockroachdb cockroach pkg util stop stopper runworker go src github com cockroachdb cockroach pkg util stop stopper go goroutine database sql db connectionopener usr local go src database sql sql go created by database sql open usr local go src database sql sql go goroutine database sql db connectionopener usr local go src database sql sql go created by database sql open usr local go src database sql sql go goroutine database sql db connectionopener usr local go src database sql sql go created by database sql open usr local go src database sql sql go goroutine database sql db connectionopener usr local go src database sql sql go created by database sql open usr local go src database sql sql go goroutine github com cockroachdb cockroach pkg rpc context runheartbeat go src github com cockroachdb cockroach pkg rpc context go github com cockroachdb cockroach pkg rpc context grpcdial go src github com cockroachdb cockroach pkg rpc context go github com cockroachdb cockroach pkg util stop stopper runworker go src github com cockroachdb cockroach pkg util stop stopper go created by github com cockroachdb cockroach pkg util stop stopper runworker go src github com cockroachdb cockroach pkg util stop stopper go goroutine net http persistconn writeloop usr local go src net http transport go created by net http transport dialconn usr local go src net http transport go goroutine net runtime pollwait usr local go src runtime netpoll go net polldesc wait usr local go src net fd poll runtime go net polldesc waitread usr local go src net fd poll runtime go net netfd read usr local go src net fd unix go net conn read usr local go src net net go net http persistconn read usr local go src net http transport go bufio reader fill usr local go src bufio bufio go bufio reader peek usr local go src bufio bufio go net http persistconn readloop usr local go src net http transport go created by net http transport dialconn usr local go src net http transport go goroutine net http persistconn writeloop usr local go src net http transport go created by net http transport dialconn usr local go src net http transport go goroutine github com cockroachdb cockroach pkg rpc context runheartbeat go src github com cockroachdb cockroach pkg rpc context go github com cockroachdb cockroach pkg rpc context grpcdial go src github com cockroachdb cockroach pkg rpc context go github com cockroachdb cockroach pkg util stop stopper runworker go src github com cockroachdb cockroach pkg util stop stopper go created by github com cockroachdb cockroach pkg util stop stopper runworker go src github com cockroachdb cockroach pkg util stop stopper go goroutine net http persistconn writeloop usr local go src net http transport go created by net http transport dialconn usr local go src net http transport go goroutine net runtime pollwait usr local go src runtime netpoll go net polldesc wait usr local go src net fd poll runtime go net polldesc waitread usr local go src net fd poll runtime go net netfd read usr local go src net fd unix go net conn read usr local go src net net go net http persistconn read usr local go src net http transport go bufio reader fill usr local go src bufio bufio go bufio reader peek usr local go src bufio bufio go net http persistconn readloop usr local go src net http transport go created by net http transport dialconn usr local go src net http transport go goroutine github com cockroachdb cockroach pkg rpc context runheartbeat go src github com cockroachdb cockroach pkg rpc context go github com cockroachdb cockroach pkg rpc context grpcdial go src github com cockroachdb cockroach pkg rpc context go github com cockroachdb cockroach pkg util stop stopper runworker go src github com cockroachdb cockroach pkg util stop stopper go created by github com cockroachdb cockroach pkg util stop stopper runworker go src github com cockroachdb cockroach pkg util stop stopper go goroutine github com cockroachdb cockroach vendor google golang org grpc addrconn resettransport go src github com cockroachdb cockroach vendor google golang org grpc clientconn go github com cockroachdb cockroach vendor google golang org grpc addrconn transportmonitor go src github com cockroachdb cockroach vendor google golang org grpc clientconn go github com cockroachdb cockroach vendor google golang org grpc clientconn resetaddrconn go src github com cockroachdb cockroach vendor google golang org grpc clientconn go created by github com cockroachdb cockroach vendor google golang org grpc clientconn resetaddrconn go src github com cockroachdb cockroach vendor google golang org grpc clientconn go goroutine net http persistconn writeloop usr local go src net http transport go created by net http transport dialconn usr local go src net http transport go goroutine net runtime pollwait usr local go src runtime netpoll go net polldesc wait usr local go src net fd poll runtime go net polldesc waitread usr local go src net fd poll runtime go net netfd read usr local go src net fd unix go net conn read usr local go src net net go net http persistconn read usr local go src net http transport go bufio reader fill usr local go src bufio bufio go bufio reader peek usr local go src bufio bufio go net http persistconn readloop usr local go src net http transport go created by net http transport dialconn usr local go src net http transport go goroutine database sql db connectionopener usr local go src database sql sql go created by database sql open usr local go src database sql sql go goroutine net http persistconn writeloop usr local go src net http transport go created by net http transport dialconn usr local go src net http transport go goroutine net runtime pollwait usr local go src runtime netpoll go net polldesc wait usr local go src net fd poll runtime go net polldesc waitread usr local go src net fd poll runtime go net netfd read usr local go src net fd unix go net conn read usr local go src net net go net http persistconn read usr local go src net http transport go bufio reader fill usr local go src bufio bufio go bufio reader peek usr local go src bufio bufio go net http persistconn readloop usr local go src net http transport go created by net http transport dialconn usr local go src net http transport go goroutine net runtime pollwait usr local go src runtime netpoll go net polldesc wait usr local go src net fd poll runtime go net polldesc waitread usr local go src net fd poll runtime go net netfd read usr local go src net fd unix go net conn read usr local go src net net go net http persistconn read usr local go src net http transport go bufio reader fill usr local go src bufio bufio go bufio reader peek usr local go src bufio bufio go net http persistconn readloop usr local go src net http transport go created by net http transport dialconn usr local go src net http transport go goroutine database sql db connectionopener usr local go src database sql sql go created by database sql open usr local go src database sql sql go goroutine github com cockroachdb cockroach vendor google golang org grpc addrconn resettransport go src github com cockroachdb cockroach vendor google golang org grpc clientconn go github com cockroachdb cockroach vendor google golang org grpc addrconn transportmonitor go src github com cockroachdb cockroach vendor google golang org grpc clientconn go github com cockroachdb cockroach vendor google golang org grpc clientconn resetaddrconn go src github com cockroachdb cockroach vendor google golang org grpc clientconn go created by github com cockroachdb cockroach vendor google golang org grpc clientconn resetaddrconn go src github com cockroachdb cockroach vendor google golang org grpc clientconn go goroutine database sql db connectionopener usr local go src database sql sql go created by database sql open usr local go src database sql sql go goroutine net runtime pollwait usr local go src runtime netpoll go net polldesc wait usr local go src net fd poll runtime go net polldesc waitread usr local go src net fd poll runtime go net netfd read usr local go src net fd unix go net conn read usr local go src net net go net http persistconn read usr local go src net http transport go bufio reader fill usr local go src bufio bufio go bufio reader peek usr local go src bufio bufio go net http persistconn readloop usr local go src net http transport go created by net http transport dialconn usr local go src net http transport go goroutine net http persistconn writeloop usr local go src net http transport go created by net http transport dialconn usr local go src net http transport go goroutine net http persistconn writeloop usr local go src net http transport go created by net http transport dialconn usr local go src net http transport go goroutine database sql db connectionopener usr local go src database sql sql go created by database sql open usr local go src database sql sql go goroutine github com cockroachdb cockroach pkg rpc context runheartbeat go src github com cockroachdb cockroach pkg rpc context go github com cockroachdb cockroach pkg rpc context grpcdial go src github com cockroachdb cockroach pkg rpc context go github com cockroachdb cockroach pkg util stop stopper runworker go src github com cockroachdb cockroach pkg util stop stopper go created by github com cockroachdb cockroach pkg util stop stopper runworker go src github com cockroachdb cockroach pkg util stop stopper go goroutine github com cockroachdb cockroach pkg rpc newcontext go src github com cockroachdb cockroach pkg rpc context go github com cockroachdb cockroach pkg util stop stopper runworker go src github com cockroachdb cockroach pkg util stop stopper go created by github com cockroachdb cockroach pkg util stop stopper runworker go src github com cockroachdb cockroach pkg util stop stopper go goroutine net runtime pollwait usr local go src runtime netpoll go net polldesc wait usr local go src net fd poll runtime go net polldesc waitread usr local go src net fd poll runtime go net netfd read usr local go src net fd unix go net conn read usr local go src net net go net http persistconn read usr local go src net http transport go bufio reader fill usr local go src bufio bufio go bufio reader peek usr local go src bufio bufio go net http persistconn readloop usr local go src net http transport go created by net http transport dialconn usr local go src net http transport go goroutine net runtime pollwait usr local go src runtime netpoll go net polldesc wait usr local go src net fd poll runtime go net polldesc waitread usr local go src net fd poll runtime go net netfd read usr local go src net fd unix go net conn read usr local go src net net go net http persistconn read usr local go src net http transport go bufio reader fill usr local go src bufio bufio go bufio reader peek usr local go src bufio bufio go net http persistconn readloop usr local go src net http transport go created by net http transport dialconn usr local go src net http transport go goroutine net http persistconn writeloop usr local go src net http transport go created by net http transport dialconn usr local go src net http transport go goroutine github com cockroachdb cockroach vendor google golang org grpc addrconn resettransport go src github com cockroachdb cockroach vendor google golang org grpc clientconn go github com cockroachdb cockroach vendor google golang org grpc addrconn transportmonitor go src github com cockroachdb cockroach vendor google golang org grpc clientconn go github com cockroachdb cockroach vendor google golang org grpc clientconn resetaddrconn go src github com cockroachdb cockroach vendor google golang org grpc clientconn go created by github com cockroachdb cockroach vendor google golang org grpc clientconn resetaddrconn go src github com cockroachdb cockroach vendor google golang org grpc clientconn go goroutine github com cockroachdb cockroach pkg rpc context runheartbeat go src github com cockroachdb cockroach pkg rpc context go github com cockroachdb cockroach pkg rpc context grpcdial go src github com cockroachdb cockroach pkg rpc context go github com cockroachdb cockroach pkg util stop stopper runworker go src github com cockroachdb cockroach pkg util stop stopper go created by github com cockroachdb cockroach pkg util stop stopper runworker go src github com cockroachdb cockroach pkg util stop stopper go goroutine github com cockroachdb cockroach pkg rpc newcontext go src github com cockroachdb cockroach pkg rpc context go github com cockroachdb cockroach pkg util stop stopper runworker go src github com cockroachdb cockroach pkg util stop stopper go created by github com cockroachdb cockroach pkg util stop stopper runworker go src github com cockroachdb cockroach pkg util stop stopper go goroutine net runtime pollwait usr local go src runtime netpoll go net polldesc wait usr local go src net fd poll runtime go net polldesc waitread usr local go src net fd poll runtime go net netfd read usr local go src net fd unix go net conn read usr local go src net net go net http persistconn read usr local go src net http transport go bufio reader fill usr local go src bufio bufio go bufio reader peek usr local go src bufio bufio go net http persistconn readloop usr local go src net http transport go created by net http transport dialconn usr local go src net http transport go goroutine net runtime pollwait usr local go src runtime netpoll go net polldesc wait usr local go src net fd poll runtime go net polldesc waitread usr local go src net fd poll runtime go net netfd read usr local go src net fd unix go net conn read usr local go src net net go net http persistconn read usr local go src net http transport go bufio reader fill usr local go src bufio bufio go bufio reader peek usr local go src bufio bufio go net http persistconn readloop usr local go src net http transport go created by net http transport dialconn usr local go src net http transport go goroutine net http persistconn writeloop usr local go src net http transport go created by net http transport dialconn usr local go src net http transport go goroutine github com cockroachdb cockroach pkg rpc context runheartbeat go src github com cockroachdb cockroach pkg rpc context go github com cockroachdb cockroach pkg rpc context grpcdial go src github com cockroachdb cockroach pkg rpc context go github com cockroachdb cockroach pkg util stop stopper runworker go src github com cockroachdb cockroach pkg util stop stopper go created by github com cockroachdb cockroach pkg util stop stopper runworker go src github com cockroachdb cockroach pkg util stop stopper go goroutine net http persistconn writeloop usr local go src net http transport go created by net http transport dialconn usr local go src net http transport go goroutine github com cockroachdb cockroach vendor google golang org grpc addrconn resettransport go src github com cockroachdb cockroach vendor google golang org grpc clientconn go github com cockroachdb cockroach vendor google golang org grpc addrconn transportmonitor go src github com cockroachdb cockroach vendor google golang org grpc clientconn go github com cockroachdb cockroach vendor google golang org grpc clientconn resetaddrconn go src github com cockroachdb cockroach vendor google golang org grpc clientconn go created by github com cockroachdb cockroach vendor google golang org grpc clientconn resetaddrconn go src github com cockroachdb cockroach vendor google golang org grpc clientconn go goroutine net http persistconn writeloop usr local go src net http transport go created by net http transport dialconn usr local go src net http transport go goroutine net http persistconn writeloop usr local go src net http transport go created by net http transport dialconn usr local go src net http transport go goroutine net runtime pollwait usr local go src runtime netpoll go net polldesc wait usr local go src net fd poll runtime go net polldesc waitread usr local go src net fd poll runtime go net netfd read usr local go src net fd unix go net conn read usr local go src net net go net http persistconn read usr local go src net http transport go bufio reader fill usr local go src bufio bufio go bufio reader peek usr local go src bufio bufio go net http persistconn readloop usr local go src net http transport go created by net http transport dialconn usr local go src net http transport go goroutine net runtime pollwait usr local go src runtime netpoll go net polldesc wait usr local go src net fd poll runtime go net polldesc waitread usr local go src net fd poll runtime go net netfd read usr local go src net fd unix go net conn read usr local go src net net go net http persistconn read usr local go src net http transport go bufio reader fill usr local go src bufio bufio go bufio reader peek usr local go src bufio bufio go net http persistconn readloop usr local go src net http transport go created by net http transport dialconn usr local go src net http transport go goroutine net runtime pollwait usr local go src runtime netpoll go net polldesc wait usr local go src net fd poll runtime go net polldesc waitread usr local go src net fd poll runtime go net netfd read usr local go src net fd unix go net conn read usr local go src net net go net http persistconn read usr local go src net http transport go bufio reader fill usr local go src bufio bufio go bufio reader peek usr local go src bufio bufio go net http persistconn readloop usr local go src net http transport go created by net http transport dialconn usr local go src net http transport go goroutine github com cockroachdb cockroach vendor google golang org grpc addrconn resettransport go src github com cockroachdb cockroach vendor google golang org grpc clientconn go github com cockroachdb cockroach vendor google golang org grpc addrconn transportmonitor go src github com cockroachdb cockroach vendor google golang org grpc clientconn go github com cockroachdb cockroach vendor google golang org grpc clientconn resetaddrconn go src github com cockroachdb cockroach vendor google golang org grpc clientconn go created by github com cockroachdb cockroach vendor google golang org grpc clientconn resetaddrconn go src github com cockroachdb cockroach vendor google golang org grpc clientconn go goroutine net runtime pollwait usr local go src runtime netpoll go net polldesc wait usr local go src net fd poll runtime go net polldesc waitread usr local go src net fd poll runtime go net netfd read usr local go src net fd unix go net conn read usr local go src net net go net http persistconn read usr local go src net http transport go bufio reader fill usr local go src bufio bufio go bufio reader peek usr local go src bufio bufio go net http persistconn readloop usr local go src net http transport go created by net http transport dialconn usr local go src net http transport go goroutine net http persistconn writeloop usr please assign take a look and update the issue accordingly | 0 |
54,500 | 6,823,491,918 | IssuesEvent | 2017-11-08 00:15:33 | blockstack/designs | https://api.github.com/repos/blockstack/designs | closed | blockstack ppt and keynote template design | design production v3.1.0 | @guylepage3 commented on [Mon Oct 03 2016](https://github.com/blockstack/blockstack/issues/84)
@muneeb-ali commented on [Thu Aug 18 2016](https://github.com/blockstack/community/issues/2)
@guylepage3 commented on [Wed Aug 17 2016](https://github.com/blockstack/marketing/issues/6)
Design the Blockstack PPT presentation template design for the community.
---
@guylepage3 commented on [Thu Aug 25 2016](https://github.com/blockstack/community/issues/2#issuecomment-242462104)
So we will need to have users download the Blockstack fonts in order to view the PPT template correctly on both Mac OS and Windows. Fortunately Blockstack utilizes cross-platform typefaces from Google Fonts. Furthermore, it's extremely easy for users to install fonts on a Windows machine.
Windows Google Font install tutorial:
https://youtu.be/eYmX5ysQLs0?t=1m30s
**Download Blockstack Fonts**:
- **Primary Font** - Source Code Pro - https://fonts.google.com/selection?query=source+code+p&selection.family=Source+Code+Pro:200,300,400,500,600,700
- **Secondary Font** - Lato - https://fonts.google.com/selection?query=Lato&selection.family=Lato:100,100i,300,300i,400,400i,700,700i
| 1.0 | blockstack ppt and keynote template design - @guylepage3 commented on [Mon Oct 03 2016](https://github.com/blockstack/blockstack/issues/84)
@muneeb-ali commented on [Thu Aug 18 2016](https://github.com/blockstack/community/issues/2)
@guylepage3 commented on [Wed Aug 17 2016](https://github.com/blockstack/marketing/issues/6)
Design the Blockstack PPT presentation template design for the community.
---
@guylepage3 commented on [Thu Aug 25 2016](https://github.com/blockstack/community/issues/2#issuecomment-242462104)
So we will need to have users download the Blockstack fonts in order to view the PPT template correctly on both Mac OS and Windows. Fortunately Blockstack utilizes cross-platform typefaces from Google Fonts. Furthermore, it's extremely easy for users to install fonts on a Windows machine.
Windows Google Font install tutorial:
https://youtu.be/eYmX5ysQLs0?t=1m30s
**Download Blockstack Fonts**:
- **Primary Font** - Source Code Pro - https://fonts.google.com/selection?query=source+code+p&selection.family=Source+Code+Pro:200,300,400,500,600,700
- **Secondary Font** - Lato - https://fonts.google.com/selection?query=Lato&selection.family=Lato:100,100i,300,300i,400,400i,700,700i
| non_priority | blockstack ppt and keynote template design commented on muneeb ali commented on commented on design the blockstack ppt presentation template design for the community commented on so we will need to have users download the blockstack fonts in order to view the ppt template correctly on both mac os and windows fortunately blockstack utilizes cross platform typefaces from google fonts furthermore it s extremely easy for users to install fonts on a windows machine windows google font install tutorial download blockstack fonts primary font source code pro secondary font lato | 0 |
27,234 | 11,463,398,728 | IssuesEvent | 2020-02-07 15:56:12 | Techini/juice-shop | https://api.github.com/repos/Techini/juice-shop | opened | CVE-2019-6283 (Medium) detected in node-sass-c6f2e5a1643dd00105b63a638756dc99fc33c3e4 | security vulnerability | ## CVE-2019-6283 - Medium Severity Vulnerability
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Library - <b>node-sassc6f2e5a1643dd00105b63a638756dc99fc33c3e4</b></p></summary>
<p>
<p>:rainbow: Node.js bindings to libsass</p>
<p>Library home page: <a href=https://github.com/sass/node-sass.git>https://github.com/sass/node-sass.git</a></p>
<p>Found in HEAD commit: <a href="https://github.com/Techini/juice-shop/commit/77ff18d7d50a1115dce65ed2ad6dd63af8059b63">77ff18d7d50a1115dce65ed2ad6dd63af8059b63</a></p>
</p>
</details>
</p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Library Source Files (65)</summary>
<p></p>
<p> * The source files were matched to this source library based on a best effort match. Source libraries are selected from a list of probable public libraries.</p>
<p>
- /juice-shop/frontend/node_modules/node-sass/src/libsass/src/expand.hpp
- /juice-shop/frontend/node_modules/node-sass/src/libsass/src/expand.cpp
- /juice-shop/frontend/node_modules/node-sass/src/sass_types/factory.cpp
- /juice-shop/frontend/node_modules/node-sass/src/libsass/src/operators.cpp
- /juice-shop/frontend/node_modules/node-sass/src/sass_types/boolean.cpp
- /juice-shop/frontend/node_modules/node-sass/src/libsass/src/util.hpp
- /juice-shop/frontend/node_modules/node-sass/src/sass_types/value.h
- /juice-shop/frontend/node_modules/node-sass/src/libsass/src/emitter.hpp
- /juice-shop/frontend/node_modules/node-sass/src/callback_bridge.h
- /juice-shop/frontend/node_modules/node-sass/src/libsass/src/file.cpp
- /juice-shop/frontend/node_modules/node-sass/src/libsass/src/sass.cpp
- /juice-shop/frontend/node_modules/node-sass/src/libsass/src/operation.hpp
- /juice-shop/frontend/node_modules/node-sass/src/libsass/src/operators.hpp
- /juice-shop/frontend/node_modules/node-sass/src/libsass/src/constants.hpp
- /juice-shop/frontend/node_modules/node-sass/src/libsass/src/error_handling.hpp
- /juice-shop/frontend/node_modules/node-sass/src/libsass/src/parser.hpp
- /juice-shop/frontend/node_modules/node-sass/src/libsass/src/constants.cpp
- /juice-shop/frontend/node_modules/node-sass/src/sass_types/list.cpp
- /juice-shop/frontend/node_modules/node-sass/src/libsass/src/cssize.cpp
- /juice-shop/frontend/node_modules/node-sass/src/libsass/src/functions.hpp
- /juice-shop/frontend/node_modules/node-sass/src/libsass/src/util.cpp
- /juice-shop/frontend/node_modules/node-sass/src/custom_function_bridge.cpp
- /juice-shop/frontend/node_modules/node-sass/src/custom_importer_bridge.h
- /juice-shop/frontend/node_modules/node-sass/src/libsass/src/bind.cpp
- /juice-shop/frontend/node_modules/node-sass/src/libsass/src/eval.hpp
- /juice-shop/frontend/node_modules/node-sass/src/libsass/src/inspect.cpp
- /juice-shop/frontend/node_modules/node-sass/src/libsass/src/backtrace.cpp
- /juice-shop/frontend/node_modules/node-sass/src/libsass/src/extend.cpp
- /juice-shop/frontend/node_modules/node-sass/src/sass_context_wrapper.h
- /juice-shop/frontend/node_modules/node-sass/src/sass_types/sass_value_wrapper.h
- /juice-shop/frontend/node_modules/node-sass/src/libsass/src/error_handling.cpp
- /juice-shop/frontend/node_modules/node-sass/src/libsass/src/parser.cpp
- /juice-shop/frontend/node_modules/node-sass/src/libsass/src/debugger.hpp
- /juice-shop/frontend/node_modules/node-sass/src/libsass/src/emitter.cpp
- /juice-shop/frontend/node_modules/node-sass/src/sass_types/number.cpp
- /juice-shop/frontend/node_modules/node-sass/src/sass_types/color.h
- /juice-shop/frontend/node_modules/node-sass/src/libsass/src/ast.hpp
- /juice-shop/frontend/node_modules/node-sass/src/libsass/src/sass_values.cpp
- /juice-shop/frontend/node_modules/node-sass/src/libsass/src/output.cpp
- /juice-shop/frontend/node_modules/node-sass/src/libsass/src/check_nesting.cpp
- /juice-shop/frontend/node_modules/node-sass/src/sass_types/null.cpp
- /juice-shop/frontend/node_modules/node-sass/src/libsass/src/ast_def_macros.hpp
- /juice-shop/frontend/node_modules/node-sass/src/libsass/src/functions.cpp
- /juice-shop/frontend/node_modules/node-sass/src/libsass/src/cssize.hpp
- /juice-shop/frontend/node_modules/node-sass/src/libsass/src/prelexer.cpp
- /juice-shop/frontend/node_modules/node-sass/src/libsass/src/ast.cpp
- /juice-shop/frontend/node_modules/node-sass/src/libsass/src/to_c.cpp
- /juice-shop/frontend/node_modules/node-sass/src/libsass/src/to_value.hpp
- /juice-shop/frontend/node_modules/node-sass/src/libsass/src/ast_fwd_decl.hpp
- /juice-shop/frontend/node_modules/node-sass/src/sass_types/color.cpp
- /juice-shop/frontend/node_modules/node-sass/src/libsass/src/inspect.hpp
- /juice-shop/frontend/node_modules/node-sass/src/libsass/src/values.cpp
- /juice-shop/frontend/node_modules/node-sass/src/sass_context_wrapper.cpp
- /juice-shop/frontend/node_modules/node-sass/src/sass_types/list.h
- /juice-shop/frontend/node_modules/node-sass/src/libsass/src/check_nesting.hpp
- /juice-shop/frontend/node_modules/node-sass/src/libsass/src/to_value.cpp
- /juice-shop/frontend/node_modules/node-sass/src/libsass/src/context.cpp
- /juice-shop/frontend/node_modules/node-sass/src/sass_types/map.cpp
- /juice-shop/frontend/node_modules/node-sass/src/binding.cpp
- /juice-shop/frontend/node_modules/node-sass/src/libsass/src/sass_context.cpp
- /juice-shop/frontend/node_modules/node-sass/src/sass_types/string.cpp
- /juice-shop/frontend/node_modules/node-sass/src/libsass/src/prelexer.hpp
- /juice-shop/frontend/node_modules/node-sass/src/libsass/src/context.hpp
- /juice-shop/frontend/node_modules/node-sass/src/sass_types/boolean.h
- /juice-shop/frontend/node_modules/node-sass/src/libsass/src/eval.cpp
</p>
</details>
<p></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/medium_vul.png' width=19 height=20> Vulnerability Details</summary>
<p>
In LibSass 3.5.5, a heap-based buffer over-read exists in Sass::Prelexer::parenthese_scope in prelexer.hpp.
<p>Publish Date: 2019-01-14
<p>URL: <a href=https://vuln.whitesourcesoftware.com/vulnerability/CVE-2019-6283>CVE-2019-6283</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/cvss3.png' width=19 height=20> CVSS 3 Score Details (<b>6.5</b>)</summary>
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: Required
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: None
- Integrity Impact: None
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/suggested_fix.png' width=19 height=20> Suggested Fix</summary>
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-6284">https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-6284</a></p>
<p>Release Date: 2019-08-06</p>
<p>Fix Resolution: 3.6.0</p>
</p>
</details>
<p></p>
***
Step up your Open Source Security Game with WhiteSource [here](https://www.whitesourcesoftware.com/full_solution_bolt_github) | True | CVE-2019-6283 (Medium) detected in node-sass-c6f2e5a1643dd00105b63a638756dc99fc33c3e4 - ## CVE-2019-6283 - Medium Severity Vulnerability
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Library - <b>node-sassc6f2e5a1643dd00105b63a638756dc99fc33c3e4</b></p></summary>
<p>
<p>:rainbow: Node.js bindings to libsass</p>
<p>Library home page: <a href=https://github.com/sass/node-sass.git>https://github.com/sass/node-sass.git</a></p>
<p>Found in HEAD commit: <a href="https://github.com/Techini/juice-shop/commit/77ff18d7d50a1115dce65ed2ad6dd63af8059b63">77ff18d7d50a1115dce65ed2ad6dd63af8059b63</a></p>
</p>
</details>
</p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Library Source Files (65)</summary>
<p></p>
<p> * The source files were matched to this source library based on a best effort match. Source libraries are selected from a list of probable public libraries.</p>
<p>
- /juice-shop/frontend/node_modules/node-sass/src/libsass/src/expand.hpp
- /juice-shop/frontend/node_modules/node-sass/src/libsass/src/expand.cpp
- /juice-shop/frontend/node_modules/node-sass/src/sass_types/factory.cpp
- /juice-shop/frontend/node_modules/node-sass/src/libsass/src/operators.cpp
- /juice-shop/frontend/node_modules/node-sass/src/sass_types/boolean.cpp
- /juice-shop/frontend/node_modules/node-sass/src/libsass/src/util.hpp
- /juice-shop/frontend/node_modules/node-sass/src/sass_types/value.h
- /juice-shop/frontend/node_modules/node-sass/src/libsass/src/emitter.hpp
- /juice-shop/frontend/node_modules/node-sass/src/callback_bridge.h
- /juice-shop/frontend/node_modules/node-sass/src/libsass/src/file.cpp
- /juice-shop/frontend/node_modules/node-sass/src/libsass/src/sass.cpp
- /juice-shop/frontend/node_modules/node-sass/src/libsass/src/operation.hpp
- /juice-shop/frontend/node_modules/node-sass/src/libsass/src/operators.hpp
- /juice-shop/frontend/node_modules/node-sass/src/libsass/src/constants.hpp
- /juice-shop/frontend/node_modules/node-sass/src/libsass/src/error_handling.hpp
- /juice-shop/frontend/node_modules/node-sass/src/libsass/src/parser.hpp
- /juice-shop/frontend/node_modules/node-sass/src/libsass/src/constants.cpp
- /juice-shop/frontend/node_modules/node-sass/src/sass_types/list.cpp
- /juice-shop/frontend/node_modules/node-sass/src/libsass/src/cssize.cpp
- /juice-shop/frontend/node_modules/node-sass/src/libsass/src/functions.hpp
- /juice-shop/frontend/node_modules/node-sass/src/libsass/src/util.cpp
- /juice-shop/frontend/node_modules/node-sass/src/custom_function_bridge.cpp
- /juice-shop/frontend/node_modules/node-sass/src/custom_importer_bridge.h
- /juice-shop/frontend/node_modules/node-sass/src/libsass/src/bind.cpp
- /juice-shop/frontend/node_modules/node-sass/src/libsass/src/eval.hpp
- /juice-shop/frontend/node_modules/node-sass/src/libsass/src/inspect.cpp
- /juice-shop/frontend/node_modules/node-sass/src/libsass/src/backtrace.cpp
- /juice-shop/frontend/node_modules/node-sass/src/libsass/src/extend.cpp
- /juice-shop/frontend/node_modules/node-sass/src/sass_context_wrapper.h
- /juice-shop/frontend/node_modules/node-sass/src/sass_types/sass_value_wrapper.h
- /juice-shop/frontend/node_modules/node-sass/src/libsass/src/error_handling.cpp
- /juice-shop/frontend/node_modules/node-sass/src/libsass/src/parser.cpp
- /juice-shop/frontend/node_modules/node-sass/src/libsass/src/debugger.hpp
- /juice-shop/frontend/node_modules/node-sass/src/libsass/src/emitter.cpp
- /juice-shop/frontend/node_modules/node-sass/src/sass_types/number.cpp
- /juice-shop/frontend/node_modules/node-sass/src/sass_types/color.h
- /juice-shop/frontend/node_modules/node-sass/src/libsass/src/ast.hpp
- /juice-shop/frontend/node_modules/node-sass/src/libsass/src/sass_values.cpp
- /juice-shop/frontend/node_modules/node-sass/src/libsass/src/output.cpp
- /juice-shop/frontend/node_modules/node-sass/src/libsass/src/check_nesting.cpp
- /juice-shop/frontend/node_modules/node-sass/src/sass_types/null.cpp
- /juice-shop/frontend/node_modules/node-sass/src/libsass/src/ast_def_macros.hpp
- /juice-shop/frontend/node_modules/node-sass/src/libsass/src/functions.cpp
- /juice-shop/frontend/node_modules/node-sass/src/libsass/src/cssize.hpp
- /juice-shop/frontend/node_modules/node-sass/src/libsass/src/prelexer.cpp
- /juice-shop/frontend/node_modules/node-sass/src/libsass/src/ast.cpp
- /juice-shop/frontend/node_modules/node-sass/src/libsass/src/to_c.cpp
- /juice-shop/frontend/node_modules/node-sass/src/libsass/src/to_value.hpp
- /juice-shop/frontend/node_modules/node-sass/src/libsass/src/ast_fwd_decl.hpp
- /juice-shop/frontend/node_modules/node-sass/src/sass_types/color.cpp
- /juice-shop/frontend/node_modules/node-sass/src/libsass/src/inspect.hpp
- /juice-shop/frontend/node_modules/node-sass/src/libsass/src/values.cpp
- /juice-shop/frontend/node_modules/node-sass/src/sass_context_wrapper.cpp
- /juice-shop/frontend/node_modules/node-sass/src/sass_types/list.h
- /juice-shop/frontend/node_modules/node-sass/src/libsass/src/check_nesting.hpp
- /juice-shop/frontend/node_modules/node-sass/src/libsass/src/to_value.cpp
- /juice-shop/frontend/node_modules/node-sass/src/libsass/src/context.cpp
- /juice-shop/frontend/node_modules/node-sass/src/sass_types/map.cpp
- /juice-shop/frontend/node_modules/node-sass/src/binding.cpp
- /juice-shop/frontend/node_modules/node-sass/src/libsass/src/sass_context.cpp
- /juice-shop/frontend/node_modules/node-sass/src/sass_types/string.cpp
- /juice-shop/frontend/node_modules/node-sass/src/libsass/src/prelexer.hpp
- /juice-shop/frontend/node_modules/node-sass/src/libsass/src/context.hpp
- /juice-shop/frontend/node_modules/node-sass/src/sass_types/boolean.h
- /juice-shop/frontend/node_modules/node-sass/src/libsass/src/eval.cpp
</p>
</details>
<p></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/medium_vul.png' width=19 height=20> Vulnerability Details</summary>
<p>
In LibSass 3.5.5, a heap-based buffer over-read exists in Sass::Prelexer::parenthese_scope in prelexer.hpp.
<p>Publish Date: 2019-01-14
<p>URL: <a href=https://vuln.whitesourcesoftware.com/vulnerability/CVE-2019-6283>CVE-2019-6283</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/cvss3.png' width=19 height=20> CVSS 3 Score Details (<b>6.5</b>)</summary>
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: Required
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: None
- Integrity Impact: None
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/suggested_fix.png' width=19 height=20> Suggested Fix</summary>
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-6284">https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-6284</a></p>
<p>Release Date: 2019-08-06</p>
<p>Fix Resolution: 3.6.0</p>
</p>
</details>
<p></p>
***
Step up your Open Source Security Game with WhiteSource [here](https://www.whitesourcesoftware.com/full_solution_bolt_github) | non_priority | cve medium detected in node sass cve medium severity vulnerability vulnerable library node rainbow node js bindings to libsass library home page a href found in head commit a href library source files the source files were matched to this source library based on a best effort match source libraries are selected from a list of probable public libraries juice shop frontend node modules node sass src libsass src expand hpp juice shop frontend node modules node sass src libsass src expand cpp juice shop frontend node modules node sass src sass types factory cpp juice shop frontend node modules node sass src libsass src operators cpp juice shop frontend node modules node sass src sass types boolean cpp juice shop frontend node modules node sass src libsass src util hpp juice shop frontend node modules node sass src sass types value h juice shop frontend node modules node sass src libsass src emitter hpp juice shop frontend node modules node sass src callback bridge h juice shop frontend node modules node sass src libsass src file cpp juice shop frontend node modules node sass src libsass src sass cpp juice shop frontend node modules node sass src libsass src operation hpp juice shop frontend node modules node sass src libsass src operators hpp juice shop frontend node modules node sass src libsass src constants hpp juice shop frontend node modules node sass src libsass src error handling hpp juice shop frontend node modules node sass src libsass src parser hpp juice shop frontend node modules node sass src libsass src constants cpp juice shop frontend node modules node sass src sass types list cpp juice shop frontend node modules node sass src libsass src cssize cpp juice shop frontend node modules node sass src libsass src functions hpp juice shop frontend node modules node sass src libsass src util cpp juice shop frontend node modules node sass src custom function bridge cpp juice shop frontend node modules node sass src custom importer bridge h juice shop frontend node modules node sass src libsass src bind cpp juice shop frontend node modules node sass src libsass src eval hpp juice shop frontend node modules node sass src libsass src inspect cpp juice shop frontend node modules node sass src libsass src backtrace cpp juice shop frontend node modules node sass src libsass src extend cpp juice shop frontend node modules node sass src sass context wrapper h juice shop frontend node modules node sass src sass types sass value wrapper h juice shop frontend node modules node sass src libsass src error handling cpp juice shop frontend node modules node sass src libsass src parser cpp juice shop frontend node modules node sass src libsass src debugger hpp juice shop frontend node modules node sass src libsass src emitter cpp juice shop frontend node modules node sass src sass types number cpp juice shop frontend node modules node sass src sass types color h juice shop frontend node modules node sass src libsass src ast hpp juice shop frontend node modules node sass src libsass src sass values cpp juice shop frontend node modules node sass src libsass src output cpp juice shop frontend node modules node sass src libsass src check nesting cpp juice shop frontend node modules node sass src sass types null cpp juice shop frontend node modules node sass src libsass src ast def macros hpp juice shop frontend node modules node sass src libsass src functions cpp juice shop frontend node modules node sass src libsass src cssize hpp juice shop frontend node modules node sass src libsass src prelexer cpp juice shop frontend node modules node sass src libsass src ast cpp juice shop frontend node modules node sass src libsass src to c cpp juice shop frontend node modules node sass src libsass src to value hpp juice shop frontend node modules node sass src libsass src ast fwd decl hpp juice shop frontend node modules node sass src sass types color cpp juice shop frontend node modules node sass src libsass src inspect hpp juice shop frontend node modules node sass src libsass src values cpp juice shop frontend node modules node sass src sass context wrapper cpp juice shop frontend node modules node sass src sass types list h juice shop frontend node modules node sass src libsass src check nesting hpp juice shop frontend node modules node sass src libsass src to value cpp juice shop frontend node modules node sass src libsass src context cpp juice shop frontend node modules node sass src sass types map cpp juice shop frontend node modules node sass src binding cpp juice shop frontend node modules node sass src libsass src sass context cpp juice shop frontend node modules node sass src sass types string cpp juice shop frontend node modules node sass src libsass src prelexer hpp juice shop frontend node modules node sass src libsass src context hpp juice shop frontend node modules node sass src sass types boolean h juice shop frontend node modules node sass src libsass src eval cpp vulnerability details in libsass a heap based buffer over read exists in sass prelexer parenthese scope in prelexer hpp publish date url a href cvss score details base score metrics exploitability metrics attack vector network attack complexity low privileges required none user interaction required scope unchanged impact metrics confidentiality impact none integrity impact none availability impact high for more information on scores click a href suggested fix type upgrade version origin a href release date fix resolution step up your open source security game with whitesource | 0 |
75,688 | 25,999,575,284 | IssuesEvent | 2022-12-20 14:20:30 | vector-im/element-android | https://api.github.com/repos/vector-im/element-android | opened | Markdown Code Fences Broken | T-Defect | ### Steps to reproduce
Type the following into the chat:
````
```python
def f(x):
pass
```
````
### Outcome
The following is a screenshot taken from element desktop. You can see that the first message looks perfectly fine (correctly rendered markdown). But the screenshot below (taken on my android phone) shows that the same message is not correctly displayed on android.
<img width="559" alt="image" src="https://user-images.githubusercontent.com/29106652/208686889-0c79bb91-c1ab-4e79-8209-68f6d13337ec.png">
### Your phone model
Pixel 4a
### Operating system version
13
### Application version and app store
1.5.11
### Homeserver
#matrix:matrix.org
### Will you send logs?
No
### Are you willing to provide a PR?
No | 1.0 | Markdown Code Fences Broken - ### Steps to reproduce
Type the following into the chat:
````
```python
def f(x):
pass
```
````
### Outcome
The following is a screenshot taken from element desktop. You can see that the first message looks perfectly fine (correctly rendered markdown). But the screenshot below (taken on my android phone) shows that the same message is not correctly displayed on android.
<img width="559" alt="image" src="https://user-images.githubusercontent.com/29106652/208686889-0c79bb91-c1ab-4e79-8209-68f6d13337ec.png">
### Your phone model
Pixel 4a
### Operating system version
13
### Application version and app store
1.5.11
### Homeserver
#matrix:matrix.org
### Will you send logs?
No
### Are you willing to provide a PR?
No | non_priority | markdown code fences broken steps to reproduce type the following into the chat python def f x pass outcome the following is a screenshot taken from element desktop you can see that the first message looks perfectly fine correctly rendered markdown but the screenshot below taken on my android phone shows that the same message is not correctly displayed on android img width alt image src your phone model pixel operating system version application version and app store homeserver matrix matrix org will you send logs no are you willing to provide a pr no | 0 |
9,550 | 6,925,201,721 | IssuesEvent | 2017-11-30 15:16:26 | galaxyproject/galaxy | https://api.github.com/repos/galaxyproject/galaxy | closed | Workflow scheduling doesn't keep track of progress within a step. | area/dataset-collections area/jobs area/performance area/workflows | From @nsoranzo on Gitter:
> I have huge issues trying to schedule a workflow which executes a series of tools on ridiculously large (21989 elements) collections. If at some point a job handler is restarted it seems it restarts already (partially) completed steps from scratch, in fact a particular step/tool has already 114,557 jobs on the history (in various states).
So the problem is we flush invocation step states only after the whole step has been scheduled. With a collection that size though you could imagine scheduling a single step to take an hour - so it is very possible a hard restart of Galaxy could cause problems like this.
| True | Workflow scheduling doesn't keep track of progress within a step. - From @nsoranzo on Gitter:
> I have huge issues trying to schedule a workflow which executes a series of tools on ridiculously large (21989 elements) collections. If at some point a job handler is restarted it seems it restarts already (partially) completed steps from scratch, in fact a particular step/tool has already 114,557 jobs on the history (in various states).
So the problem is we flush invocation step states only after the whole step has been scheduled. With a collection that size though you could imagine scheduling a single step to take an hour - so it is very possible a hard restart of Galaxy could cause problems like this.
| non_priority | workflow scheduling doesn t keep track of progress within a step from nsoranzo on gitter i have huge issues trying to schedule a workflow which executes a series of tools on ridiculously large elements collections if at some point a job handler is restarted it seems it restarts already partially completed steps from scratch in fact a particular step tool has already jobs on the history in various states so the problem is we flush invocation step states only after the whole step has been scheduled with a collection that size though you could imagine scheduling a single step to take an hour so it is very possible a hard restart of galaxy could cause problems like this | 0 |
40,330 | 8,774,759,865 | IssuesEvent | 2018-12-18 20:50:44 | rubberduck-vba/Rubberduck | https://api.github.com/repos/rubberduck-vba/Rubberduck | opened | NRE in AssignmentNotUsedInspection | bug code-path-analysis | Taken from the Logs presented in #4645, apparently there's a NRE in the AssignmentNotUsedInspection:
```
2018-12-17 15:02:39.0728;WARN-2.3.1.4327;Rubberduck.Inspections.Rubberduck.Inspections.Inspector;System.NullReferenceException: Object reference not set to an instance of an object.
at Rubberduck.Inspections.CodePathAnalysis.Walker.GenerateTree(IParseTree tree, Declaration declaration) in C:\projects\rubberduck\Rubberduck.CodeAnalysis\CodePathAnalysis\Walker.cs:line 72
at Rubberduck.Inspections.Concrete.AssignmentNotUsedInspection.DoGetInspectionResults() in C:\projects\rubberduck\Rubberduck.CodeAnalysis\Inspections\Concrete\AssignmentNotUsedInspection.cs:line 33
at Rubberduck.Inspections.Abstract.InspectionBase.GetInspectionResults(CancellationToken token) in C:\projects\rubberduck\Rubberduck.CodeAnalysis\Inspections\Abstract\InspectionBase.cs:line 166
at Rubberduck.Inspections.Rubberduck.Inspections.Inspector.RunInspection(IInspection inspection, ConcurrentBag`1 allIssues, CancellationToken token) in C:\projects\rubberduck\Rubberduck.CodeAnalysis\Inspections\Inspector.cs:line 188;System.NullReferenceException: Object reference not set to an instance of an object.
at Rubberduck.Inspections.CodePathAnalysis.Walker.GenerateTree(IParseTree tree, Declaration declaration) in C:\projects\rubberduck\Rubberduck.CodeAnalysis\CodePathAnalysis\Walker.cs:line 72
at Rubberduck.Inspections.Concrete.AssignmentNotUsedInspection.DoGetInspectionResults() in C:\projects\rubberduck\Rubberduck.CodeAnalysis\Inspections\Concrete\AssignmentNotUsedInspection.cs:line 33
at Rubberduck.Inspections.Abstract.InspectionBase.GetInspectionResults(CancellationToken token) in C:\projects\rubberduck\Rubberduck.CodeAnalysis\Inspections\Abstract\InspectionBase.cs:line 166
at Rubberduck.Inspections.Rubberduck.Inspections.Inspector.RunInspection(IInspection inspection, ConcurrentBag`1 allIssues, CancellationToken token) in C:\projects\rubberduck\Rubberduck.CodeAnalysis\Inspections\Inspector.cs:line 188
``` | 1.0 | NRE in AssignmentNotUsedInspection - Taken from the Logs presented in #4645, apparently there's a NRE in the AssignmentNotUsedInspection:
```
2018-12-17 15:02:39.0728;WARN-2.3.1.4327;Rubberduck.Inspections.Rubberduck.Inspections.Inspector;System.NullReferenceException: Object reference not set to an instance of an object.
at Rubberduck.Inspections.CodePathAnalysis.Walker.GenerateTree(IParseTree tree, Declaration declaration) in C:\projects\rubberduck\Rubberduck.CodeAnalysis\CodePathAnalysis\Walker.cs:line 72
at Rubberduck.Inspections.Concrete.AssignmentNotUsedInspection.DoGetInspectionResults() in C:\projects\rubberduck\Rubberduck.CodeAnalysis\Inspections\Concrete\AssignmentNotUsedInspection.cs:line 33
at Rubberduck.Inspections.Abstract.InspectionBase.GetInspectionResults(CancellationToken token) in C:\projects\rubberduck\Rubberduck.CodeAnalysis\Inspections\Abstract\InspectionBase.cs:line 166
at Rubberduck.Inspections.Rubberduck.Inspections.Inspector.RunInspection(IInspection inspection, ConcurrentBag`1 allIssues, CancellationToken token) in C:\projects\rubberduck\Rubberduck.CodeAnalysis\Inspections\Inspector.cs:line 188;System.NullReferenceException: Object reference not set to an instance of an object.
at Rubberduck.Inspections.CodePathAnalysis.Walker.GenerateTree(IParseTree tree, Declaration declaration) in C:\projects\rubberduck\Rubberduck.CodeAnalysis\CodePathAnalysis\Walker.cs:line 72
at Rubberduck.Inspections.Concrete.AssignmentNotUsedInspection.DoGetInspectionResults() in C:\projects\rubberduck\Rubberduck.CodeAnalysis\Inspections\Concrete\AssignmentNotUsedInspection.cs:line 33
at Rubberduck.Inspections.Abstract.InspectionBase.GetInspectionResults(CancellationToken token) in C:\projects\rubberduck\Rubberduck.CodeAnalysis\Inspections\Abstract\InspectionBase.cs:line 166
at Rubberduck.Inspections.Rubberduck.Inspections.Inspector.RunInspection(IInspection inspection, ConcurrentBag`1 allIssues, CancellationToken token) in C:\projects\rubberduck\Rubberduck.CodeAnalysis\Inspections\Inspector.cs:line 188
``` | non_priority | nre in assignmentnotusedinspection taken from the logs presented in apparently there s a nre in the assignmentnotusedinspection warn rubberduck inspections rubberduck inspections inspector system nullreferenceexception object reference not set to an instance of an object at rubberduck inspections codepathanalysis walker generatetree iparsetree tree declaration declaration in c projects rubberduck rubberduck codeanalysis codepathanalysis walker cs line at rubberduck inspections concrete assignmentnotusedinspection dogetinspectionresults in c projects rubberduck rubberduck codeanalysis inspections concrete assignmentnotusedinspection cs line at rubberduck inspections abstract inspectionbase getinspectionresults cancellationtoken token in c projects rubberduck rubberduck codeanalysis inspections abstract inspectionbase cs line at rubberduck inspections rubberduck inspections inspector runinspection iinspection inspection concurrentbag allissues cancellationtoken token in c projects rubberduck rubberduck codeanalysis inspections inspector cs line system nullreferenceexception object reference not set to an instance of an object at rubberduck inspections codepathanalysis walker generatetree iparsetree tree declaration declaration in c projects rubberduck rubberduck codeanalysis codepathanalysis walker cs line at rubberduck inspections concrete assignmentnotusedinspection dogetinspectionresults in c projects rubberduck rubberduck codeanalysis inspections concrete assignmentnotusedinspection cs line at rubberduck inspections abstract inspectionbase getinspectionresults cancellationtoken token in c projects rubberduck rubberduck codeanalysis inspections abstract inspectionbase cs line at rubberduck inspections rubberduck inspections inspector runinspection iinspection inspection concurrentbag allissues cancellationtoken token in c projects rubberduck rubberduck codeanalysis inspections inspector cs line | 0 |